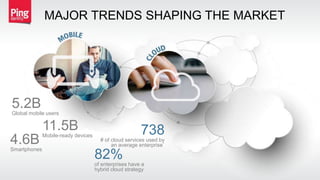
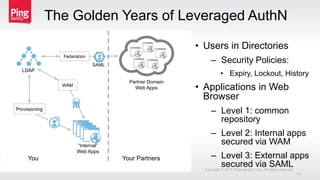
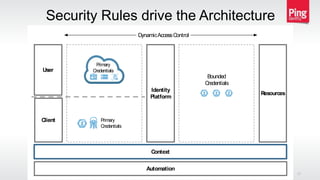
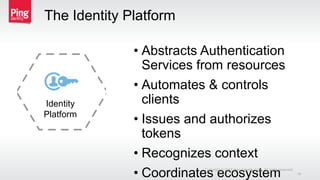
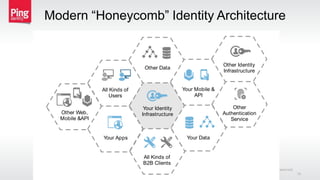
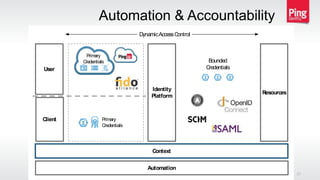
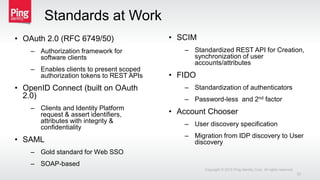
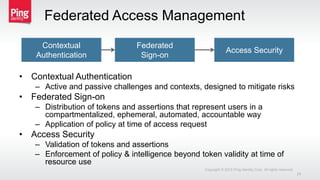
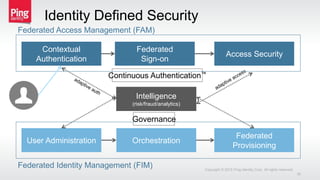
The document discusses a new approach to securing enterprise identity, emphasizing the trends towards cloud and mobile technologies, as well as the importance of modern security design principles such as compartmentalization, ephemerality, automation, and accountability. It highlights the risks associated with compromised credentials, the necessity for robust identity architectures, and the use of standards like OAuth 2.0 and OpenID Connect for secure access management. The recommendations urge organizations to address immediate risks and develop long-term strategies for identity and access security.