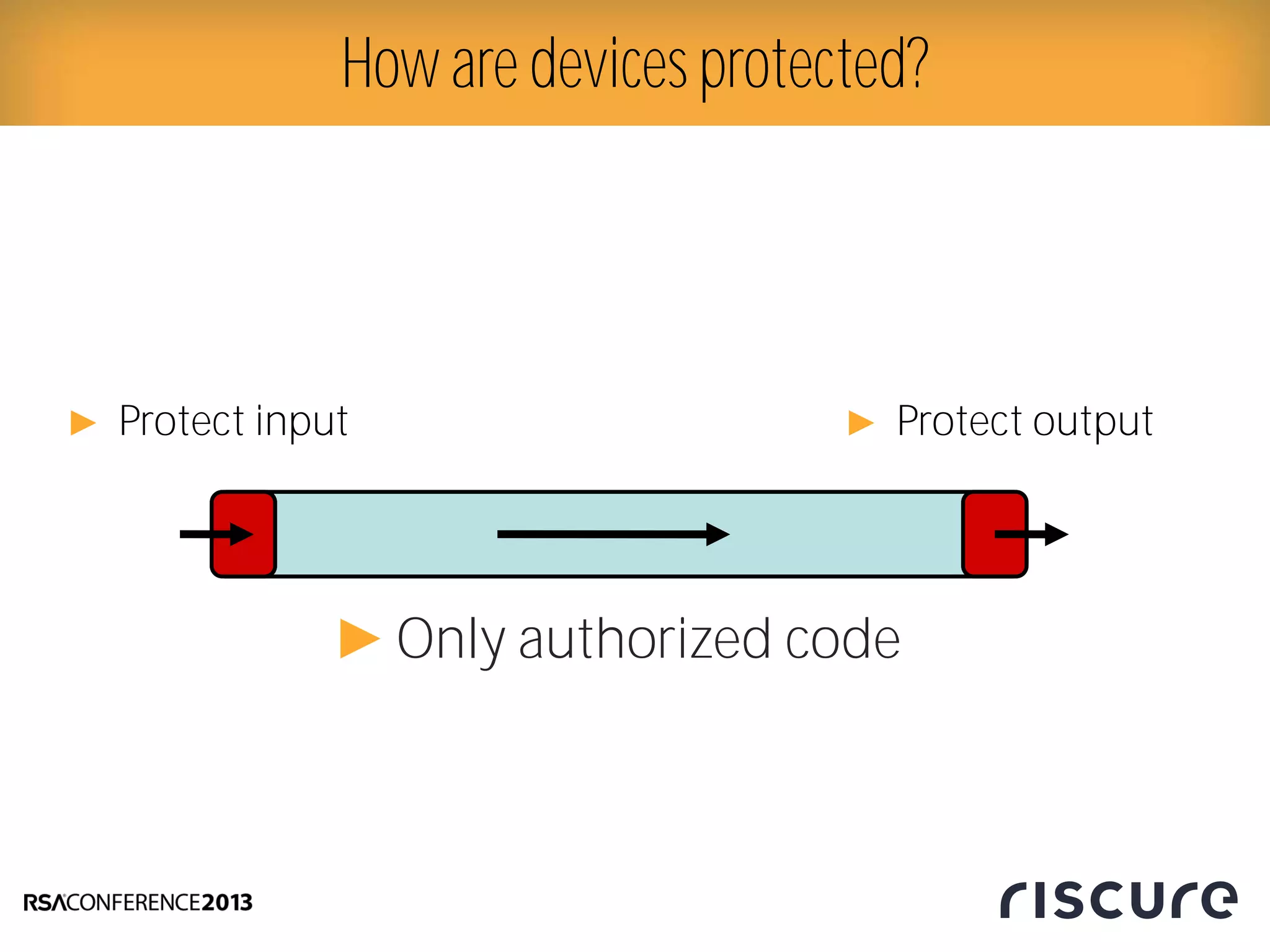
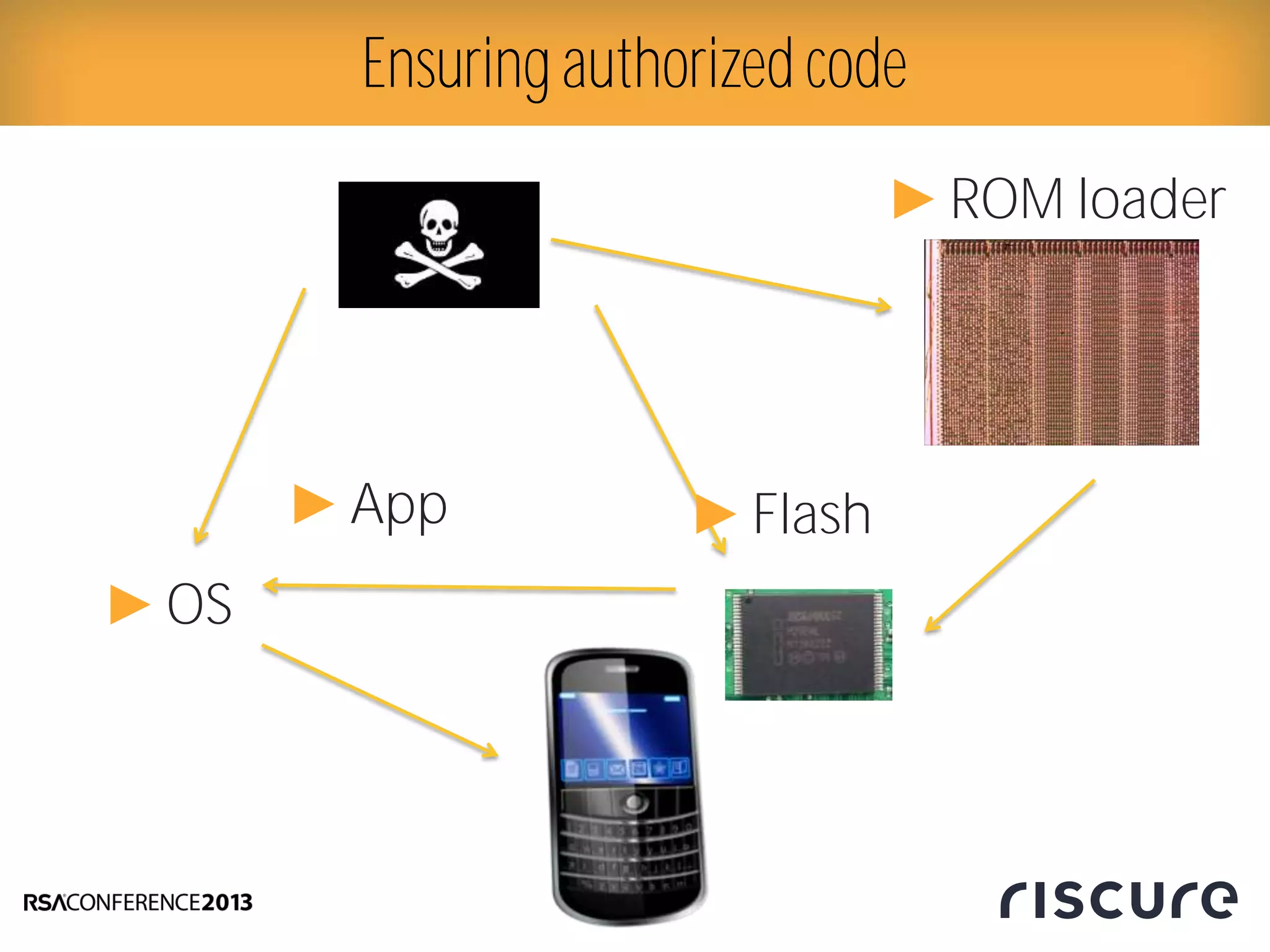
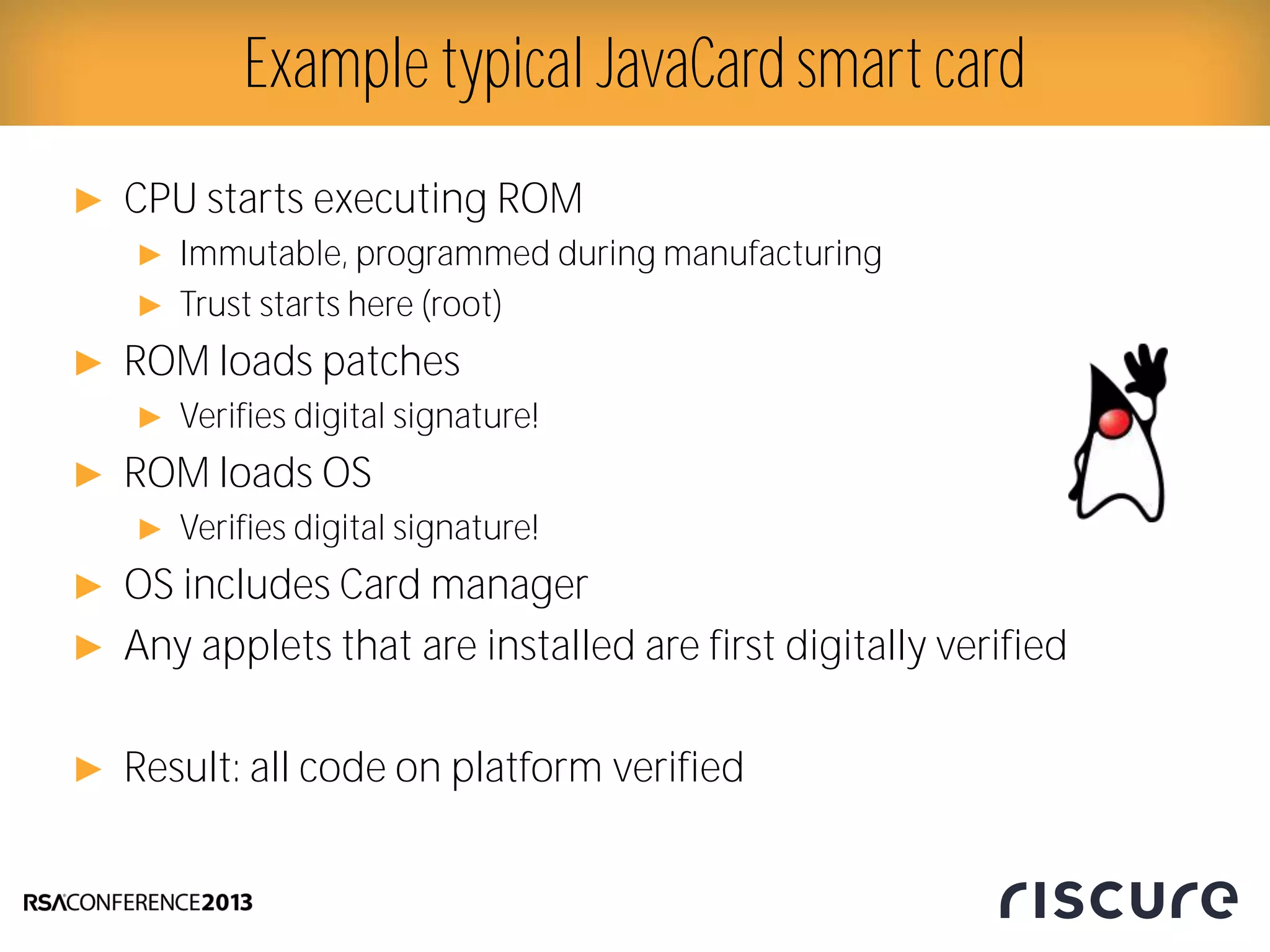
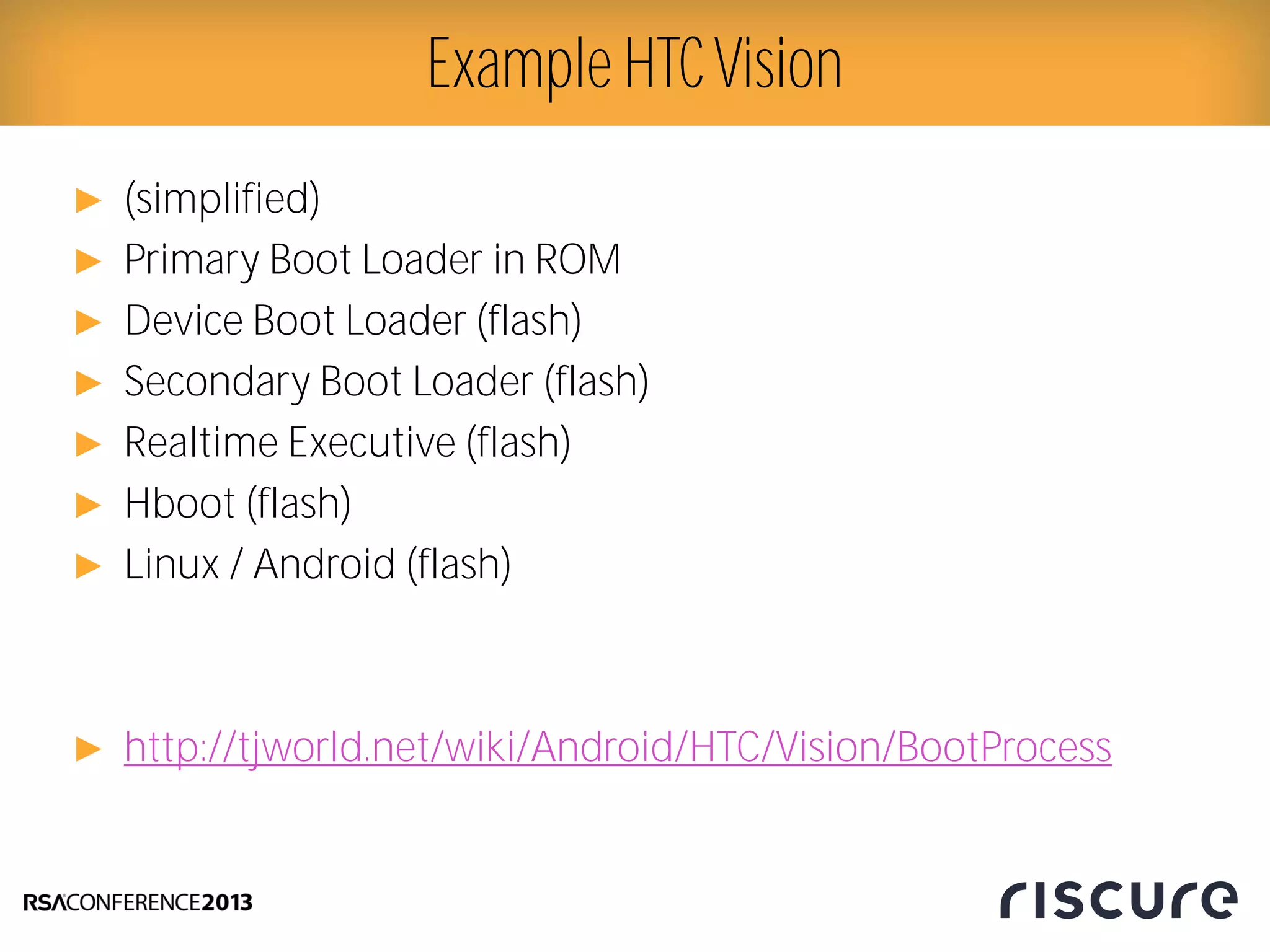
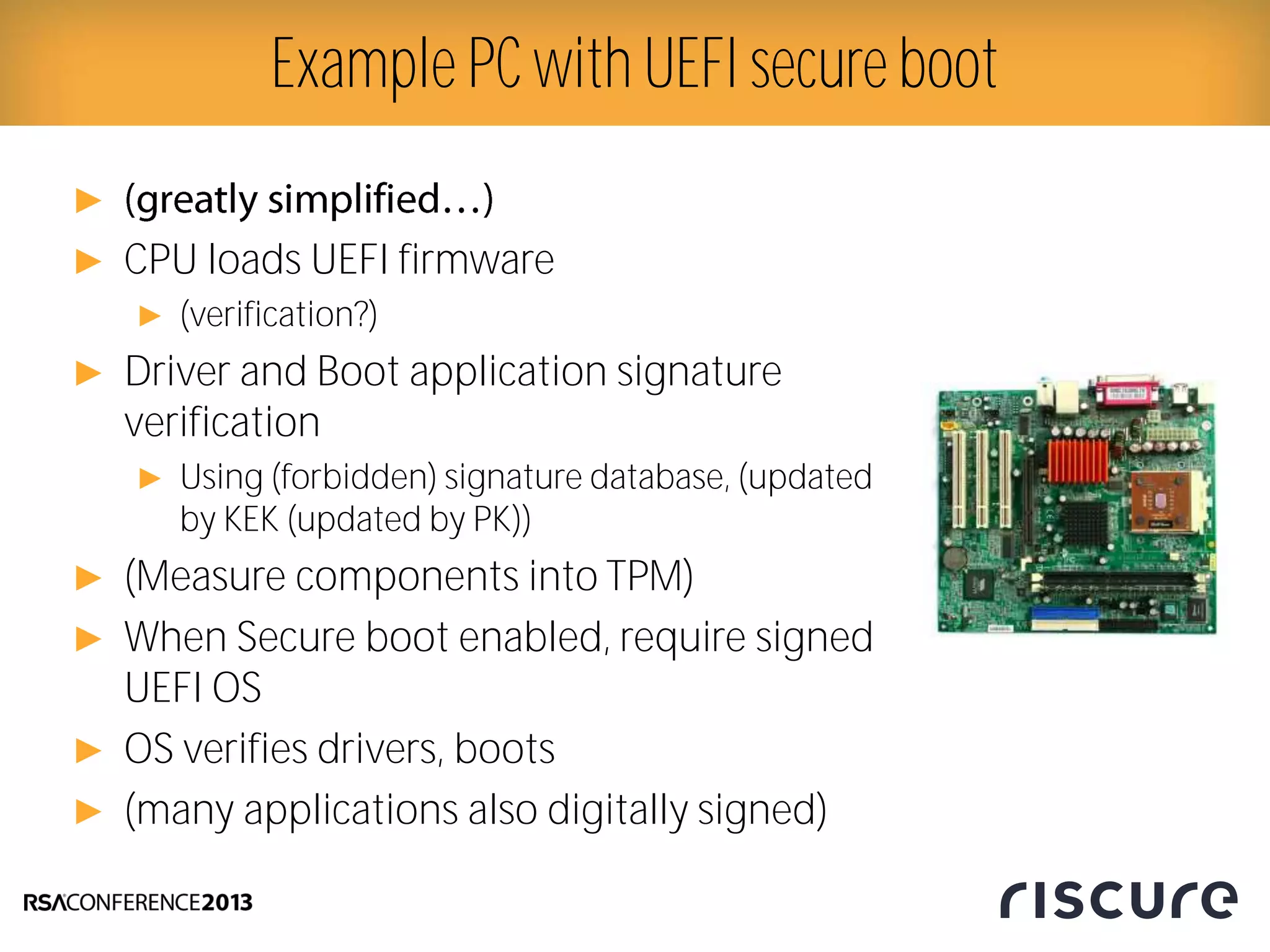
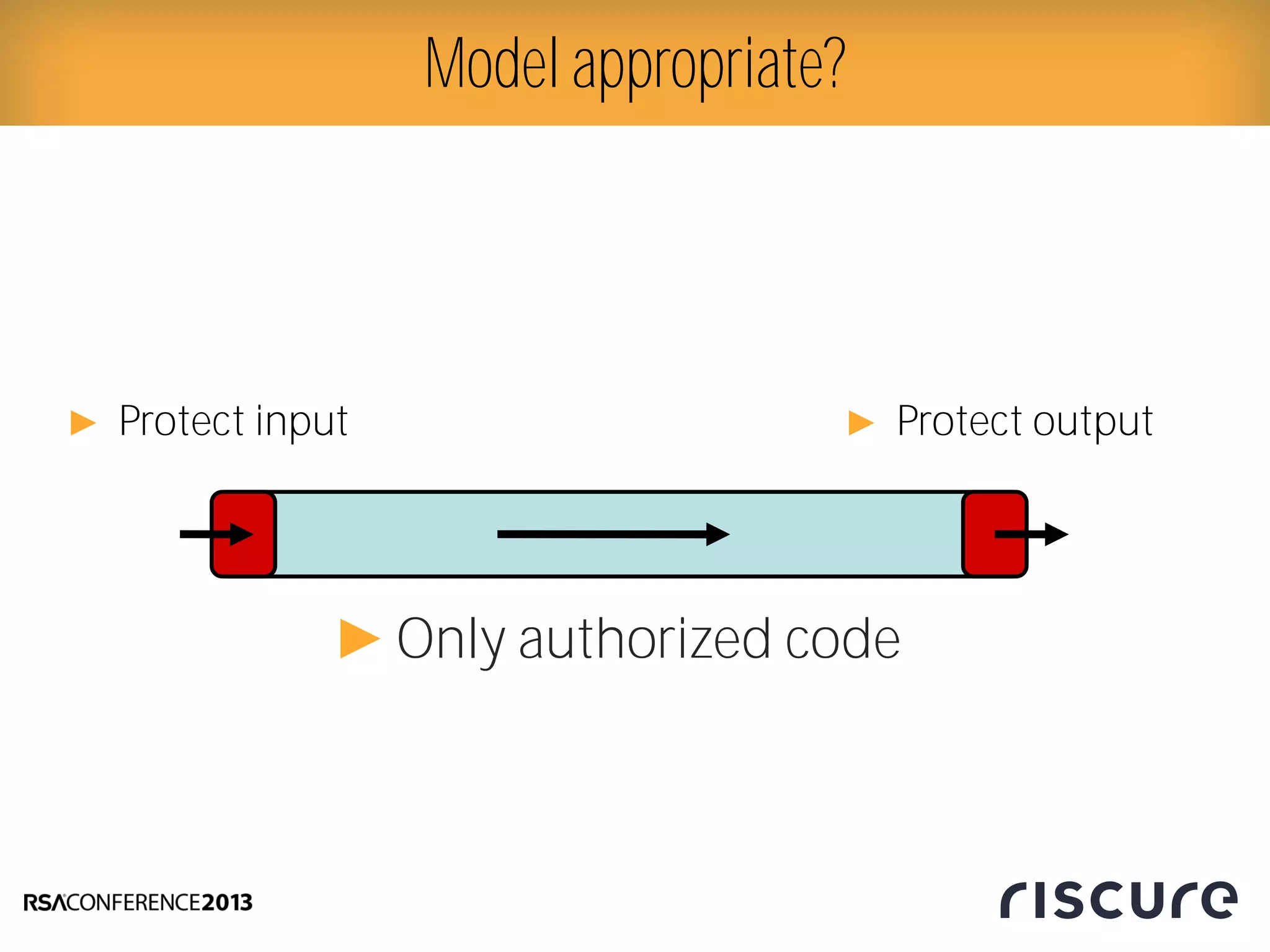
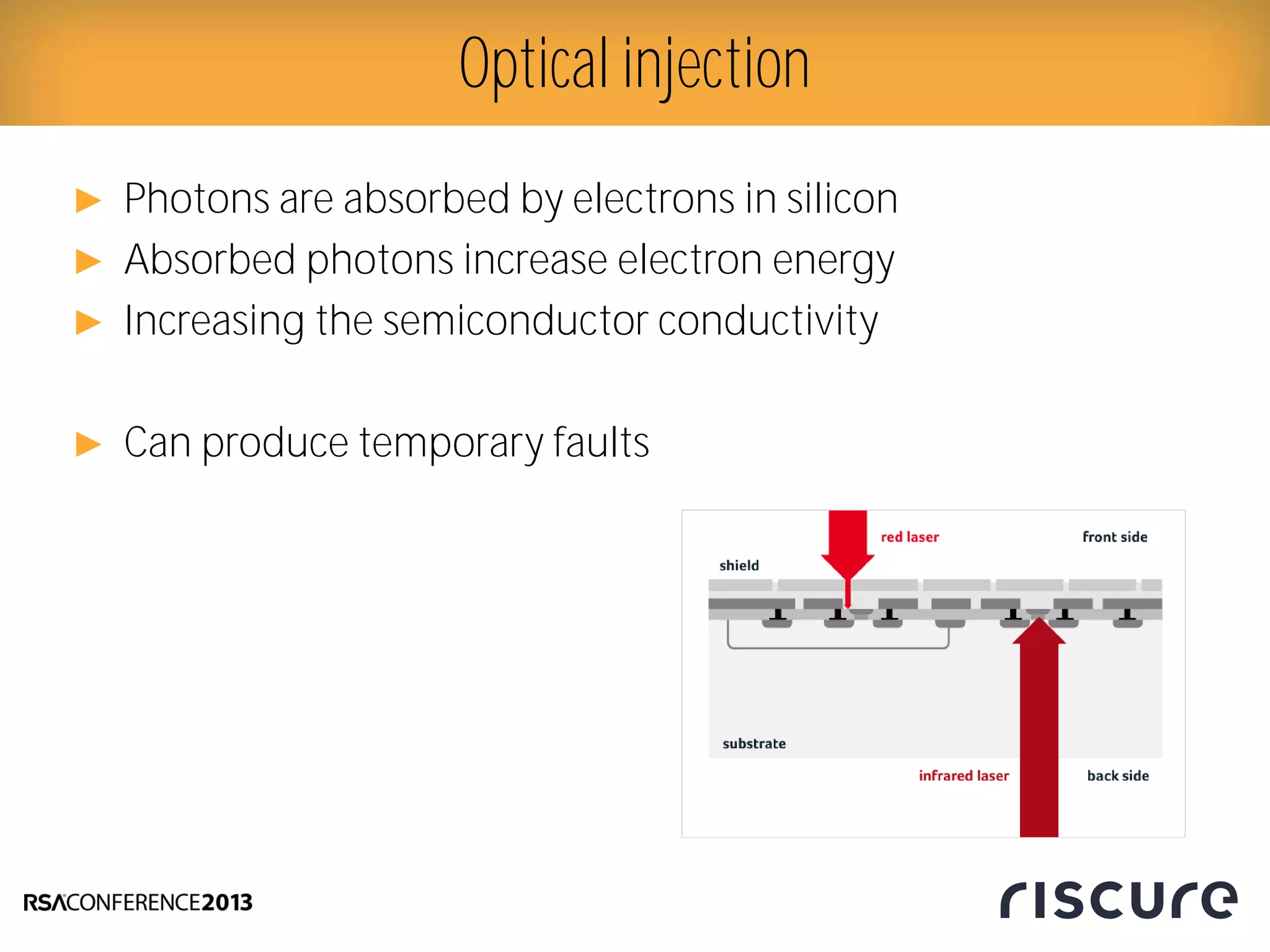
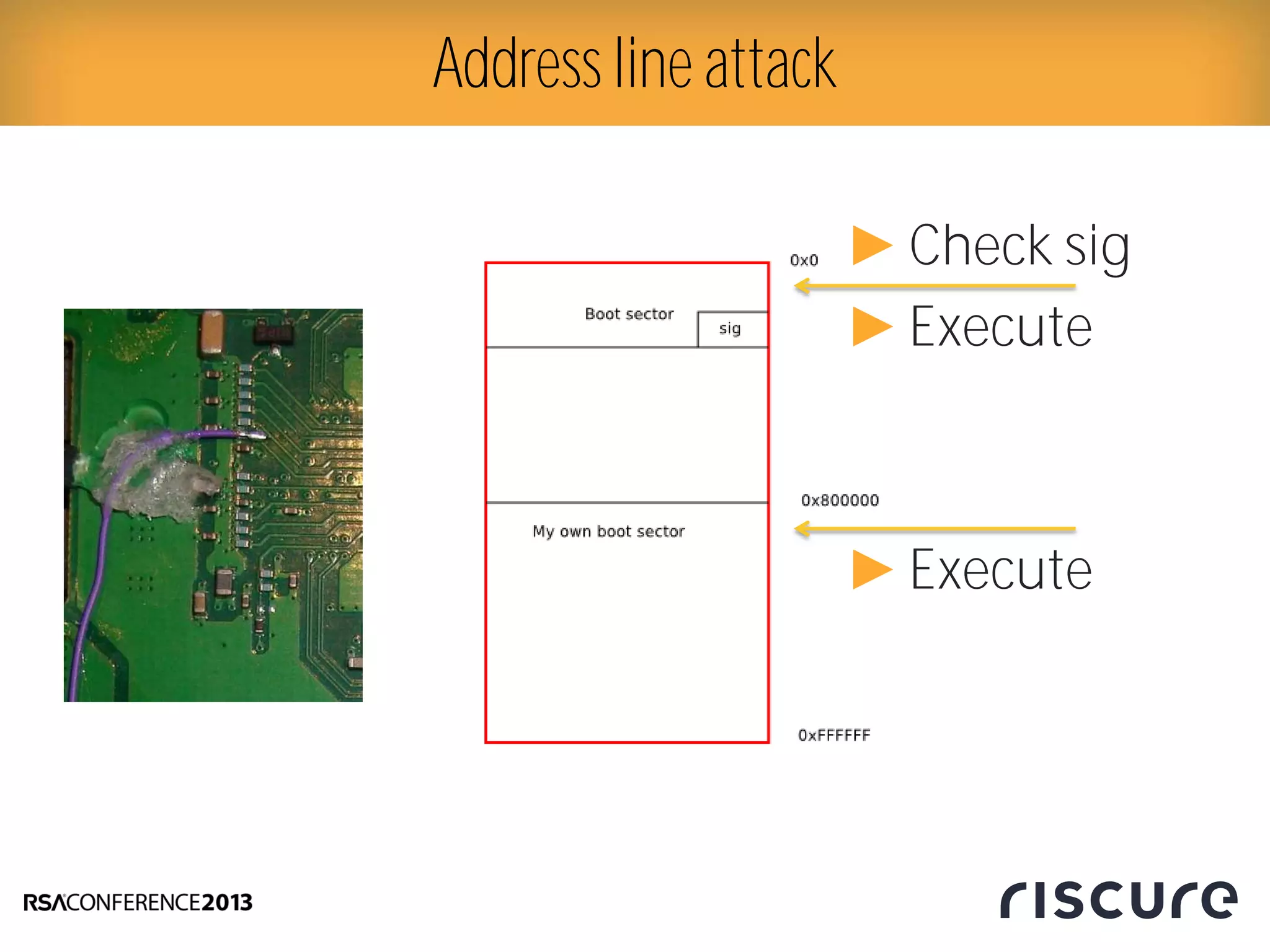
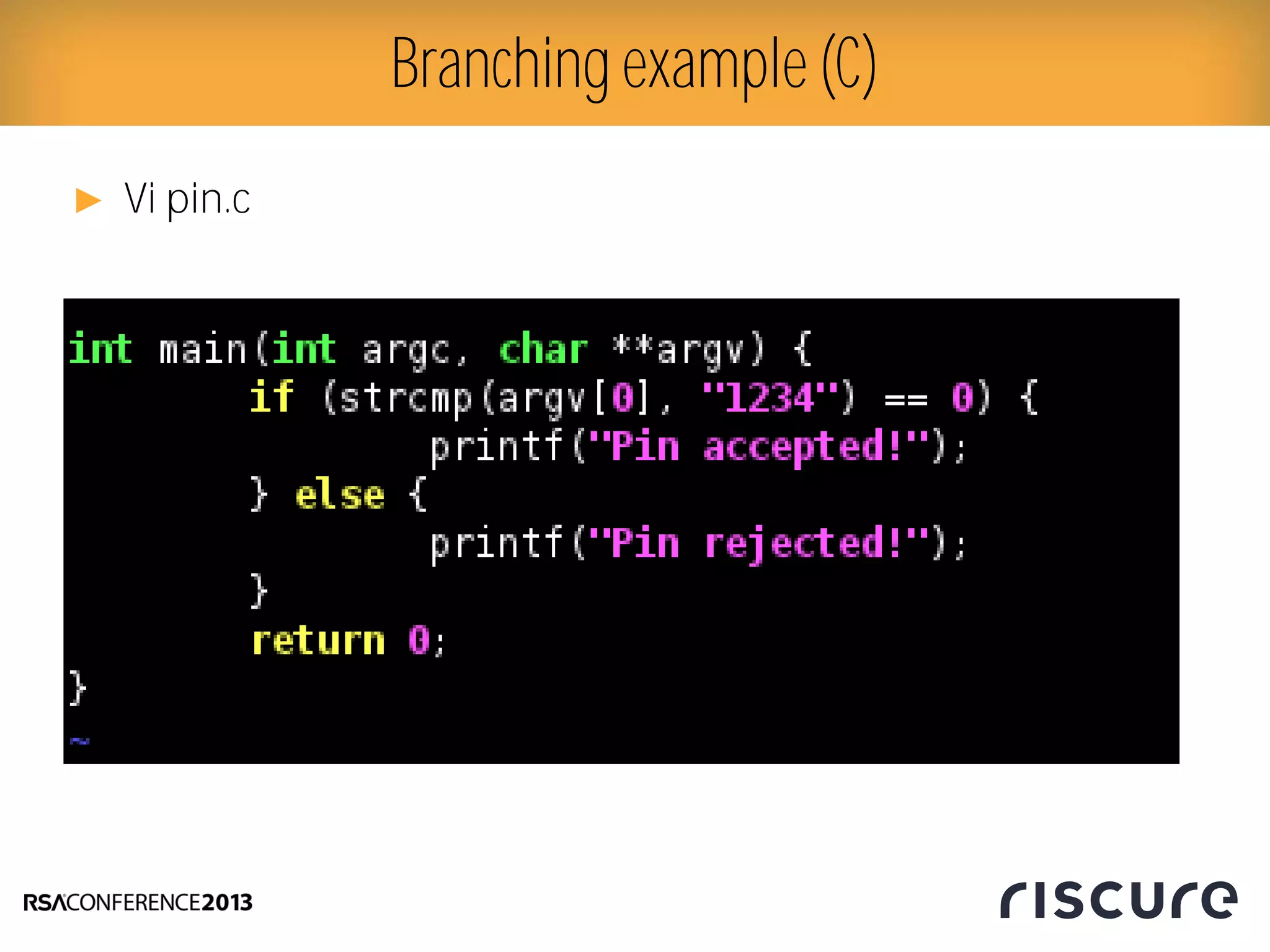
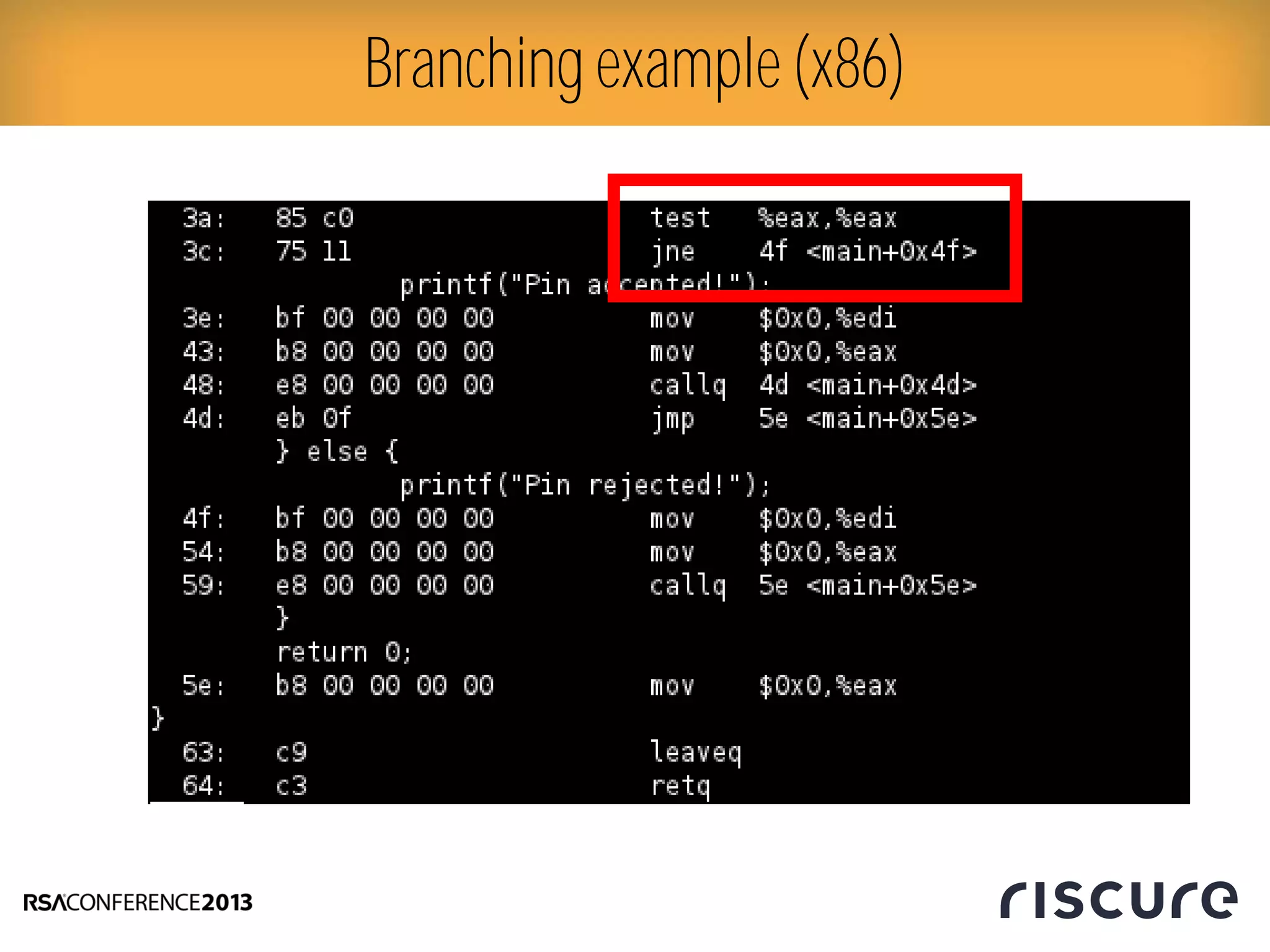
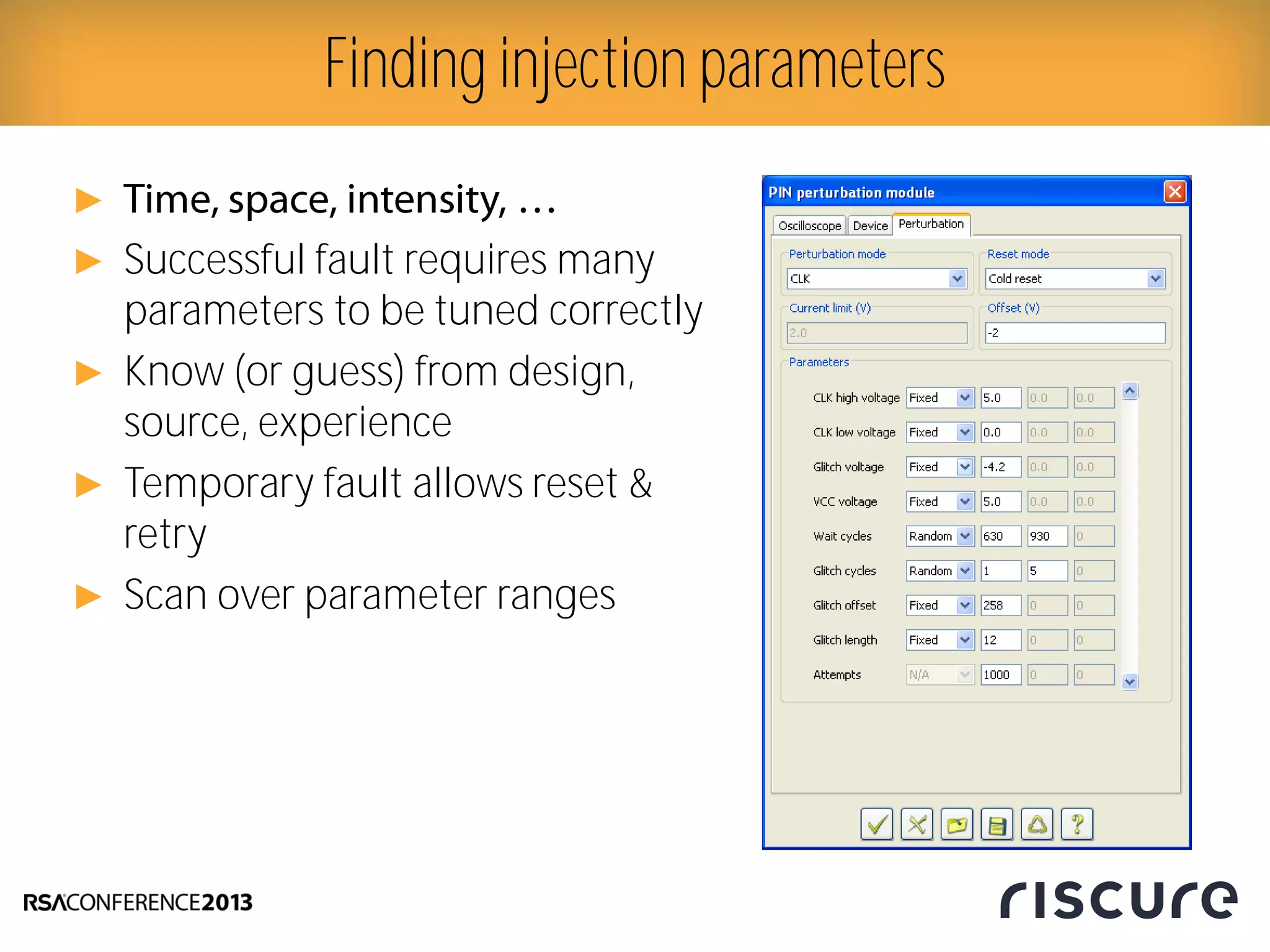
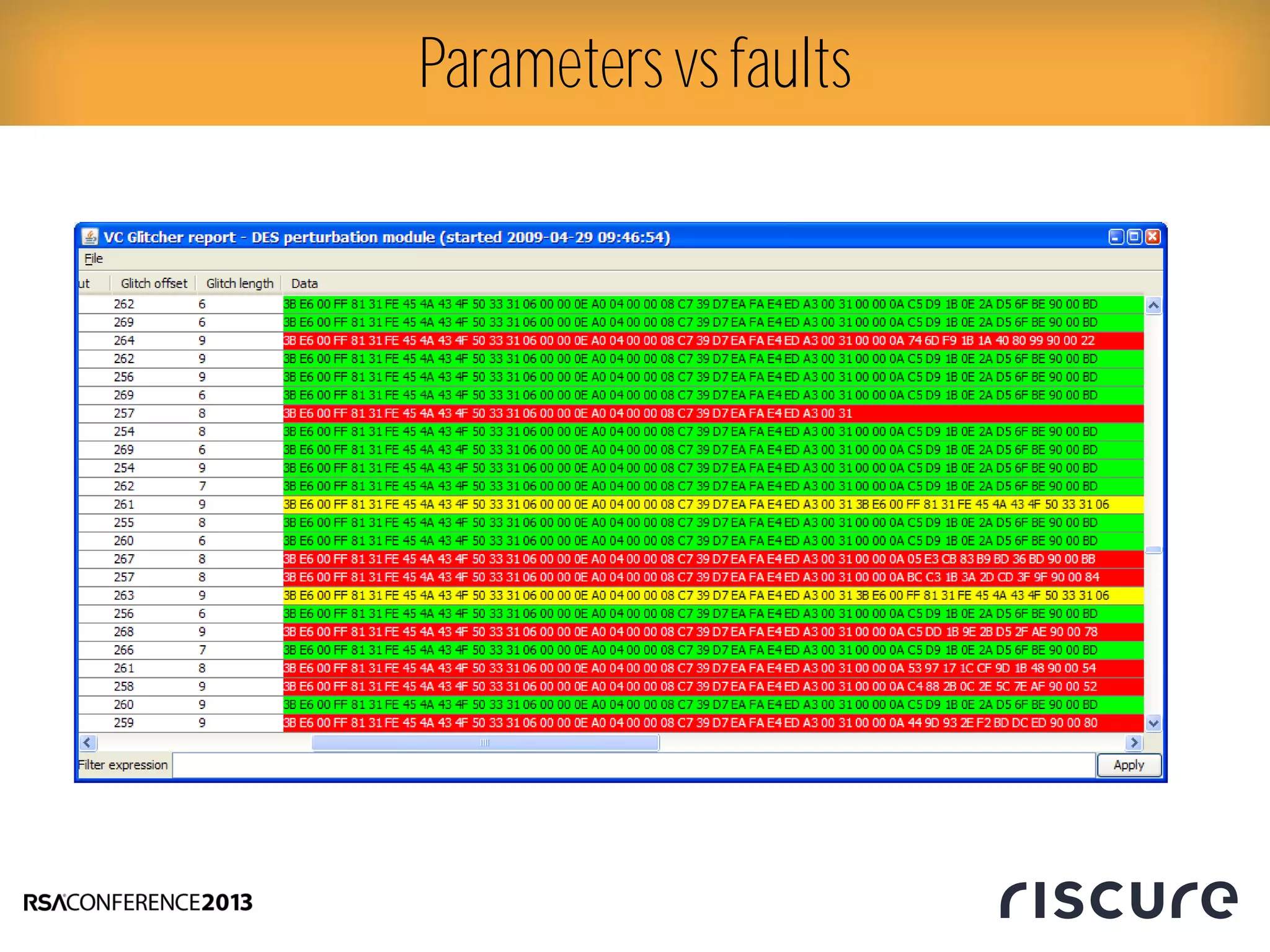
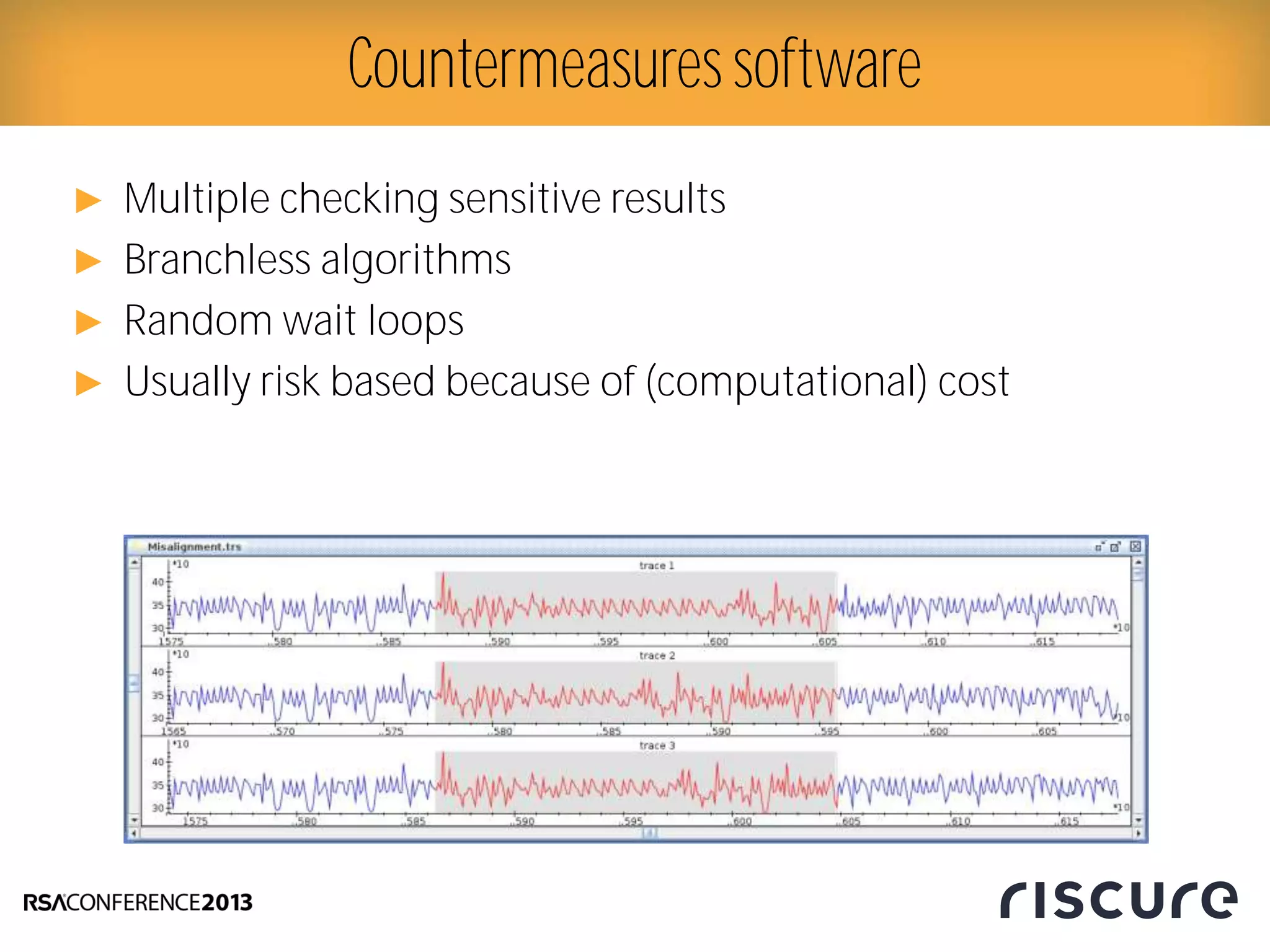
This document discusses fault injection attacks on secure boot implementations in embedded systems. It begins by explaining how secure boot works, using a hardware root of trust to verify that only authorized code is executed. It then introduces different methods of fault injection, such as voltage manipulation and electromagnetic interference, that can corrupt code verification and execution. Examples are given of how faults could bypass signature checks or modify execution. Countermeasures at both the software and hardware level are outlined to make systems more robust against fault injection. The document concludes that while hardware roots of trust increase security, physical attacks still remain a threat, and both hardware and software countermeasures are needed to protect against fault injection in secure embedded systems.