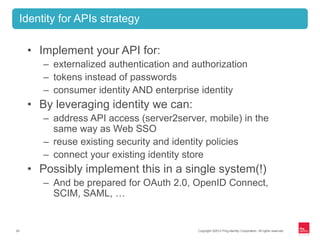
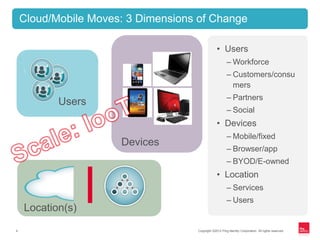
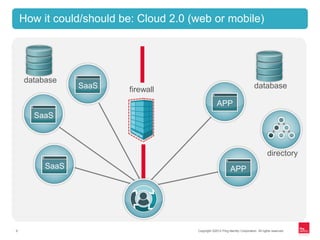
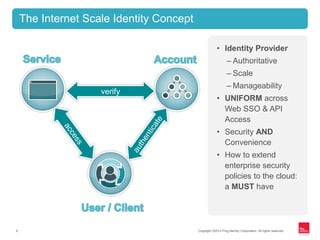
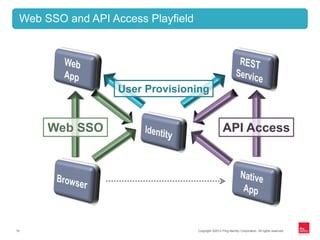
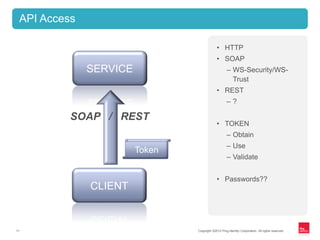
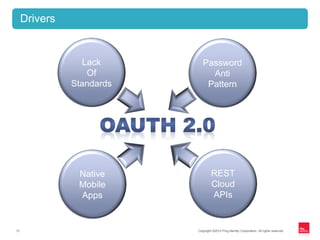
This document discusses identity management for APIs, web, and mobile applications. It begins with an overview of trends in cloud computing and APIs. It then discusses how traditional network security is inadequate for these new architectures and that identity has become the new perimeter. The document outlines recommendations for an API identity strategy, including implementing OAuth 2.0 for authorization instead of passwords and leveraging an identity provider to apply enterprise security policies to cloud applications and APIs. It recommends architects design for interoperability across multiple devices, users, locations, and protocols.

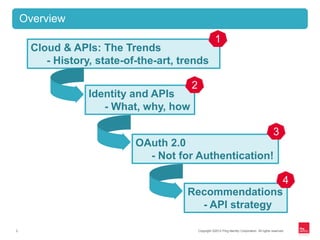
![Copyright ©2012 Ping Identity Corporation. All rights reserved.3
CLOUD & APIS: THE TRENDS
[section lead-in]](https://image.slidesharecdn.com/ping-identity-nordicapis-1-0-130527134017-phpapp02/85/Who-s-Knocking-Identity-for-APIs-Web-and-Mobile-3-320.jpg)






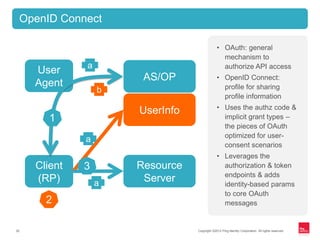
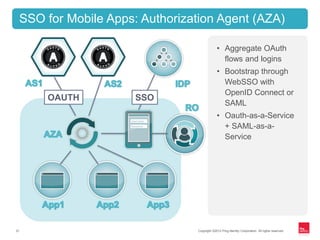
![Copyright ©2012 Ping Identity Corporation. All rights reserved.22
RECOMMENDATIONS
[section lead-in]](https://image.slidesharecdn.com/ping-identity-nordicapis-1-0-130527134017-phpapp02/85/Who-s-Knocking-Identity-for-APIs-Web-and-Mobile-22-320.jpg)