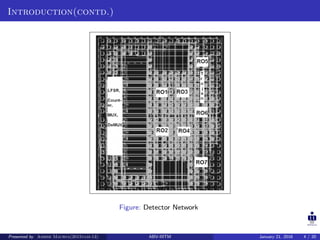
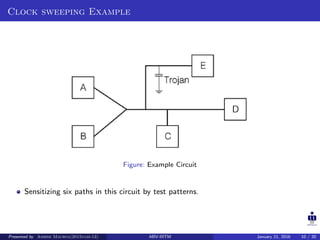
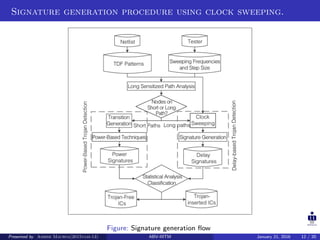
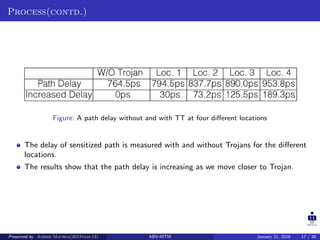
The document summarizes a presentation on detecting hardware Trojans using clock sweeping. It introduces the clock sweeping technique, which involves applying test patterns at different clock frequencies to obtain path delay information without additional hardware. Signatures are generated from the path delay data and compared to identify potential Trojans. The technique aims to detect Trojans through their impact on circuit delays, especially shorter paths. It is shown to be effective for critical and non-critical paths, and can detect Trojans without full activation. However, process variations and measurement noise still pose challenges.