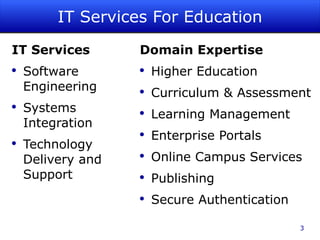
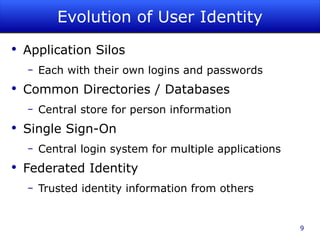
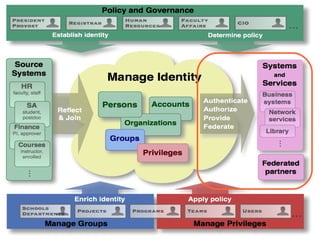
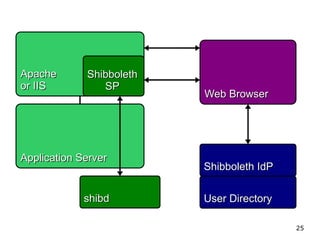
The document is a guided tour of Shibboleth, a federated identity management software primarily used in education. It discusses identity management principles, SAML standards, installation and configuration, and the benefits of federated identity systems. The content emphasizes open-source technology, security, and integration with existing systems while providing resources and support for users and developers.