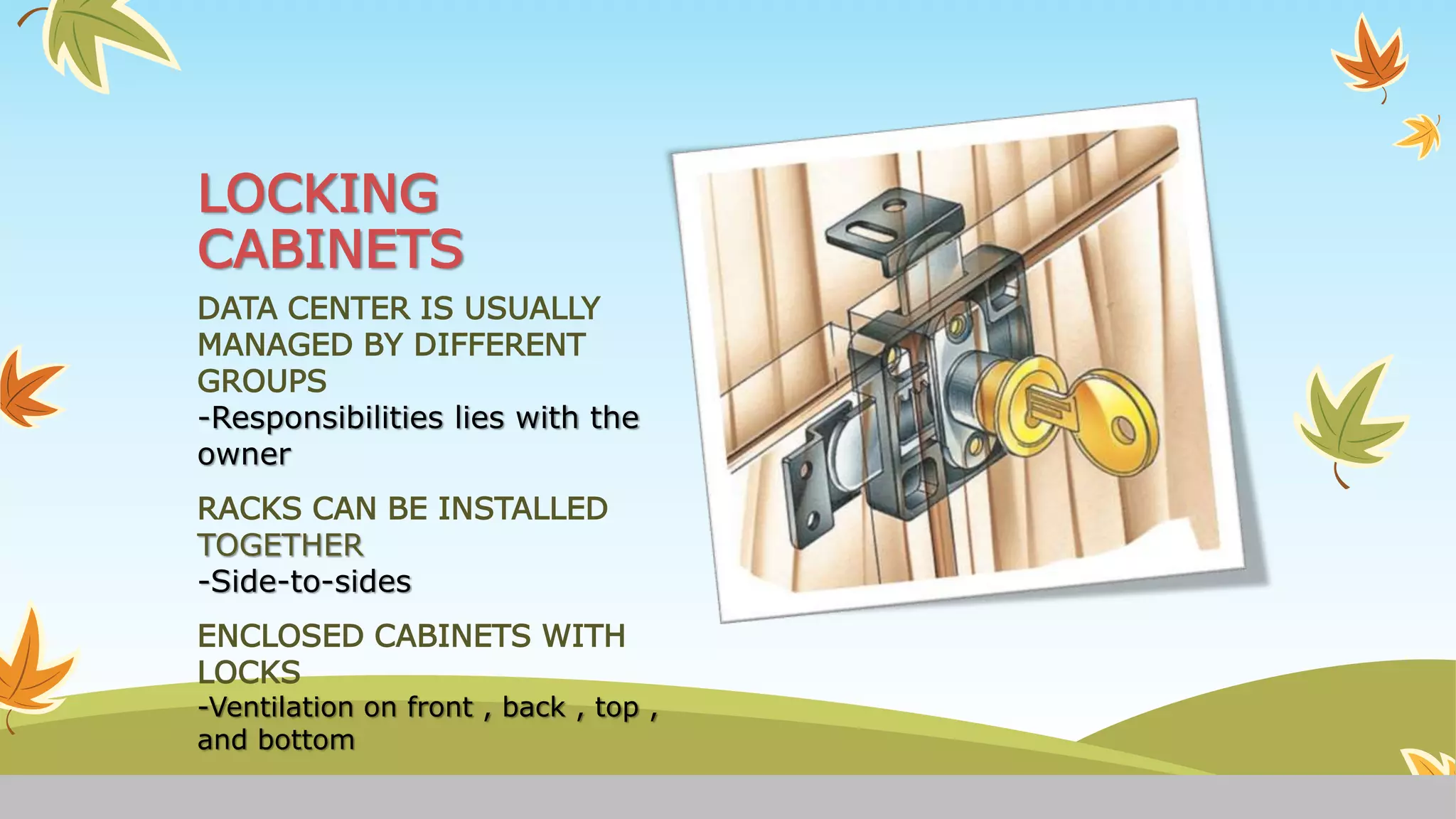
Hardware plays a key role in securing computer systems and physical assets. This includes cable locks to secure laptops and monitors, locking cabinets for servers and networking equipment, and hardware security modules that securely store and manage digital keys for authentication. Physical security measures like locking server rooms, securing vulnerable devices, and disabling removable media are also important to prevent theft and hacking of systems and data. As technology changes, secure hardware will take on an increasingly important role in security initiatives like trusted computing.