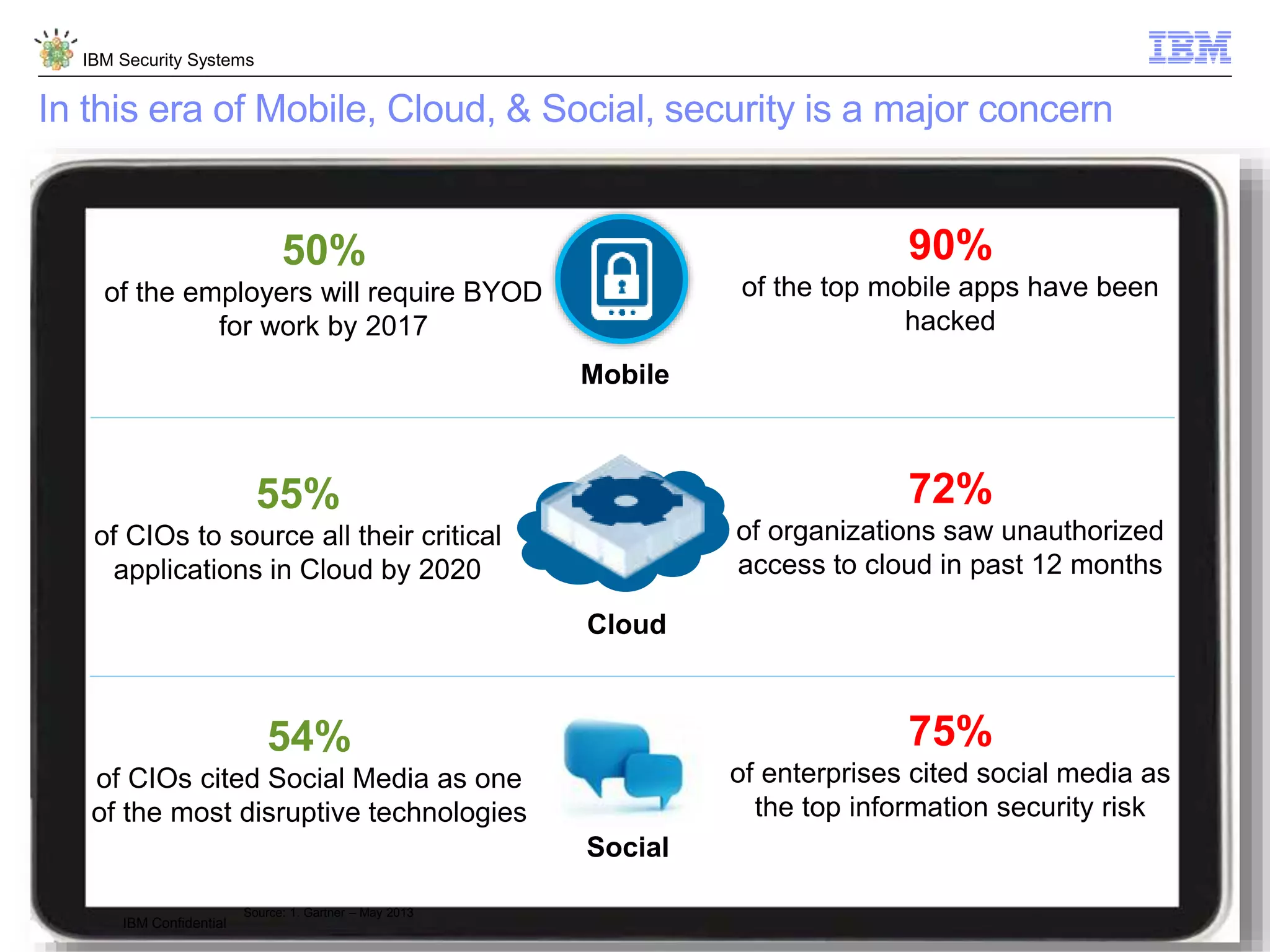
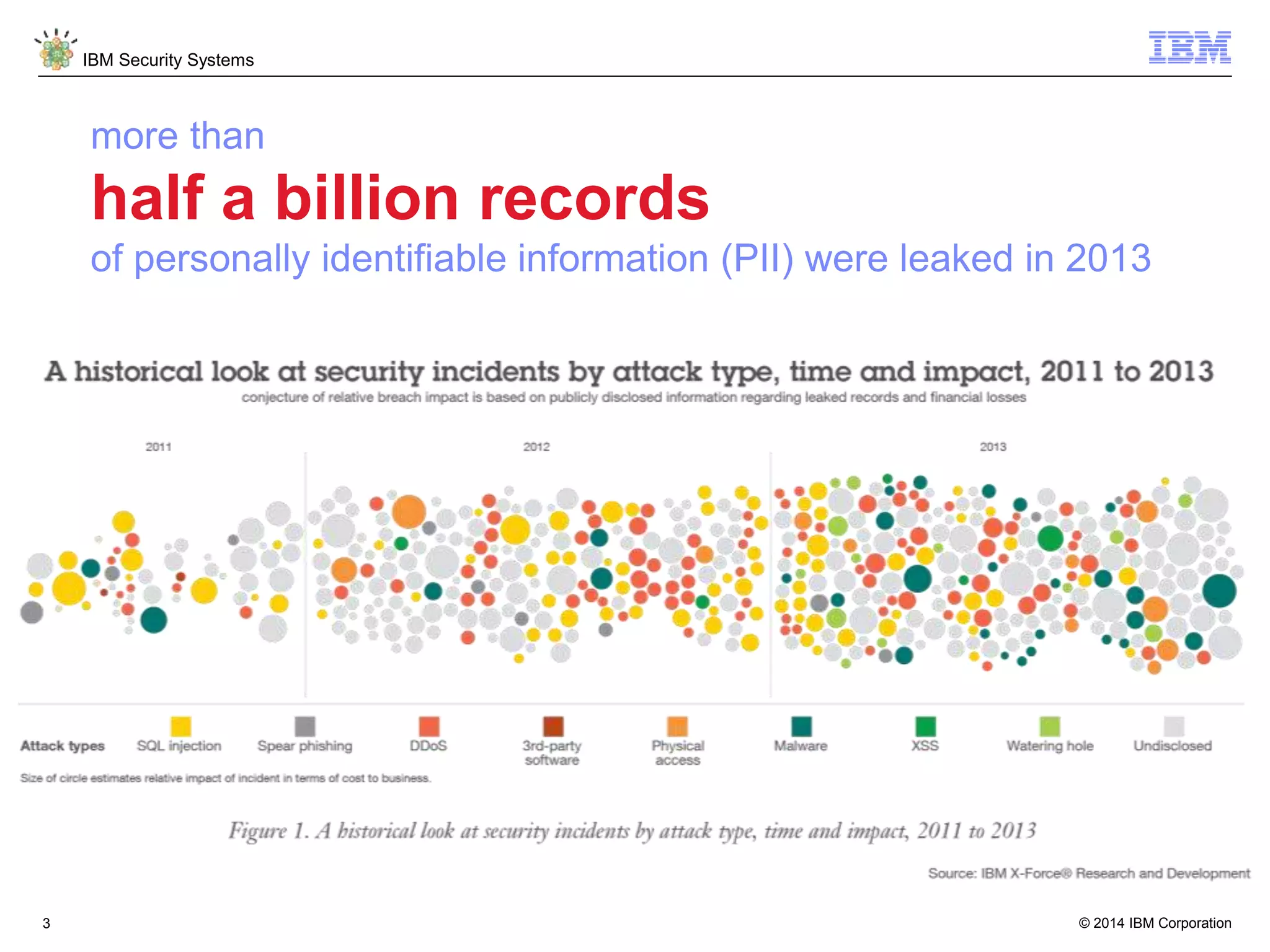
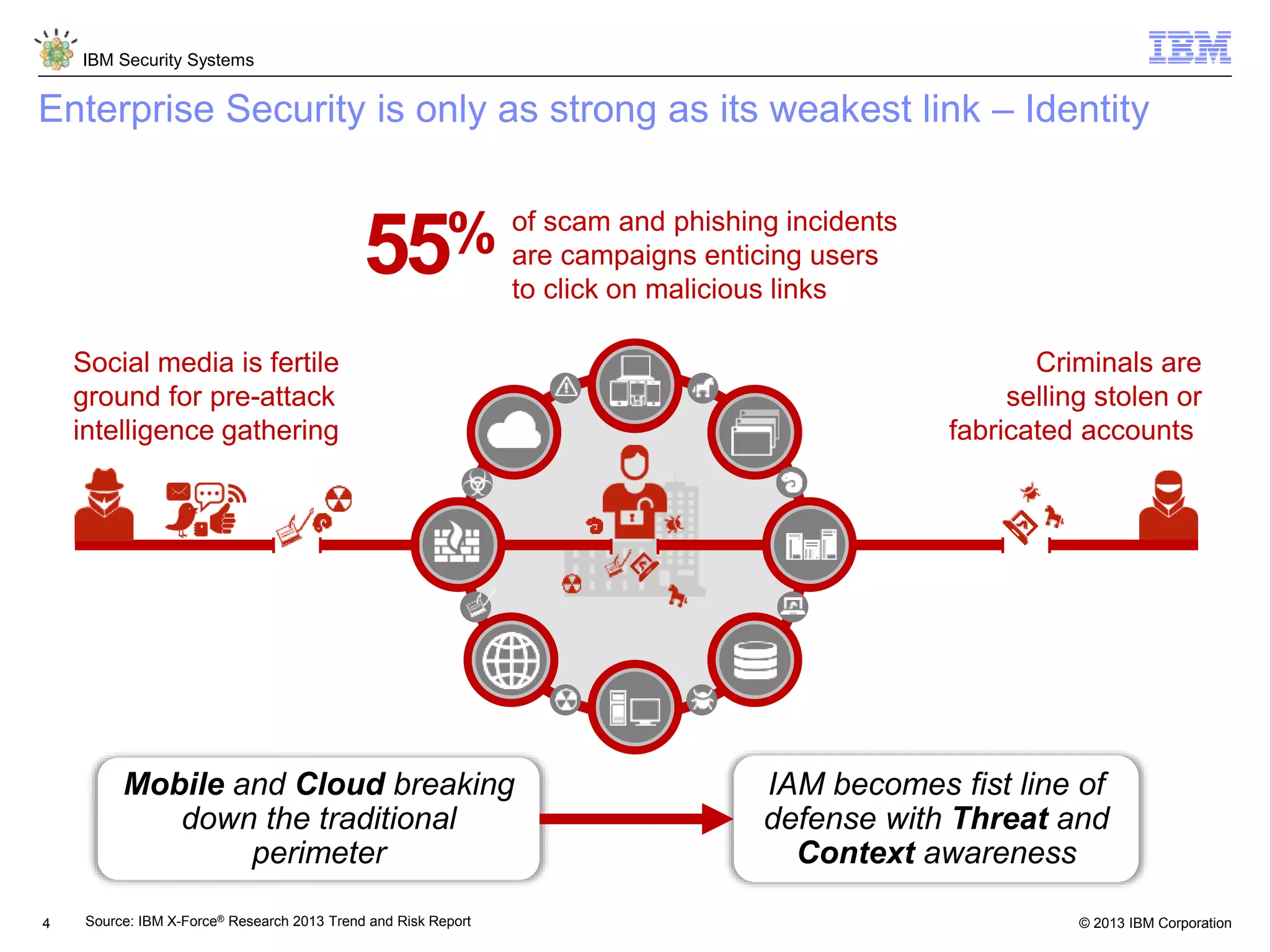
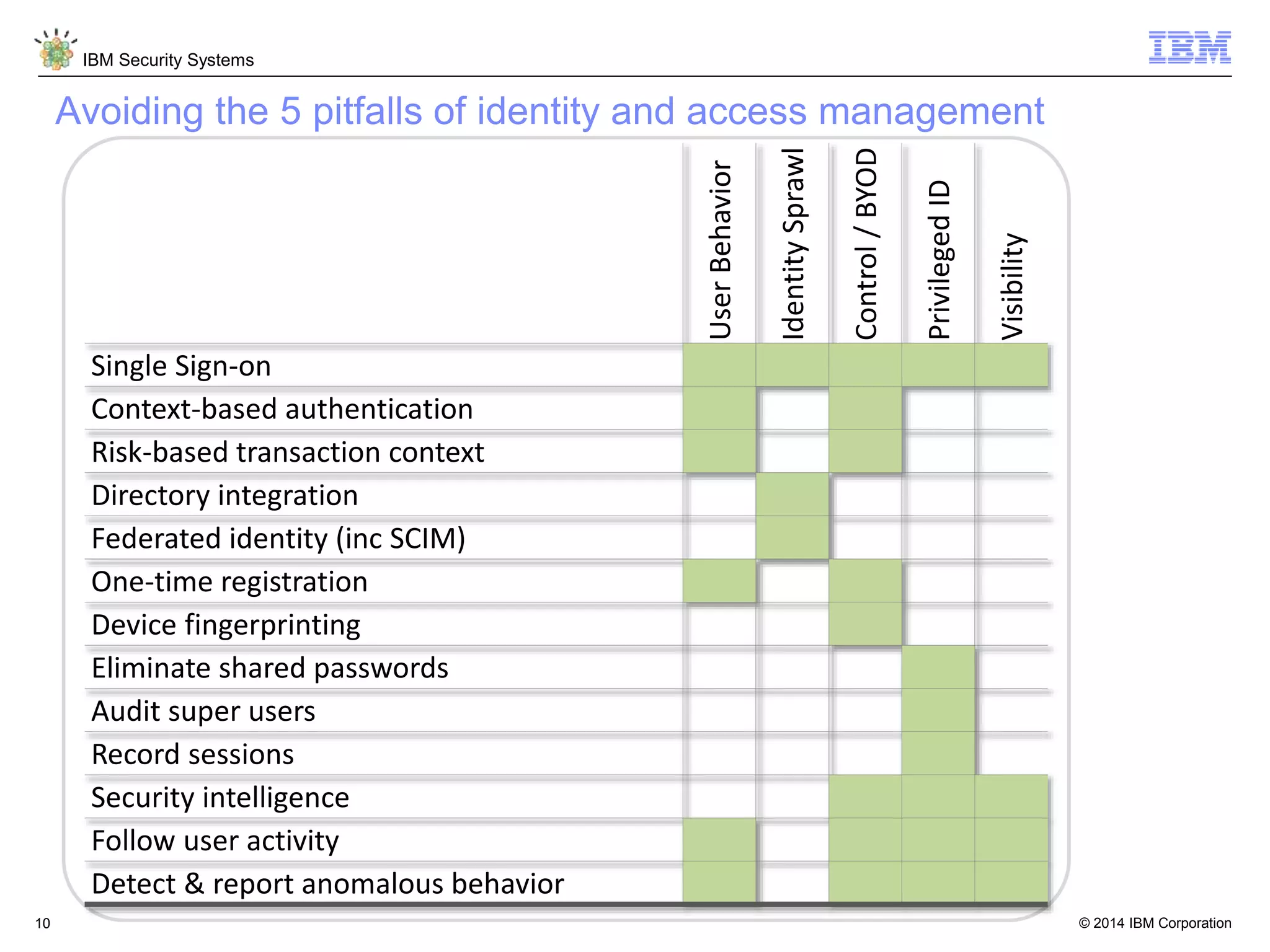
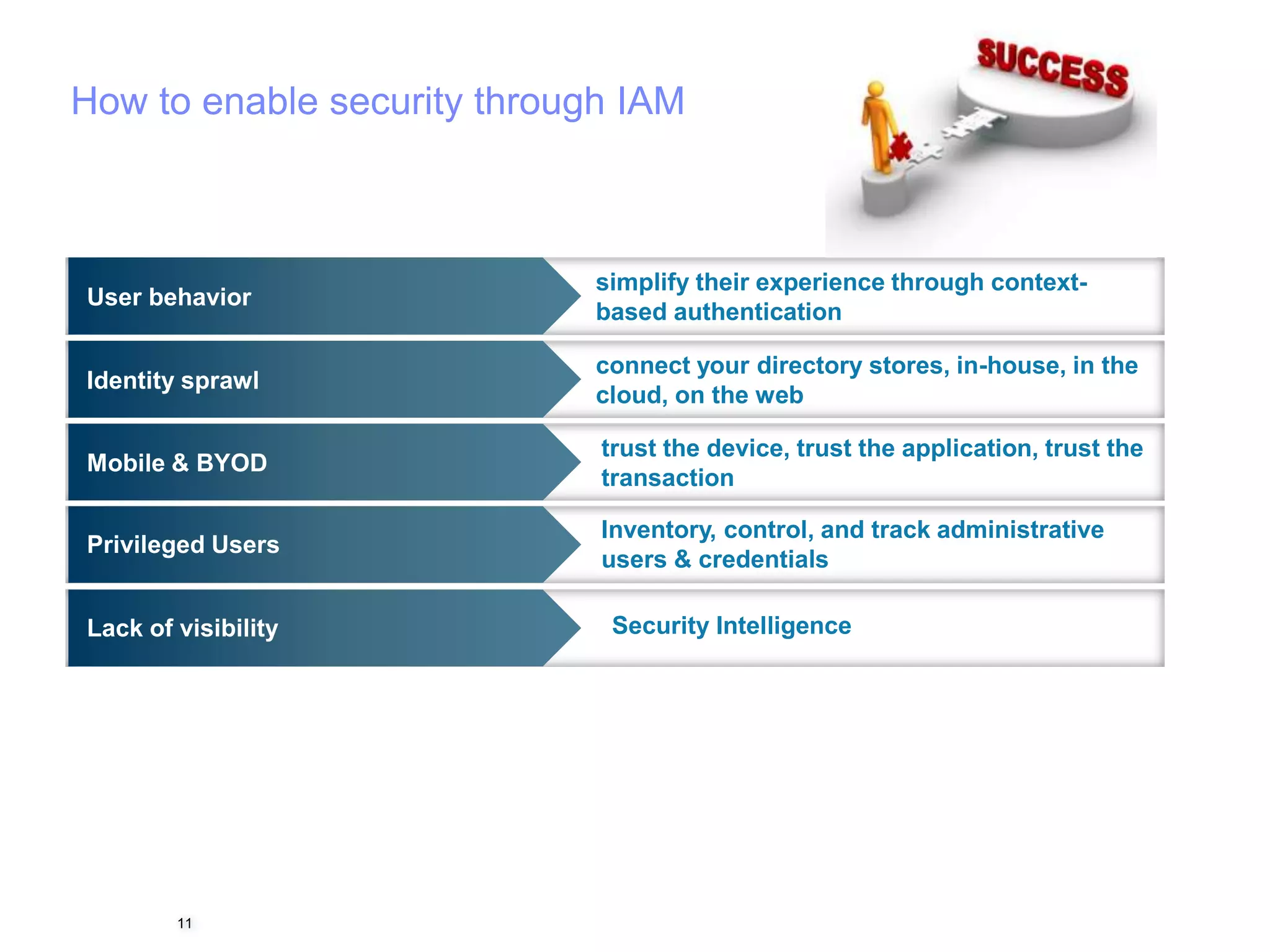
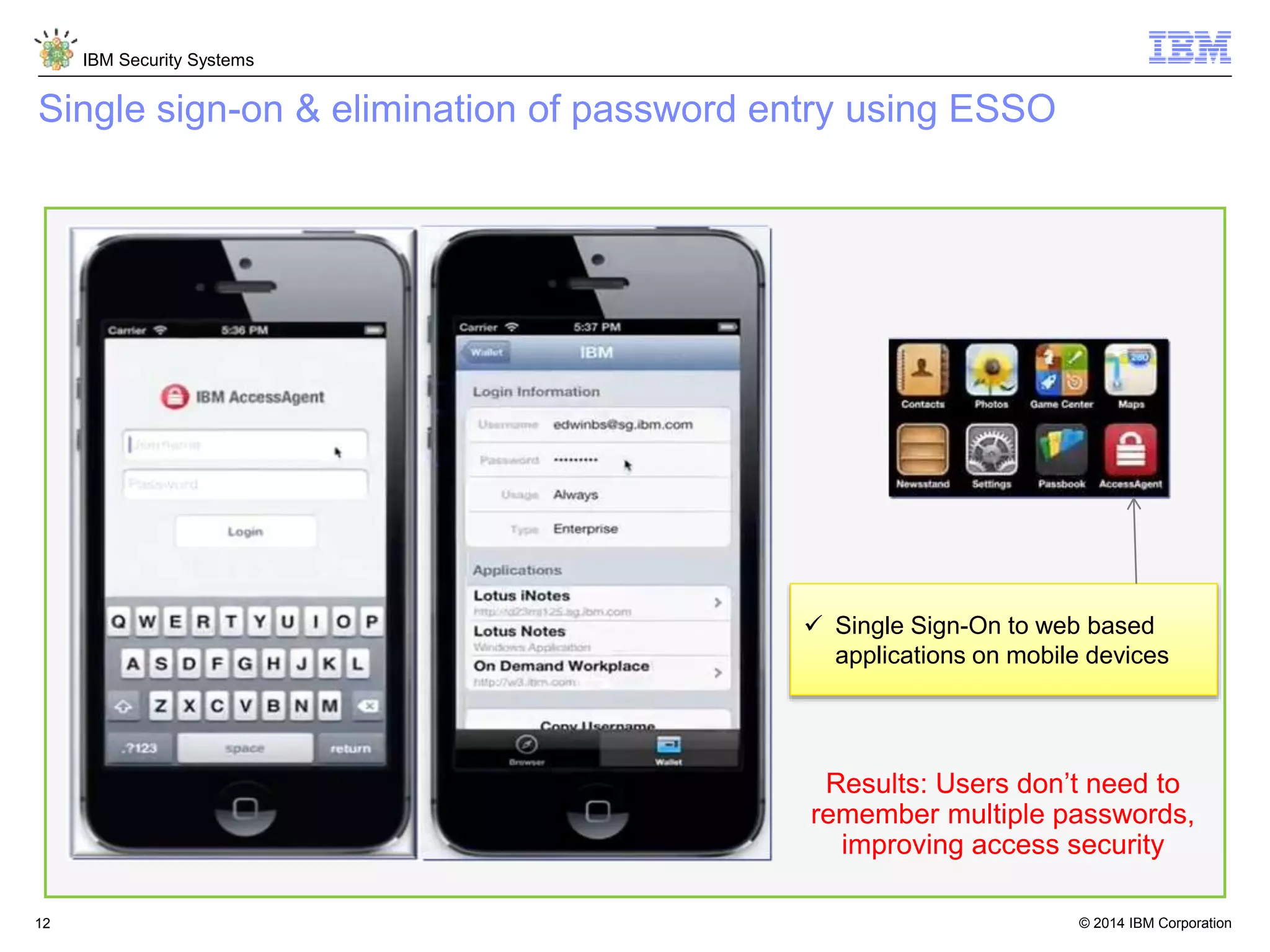
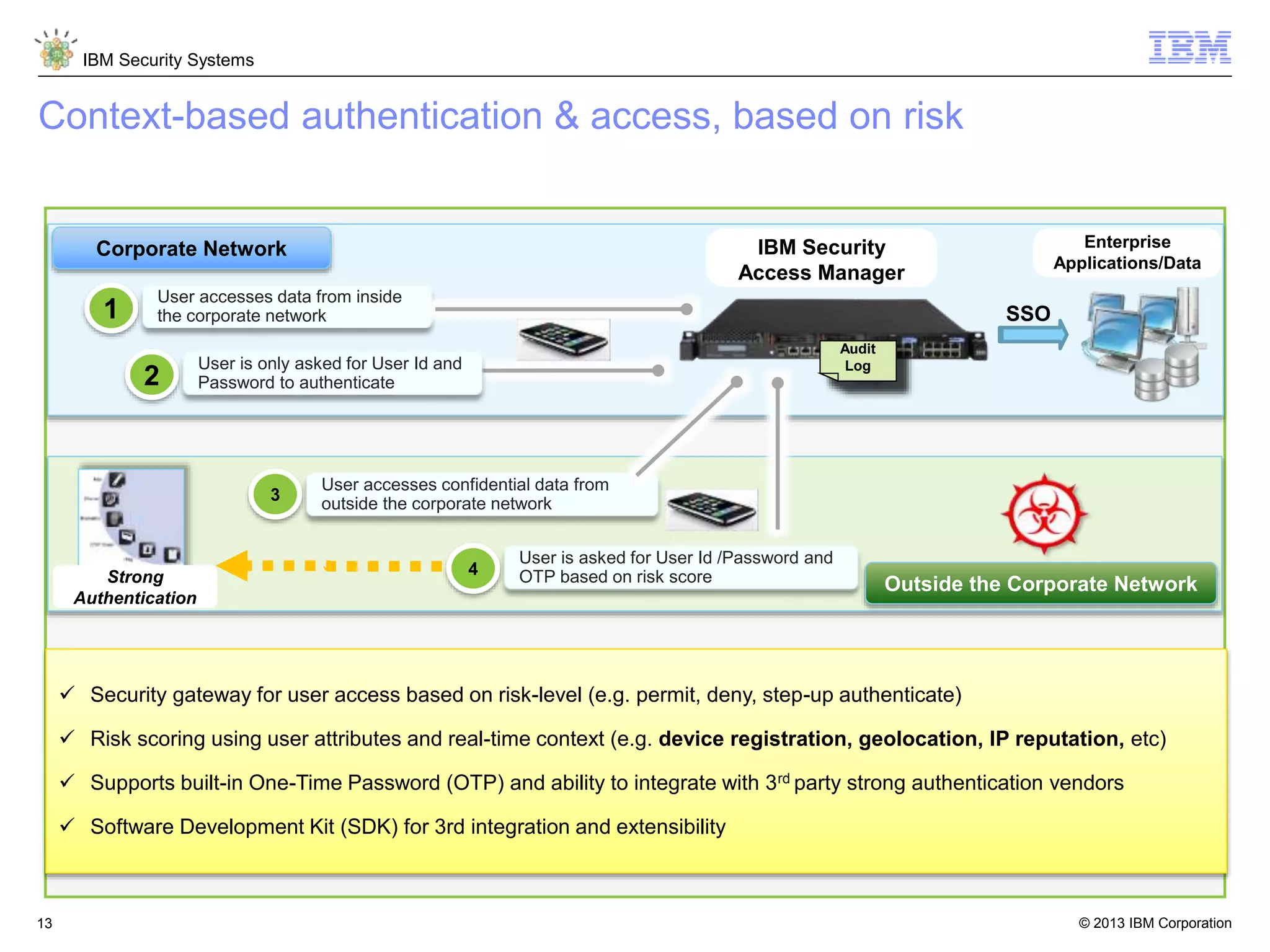
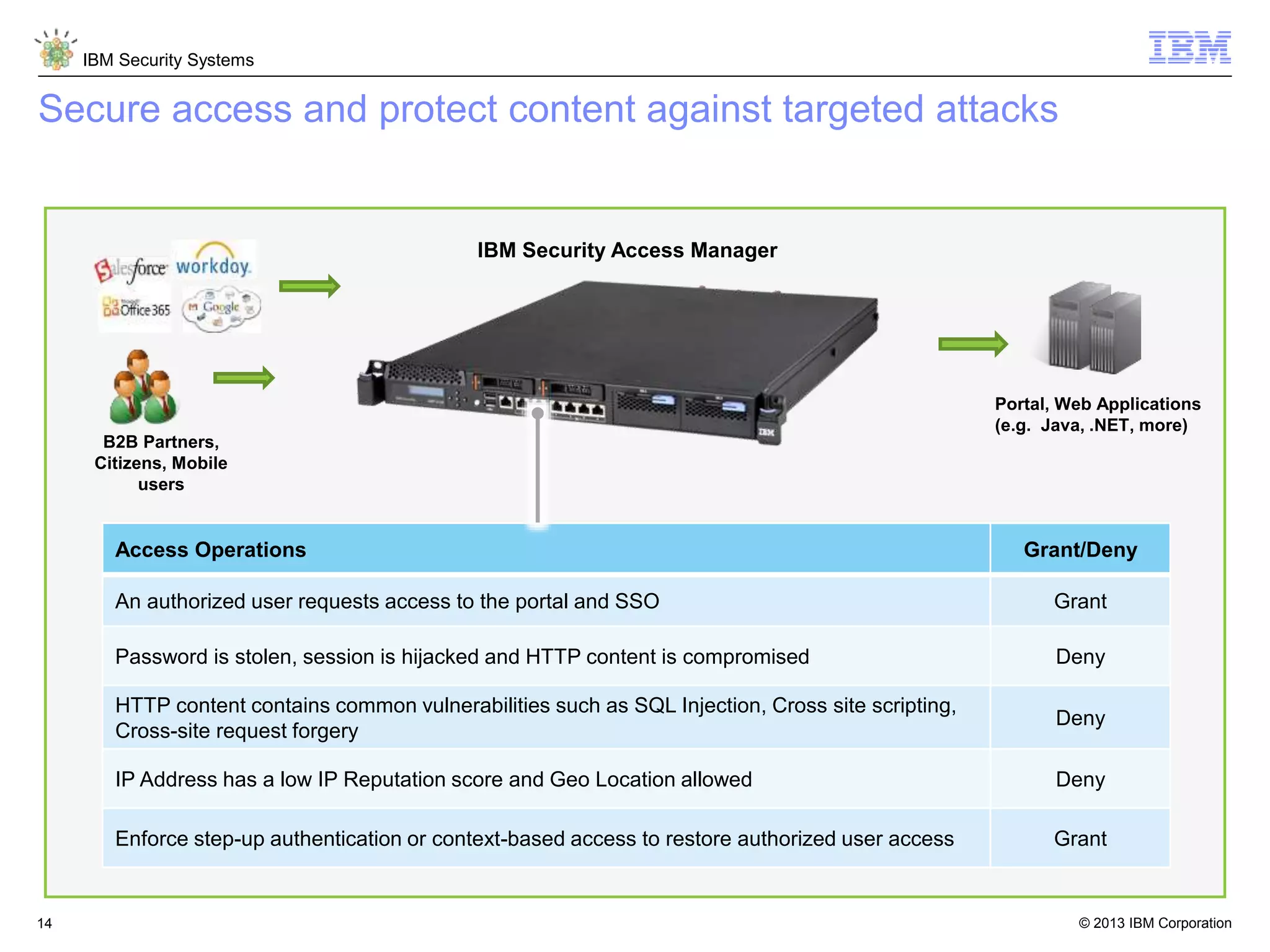
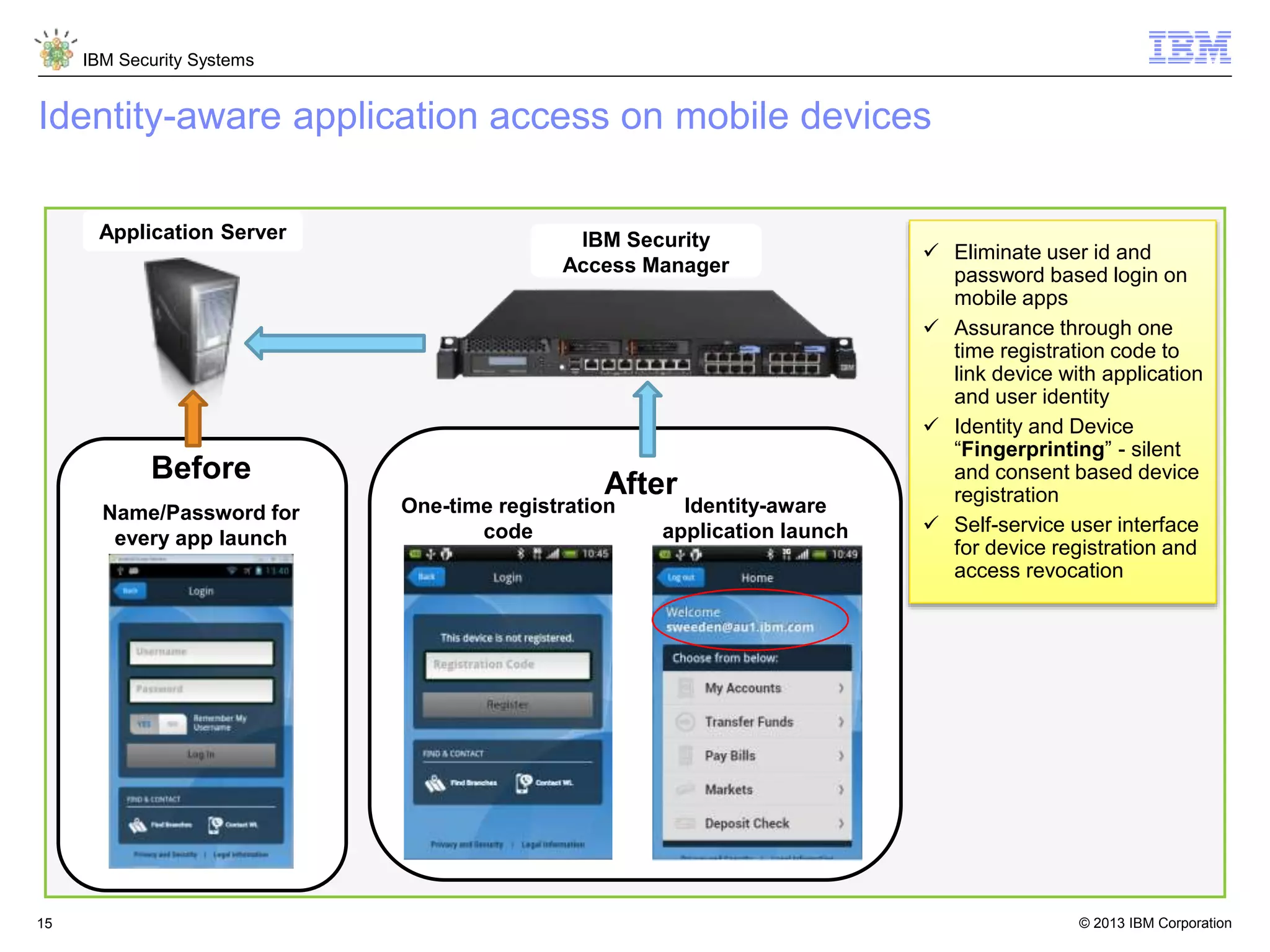
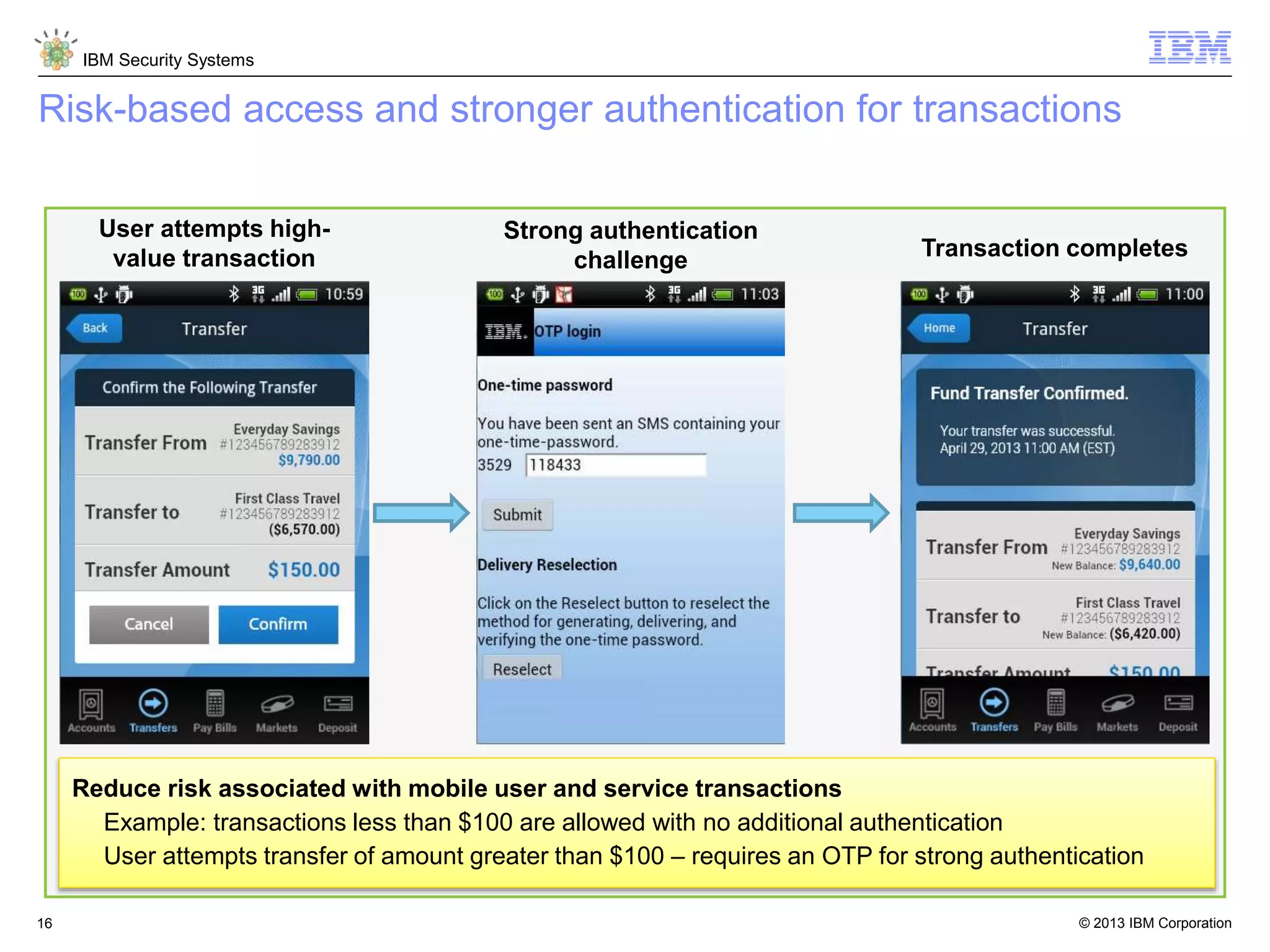
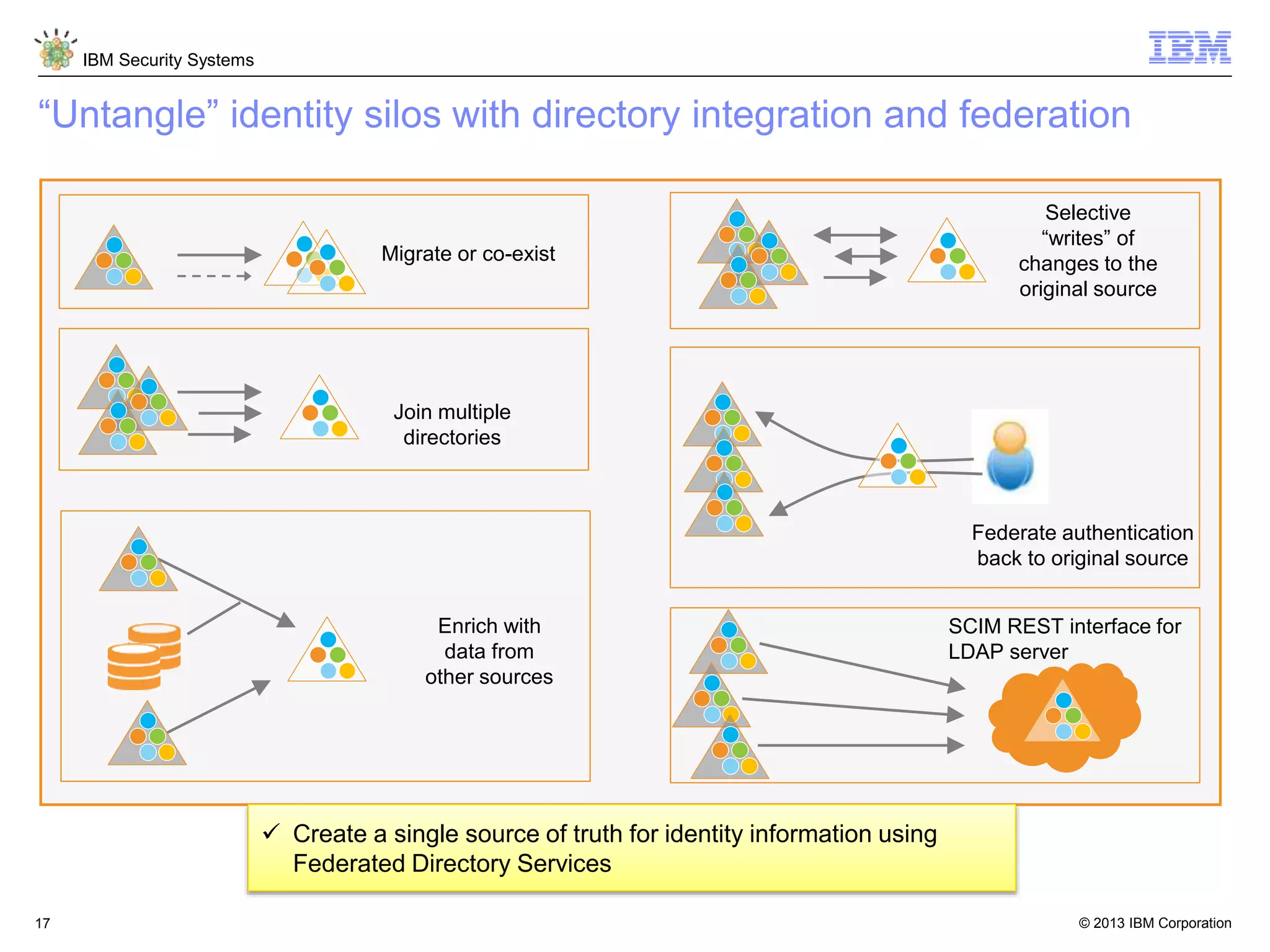
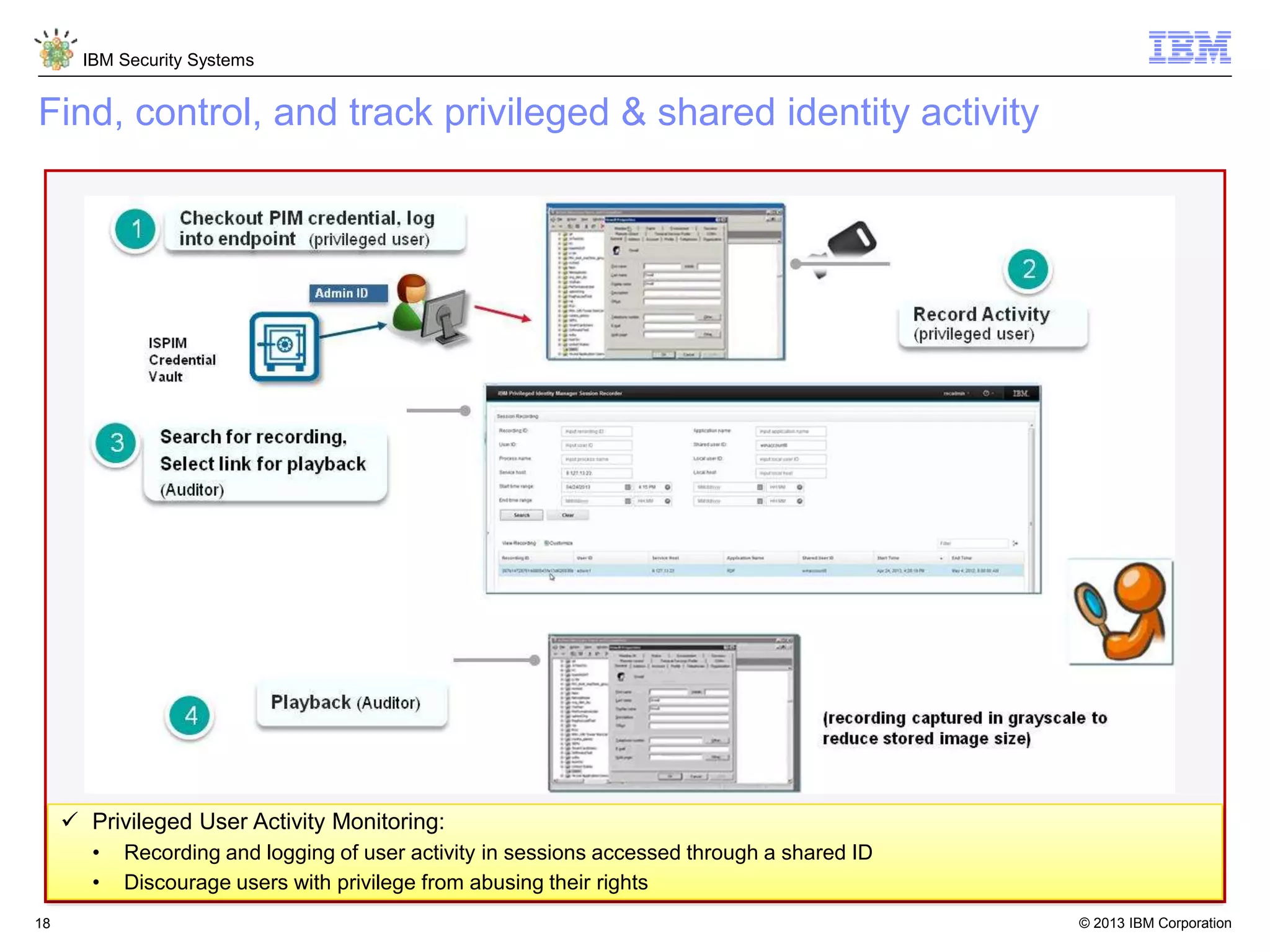
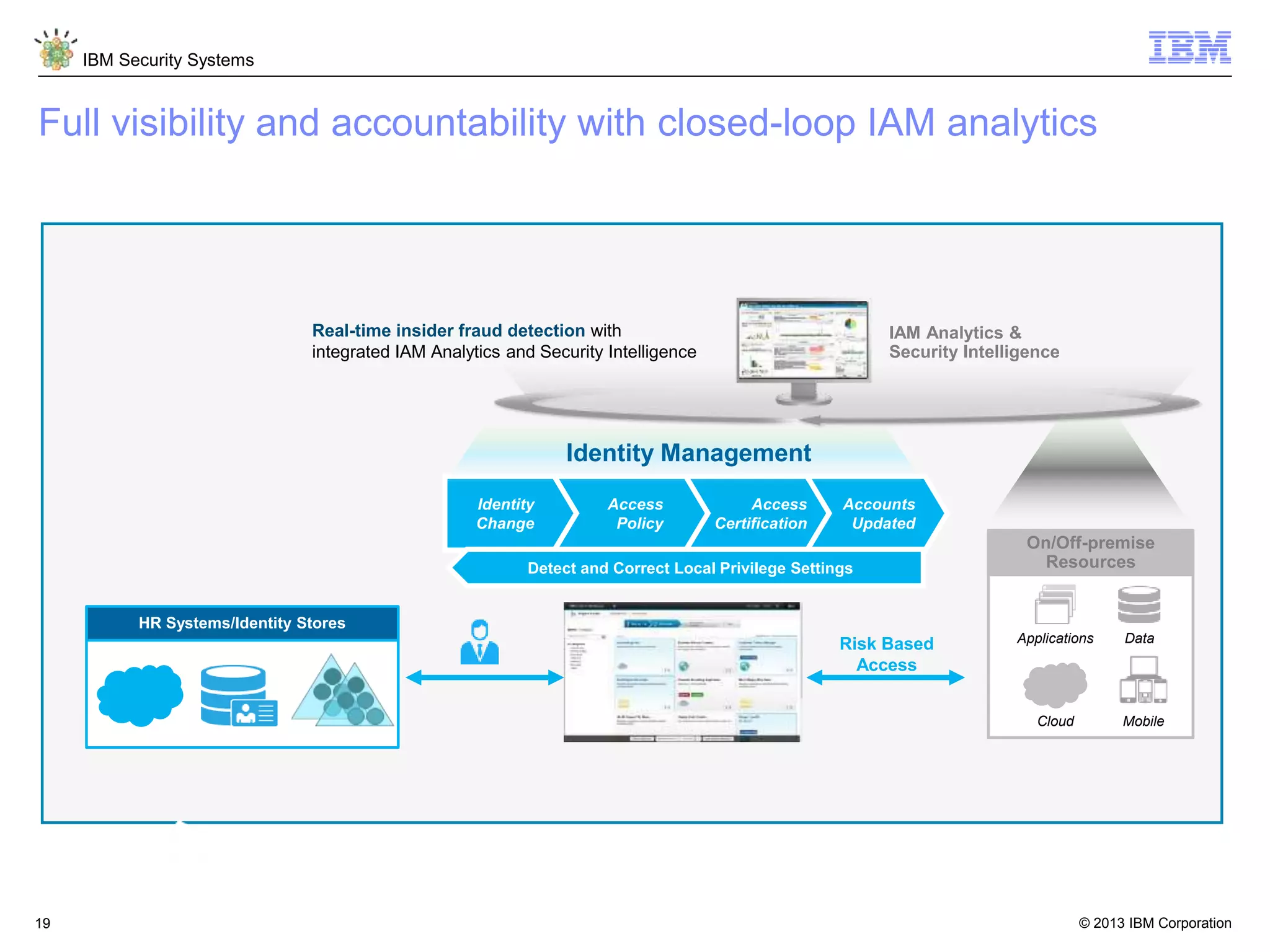
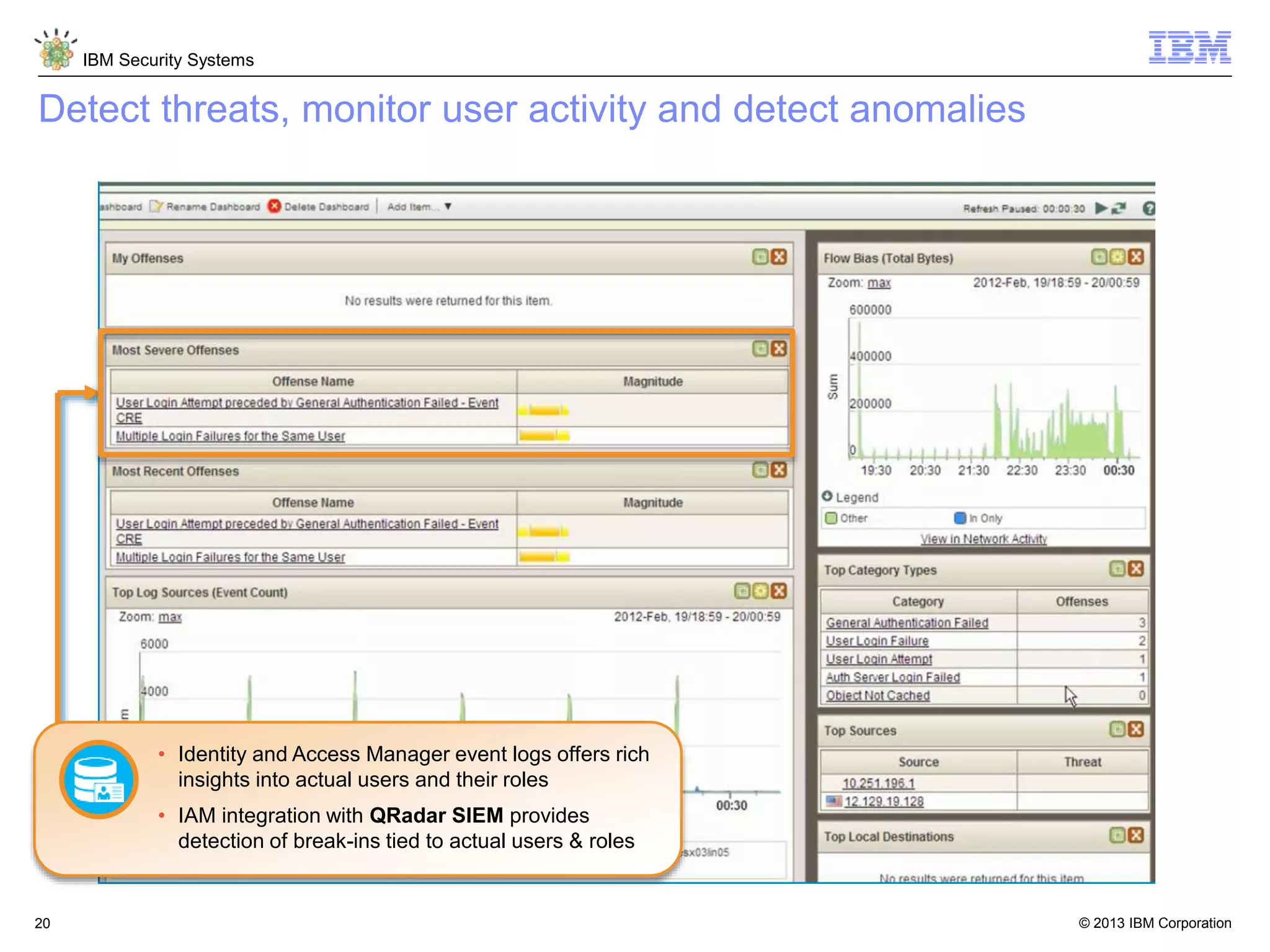
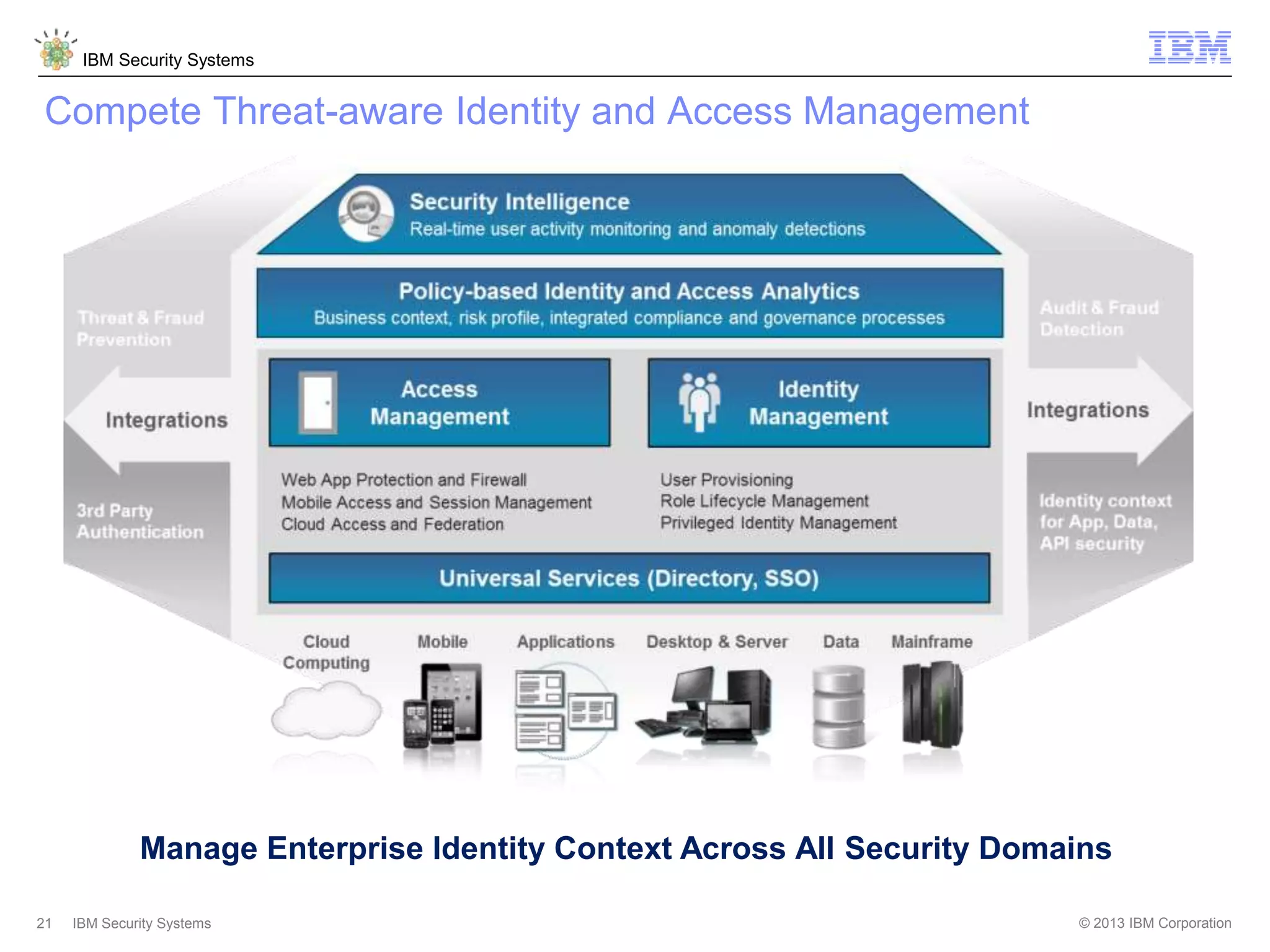
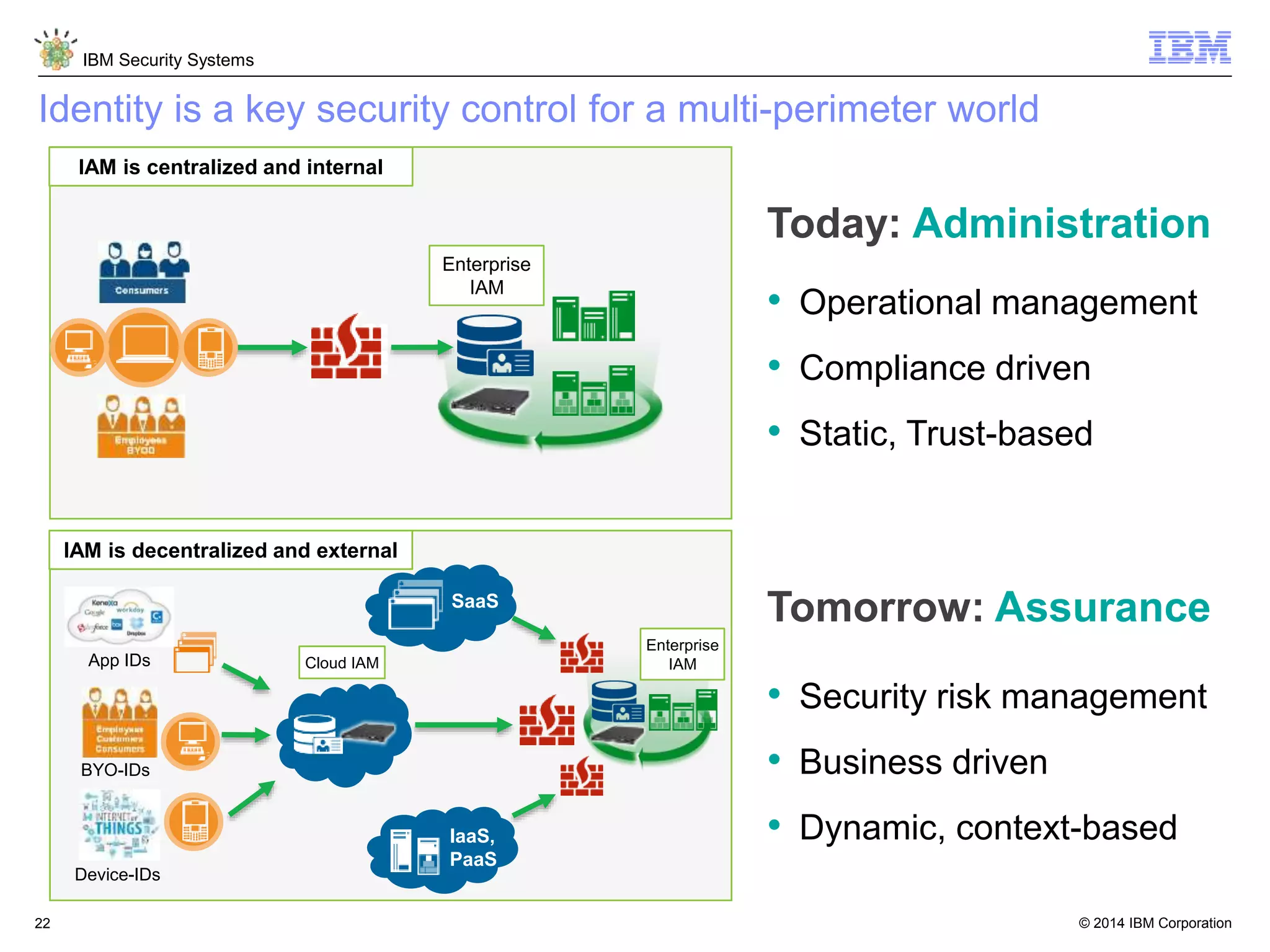
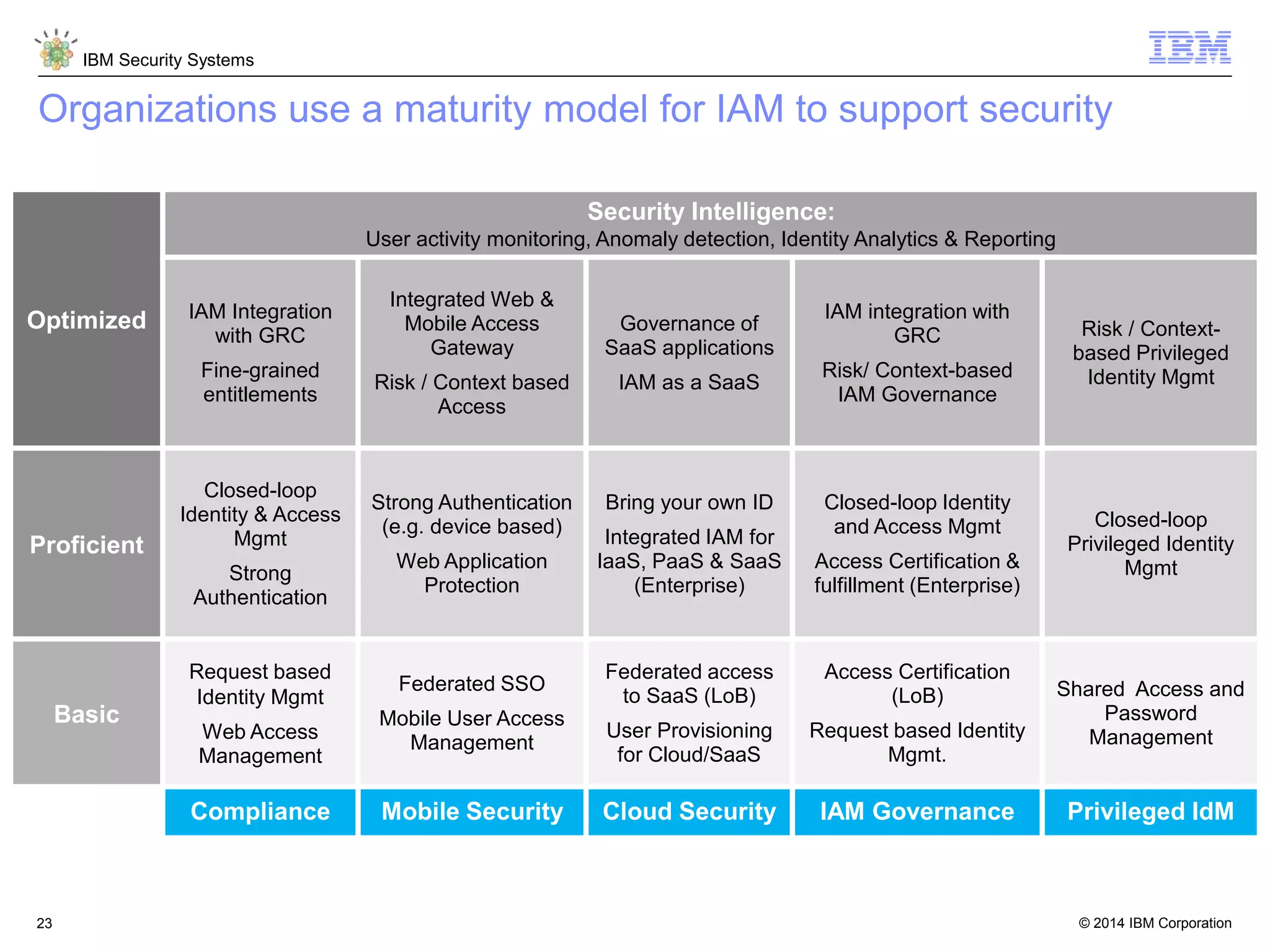
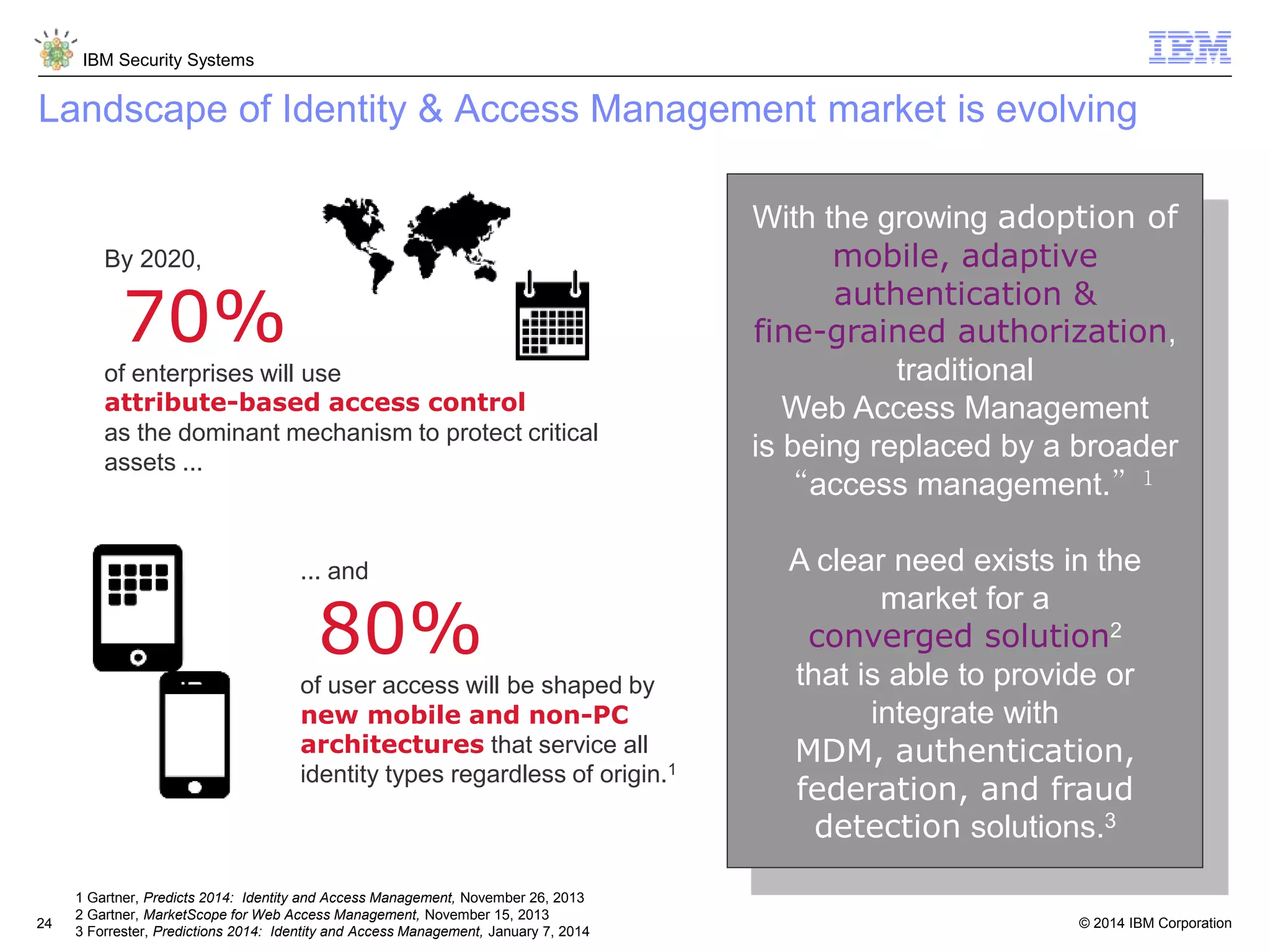
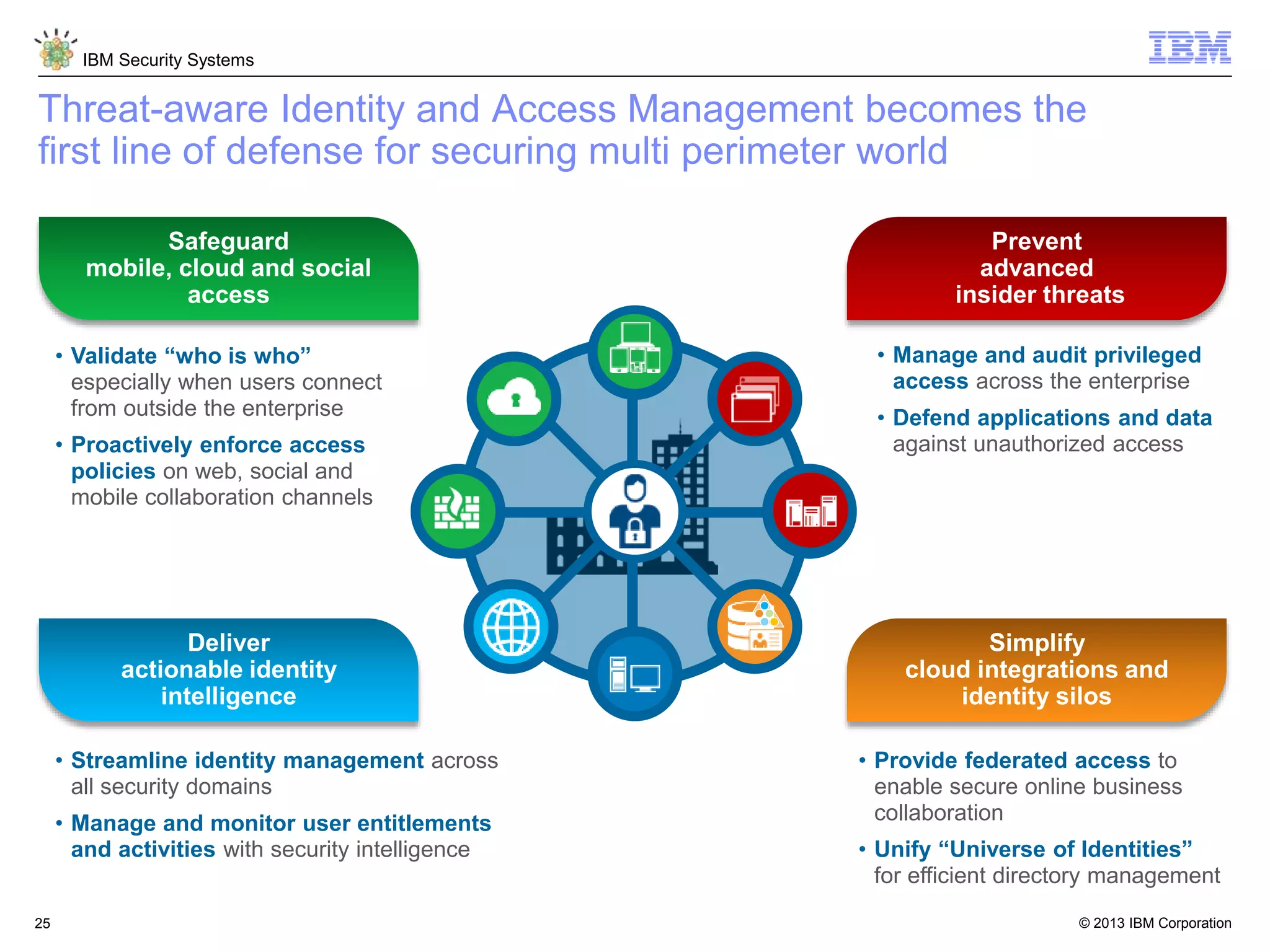
The document discusses 5 reasons why identity and access management (IAM) solutions fail. It identifies human factors like weak passwords, identity sprawl across multiple systems, losing control of devices in bring-your-own models, threats from rogue privileged insiders, and lack of visibility into user activity as reasons for IAM failure. It provides recommendations to avoid these pitfalls through approaches like single sign-on, context-based authentication, risk-based access controls, directory integration, and security intelligence for monitoring. The goal is to enable secure access across mobile, cloud and social environments through an optimized IAM strategy.