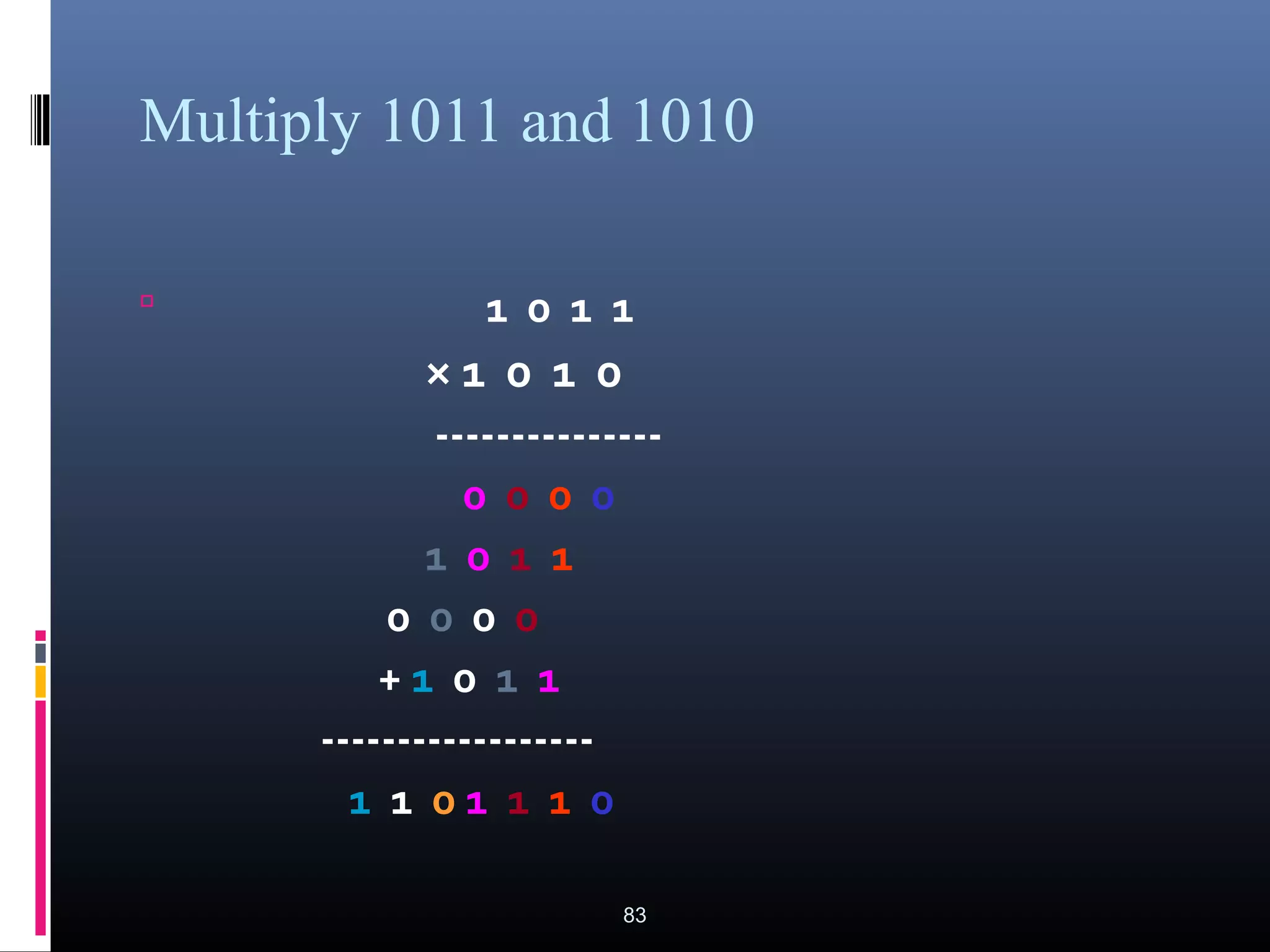
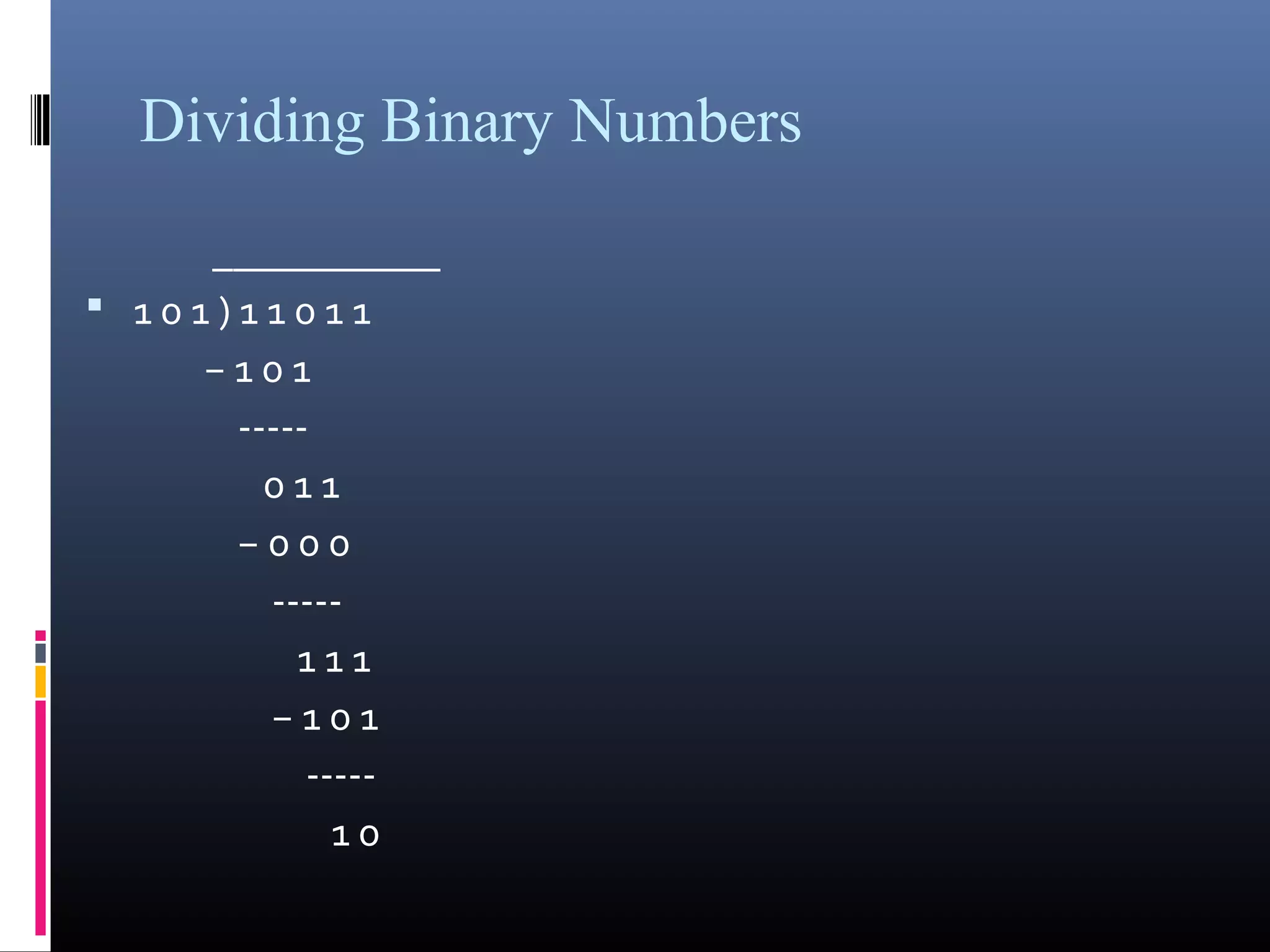
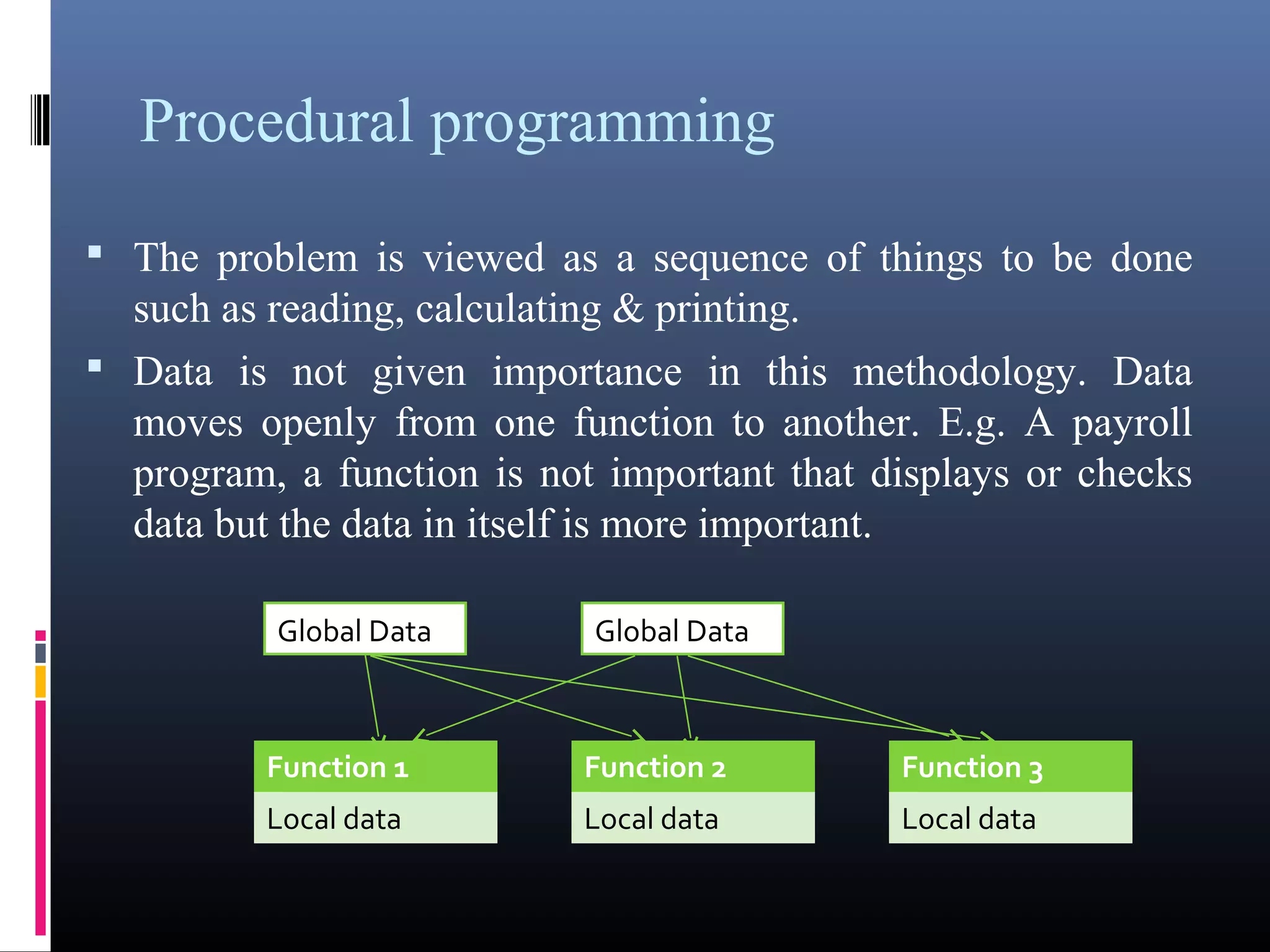
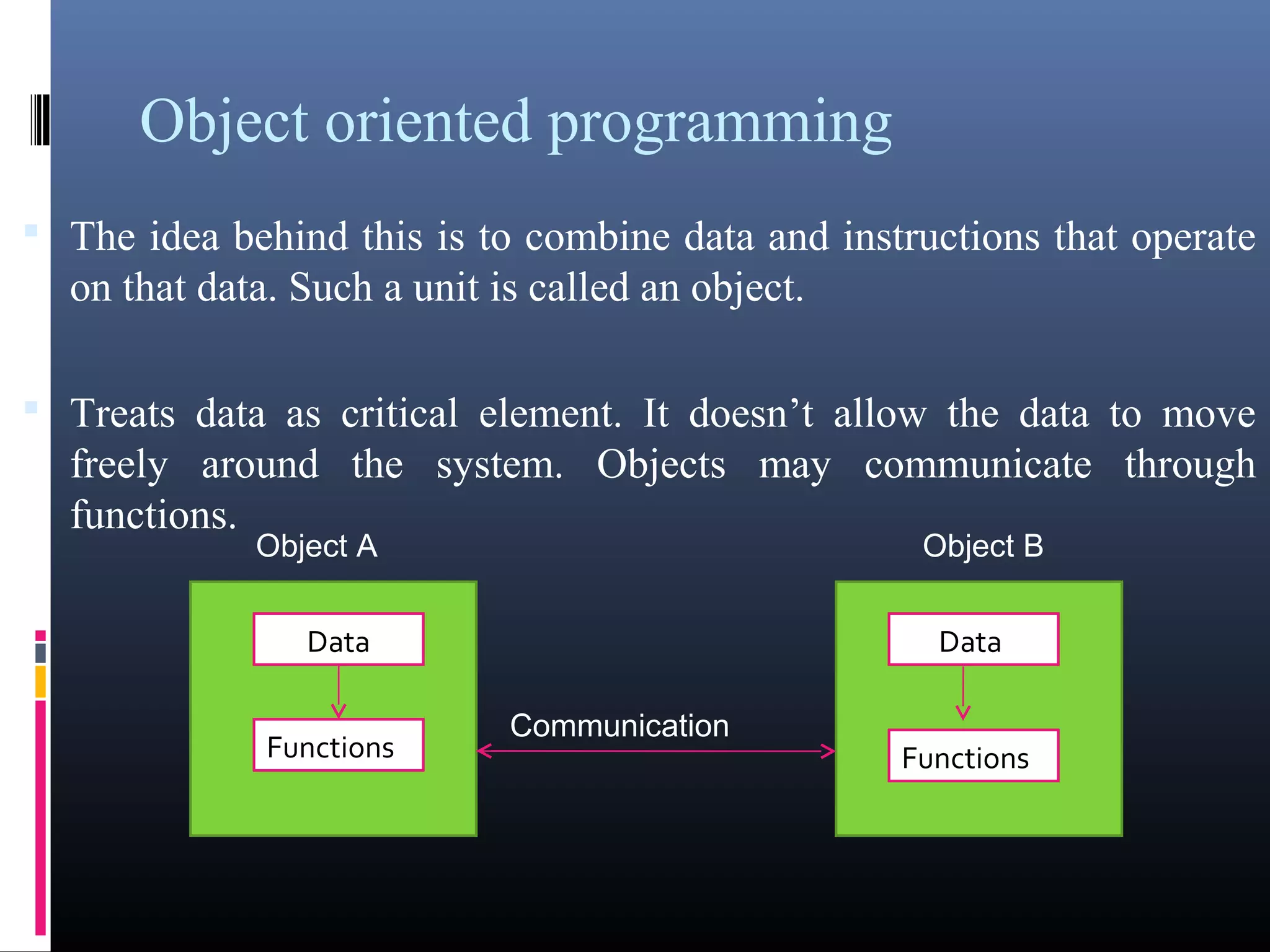
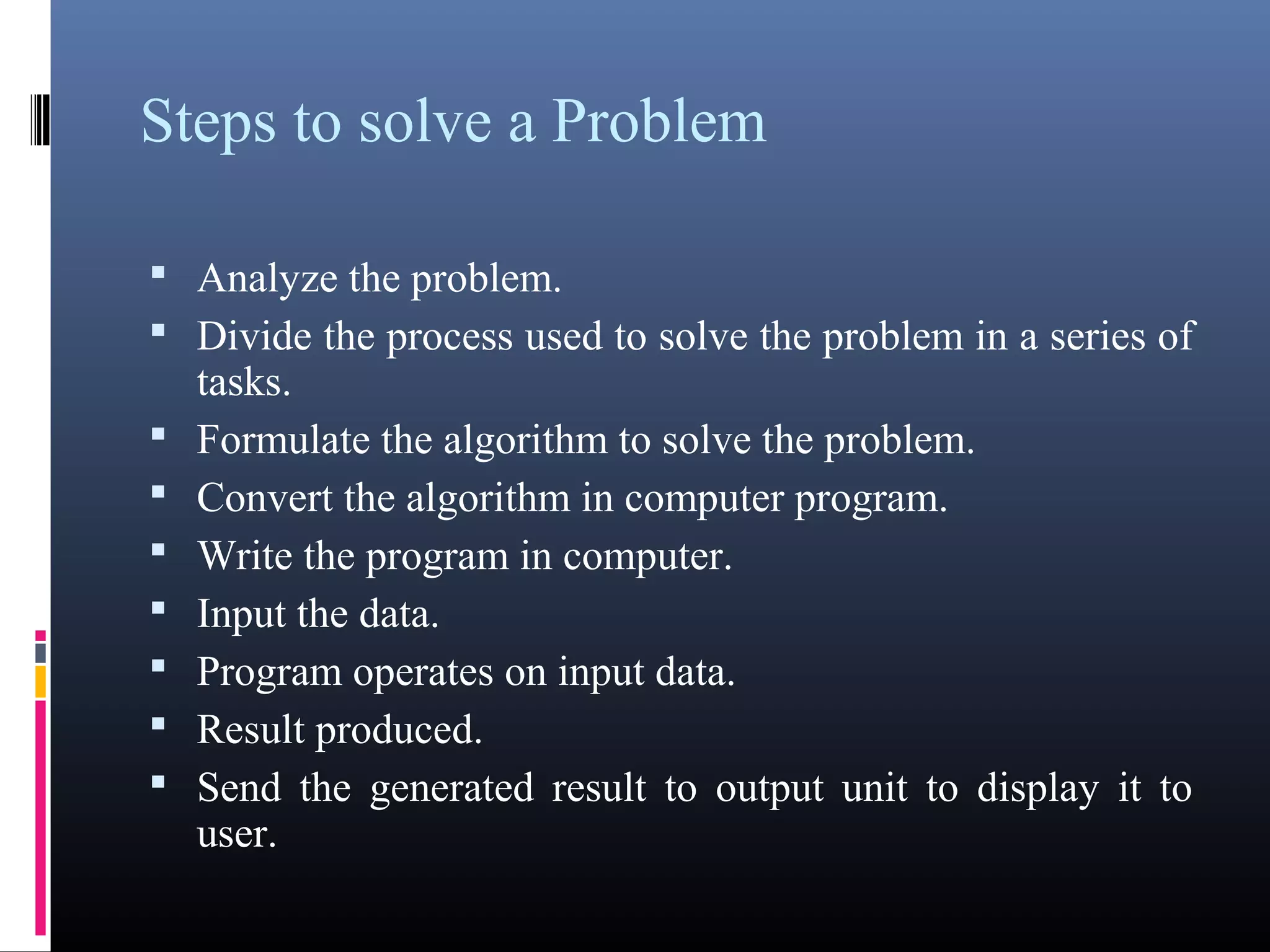
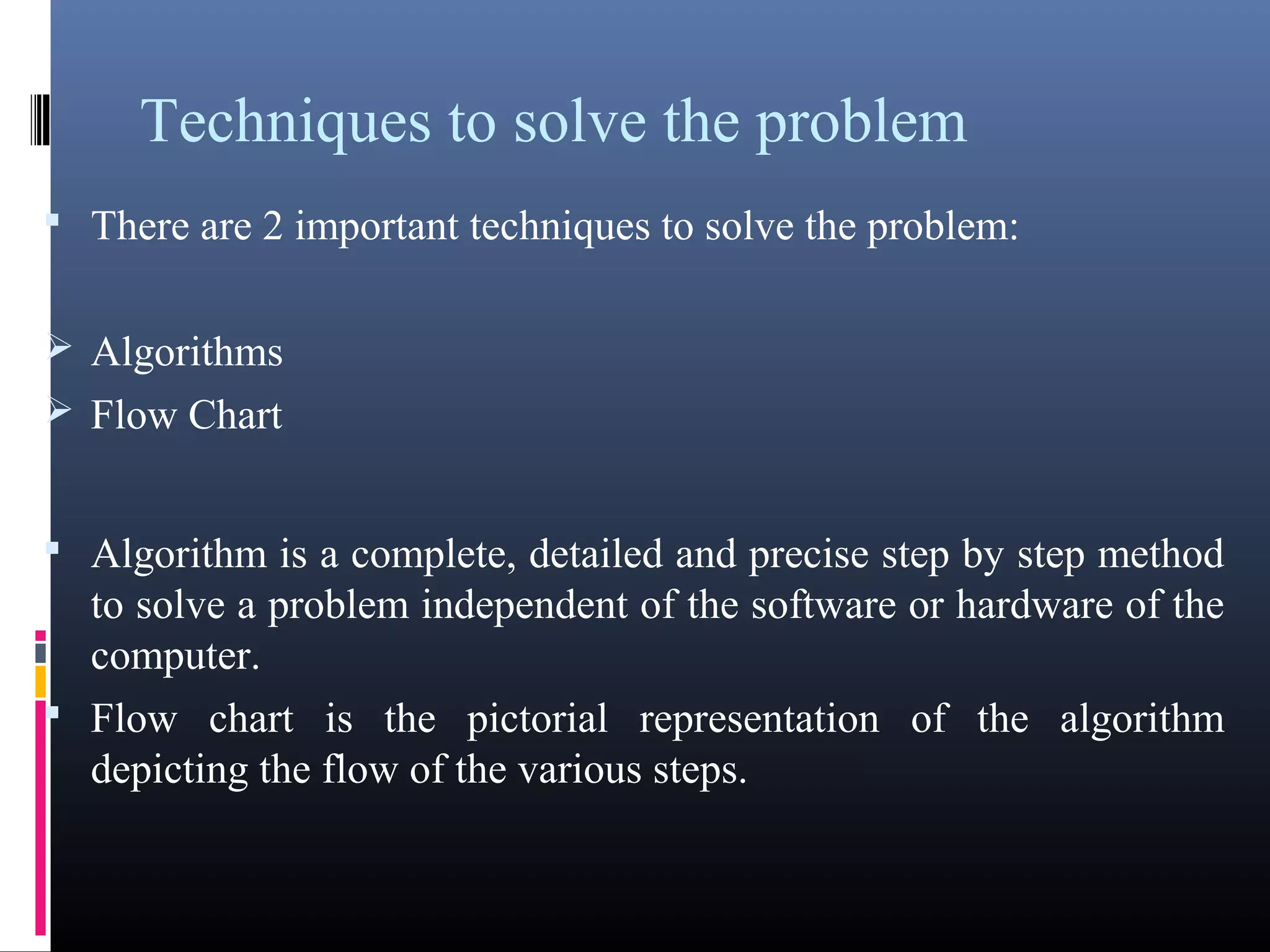
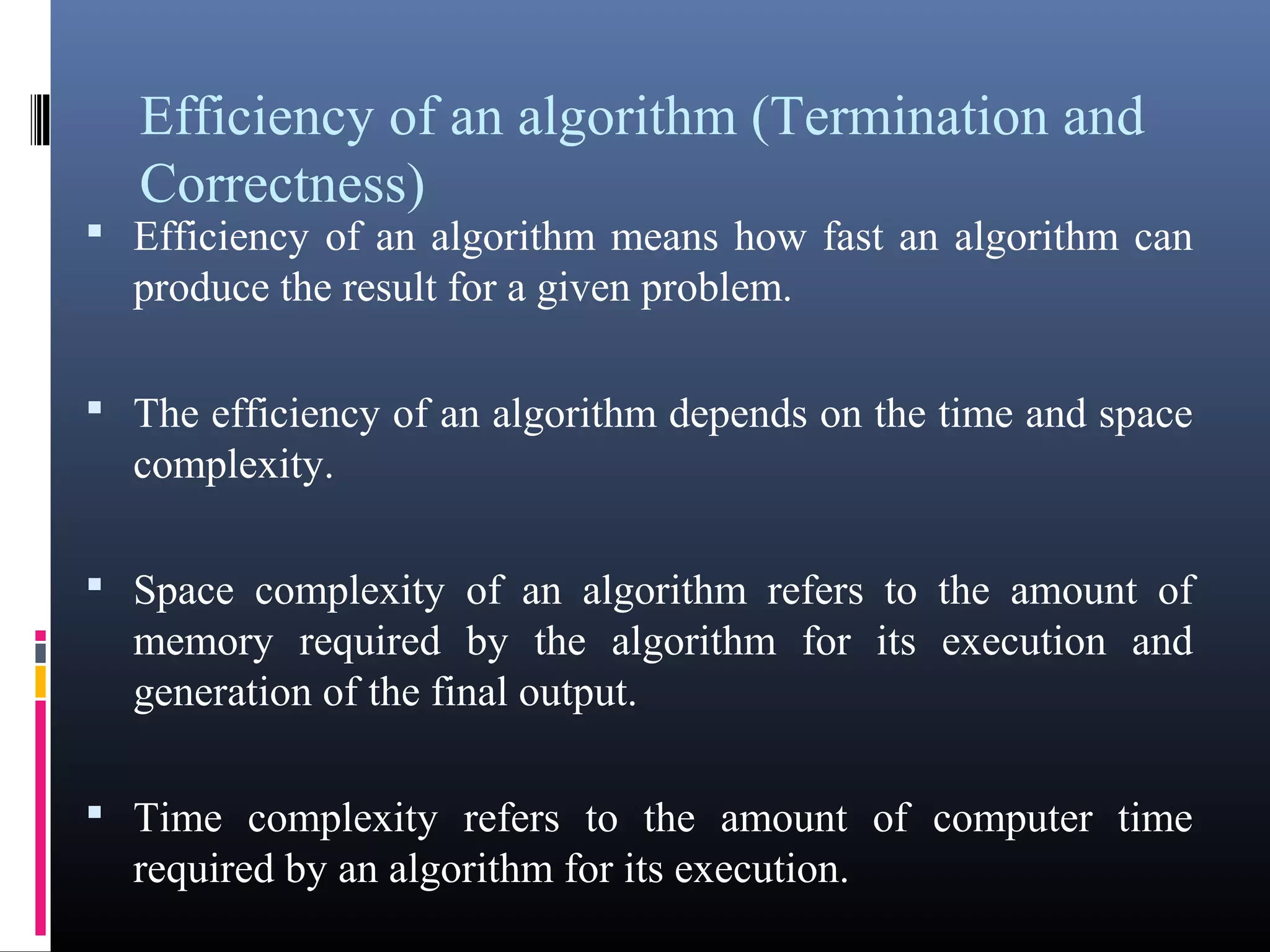
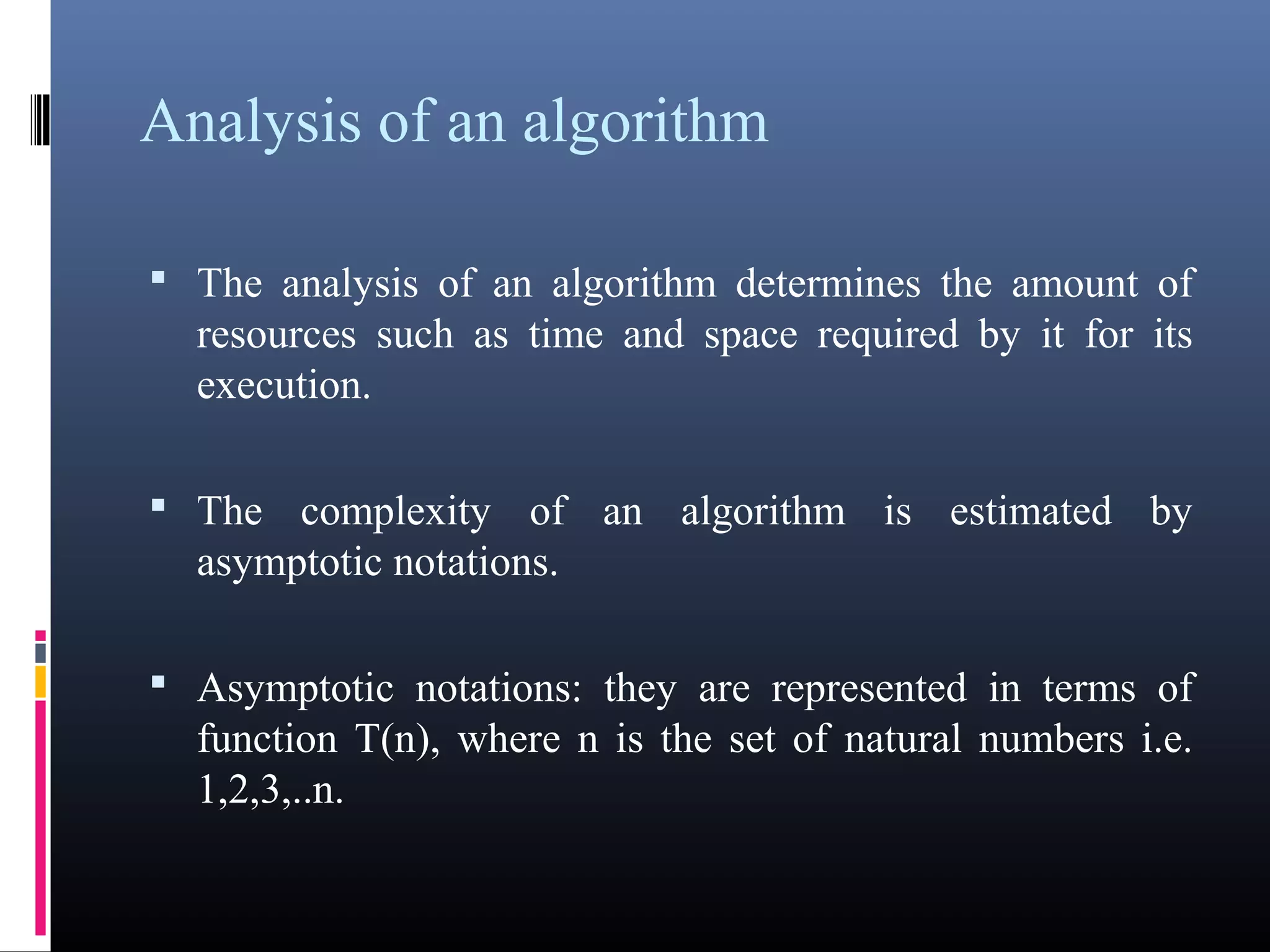
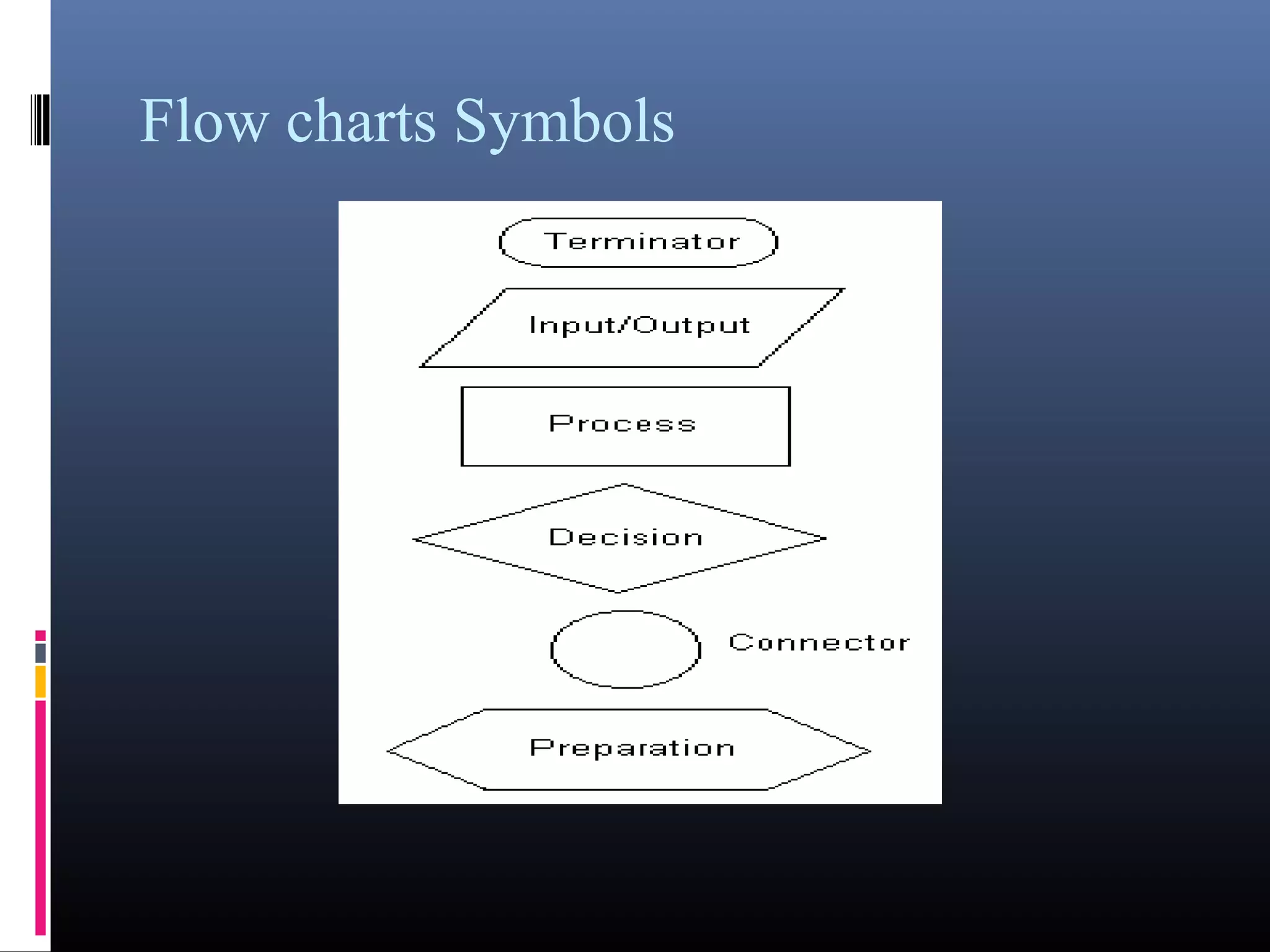
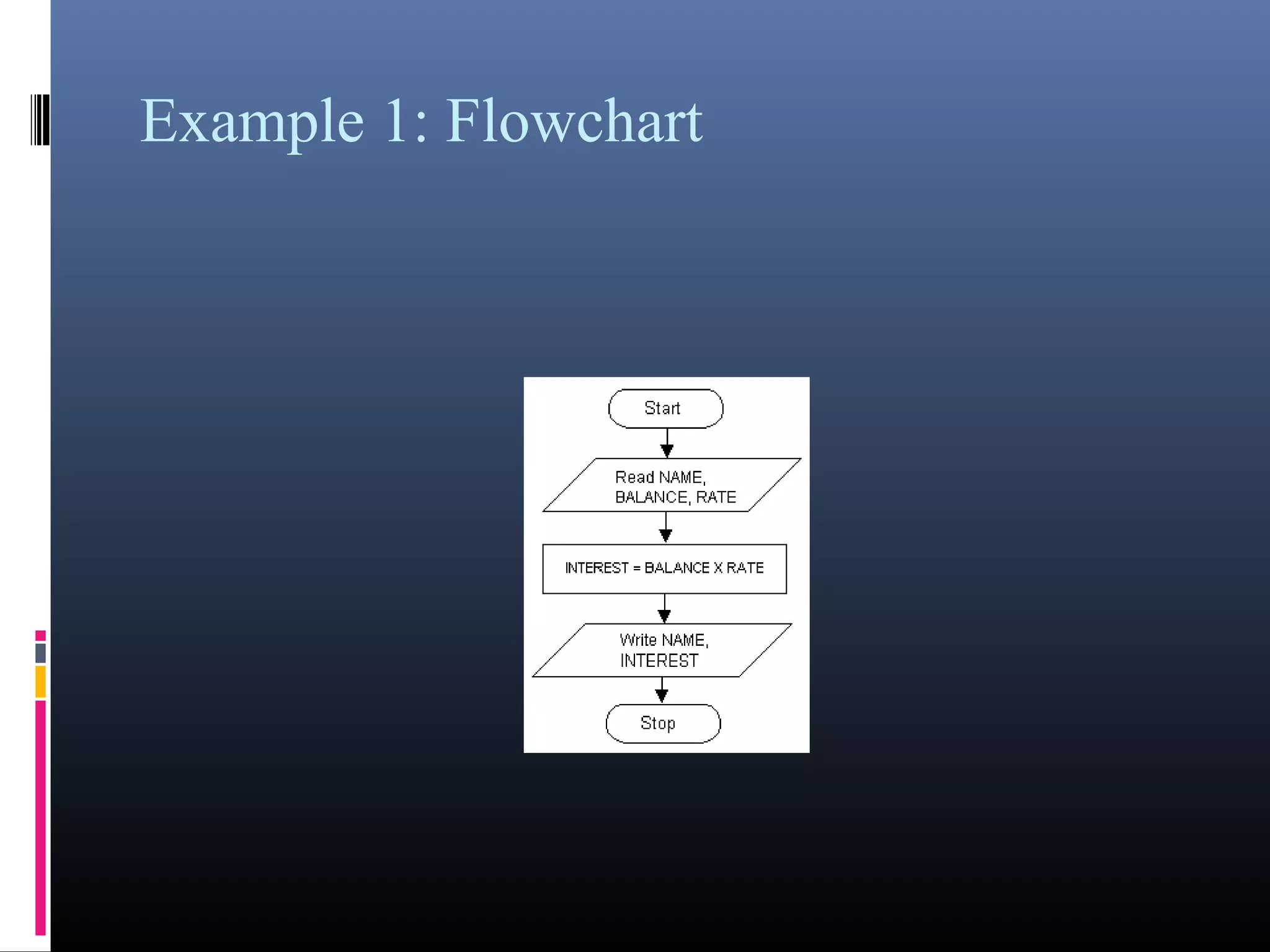
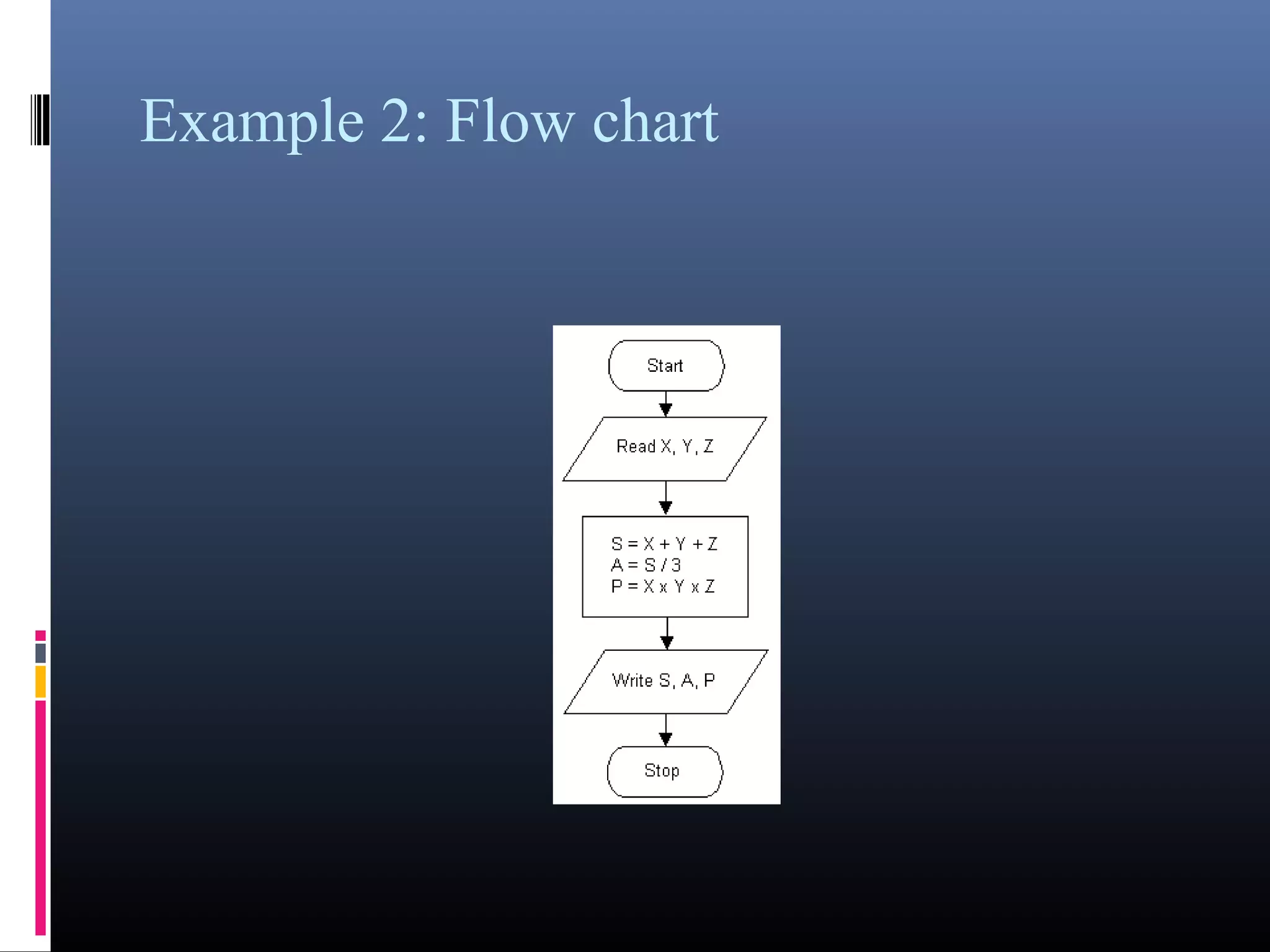
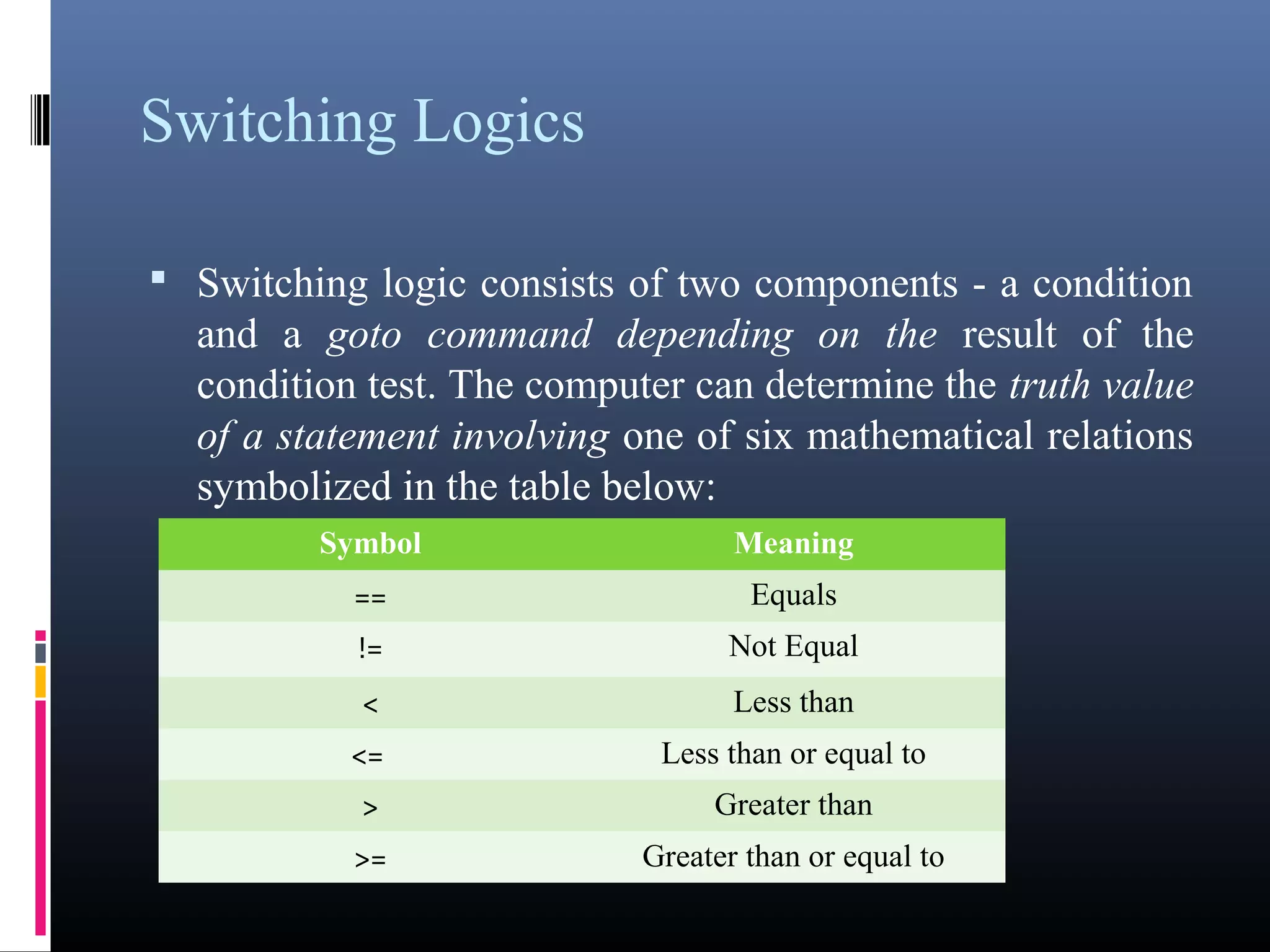
The document provides an overview of fundamentals of computers including:
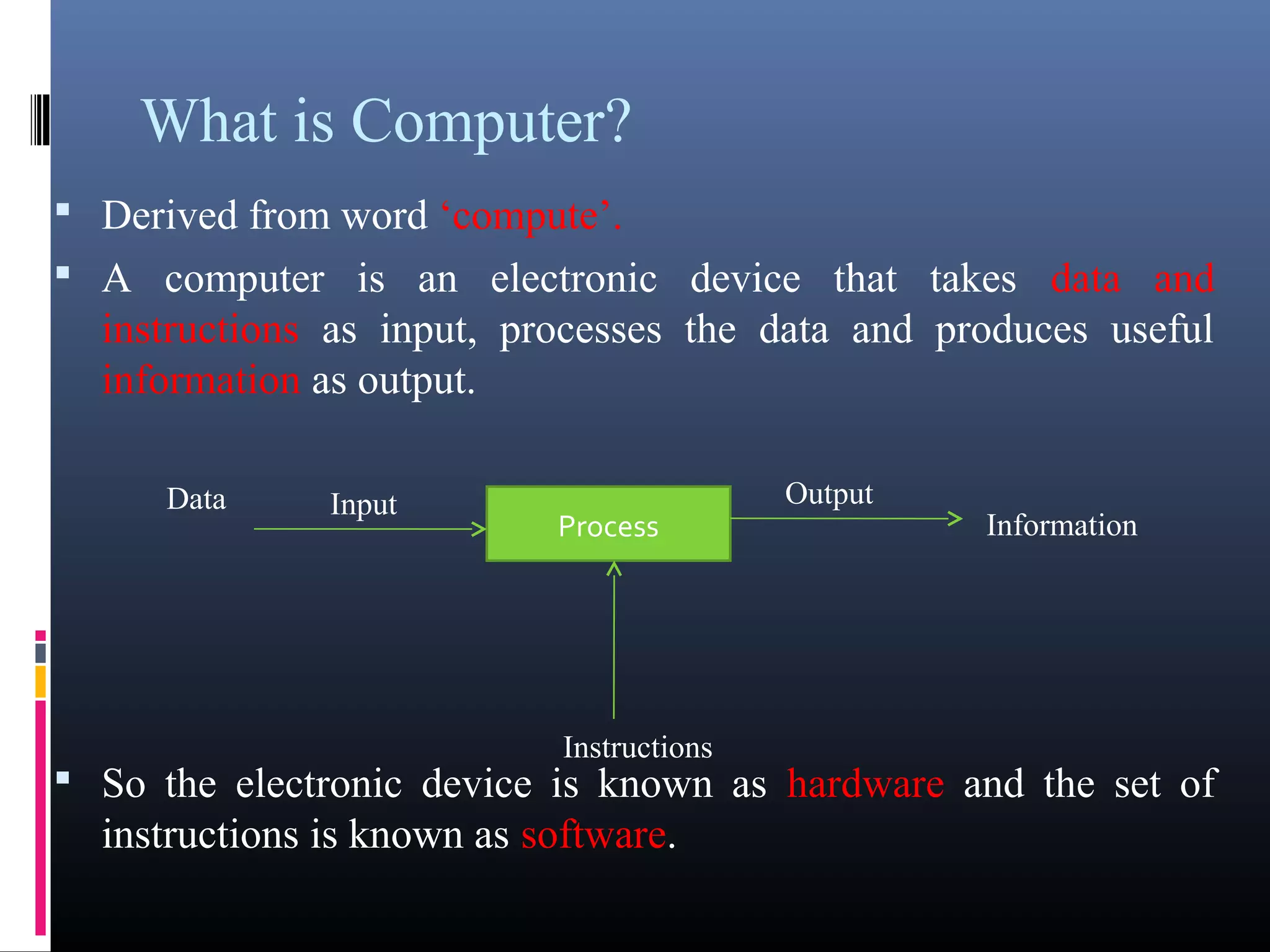
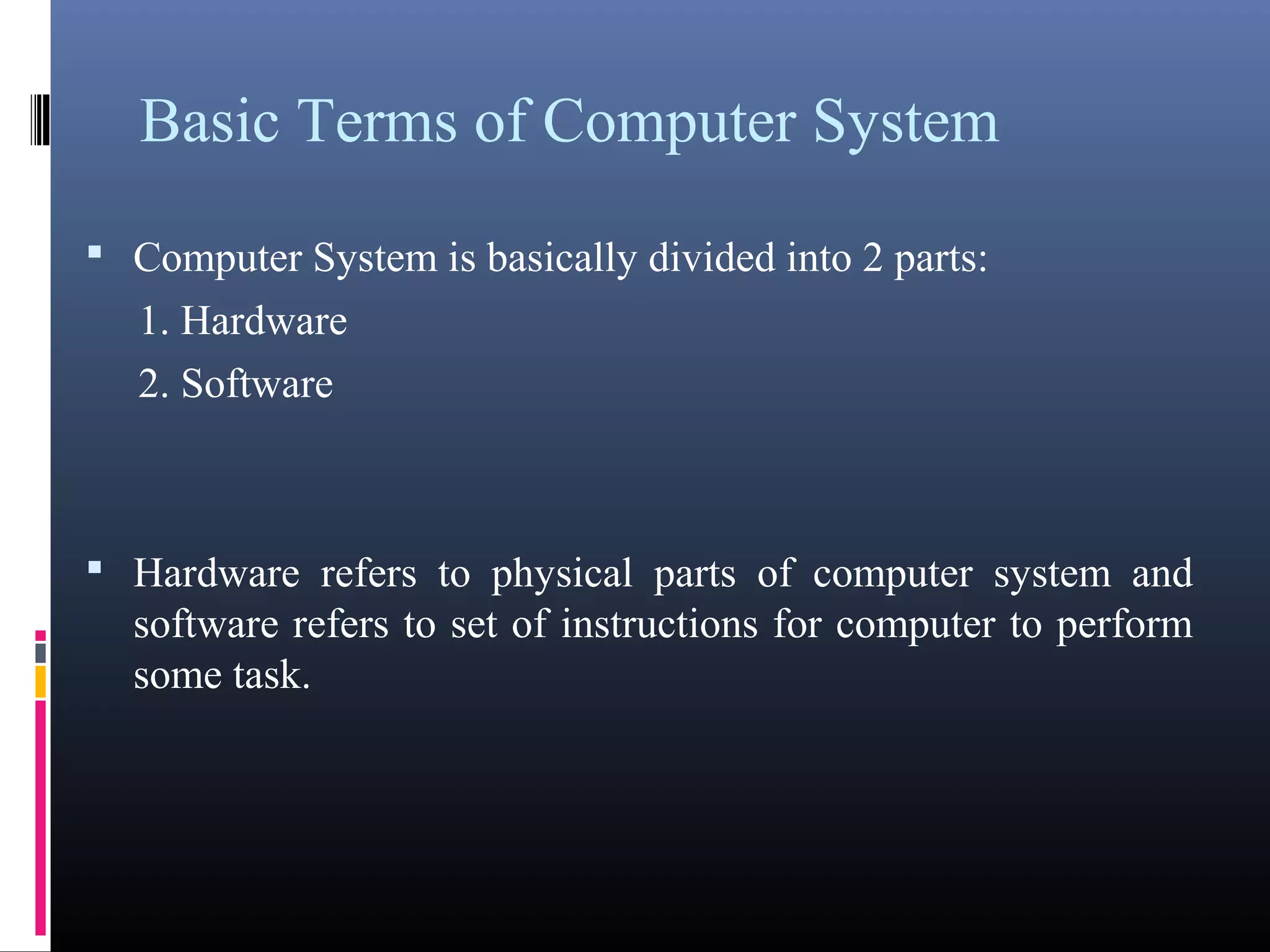
- What a computer is and its basic components like hardware, software, input, output, and processing.
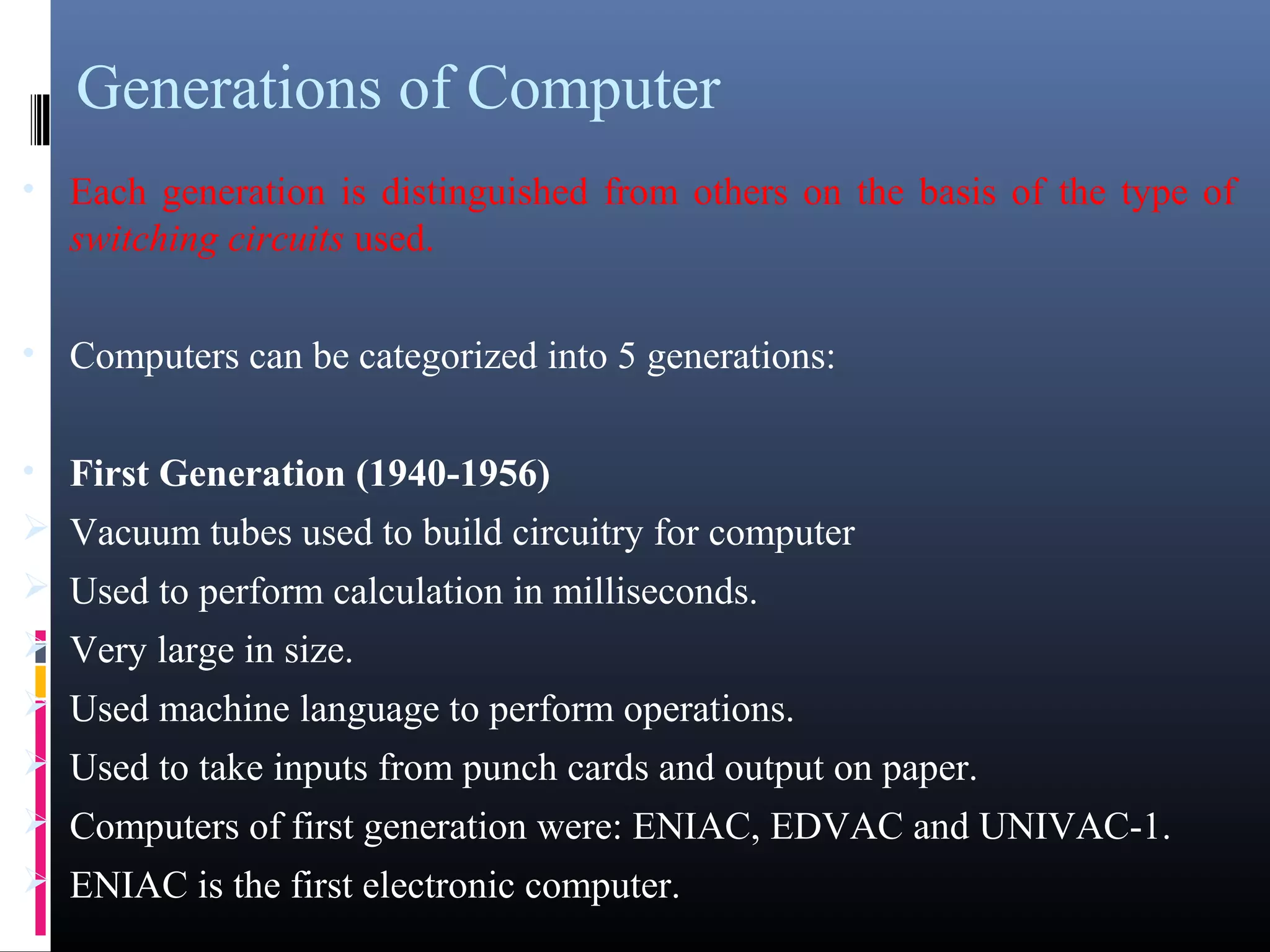
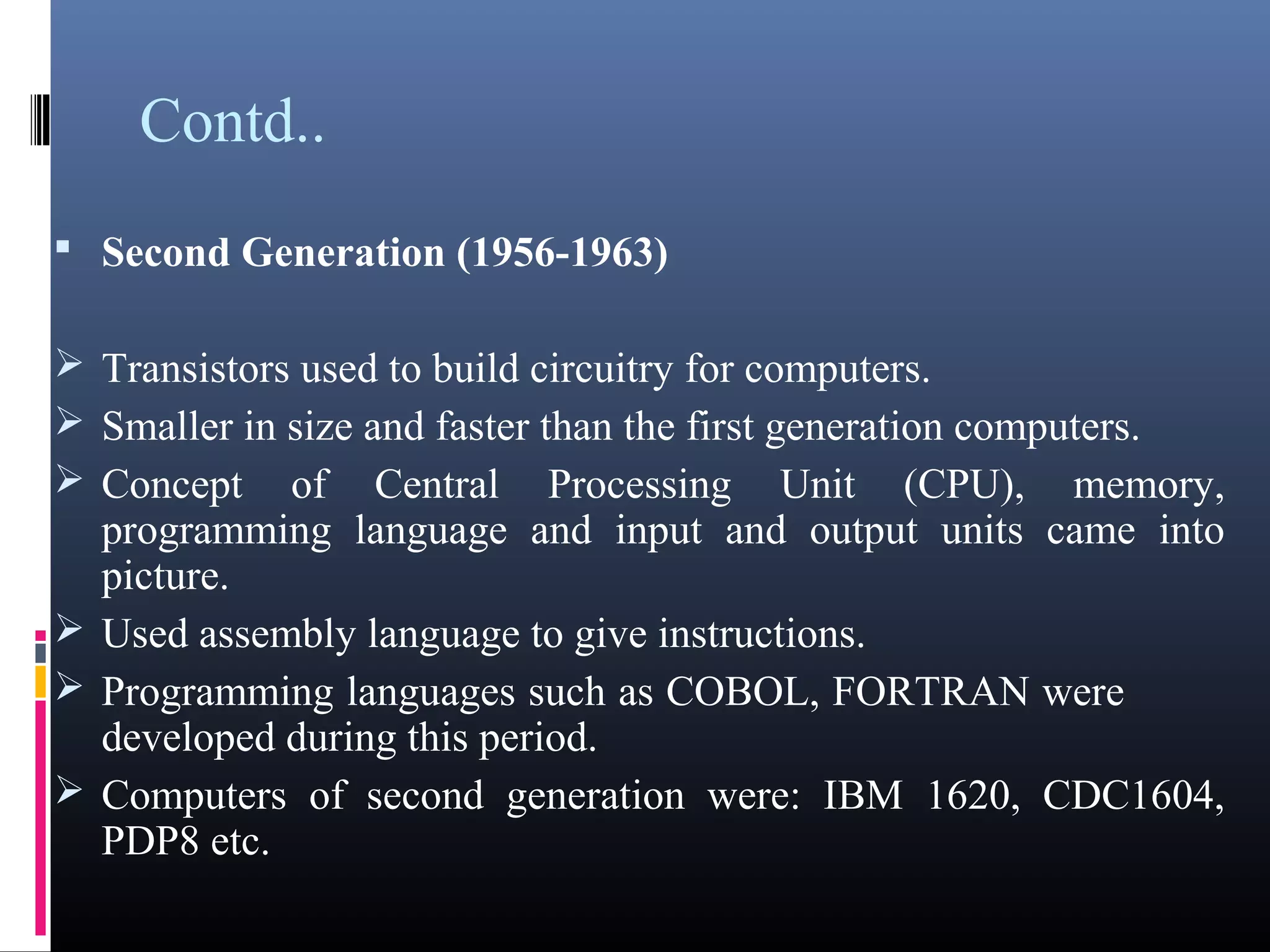
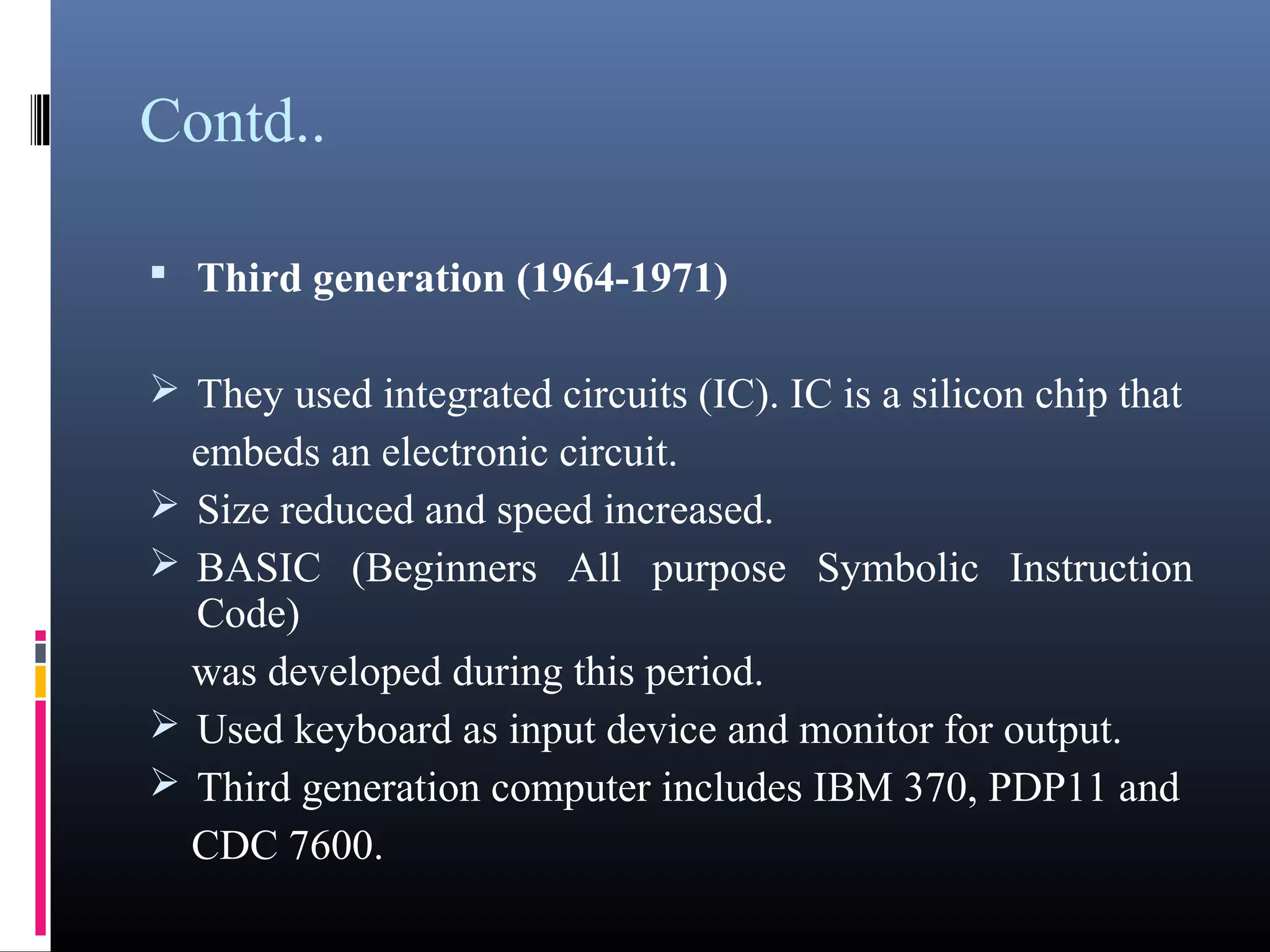
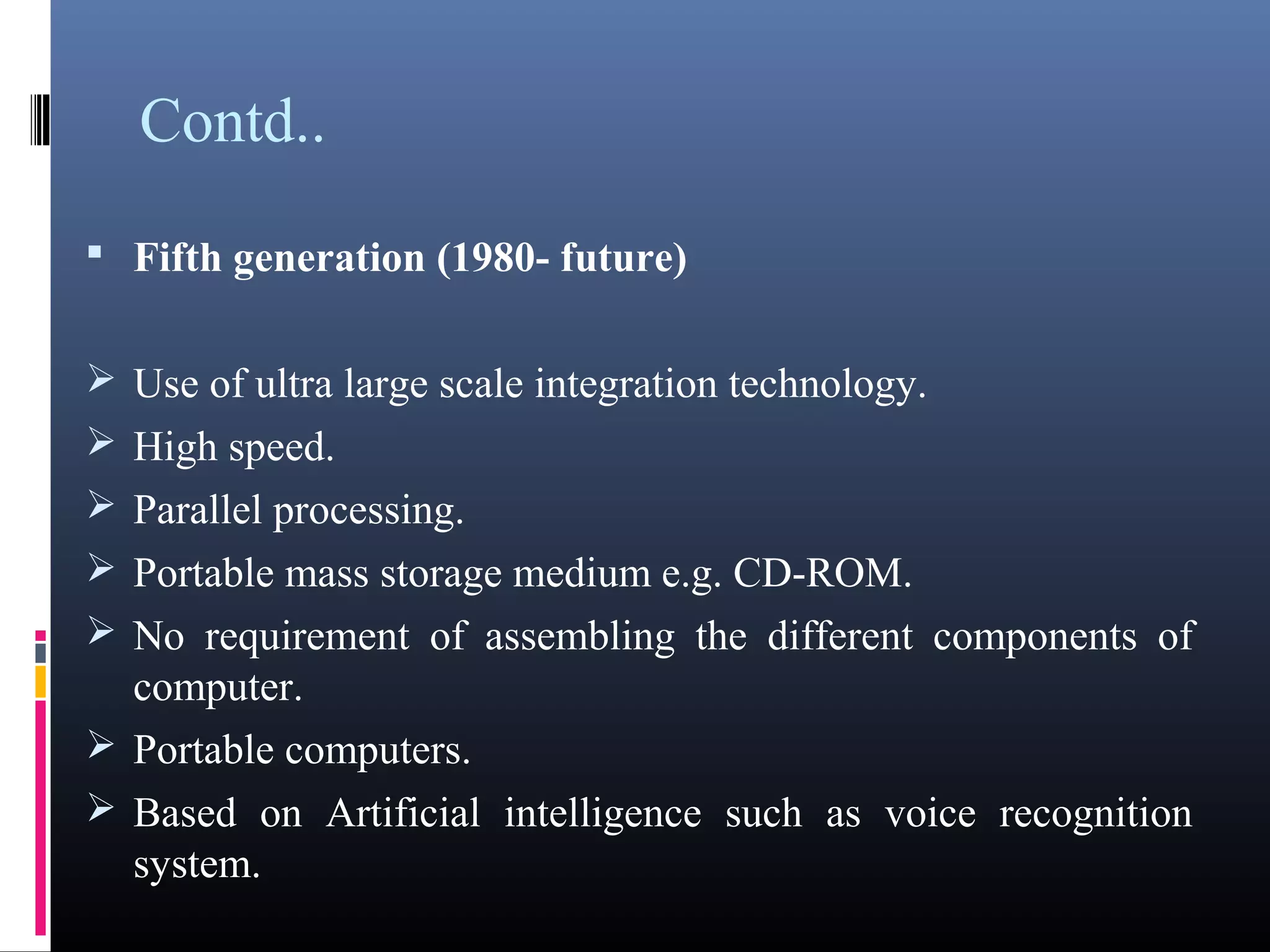
- The five generations of computers distinguished by their circuitry and technology used.
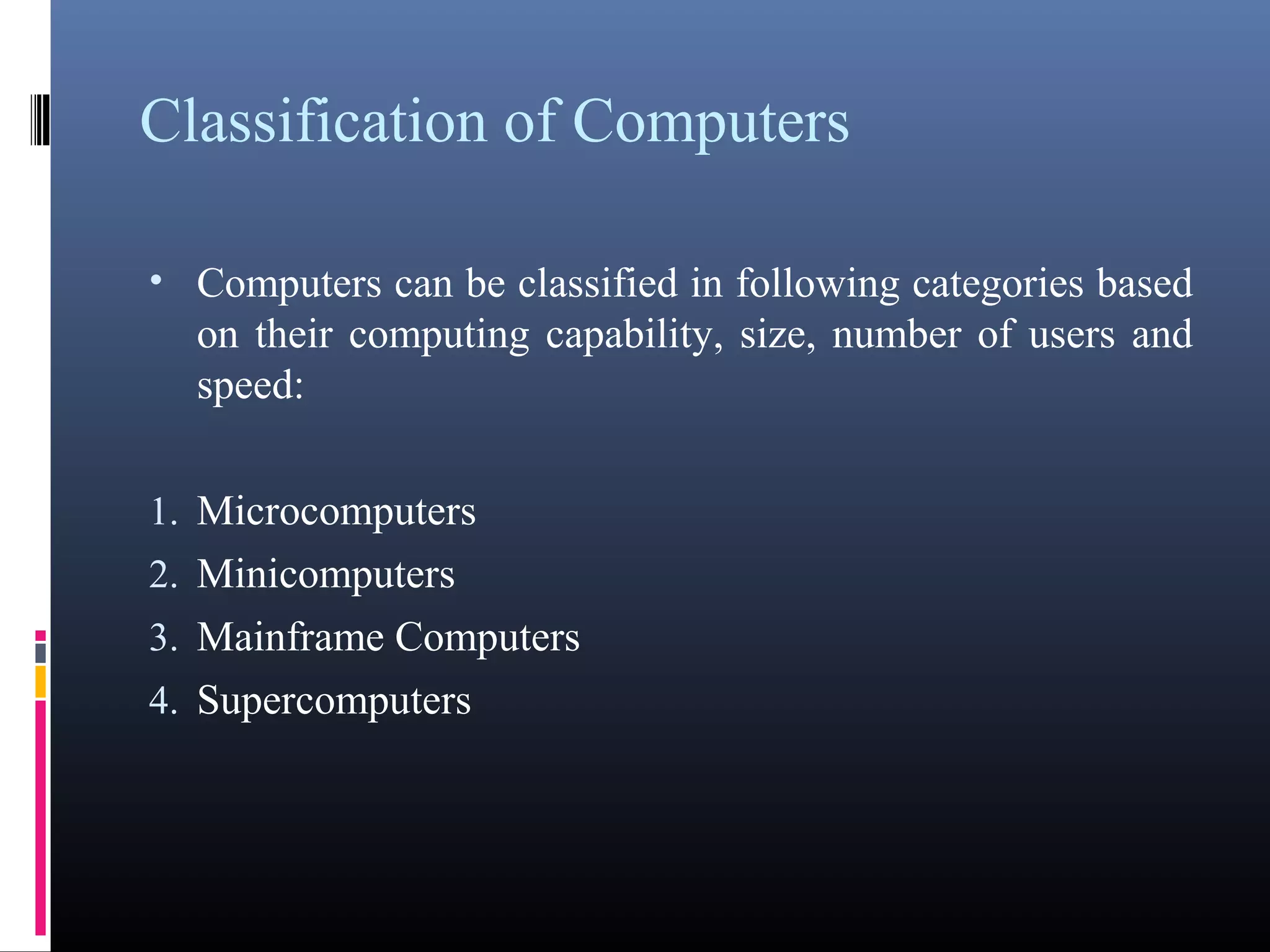
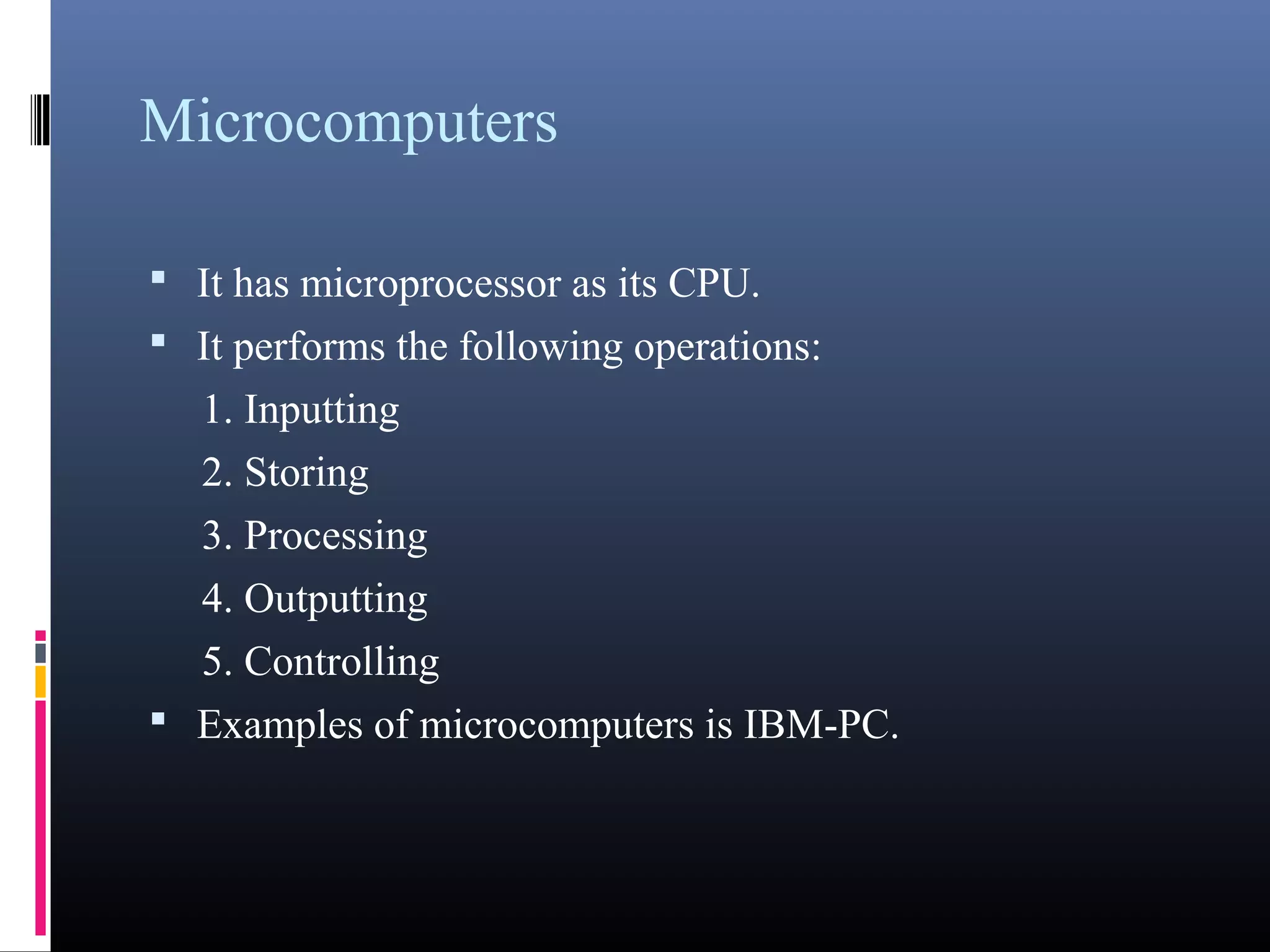
- Different types of computers classified by their capabilities, size, users, and speed such as microcomputers, minicomputers, mainframes, and supercomputers.
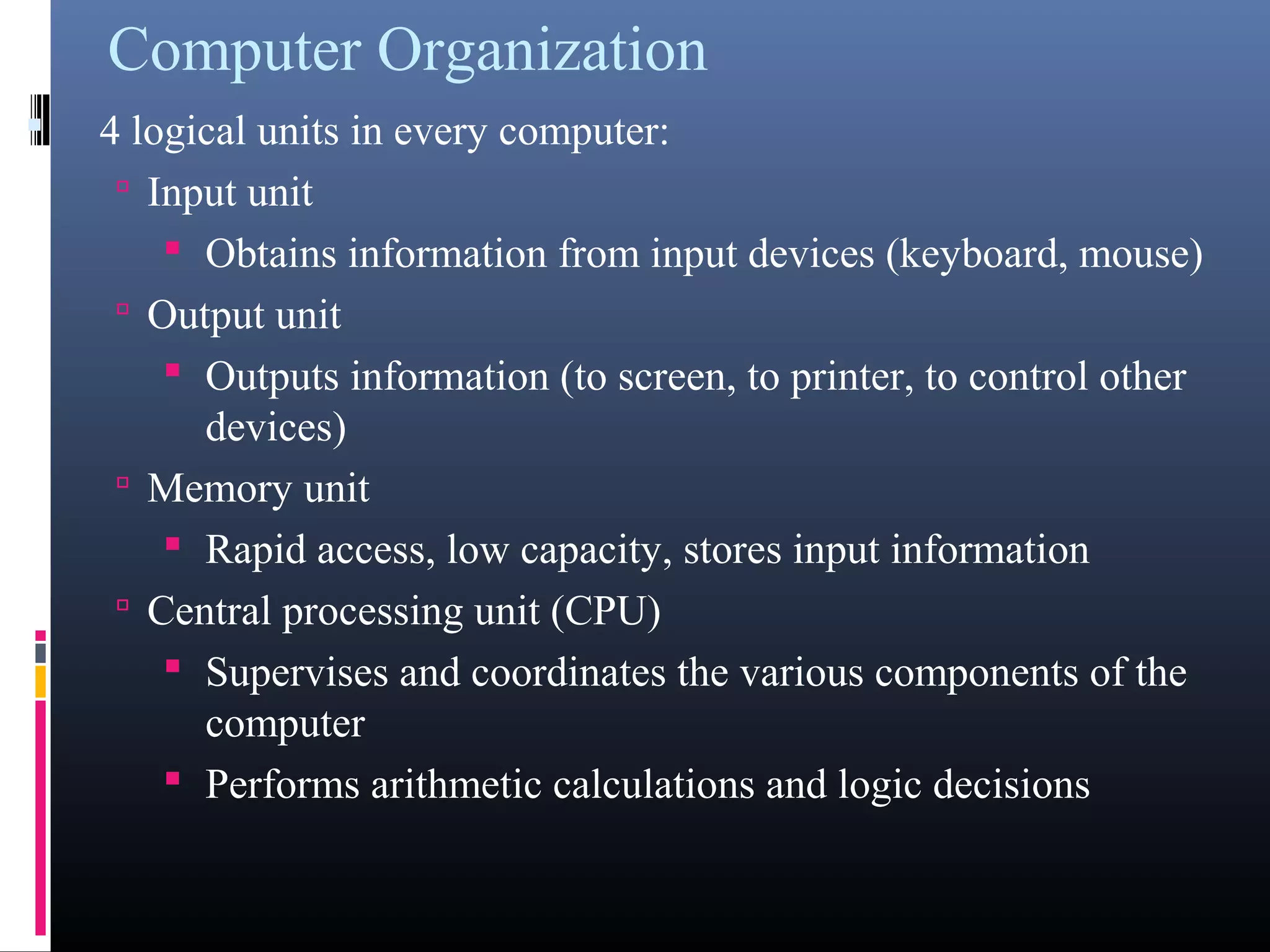
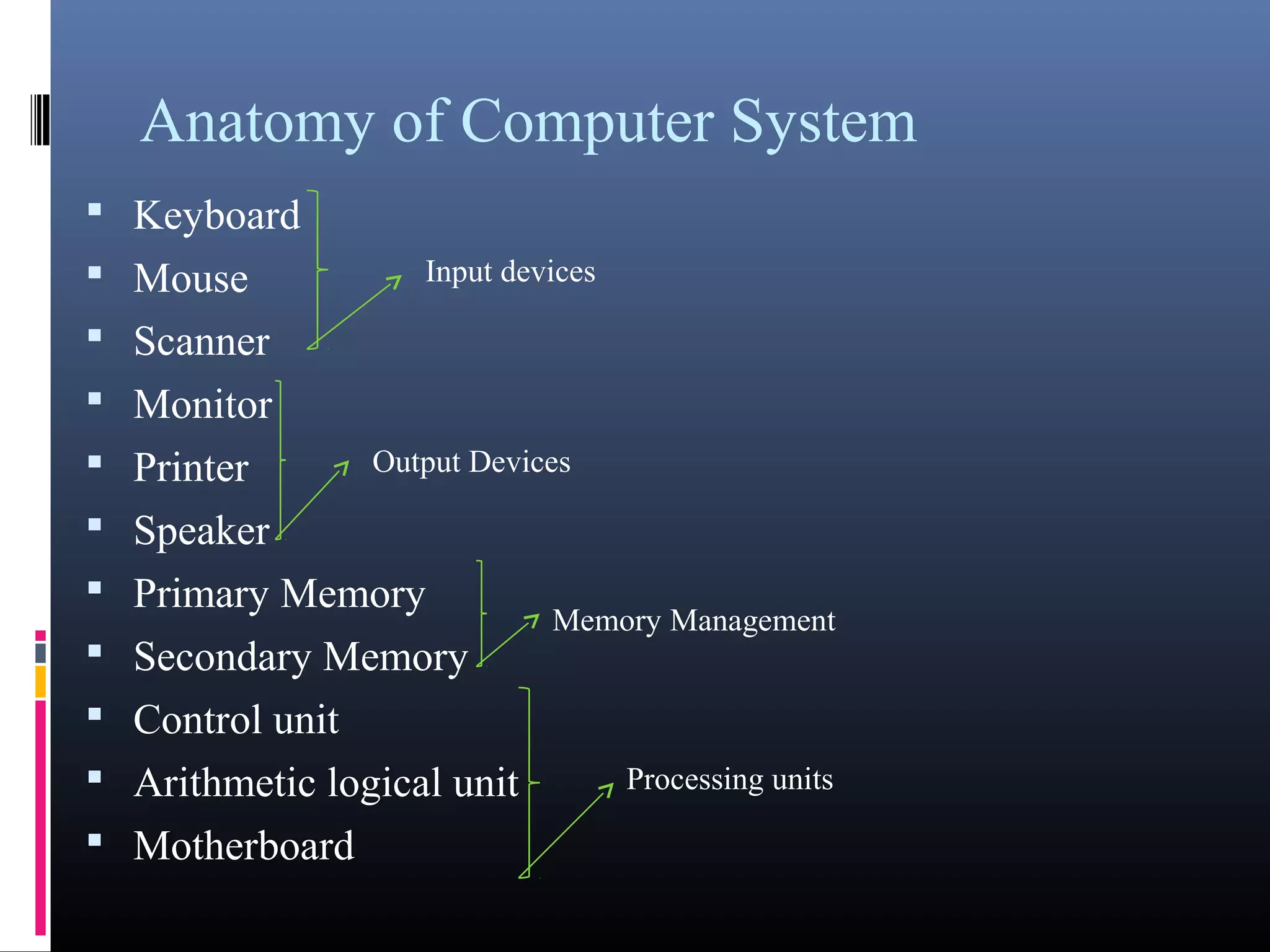
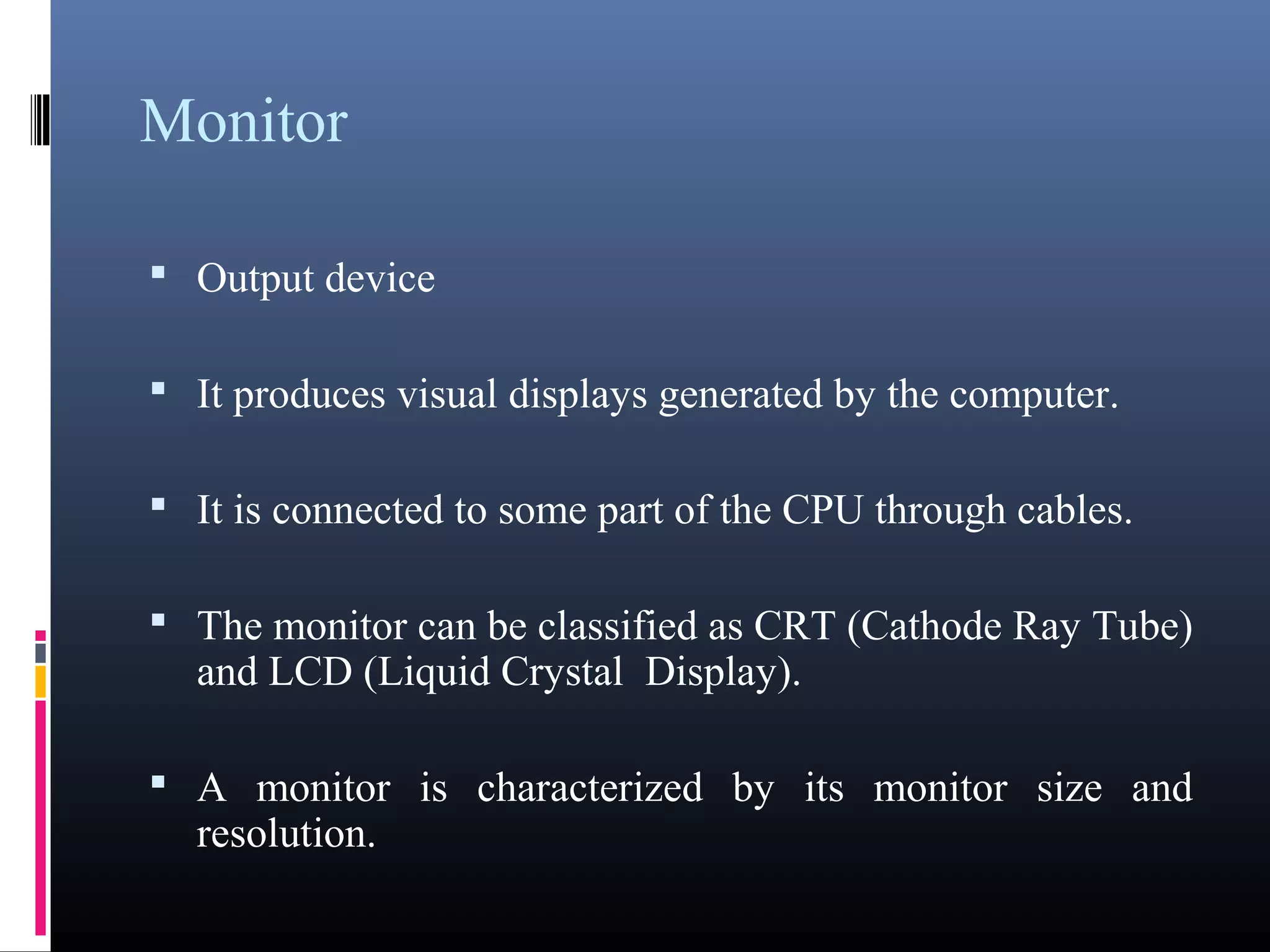
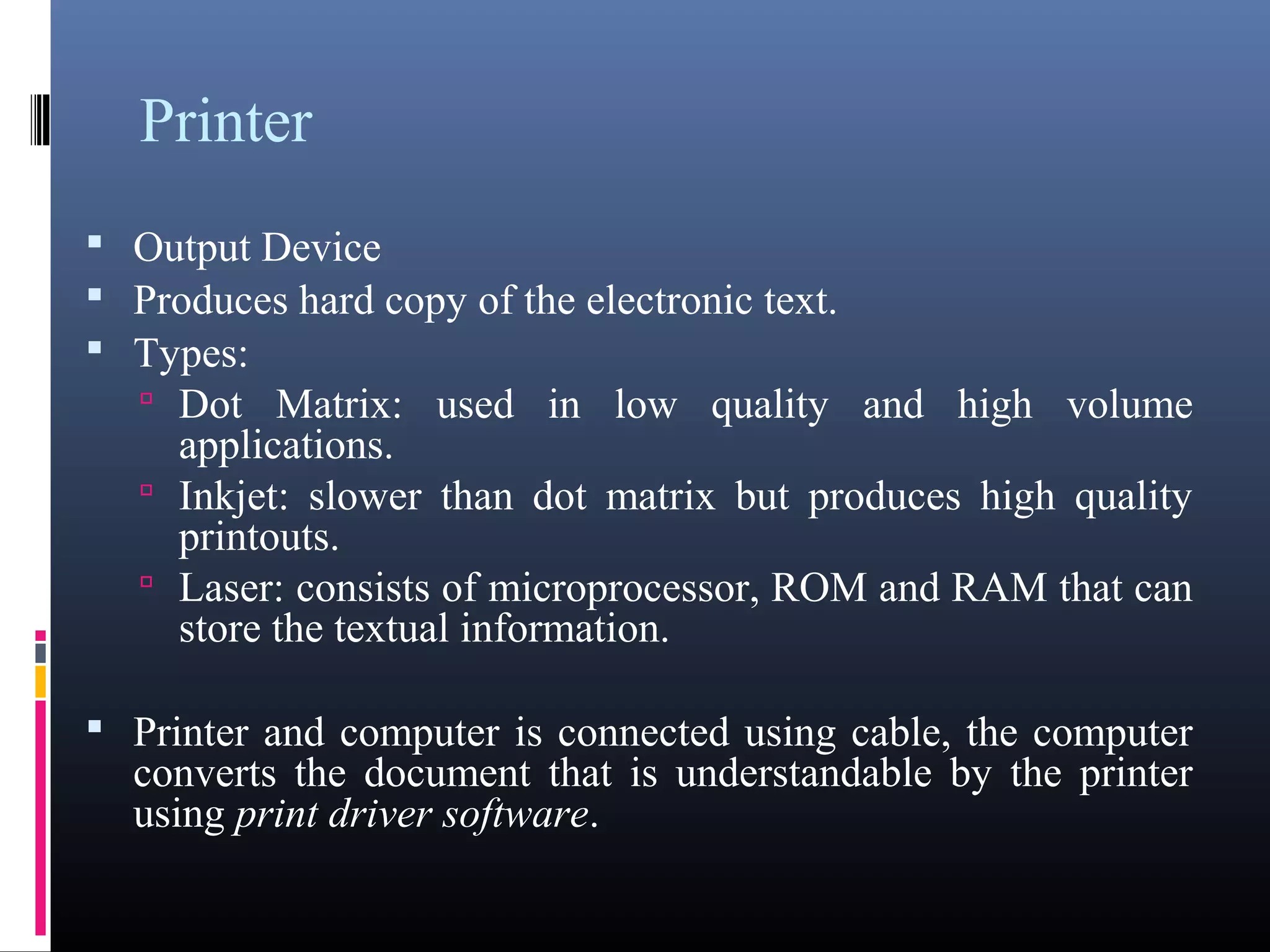
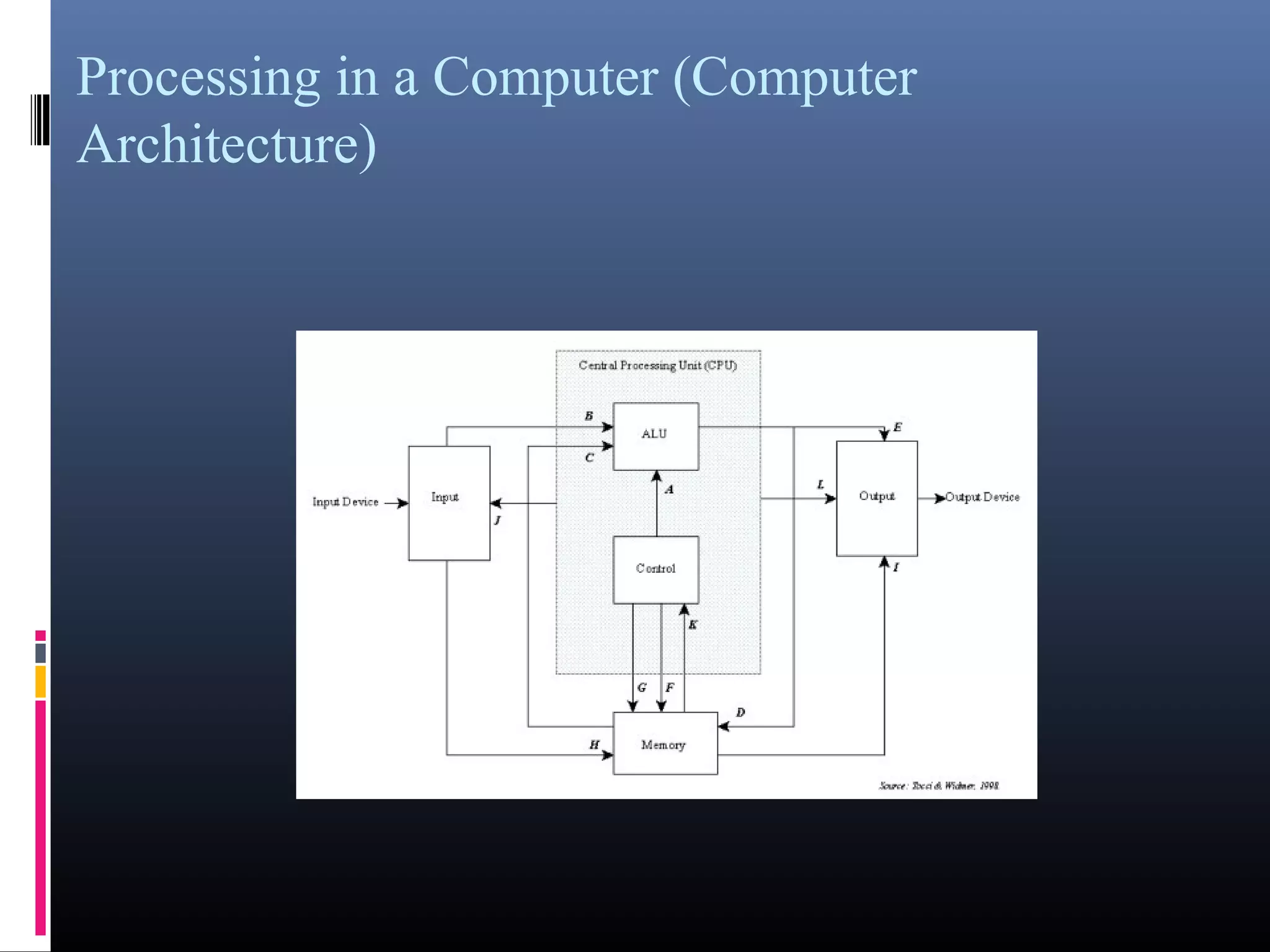
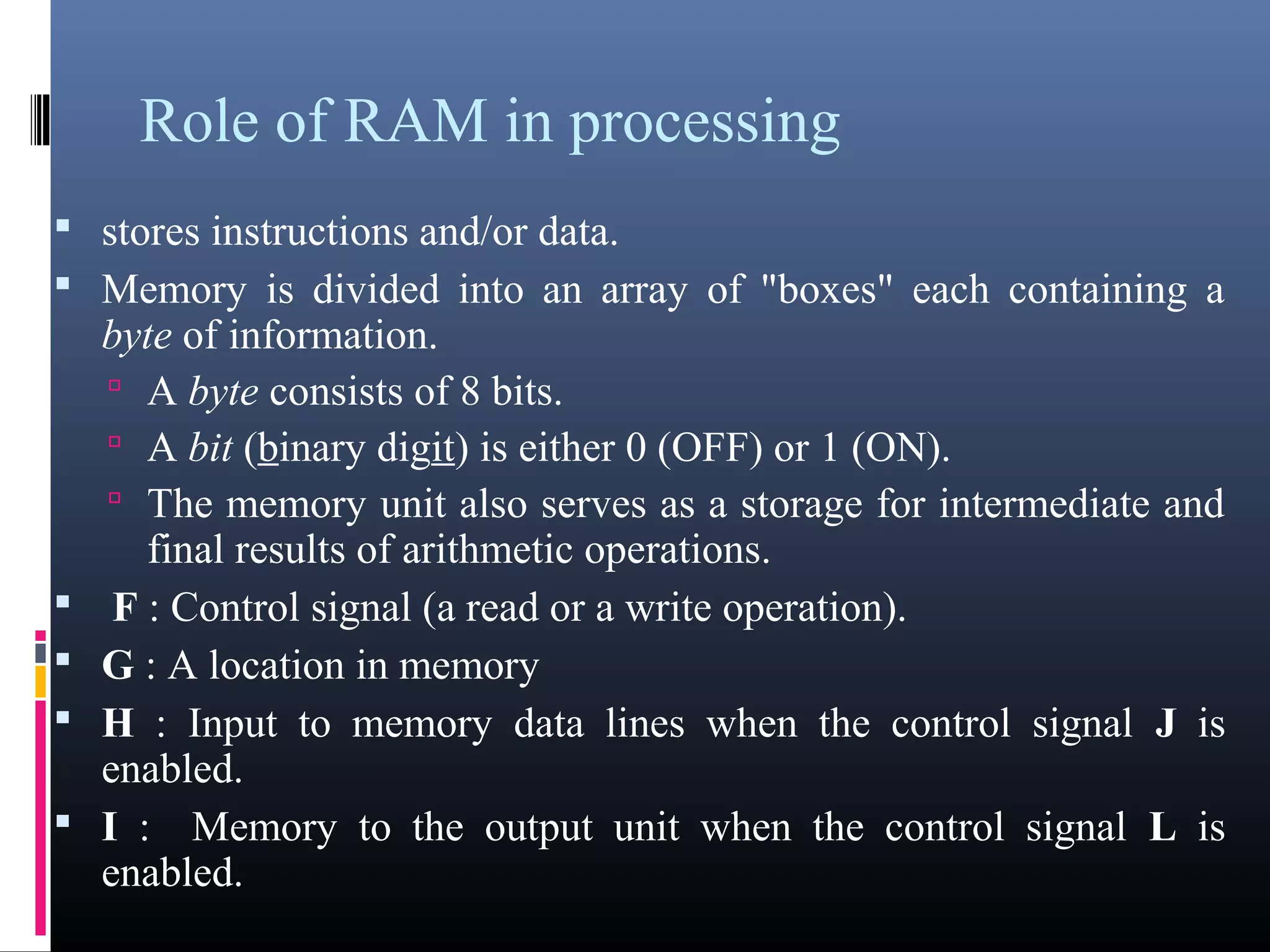
- Key components of a computer system including input, output, memory, processing units, and the motherboard.
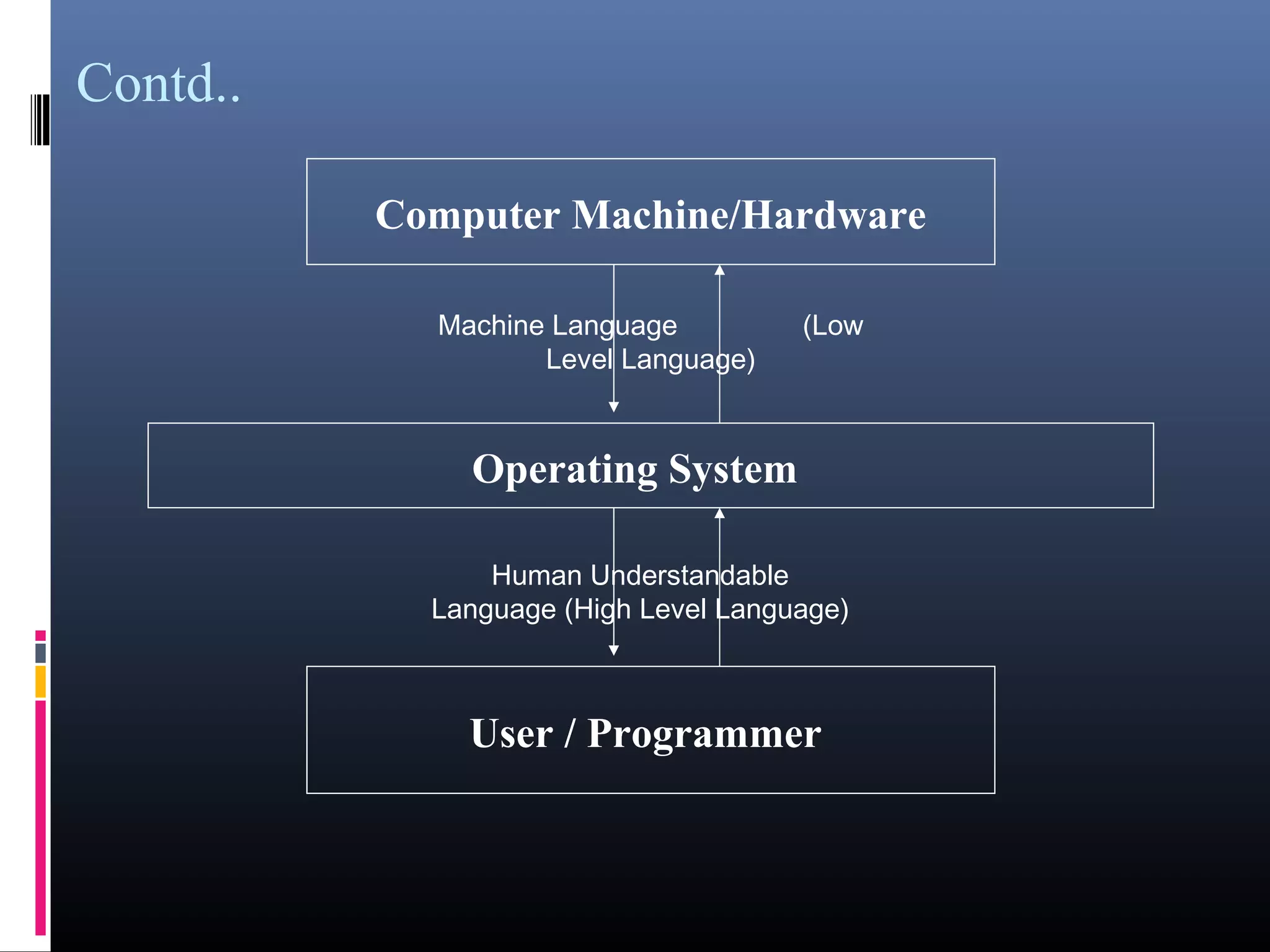
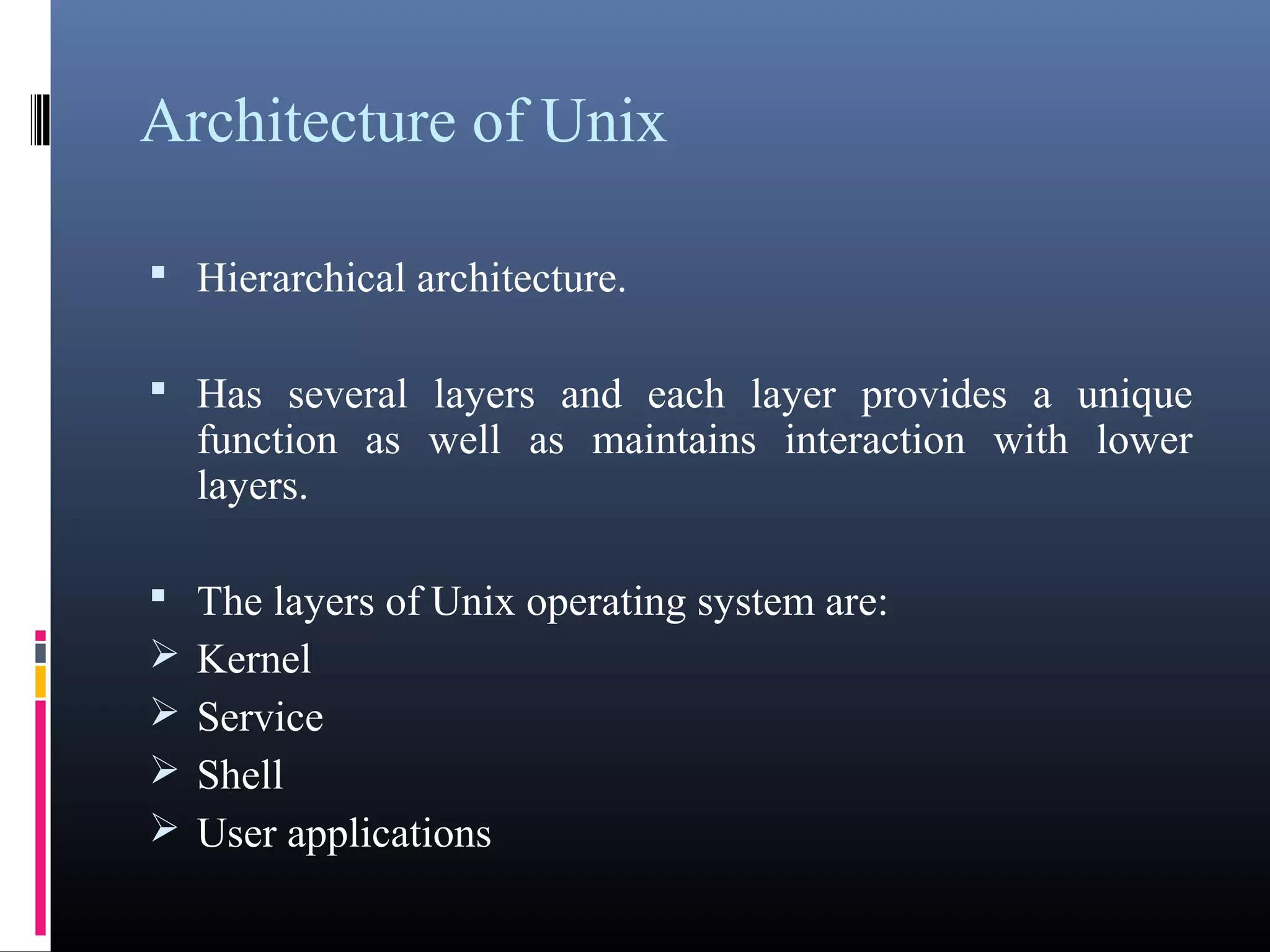
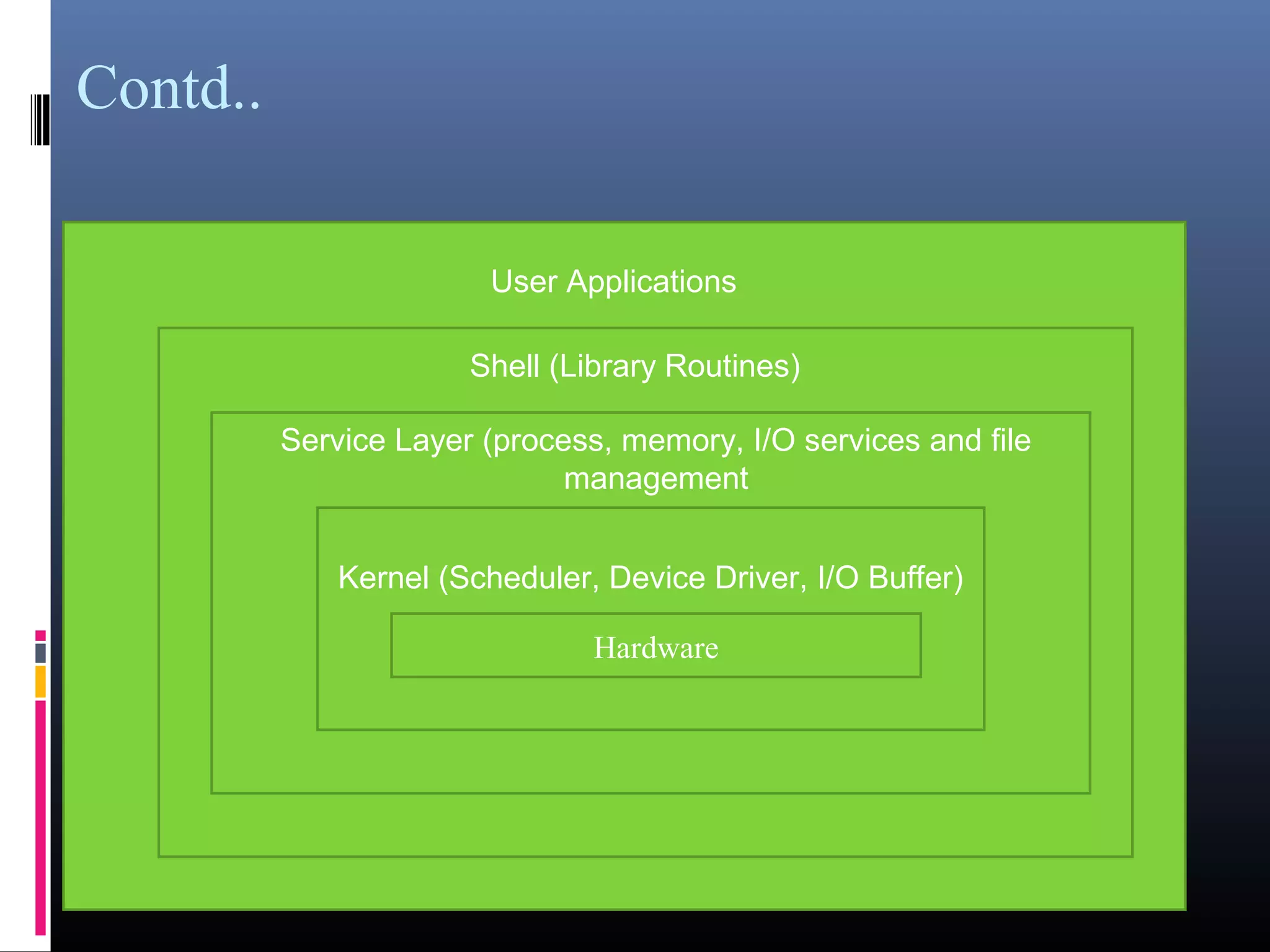
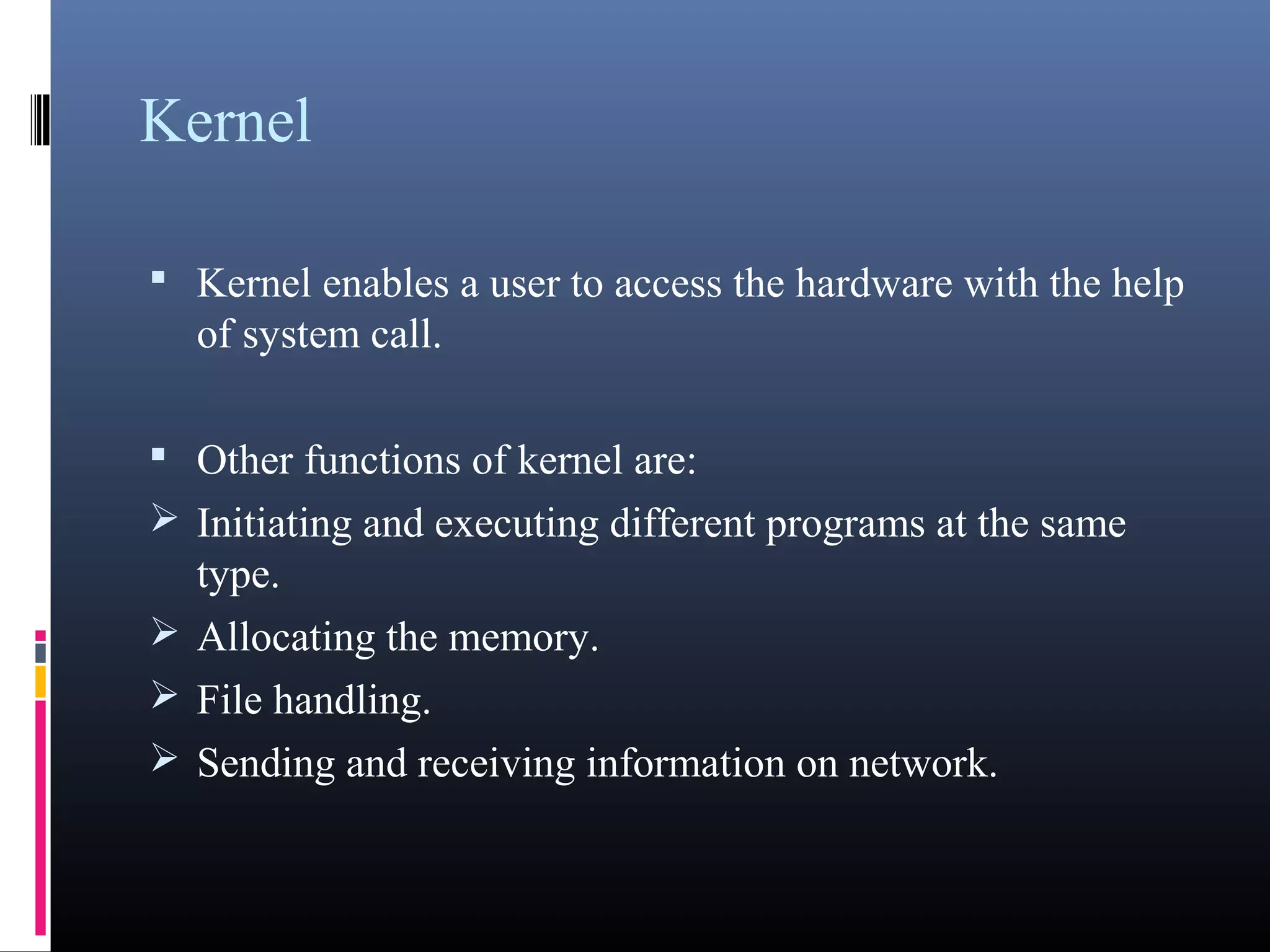
- An introduction to operating systems, their types, examples like DOS, UNIX, and components like the kernel, service layer, and shell.