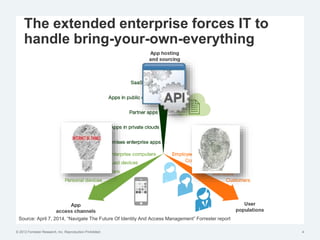
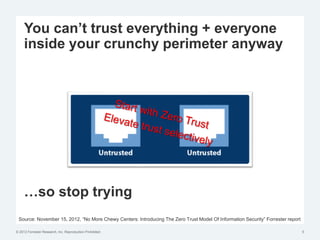
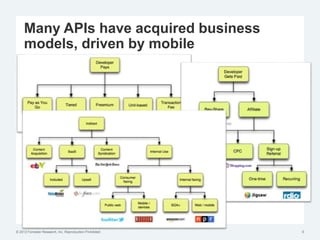
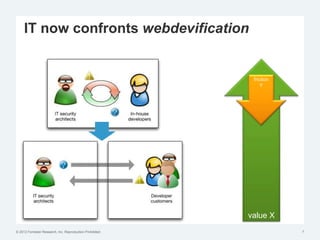
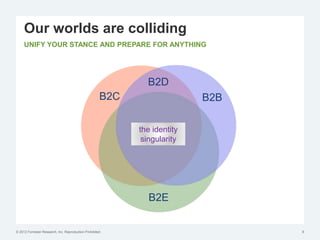
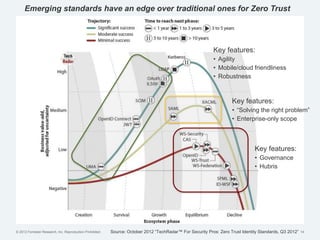
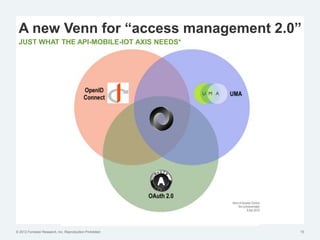
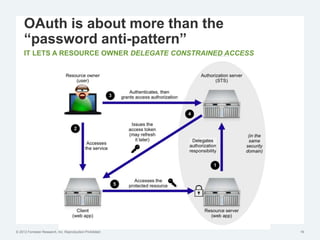
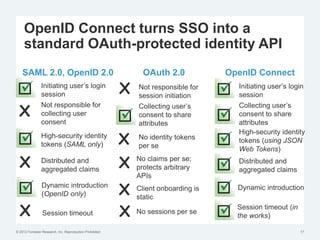
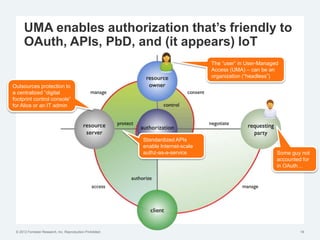
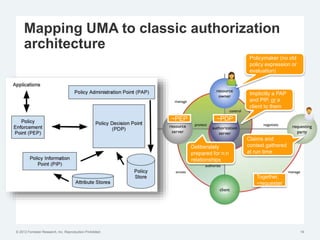
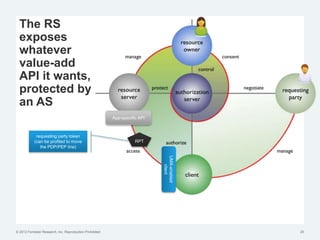
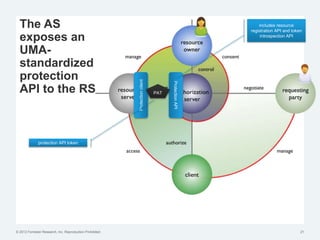
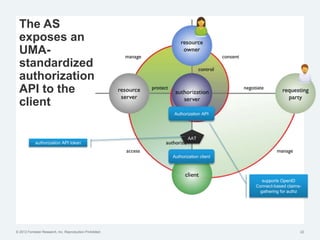
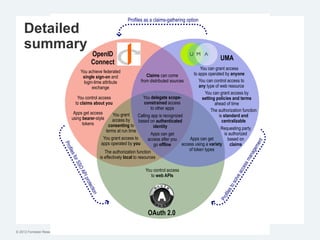
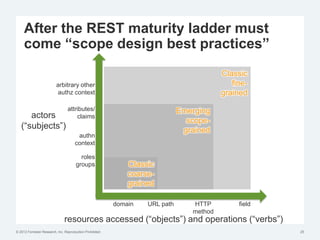
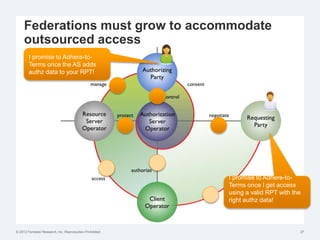
The document discusses the challenges of traditional identity and access management (IAM) in the context of APIs, mobile, and IoT, emphasizing the inadequacy of existing solutions. It introduces the concept of zero trust security and explores how emerging technologies can help transition to a more secure access management paradigm. The need for adaptive authorization practices and federated identities is highlighted, particularly in light of the bring-your-own-everything trend.