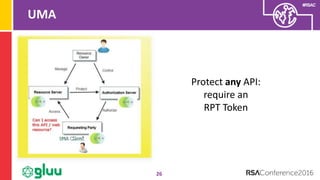
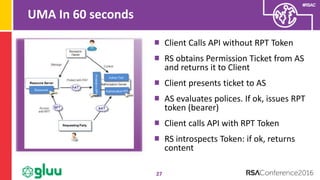
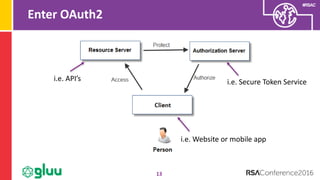
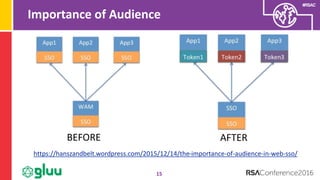
The document discusses the importance of two-factor authentication (2FA) and multi-factor authentication in enhancing security, emphasizing the need for standardized API usage for trust elevation and the challenges associated with deploying these methods. It also highlights the role of OAuth2 in making 2FA more deployable and the necessity of collaboration among domains to align on authentication standards. Finally, the document advocates for broader trust elevation strategies beyond just 2FA to enhance overall security in applications.












![#RSAC
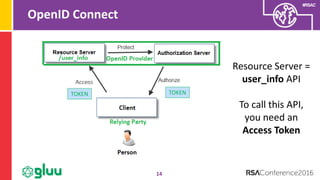
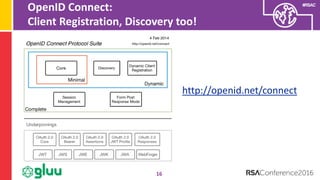
OpenID Connect id_token
18
Information about
authentication event
{
"iss": "https://server.example.com",
“sub": "248289761001",
"aud": "3214244",
"iat": 1311195570,
"exp": 1311281970,
“auth_time”: 131195001,
“acr”: http://example.com/basic_bio”
“amr”: [‘eye’, ‘pwd’, ‘12’]
}](https://image.slidesharecdn.com/idy-f02-dont-use-two-factor-authentication-unless-you-need-it-160303175454/85/RSA-Conference-2016-Don-t-Use-Two-Factor-Authentication-Unless-You-Need-It-18-320.jpg)




![#RSAC
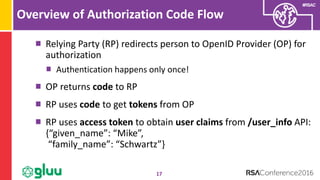
id_token
23
Returned id_token
confirms acr and amr
values
{
"iss": "https://server.example.com",
“sub": "248289761001",
"aud": "3214244",
"iat": 1311195570,
"exp": 1311281970,
“auth_time”: 131195001,
“acr”: http://example.com/basic_bio”
“amr”: [‘eye’, ‘pwd’, ‘12’]
}](https://image.slidesharecdn.com/idy-f02-dont-use-two-factor-authentication-unless-you-need-it-160303175454/85/RSA-Conference-2016-Don-t-Use-Two-Factor-Authentication-Unless-You-Need-It-23-320.jpg)