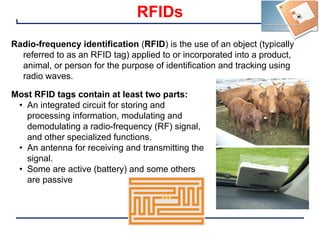
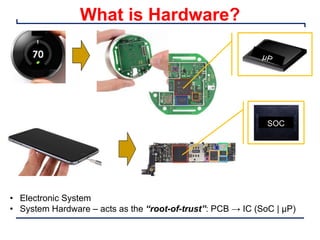
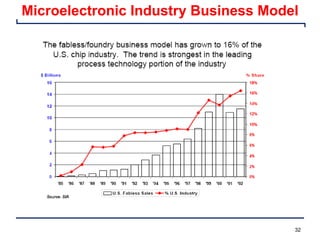
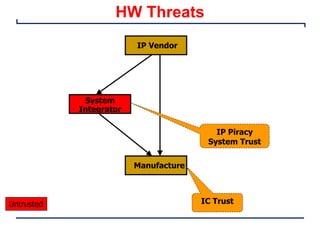
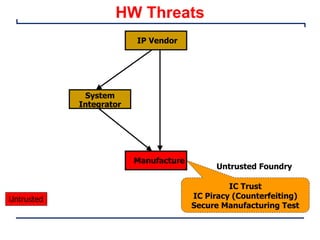
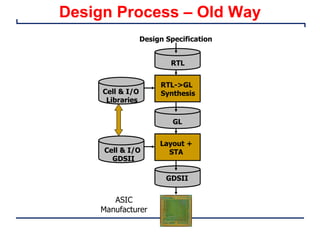
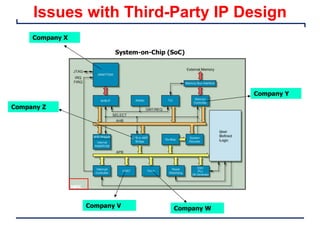
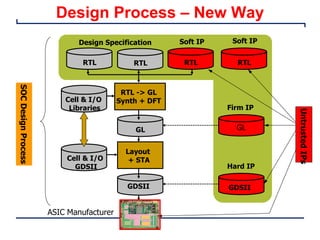
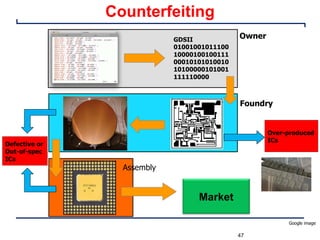
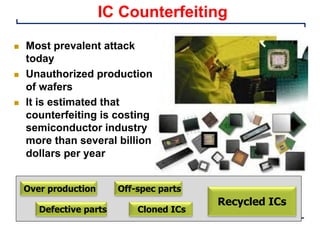
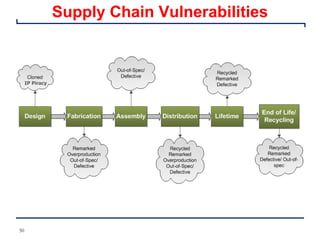
This document provides an introduction and overview of a university course on hardware security and trust. It discusses the course content which will cover topics like cryptographic hardware vulnerabilities, physical and side-channel attacks, physically unclonable functions, hardware trojans, and counterfeit detection. It outlines the course goals of integrating security into hardware design and protecting against various attacks. It also provides information about assignments, projects, textbooks, and software tools that will be used in the course.