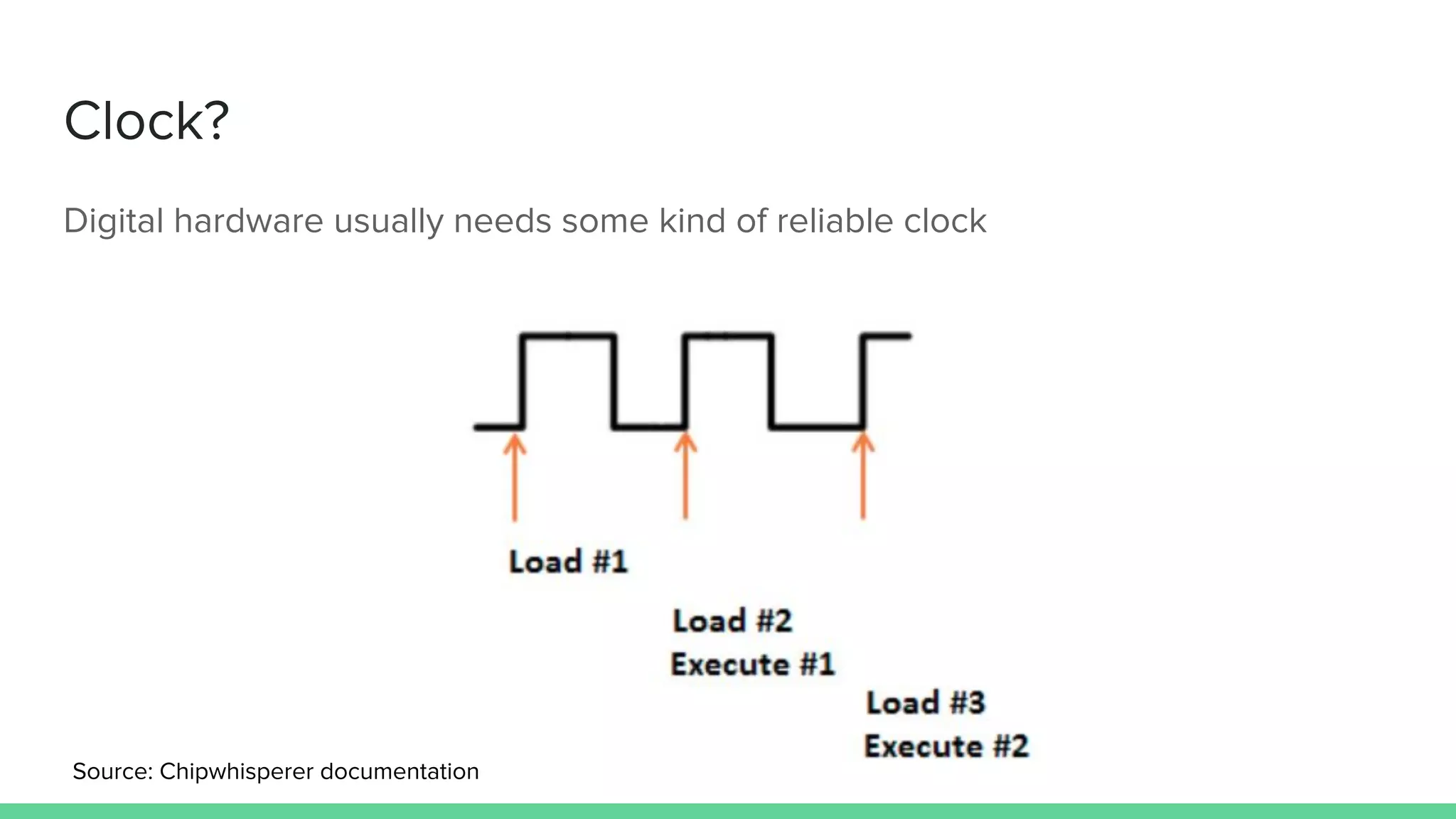
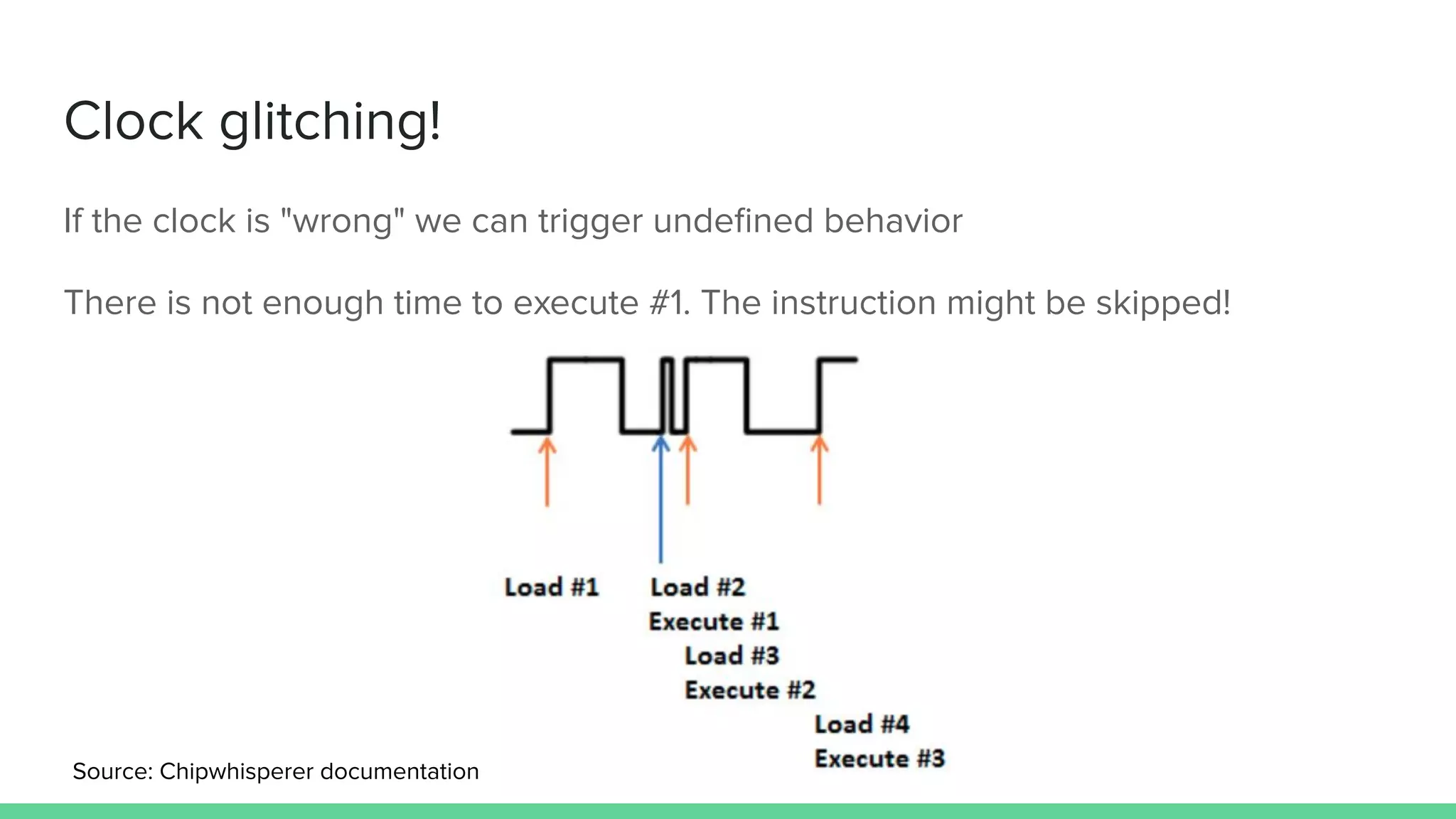
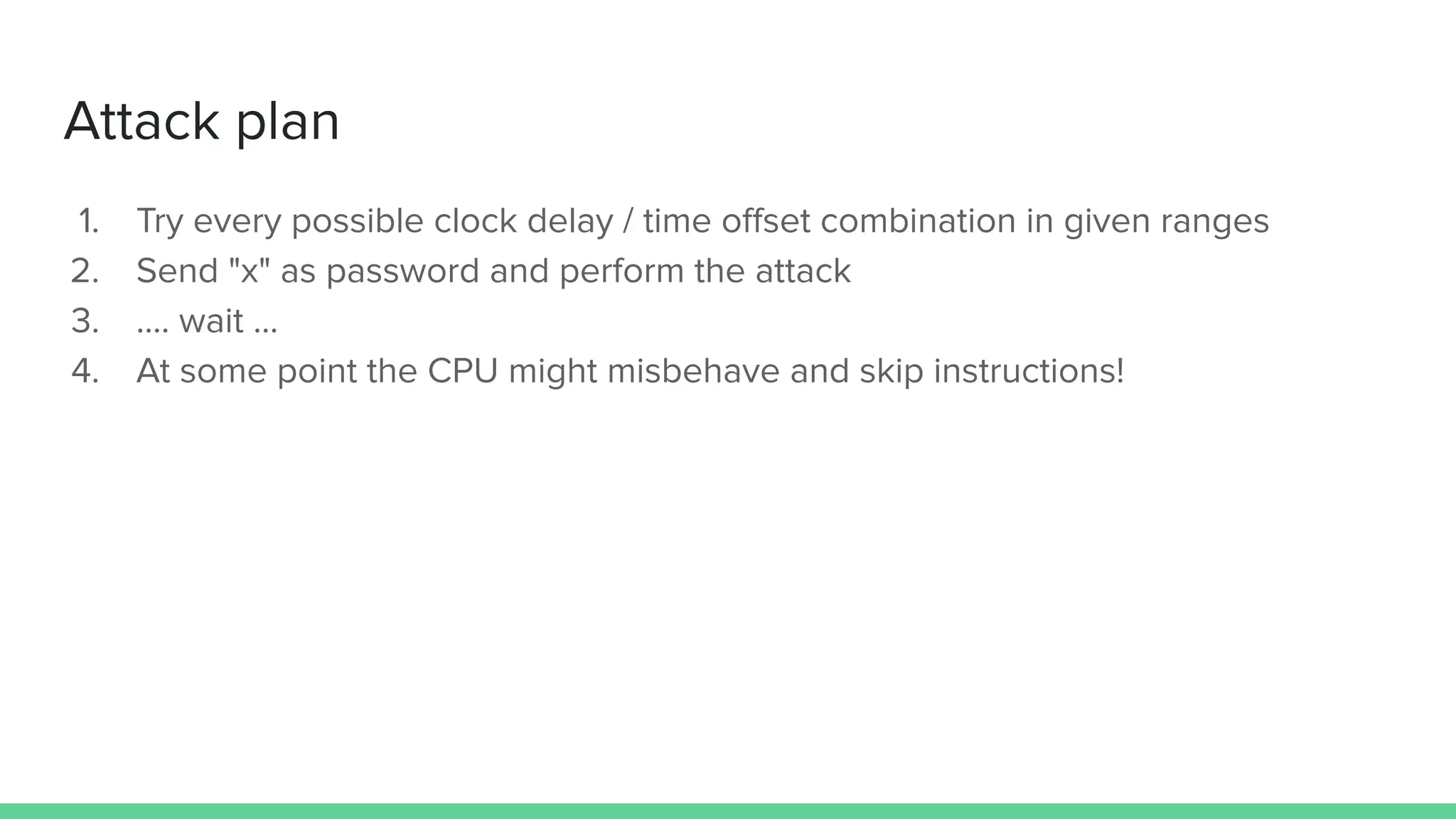
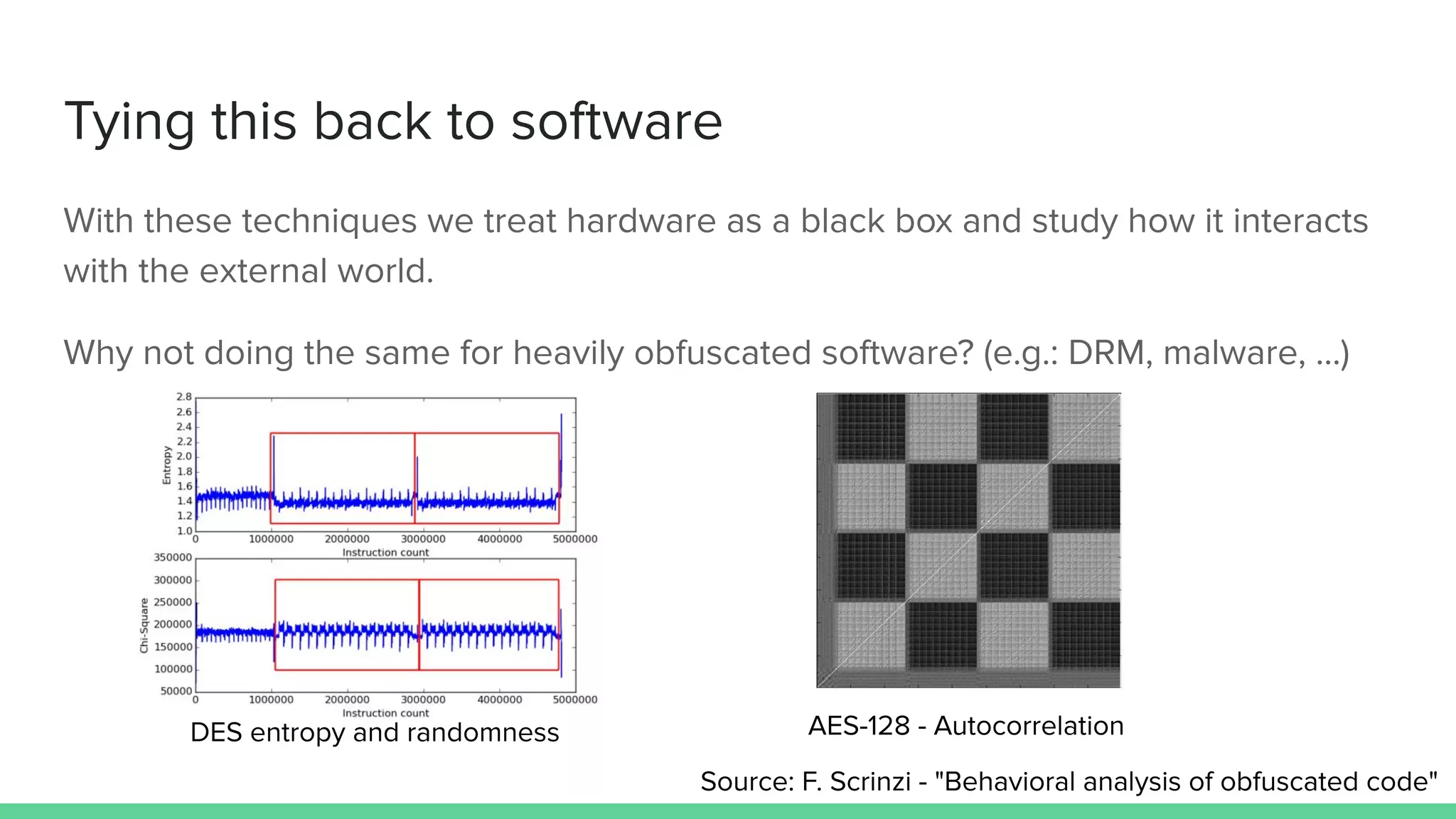
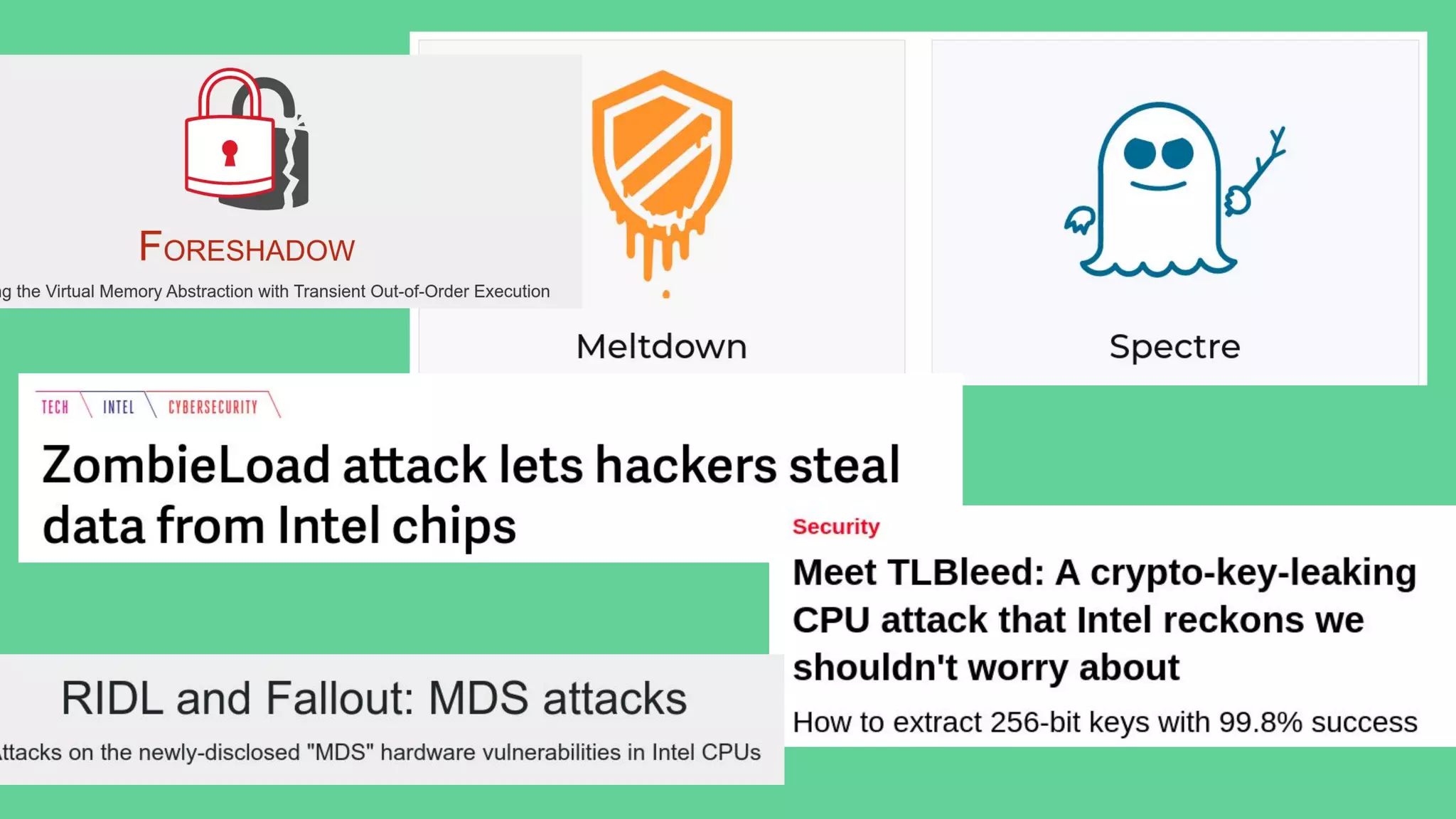
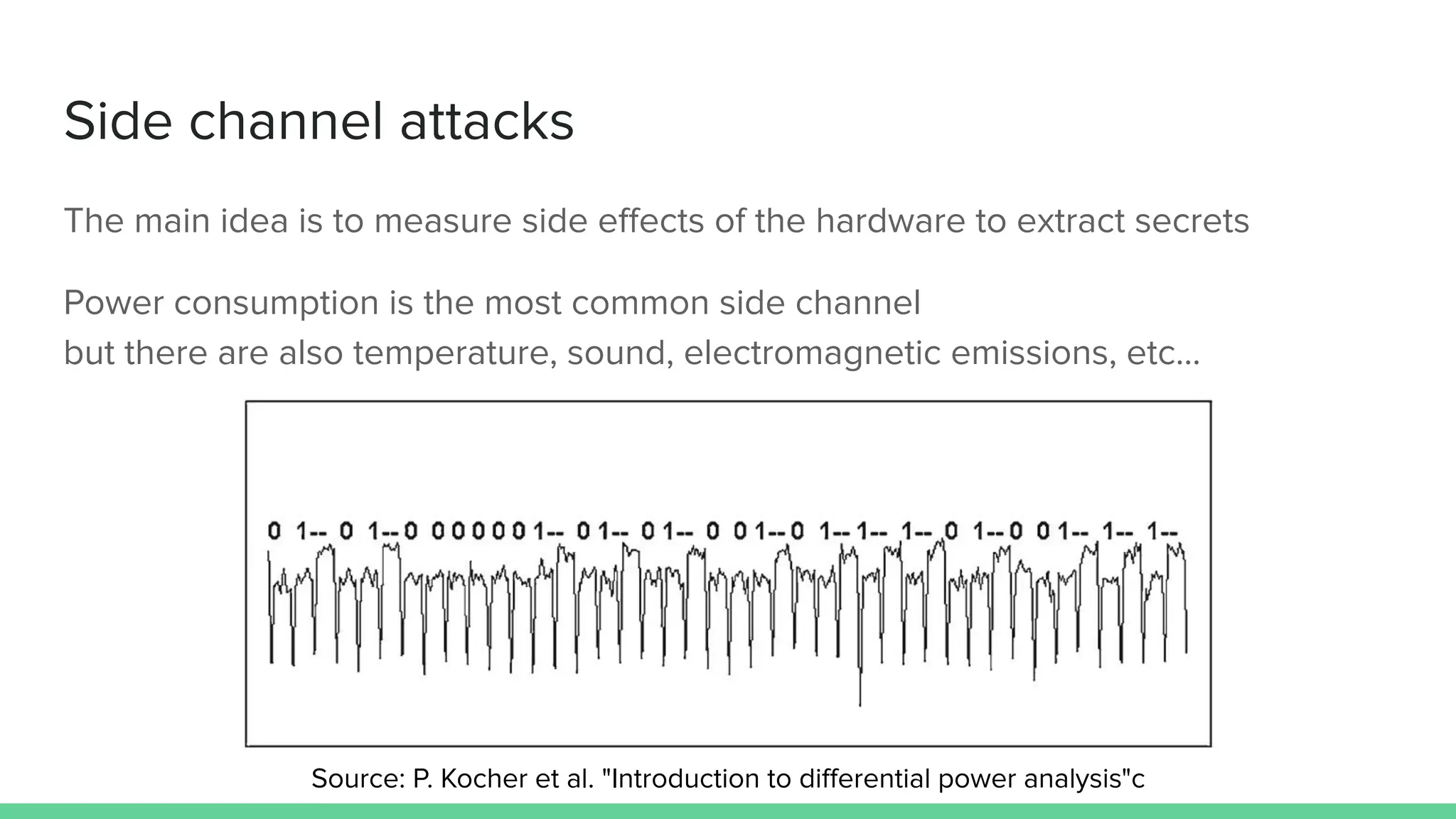
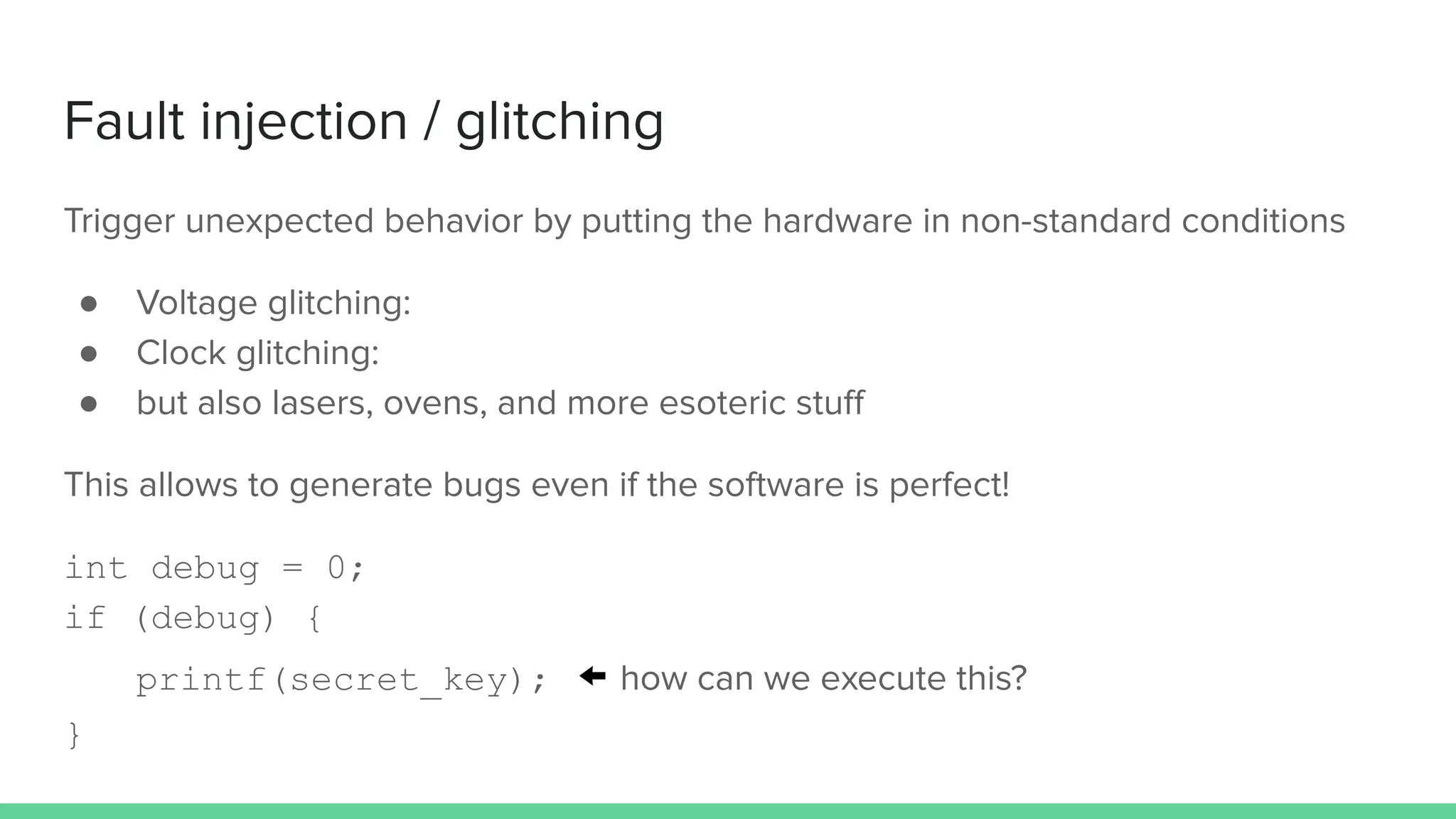
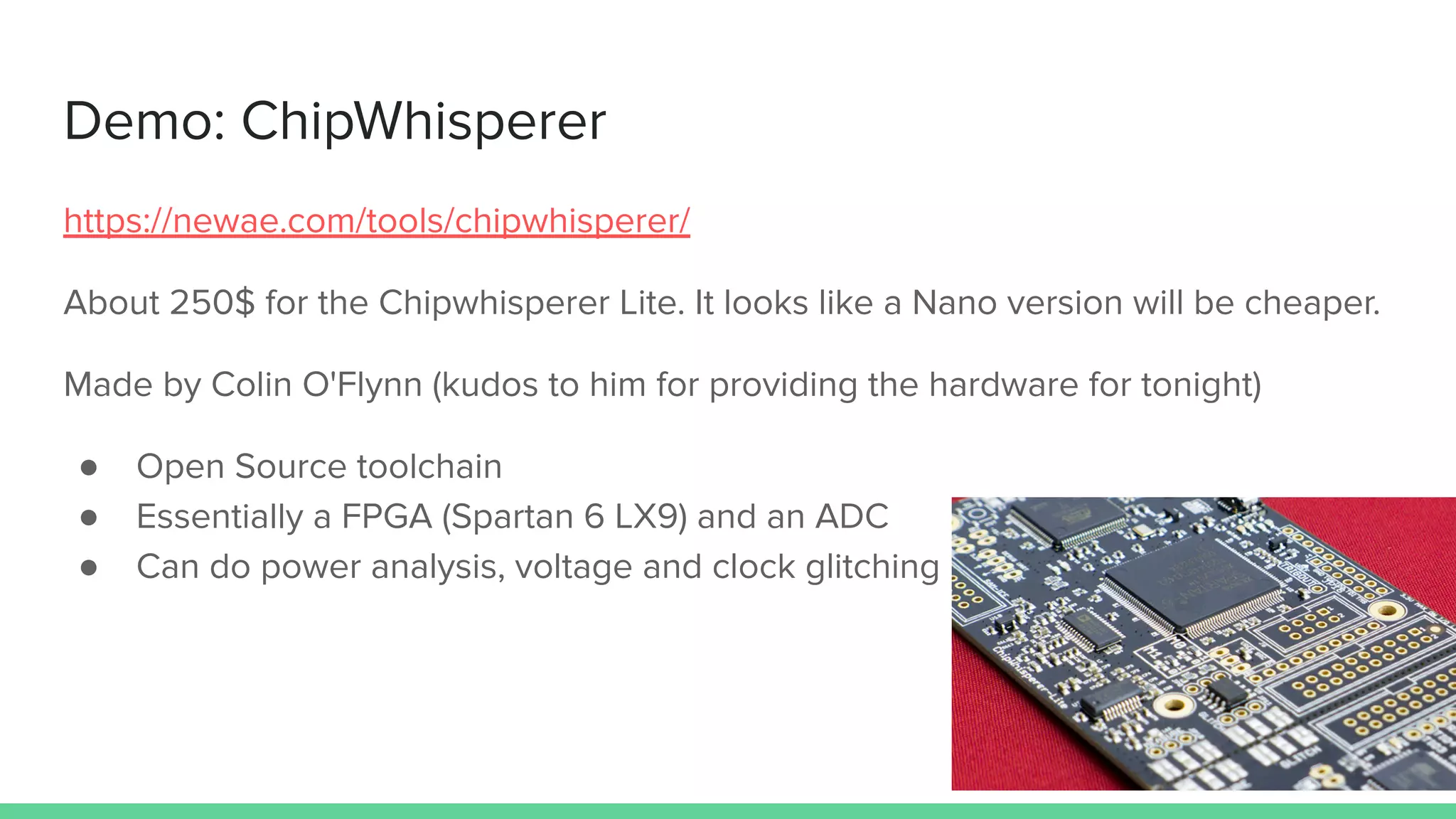
The document discusses the importance of hardware security, explaining how hardware vulnerabilities can be exploited through various attack methods such as side channel attacks and fault injection. It emphasizes that these attacks are not just theoretical and can be conducted with affordable equipment, showcasing tools like the Chipwhisperer. The talk concludes by encouraging a shift in perspective on hardware security and highlights the need for effective countermeasures against potential threats.









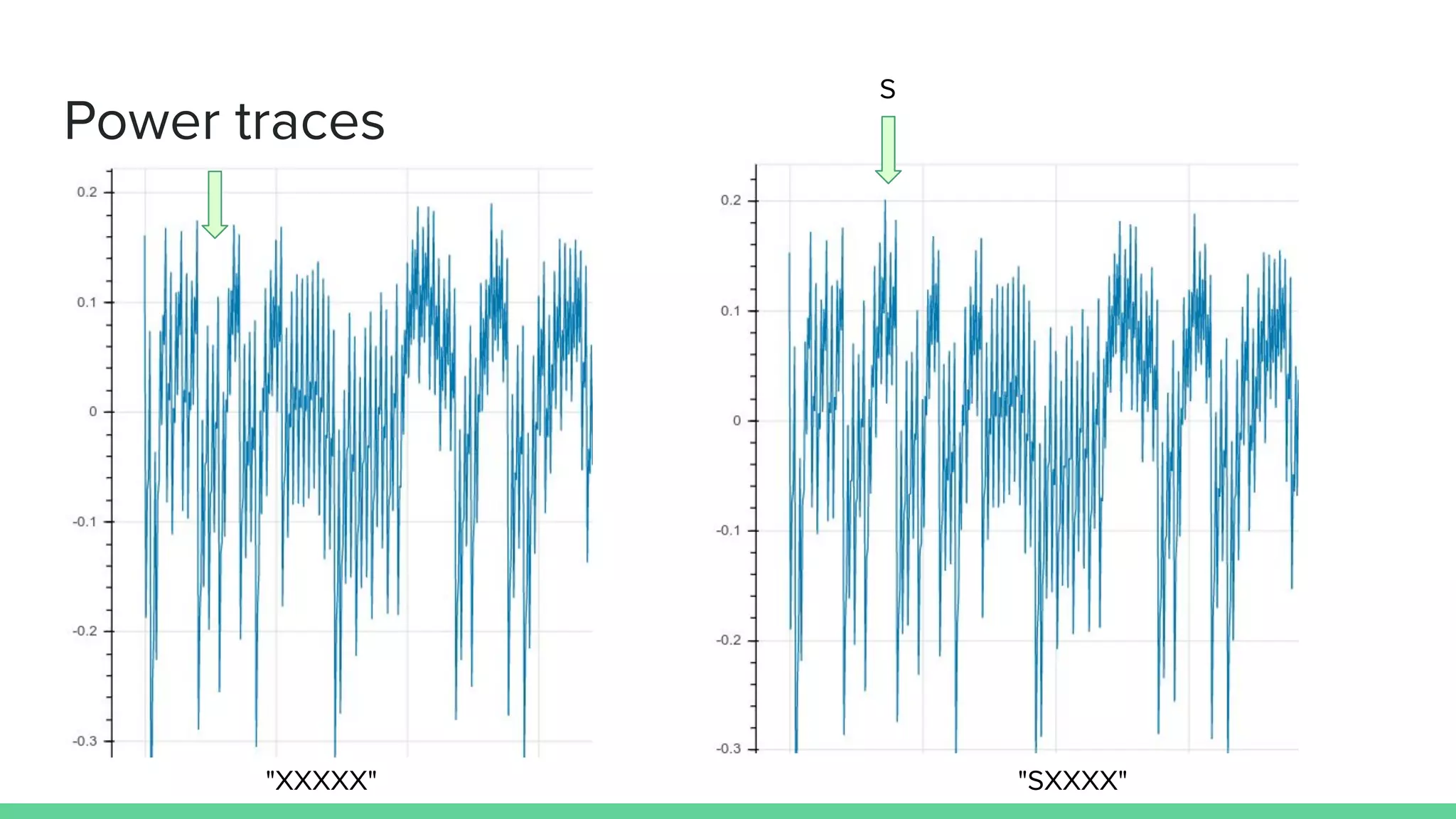
![Demo 1: timing
uint8_t passbad = 0;
for (uint8_t i = 0; i < sizeof(correct_passwd); i++){
if (correct_passwd[i] != passwd[i]){
passbad = 1;
break;
}
}
if (passbad) {
puts("PASSWORD FAILn");
} else {
puts("Access granted, Welcome!n")
}](https://image.slidesharecdn.com/hardwaresecurity-specktech-october2019-191005135914/75/Exploring-Hardware-Security-16-2048.jpg)
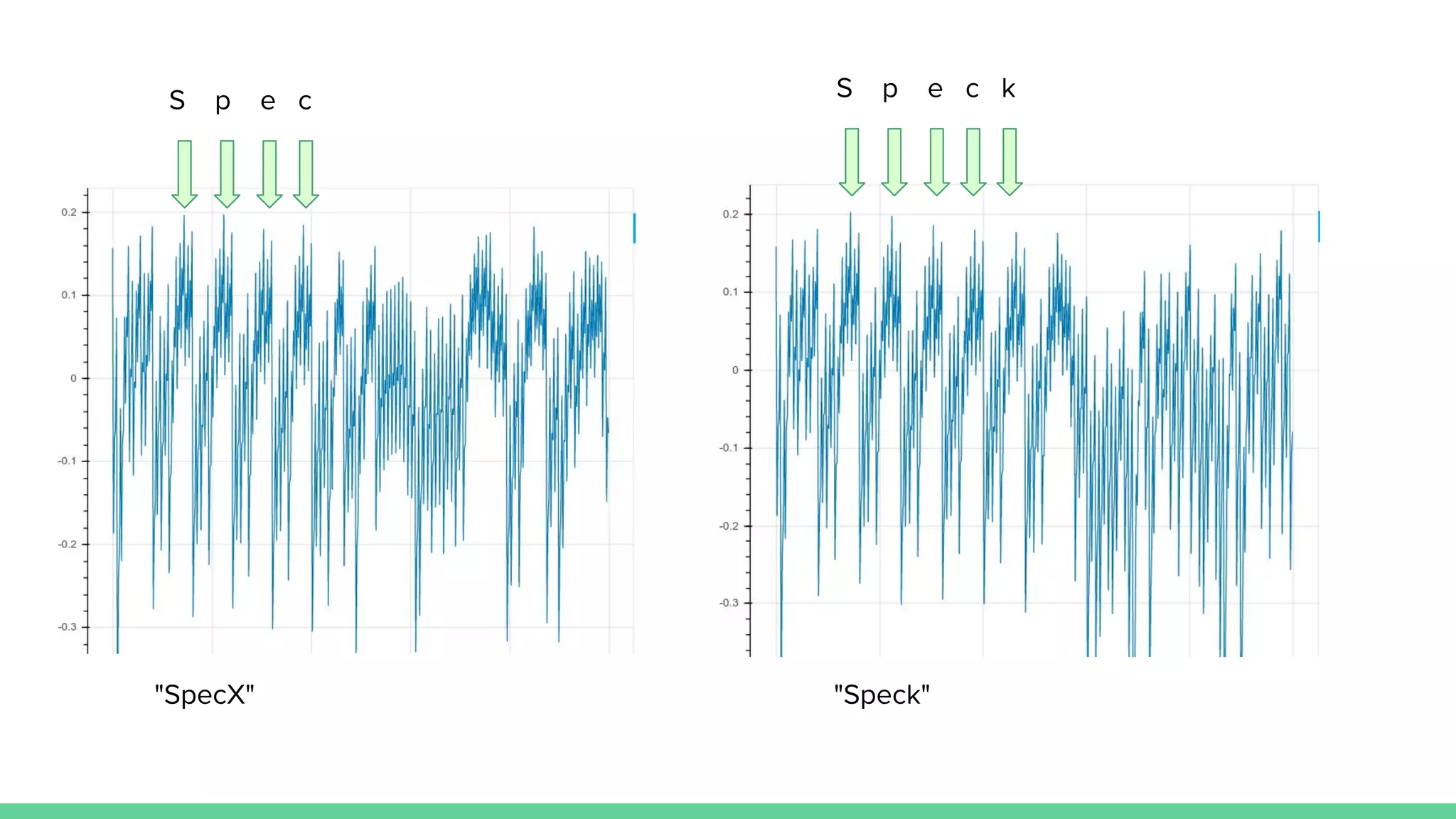
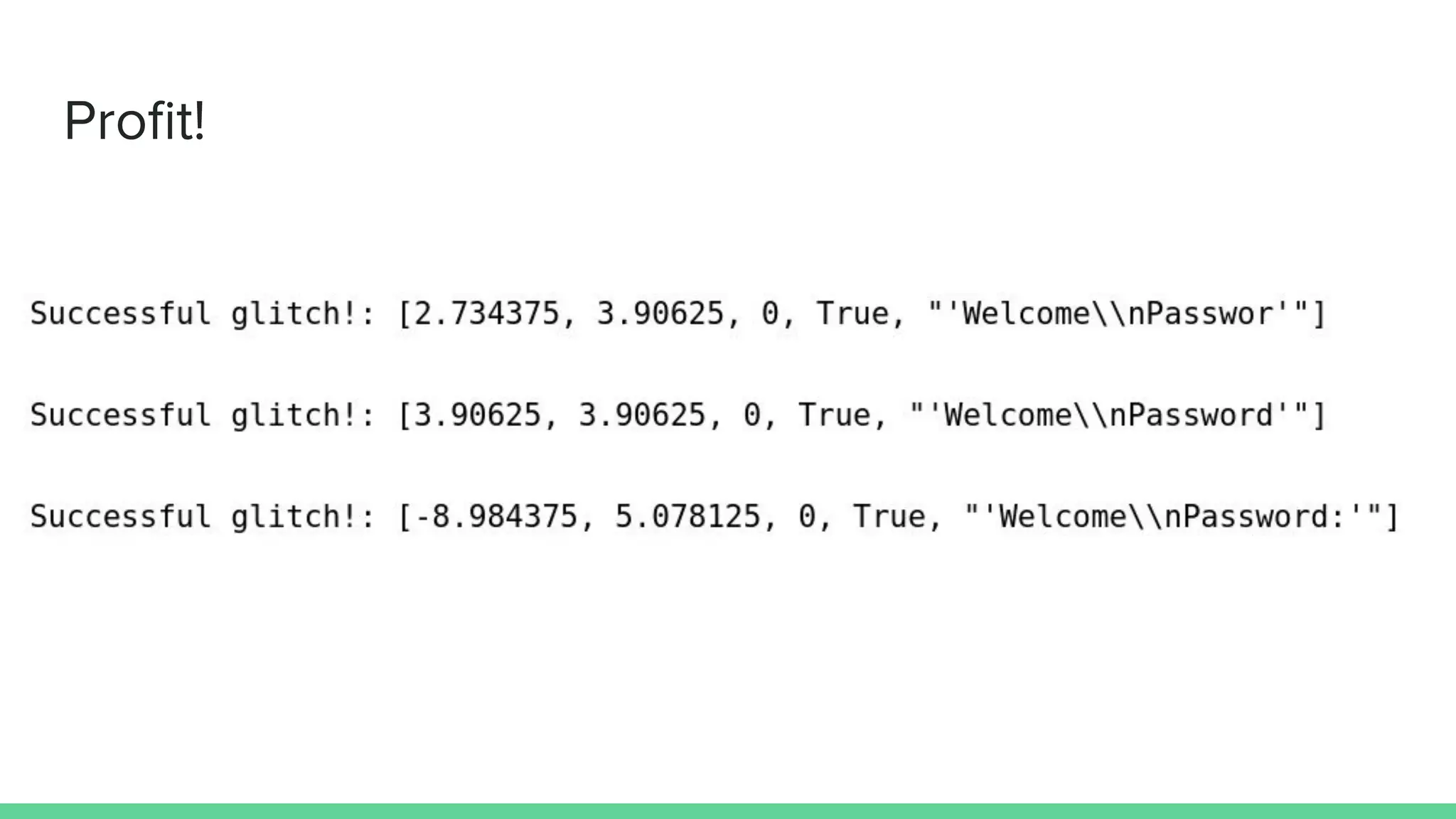
![Demo 2: Clock glitching
int passok = 1;
for (cnt = 0; cnt < 5; cnt++){
if (inp[cnt] != passwd[cnt]){
passok = 0;
}
}
if (!passok){
puts("Deniedn");
} else {
puts("Welcomen");
}](https://image.slidesharecdn.com/hardwaresecurity-specktech-october2019-191005135914/75/Exploring-Hardware-Security-20-2048.jpg)