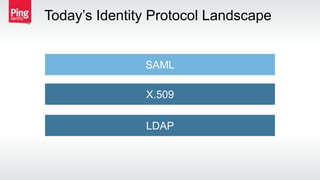
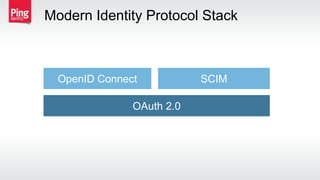
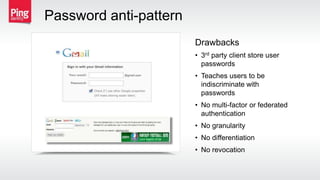
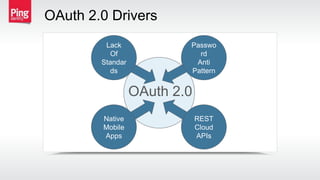
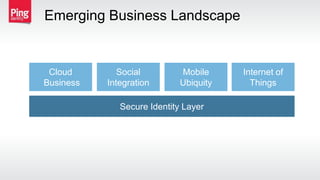
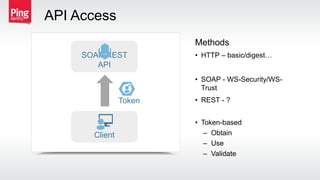
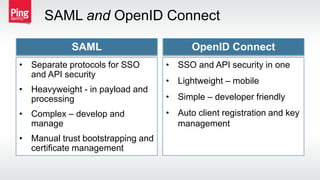
The document discusses how identity management protocols like OAuth 2.0 and OpenID Connect can help connect physical devices and systems to digital networks and services by providing scalable identification, authentication, and authorization. It outlines challenges like security at scale and password overuse that these protocols help address. Examples are given of how identity solutions can enable use cases across different industries involving manufacturing, healthcare, automotive, and home automation.