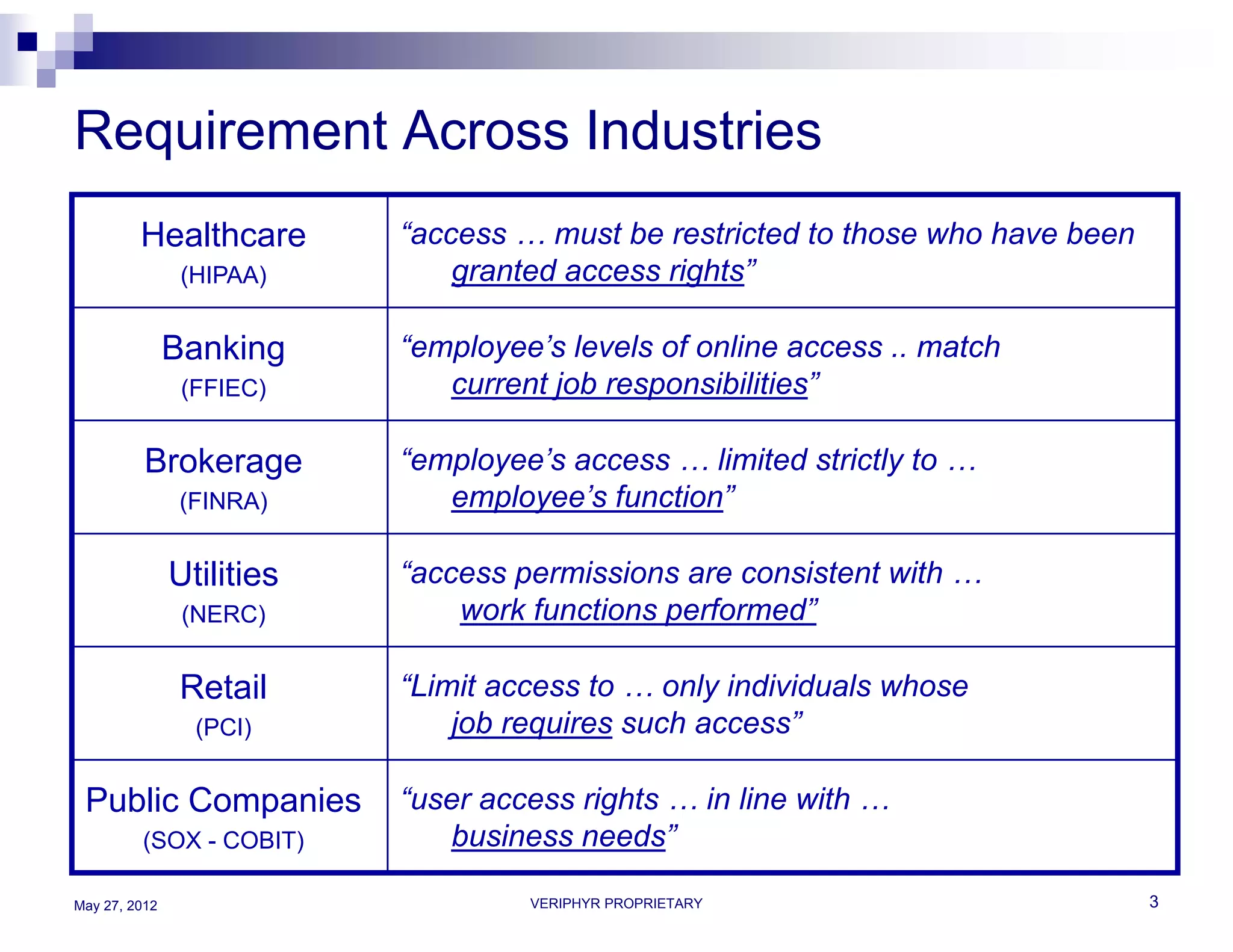
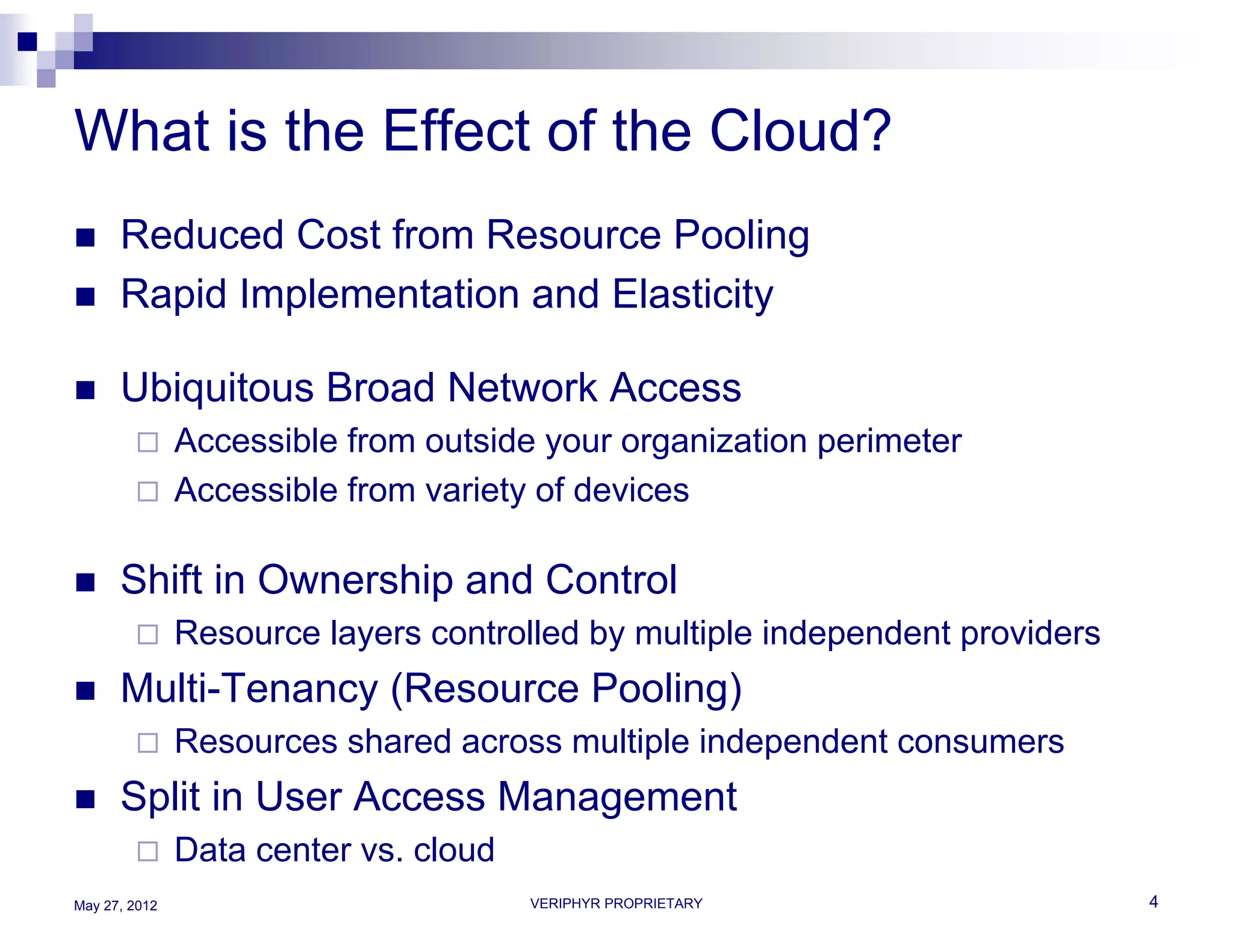
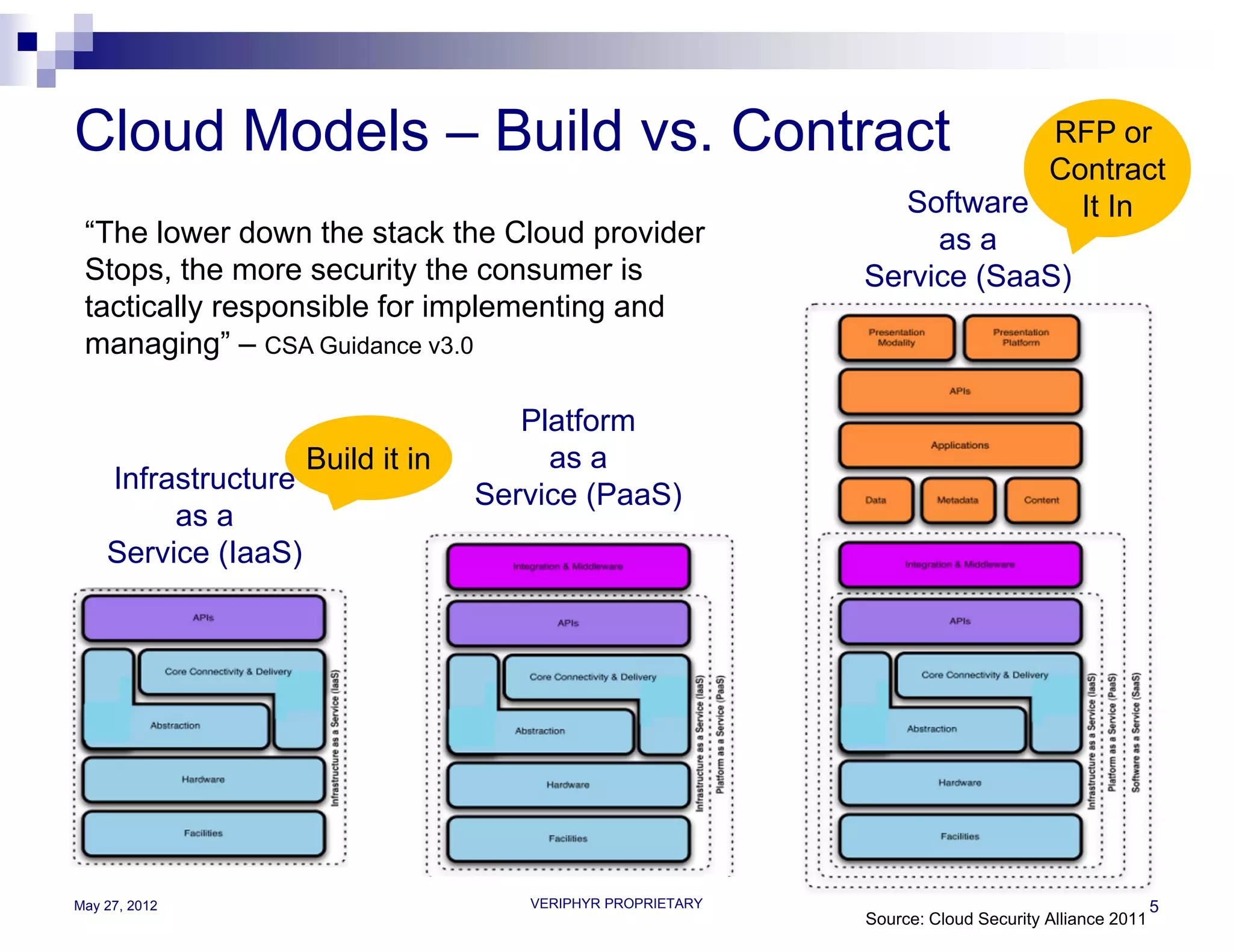
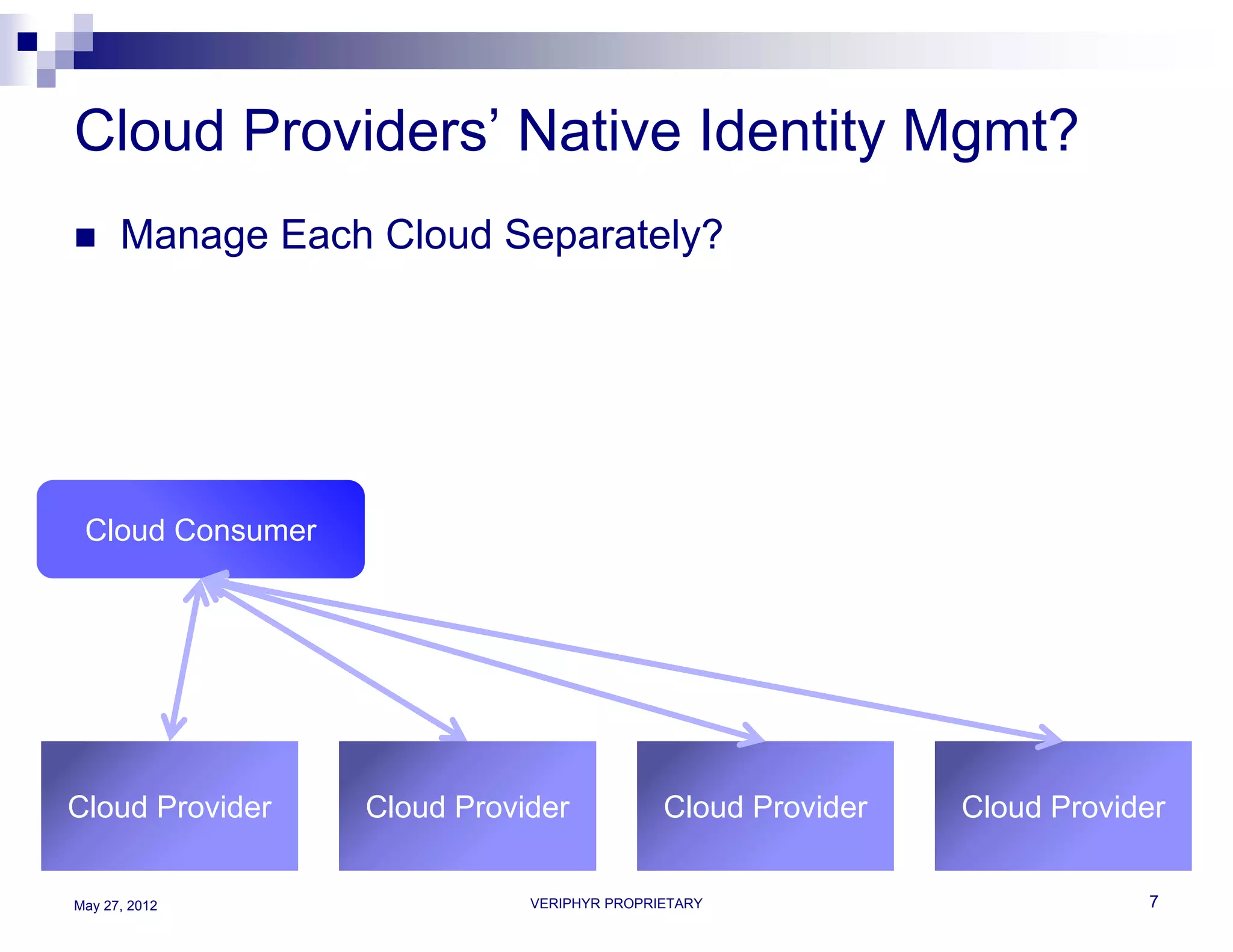
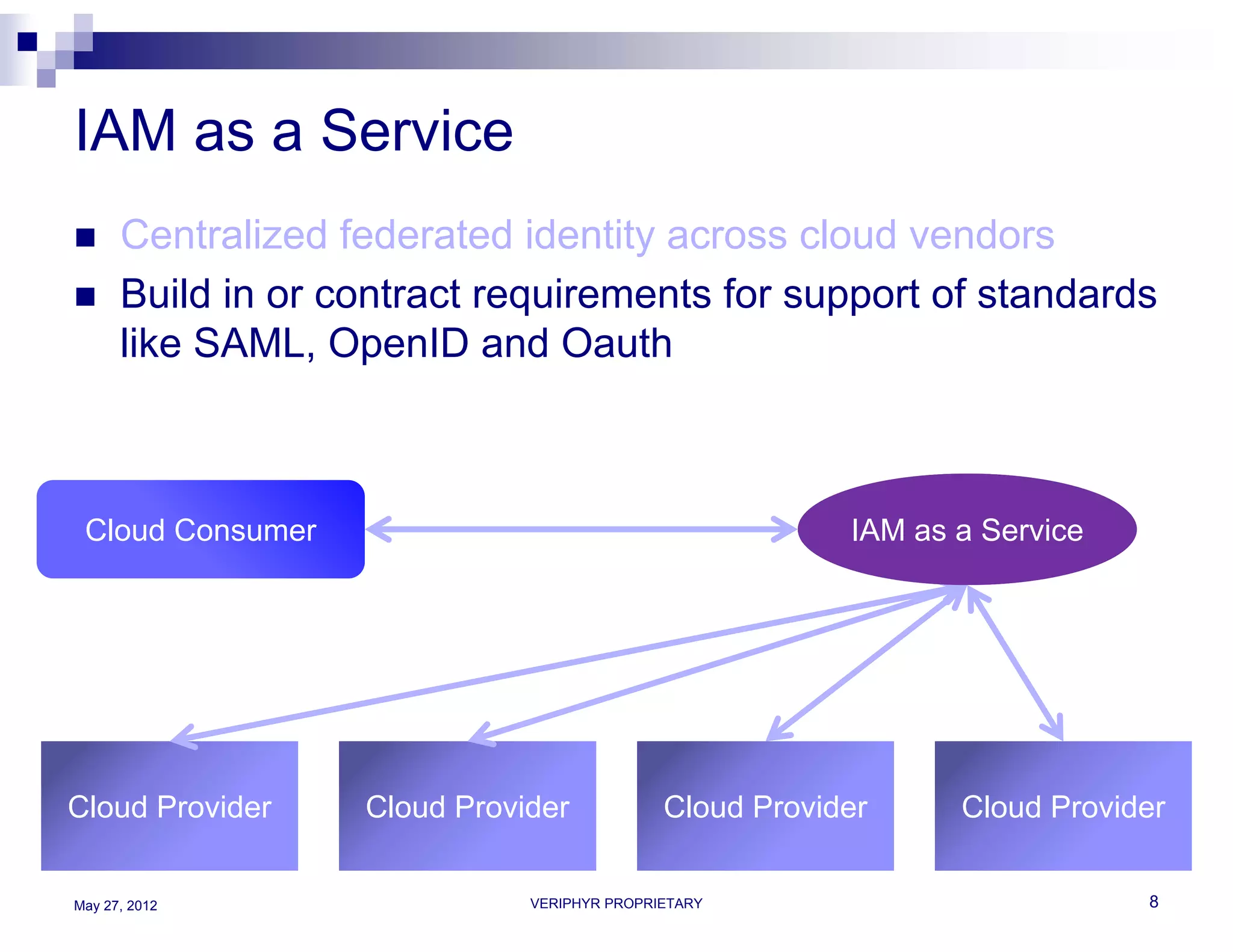
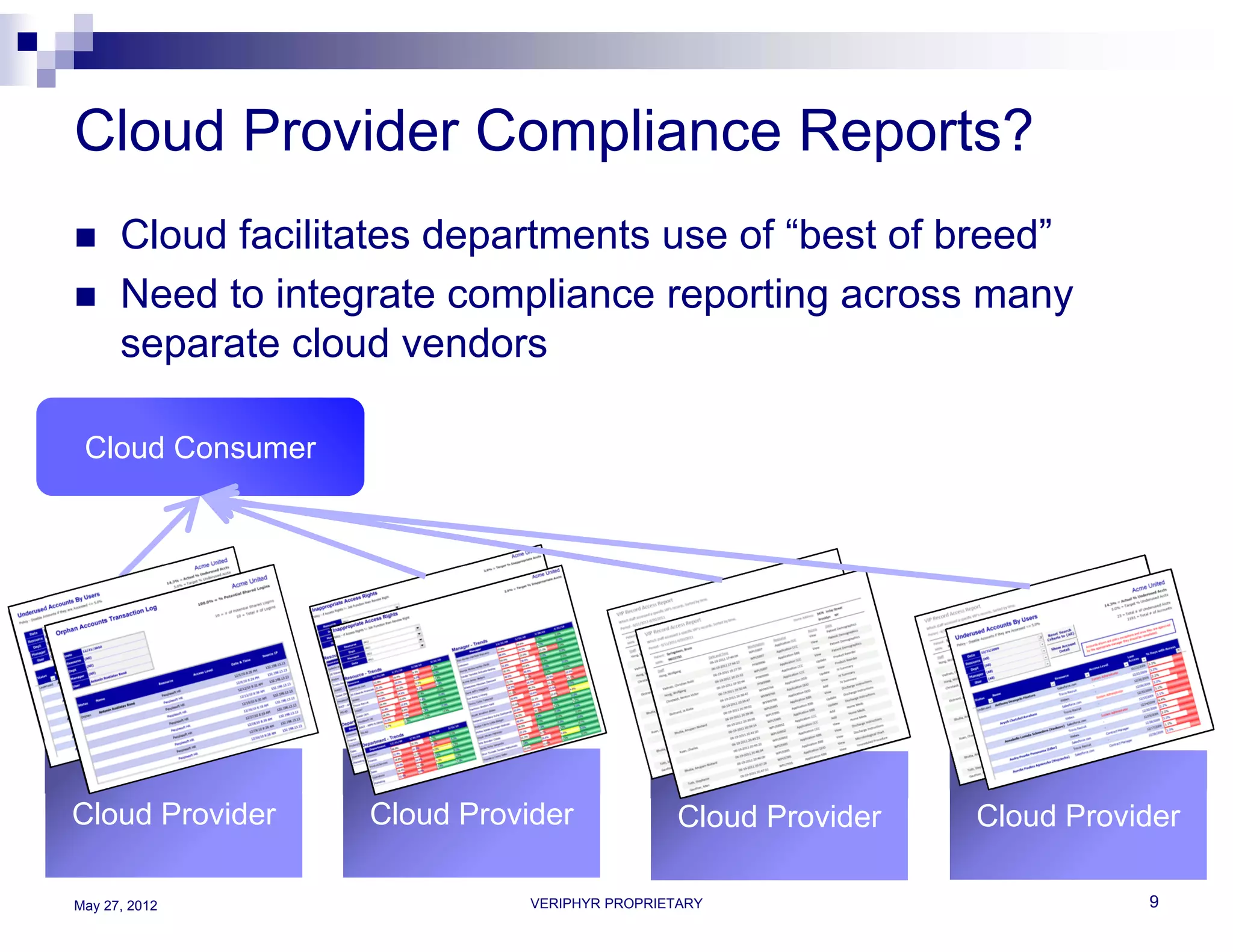
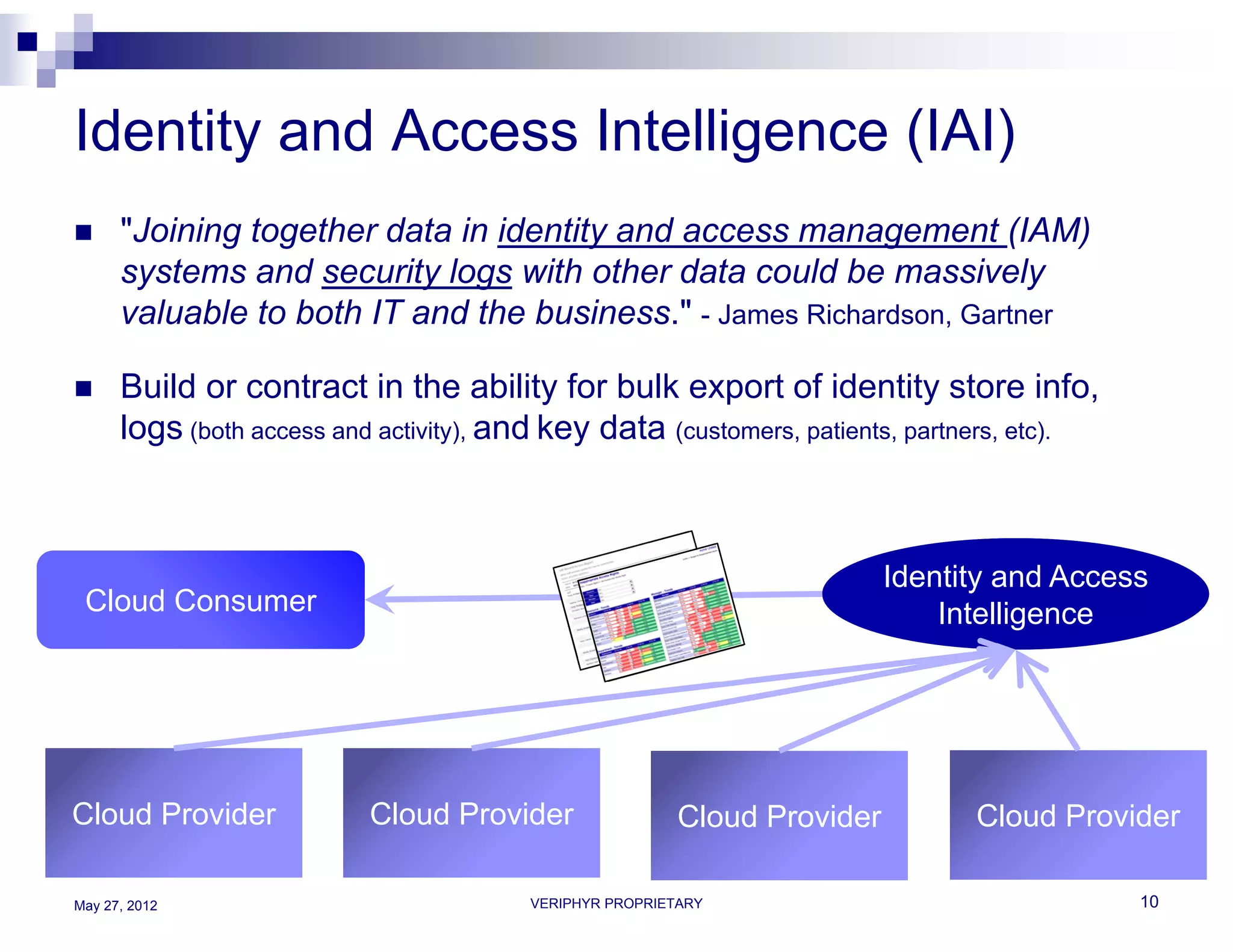
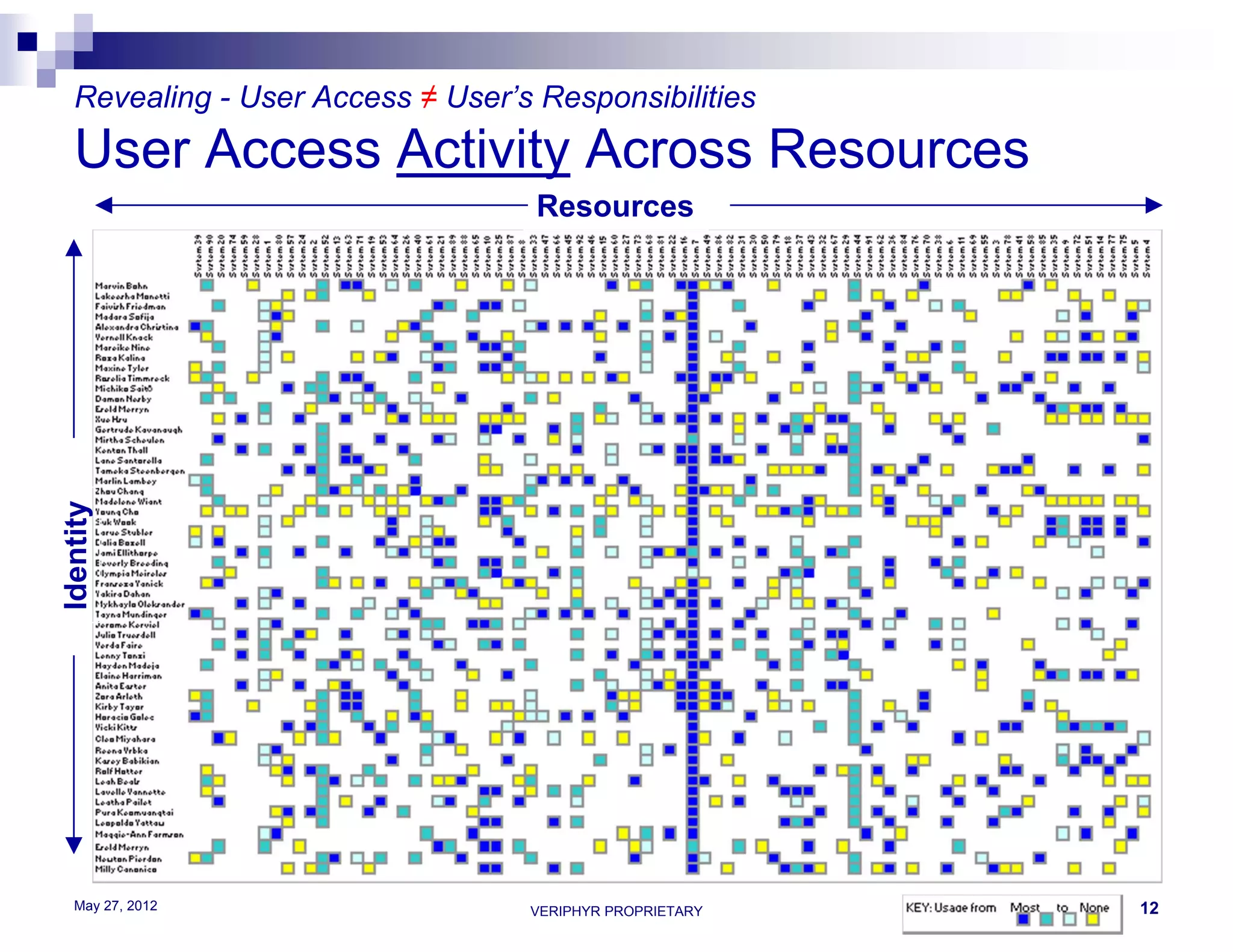
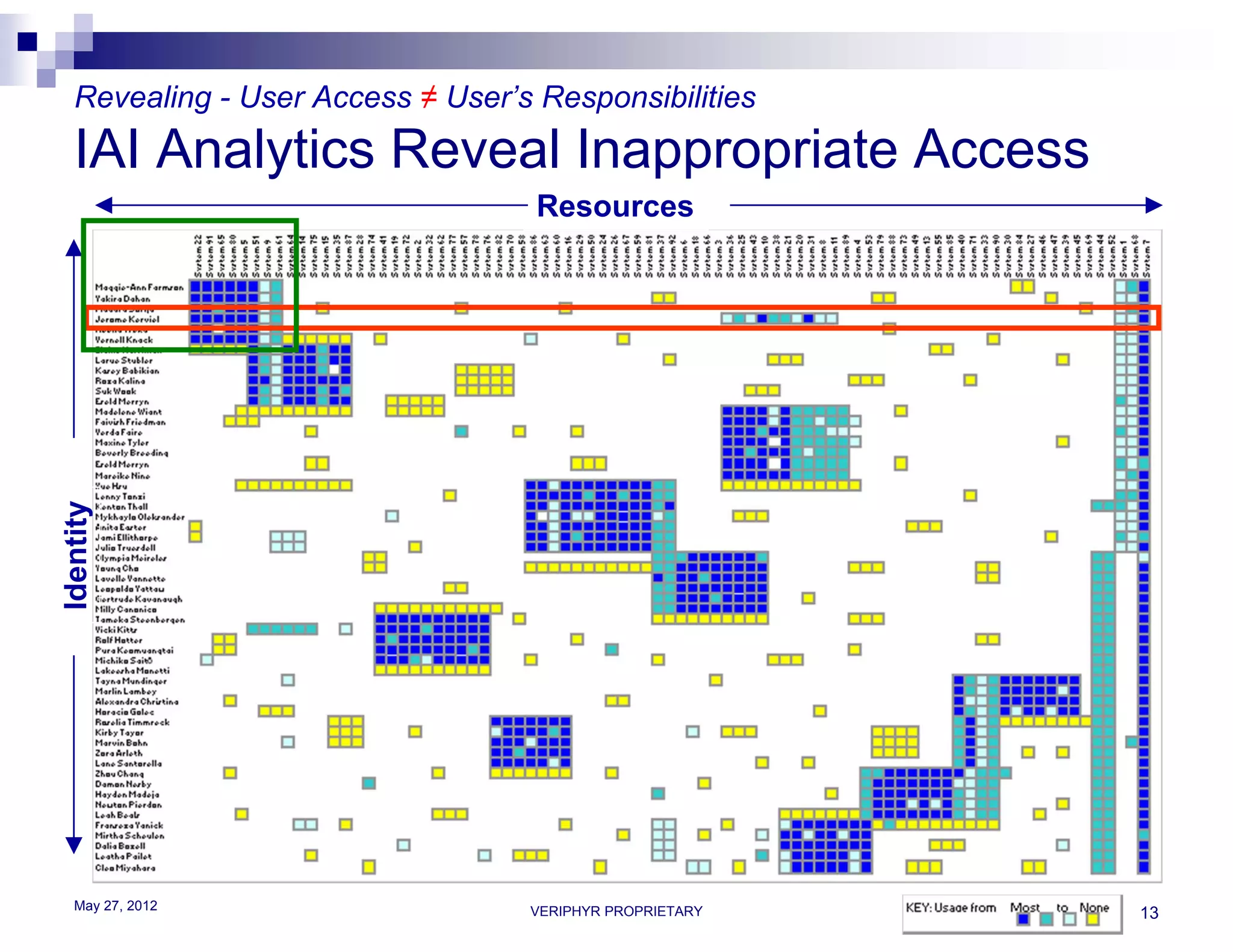
The document discusses user access governance and compliance challenges in the cloud. It notes that cloud computing shifts ownership and control of resources to multiple independent providers. This makes it important to build or contract identity and access management (IAM) services that work across cloud vendors, and to use identity and access intelligence (IAI) to analyze user access and activity across different cloud resource types. IAI can help identify when user access does not match job responsibilities, revealing inappropriate access. The document promotes contacting the author for more information on IAM as a service and IAI solutions.