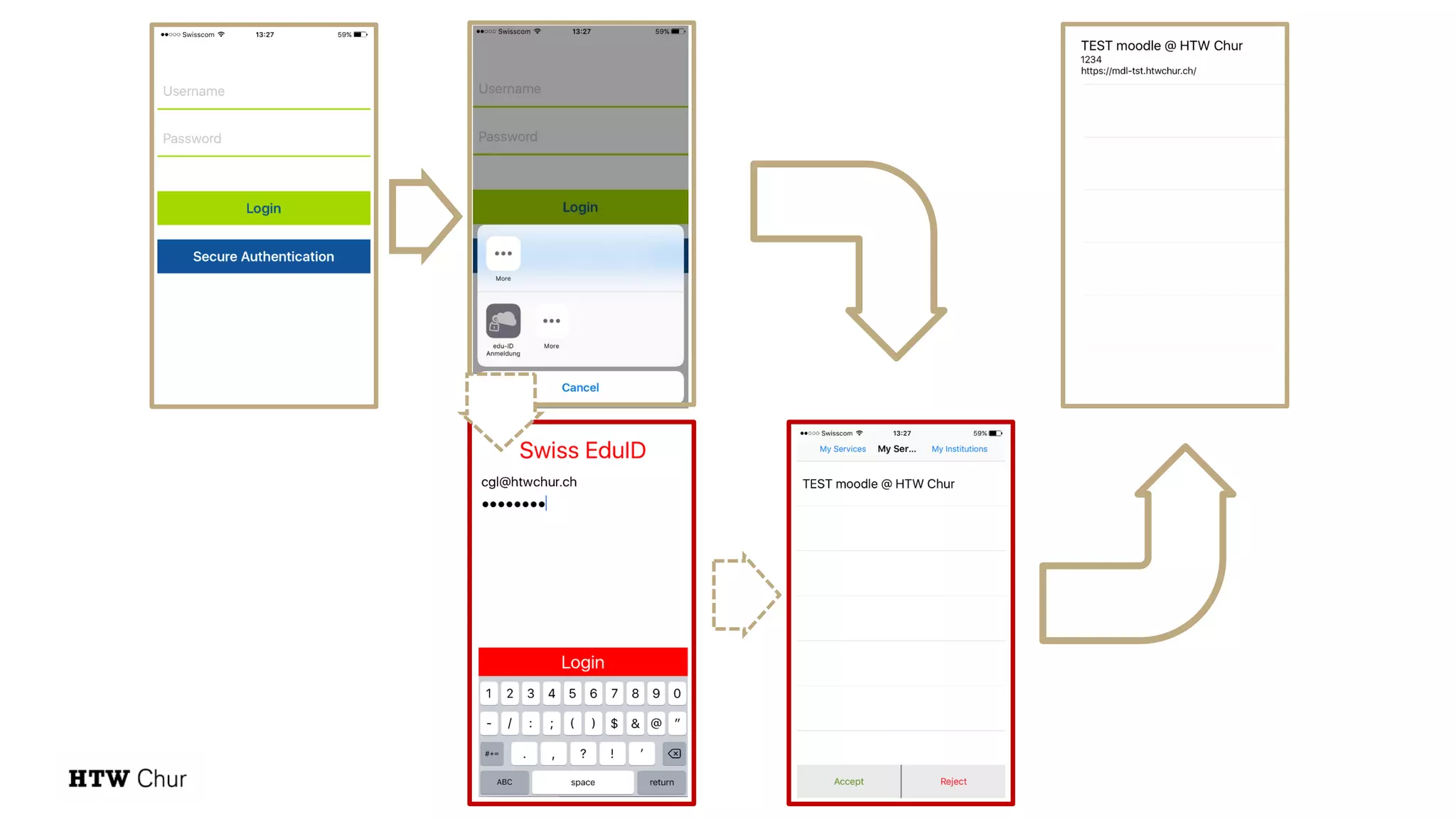
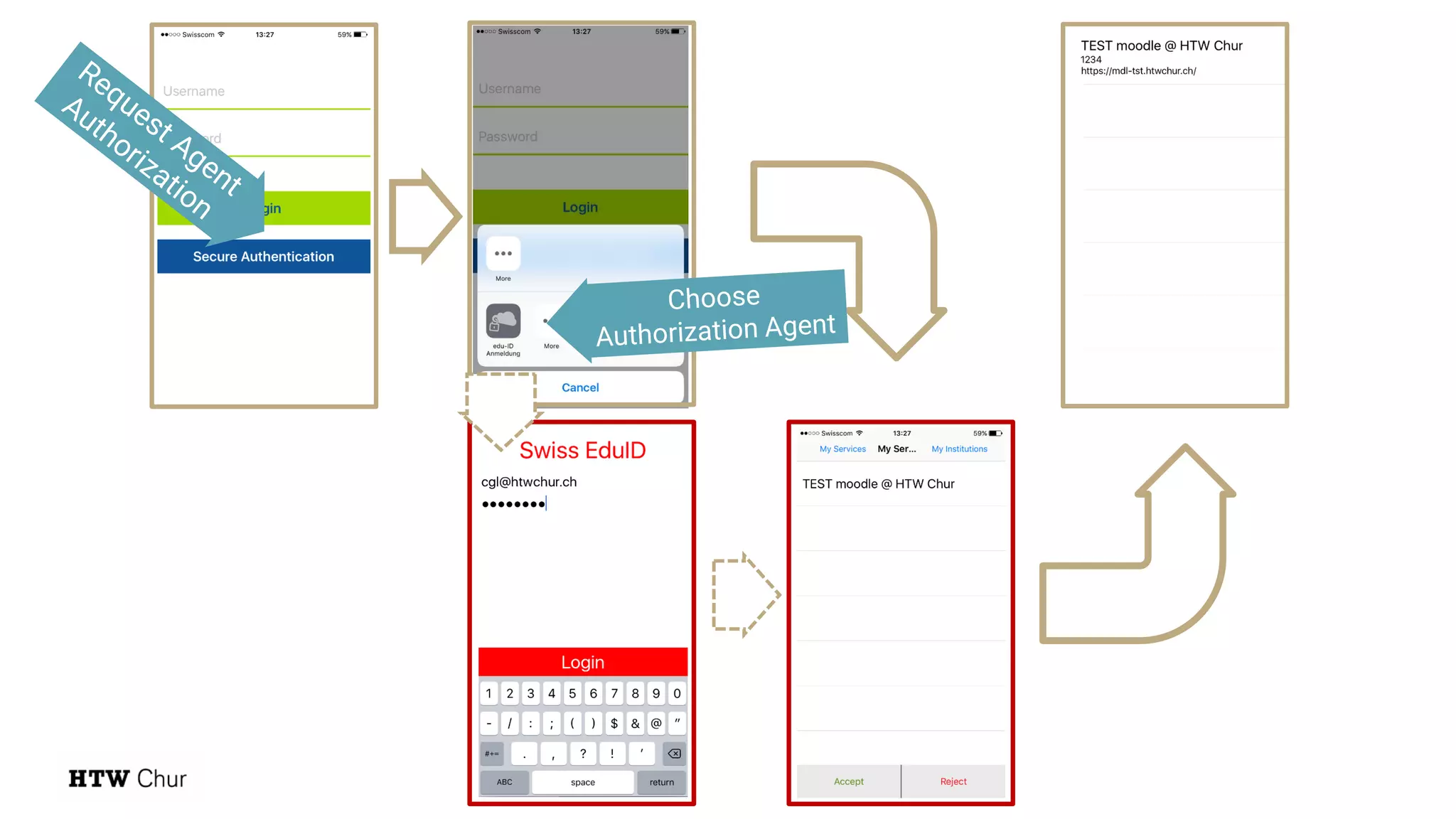
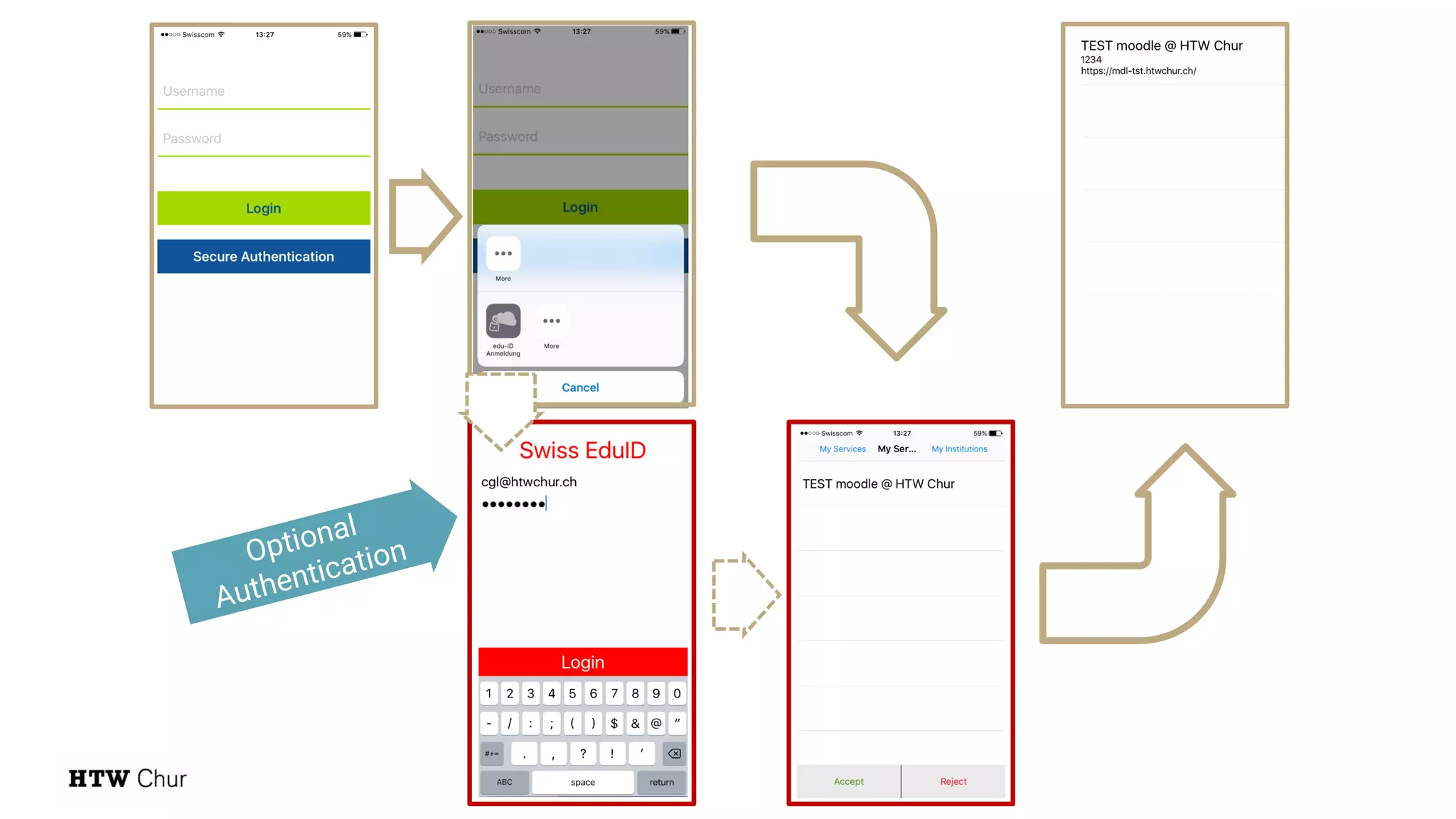
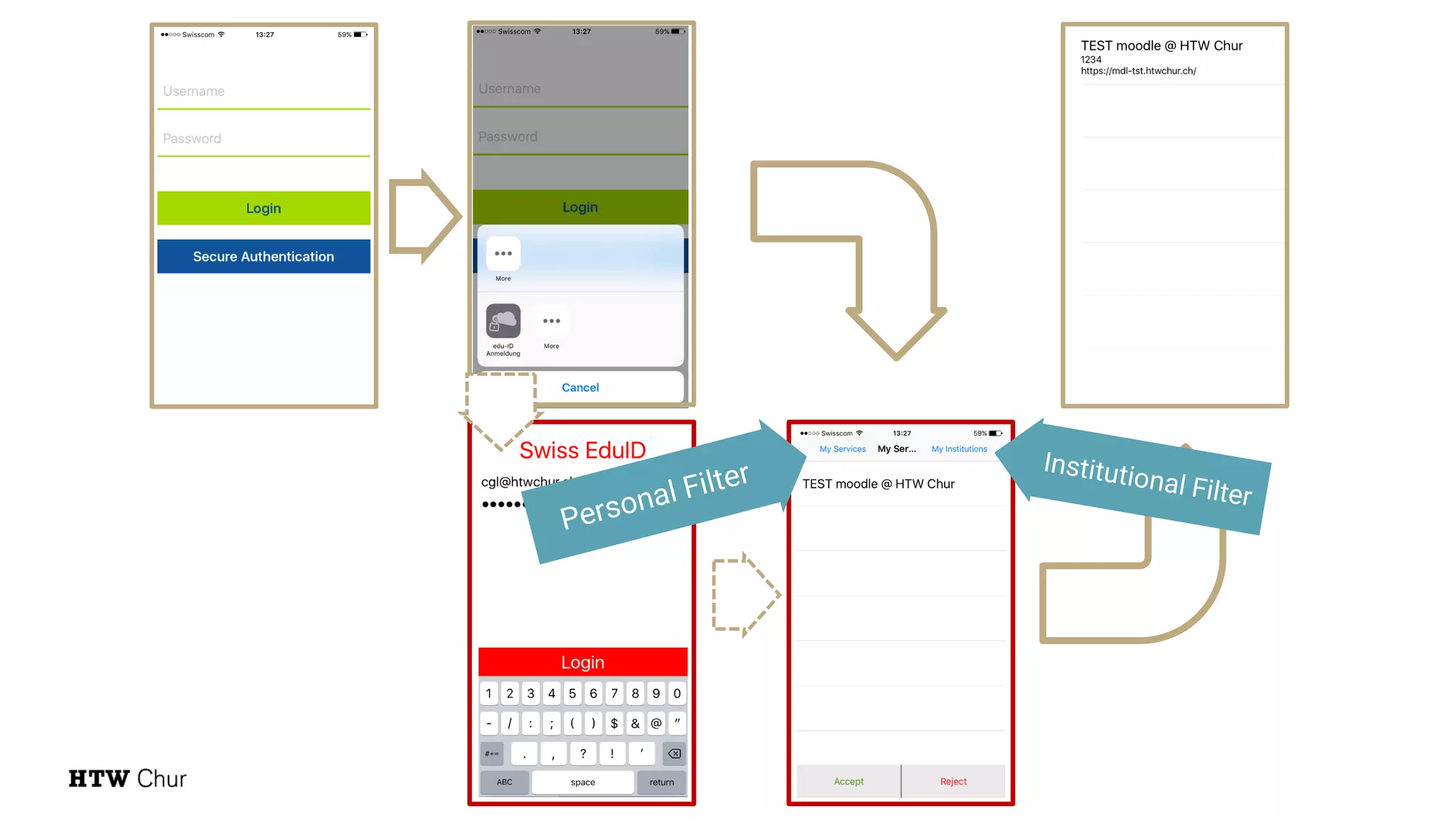
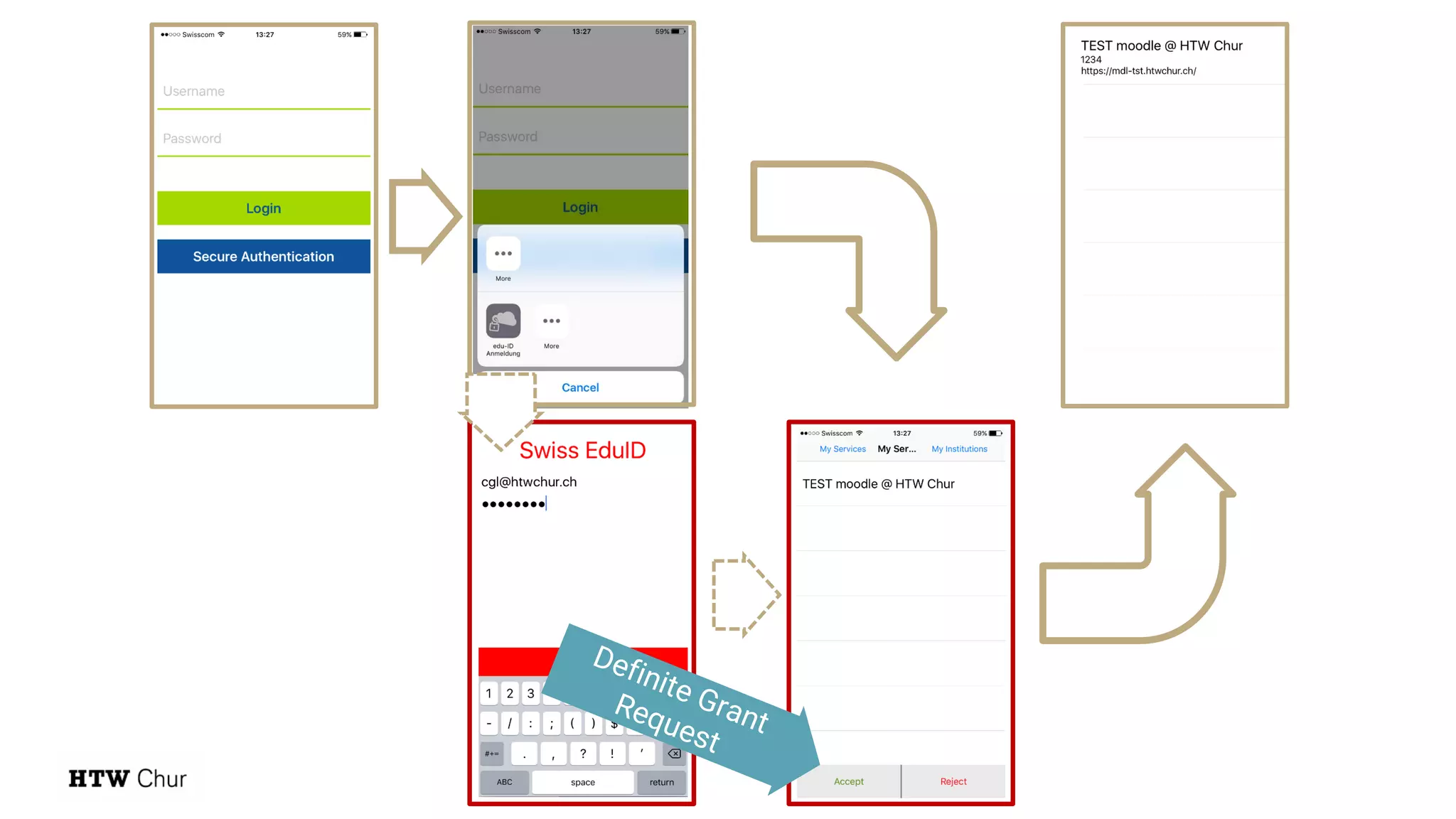
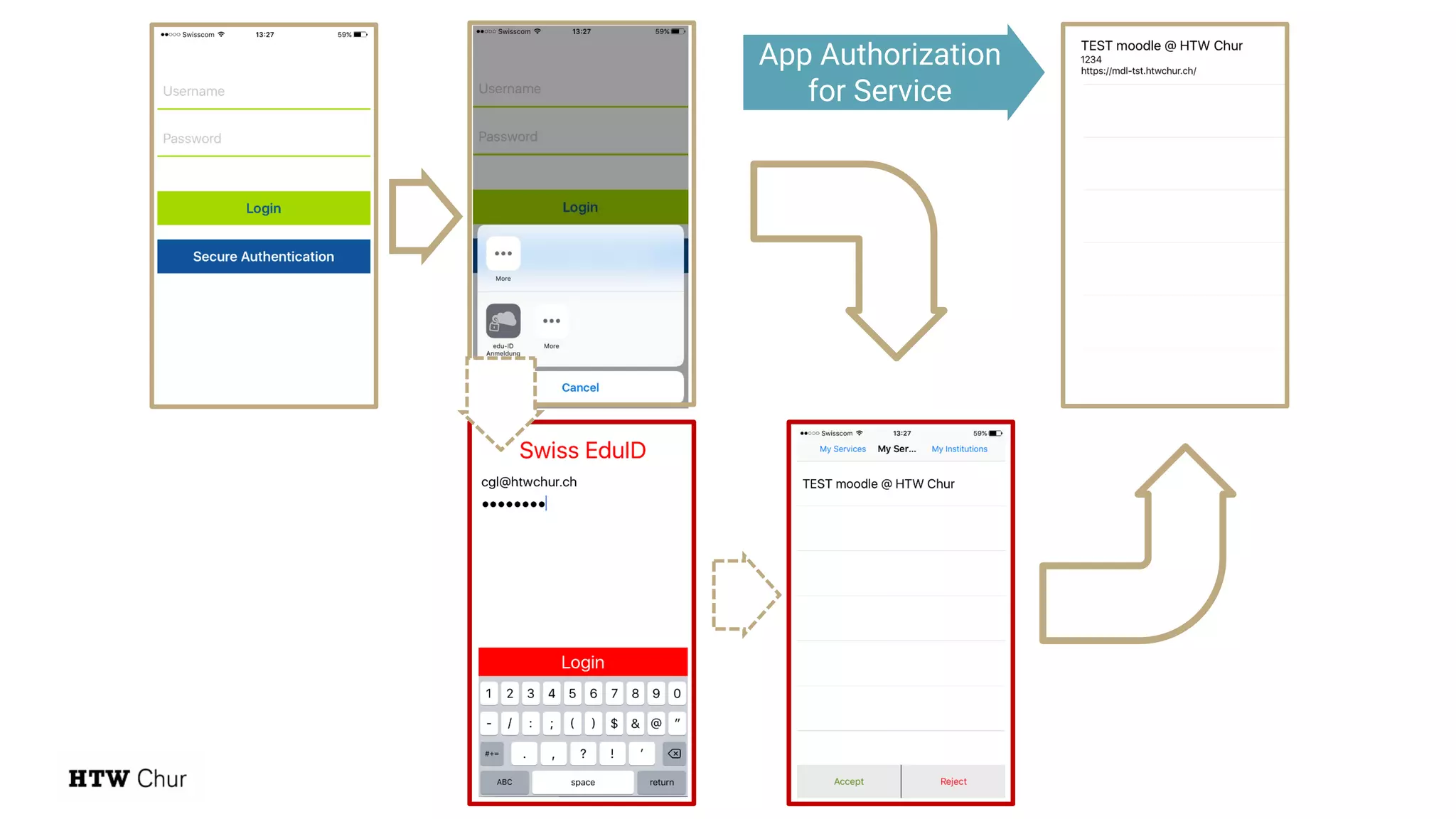
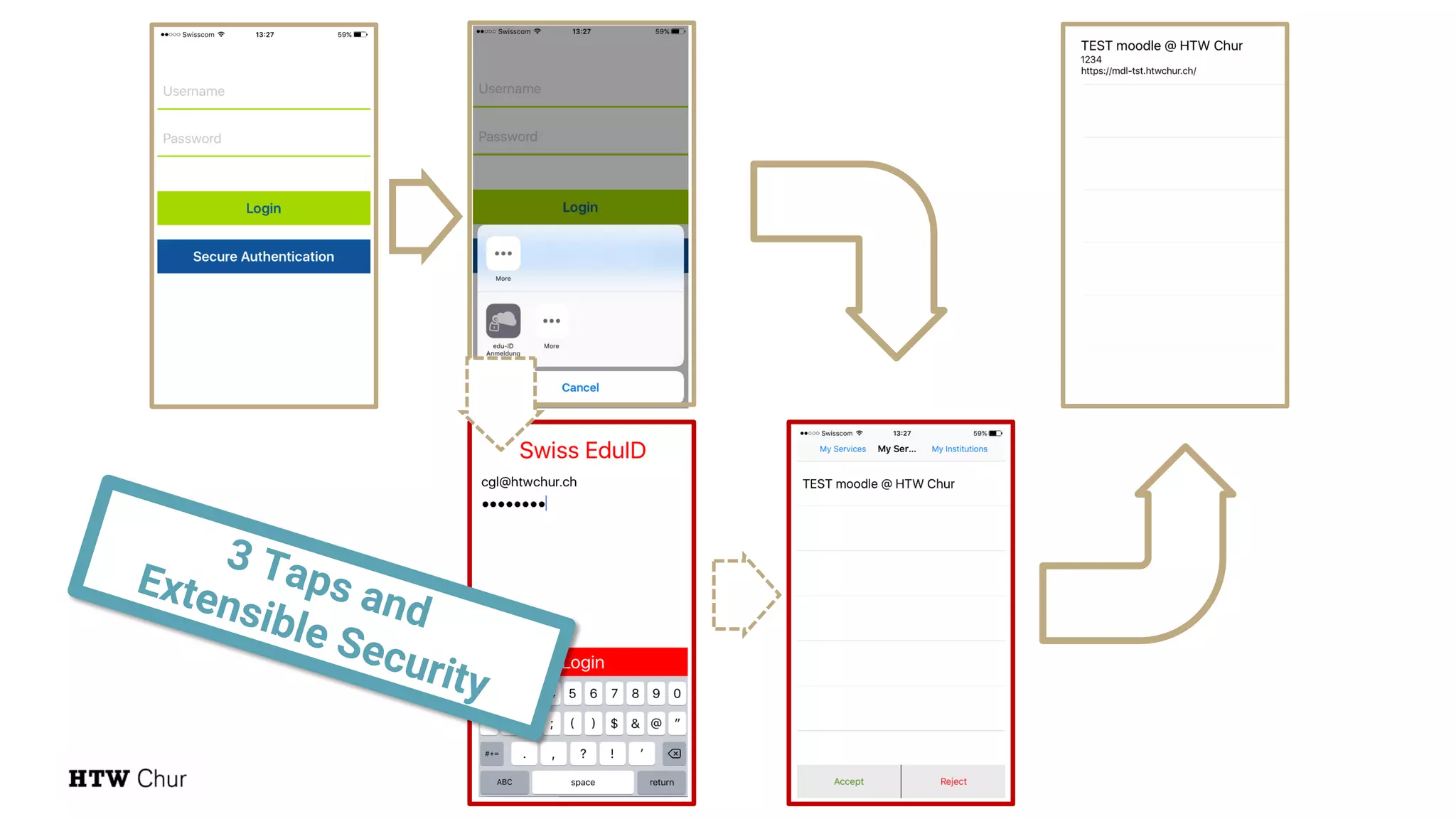
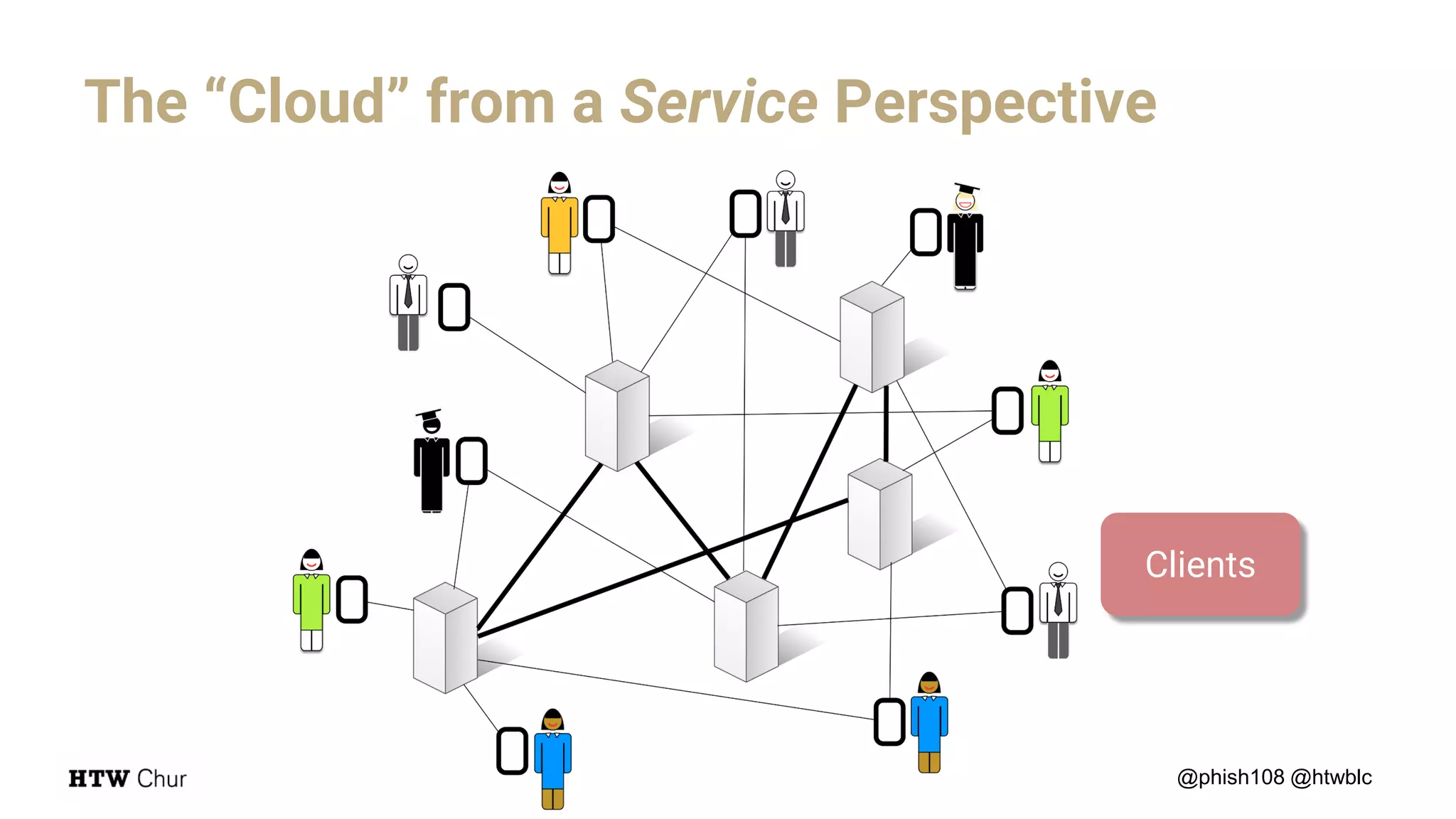
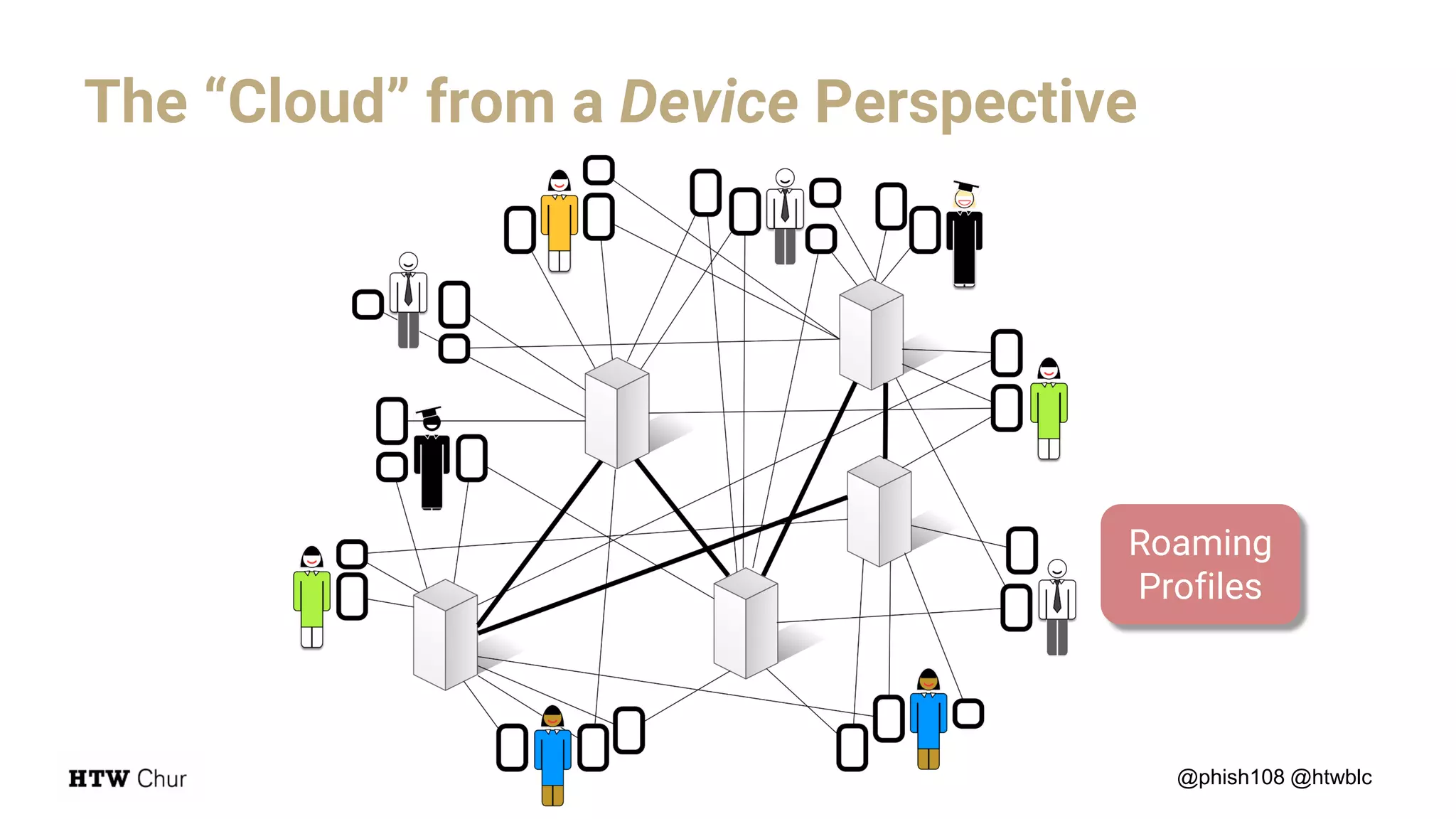
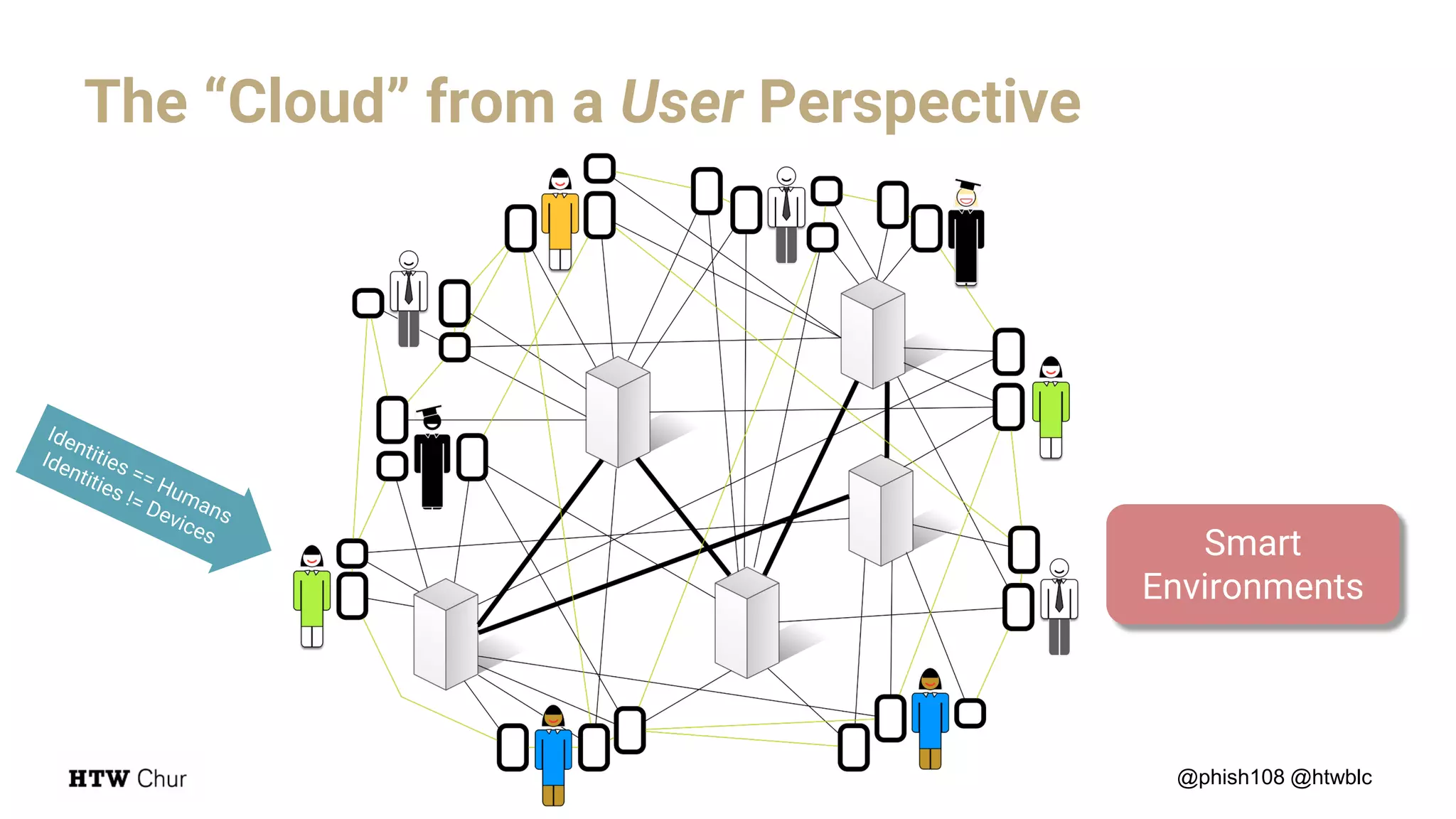
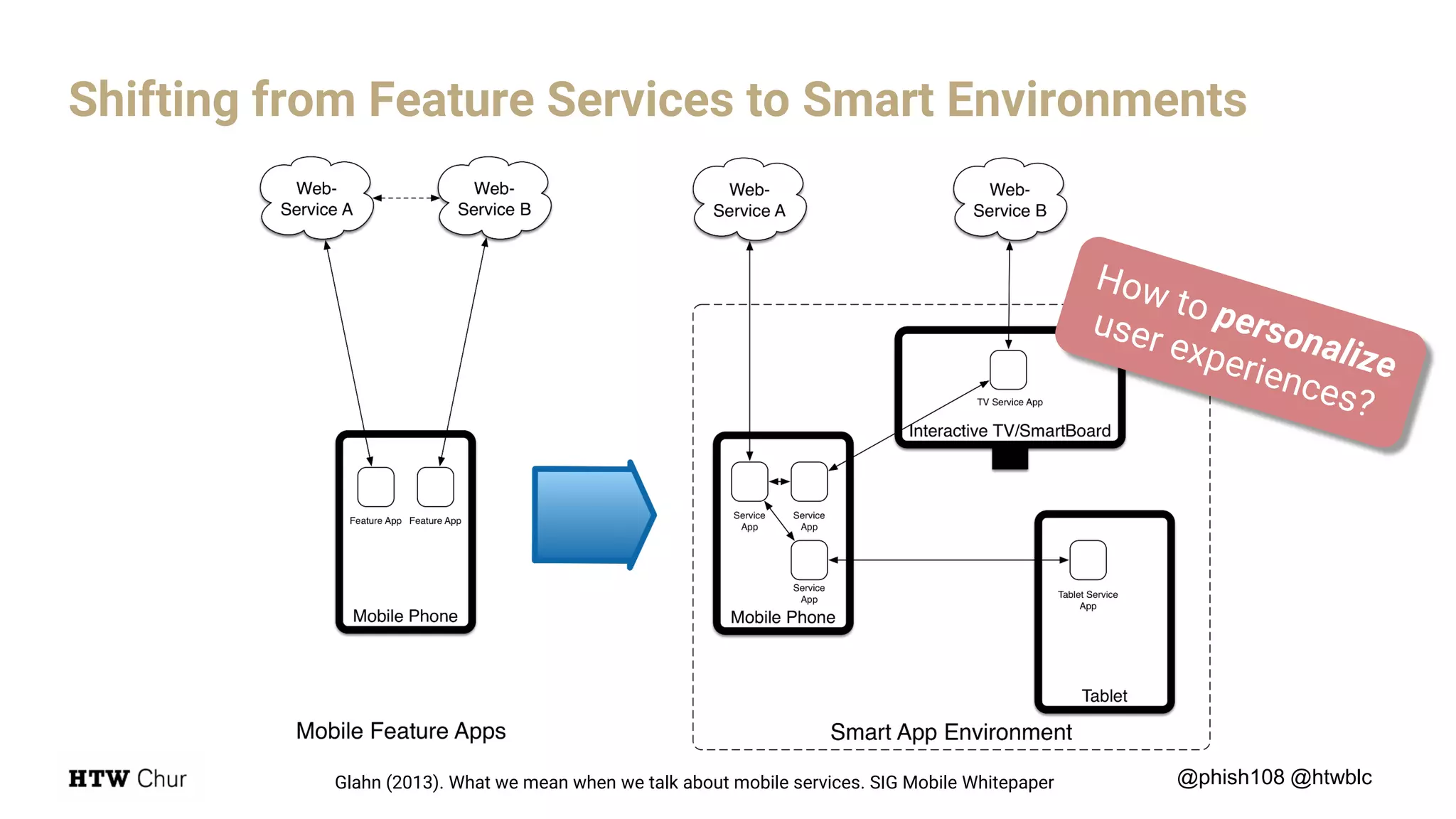
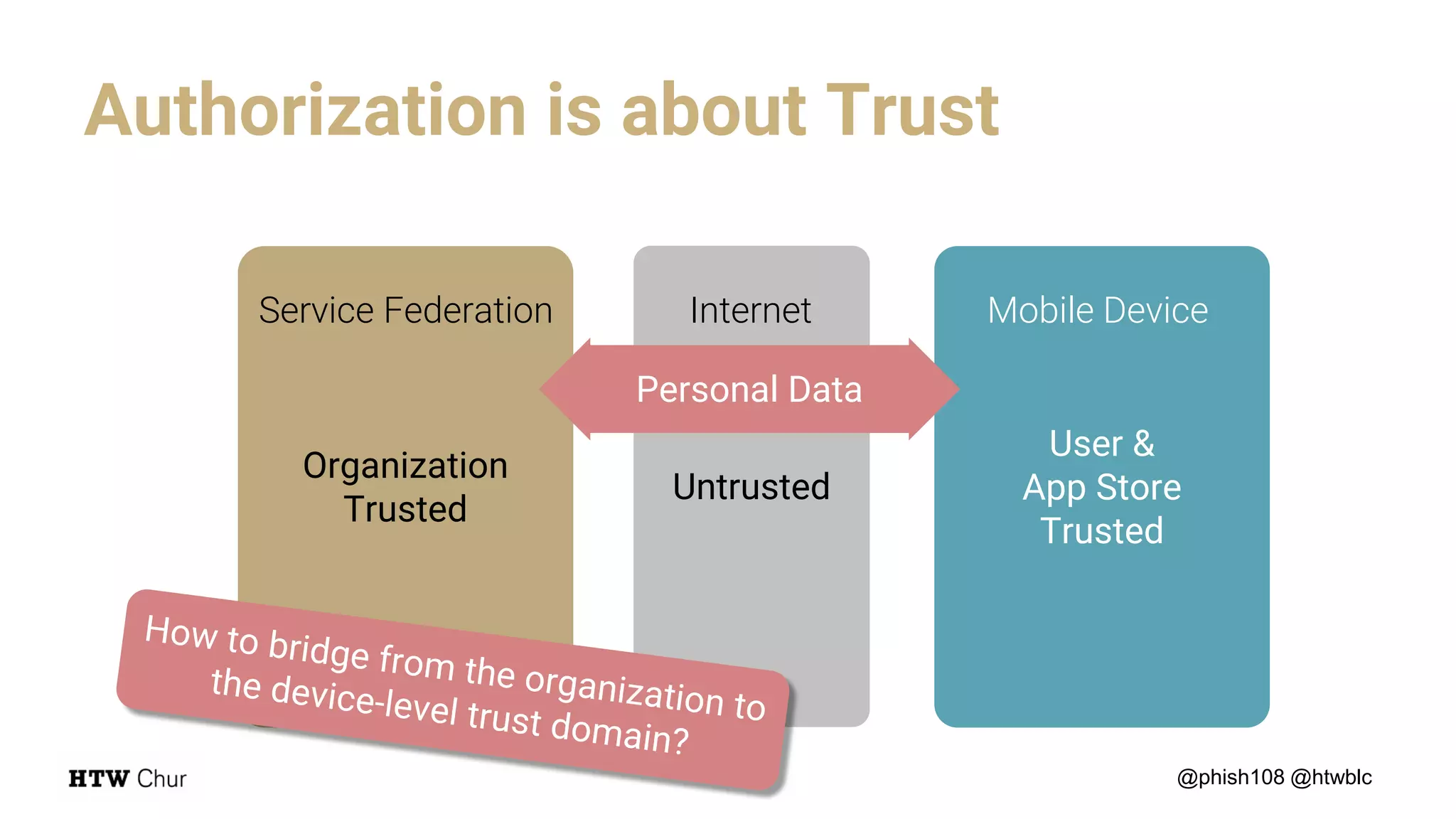
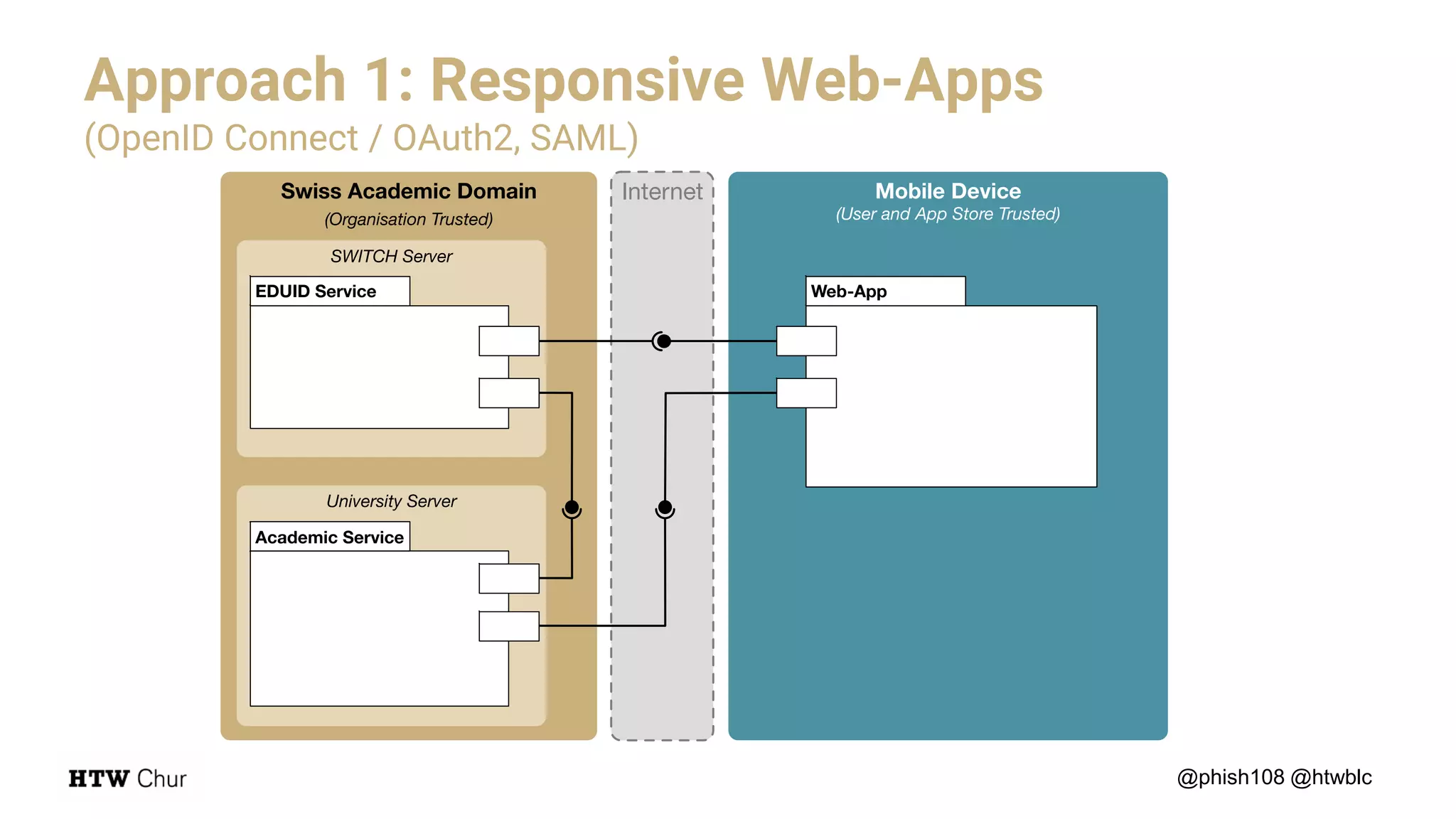
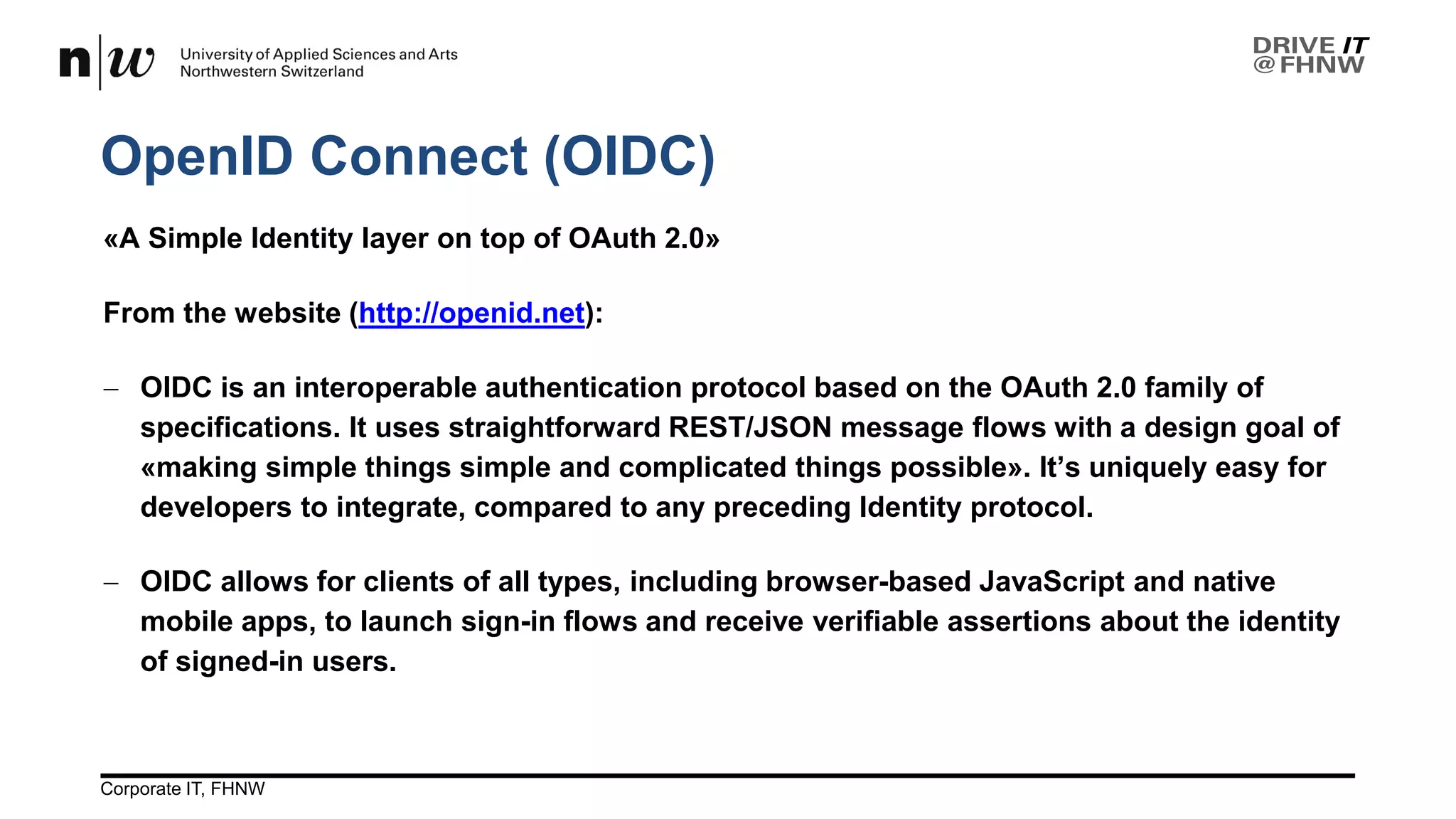
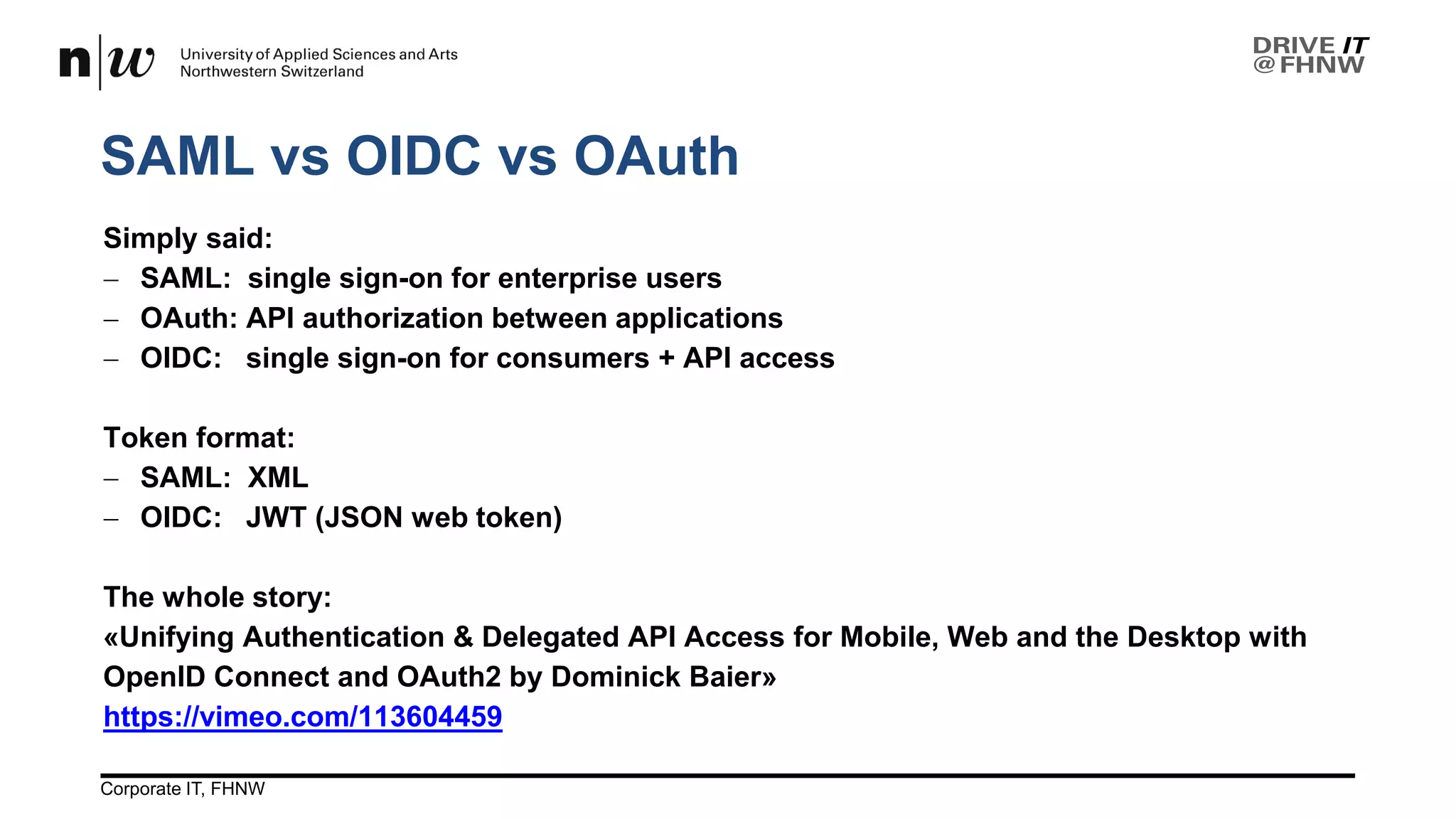
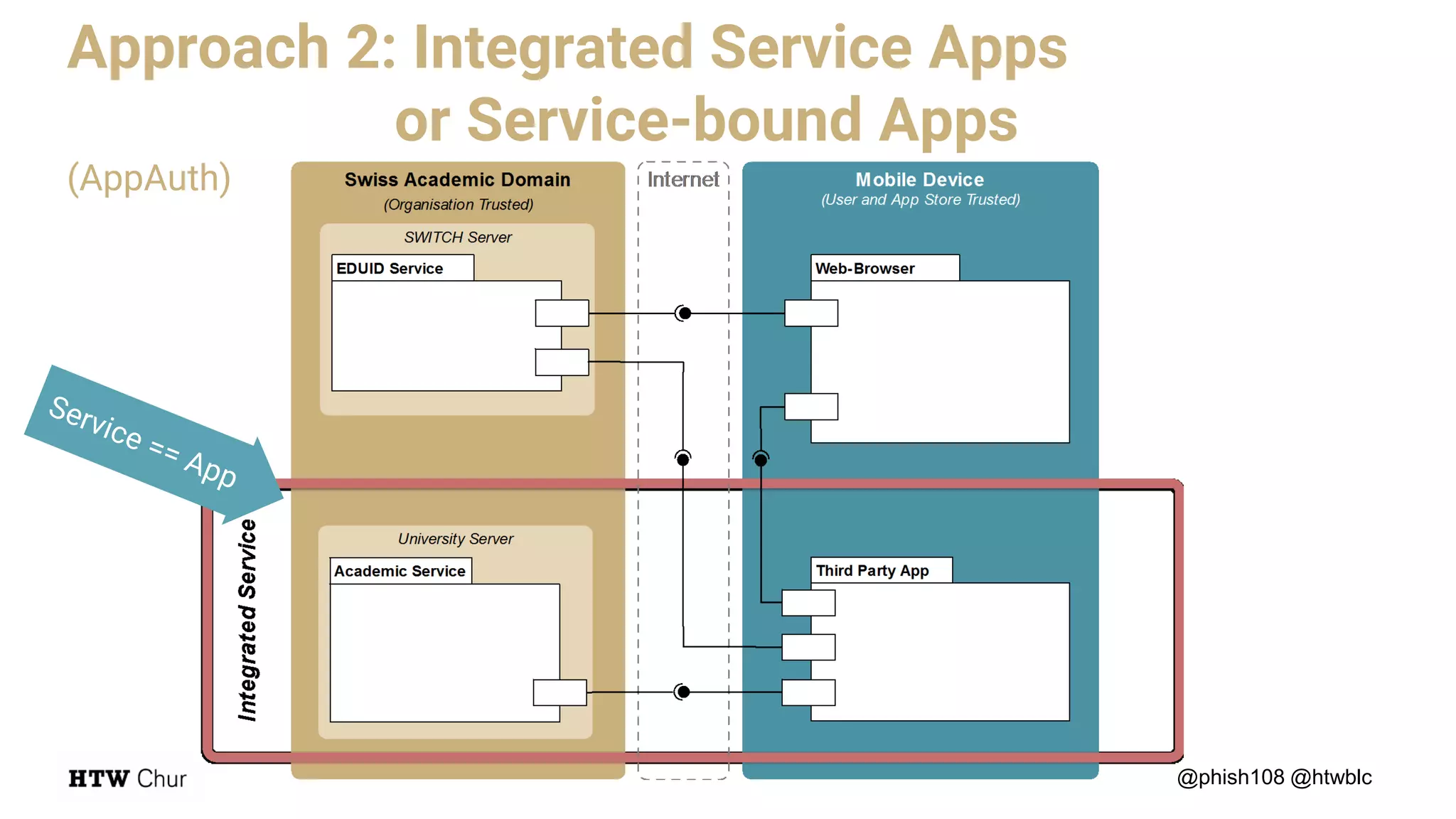
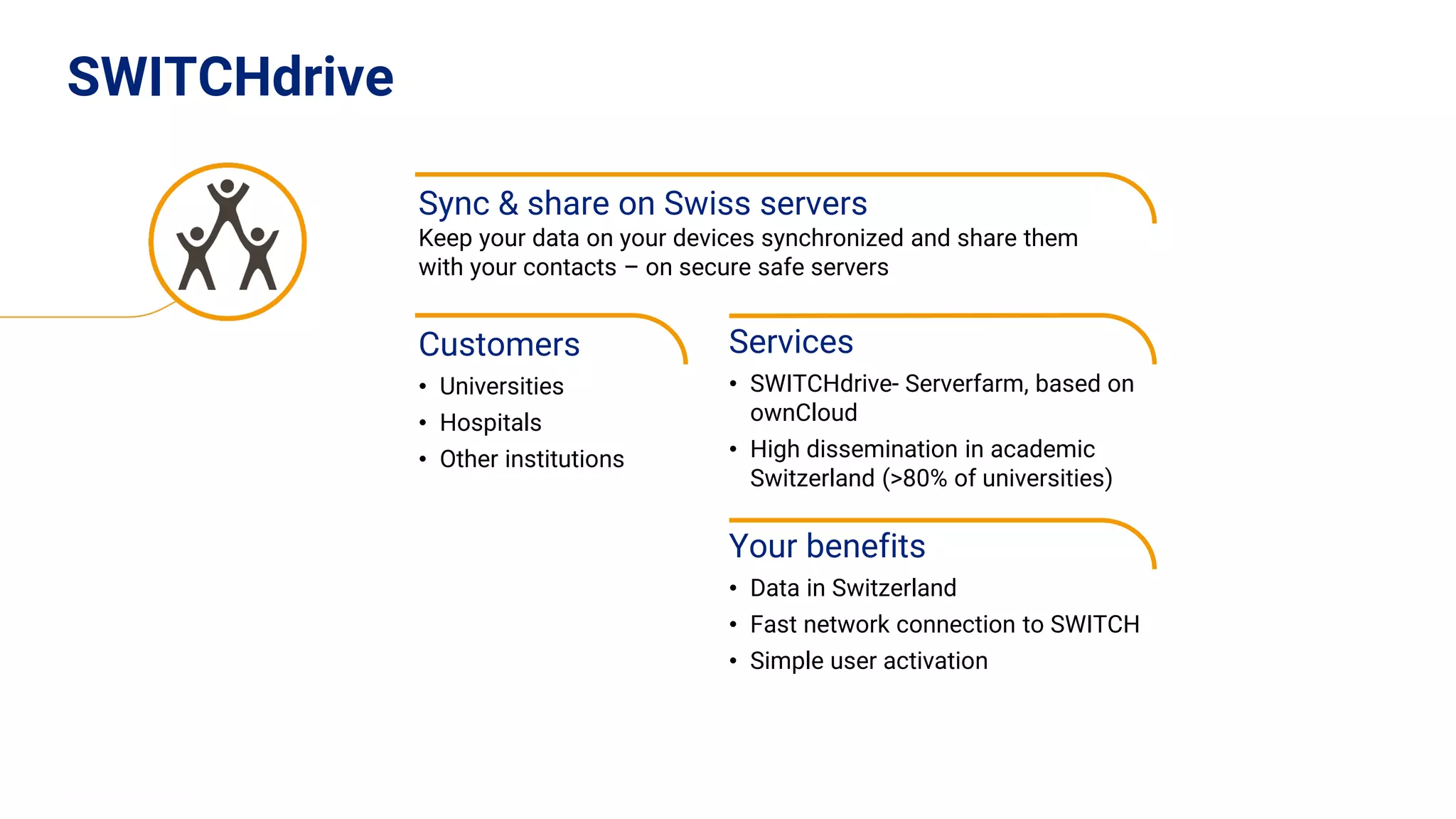
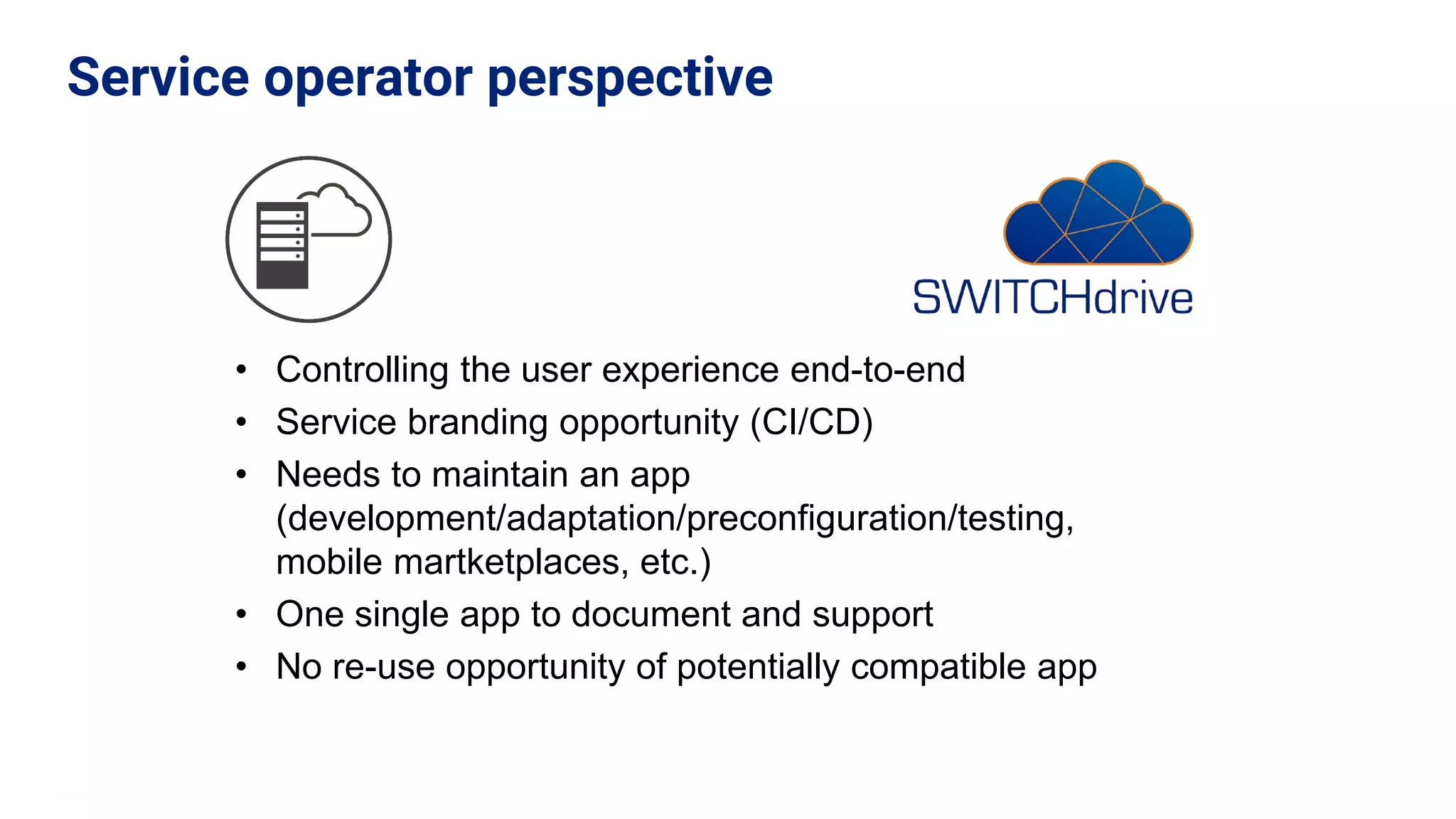
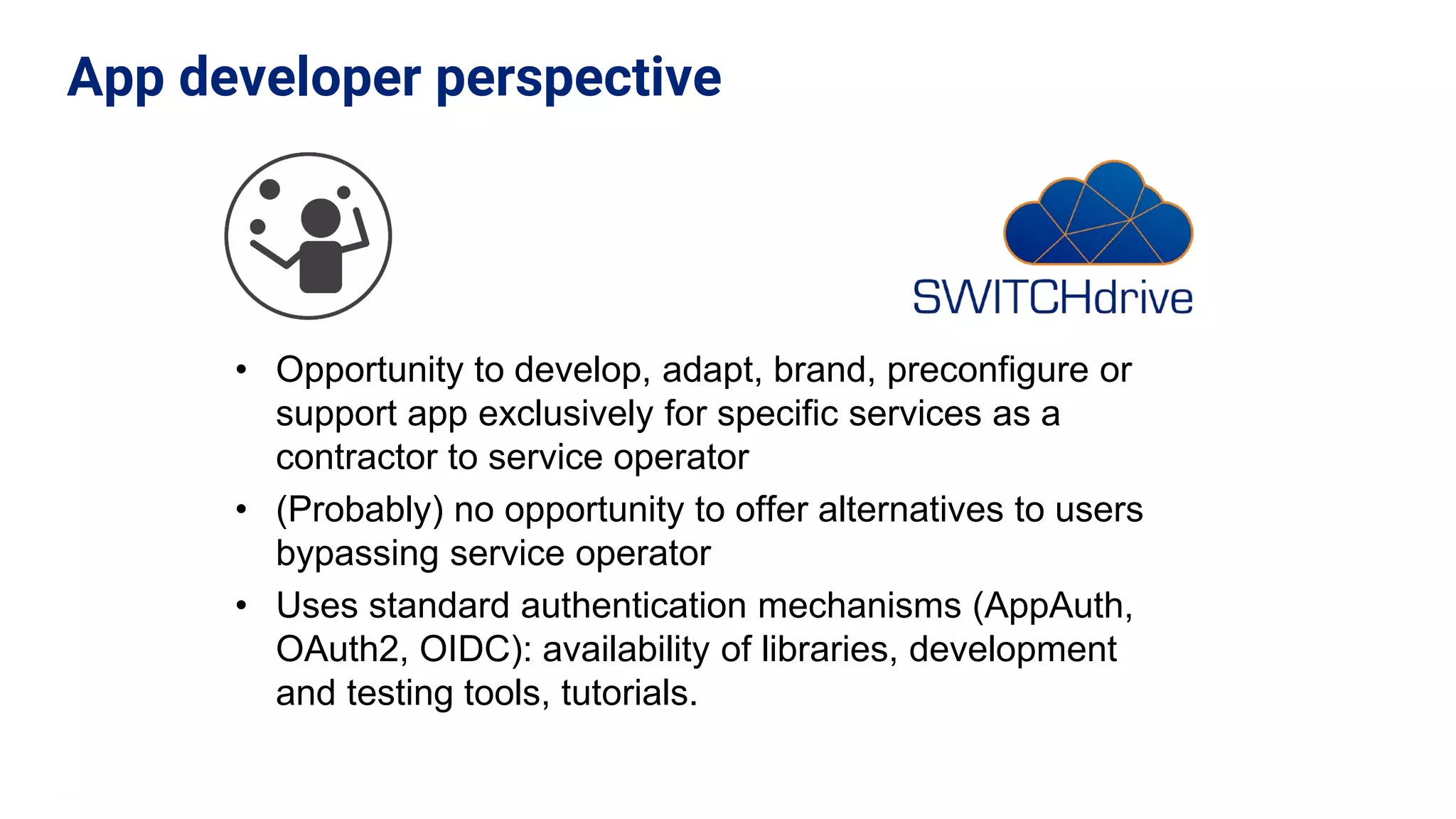
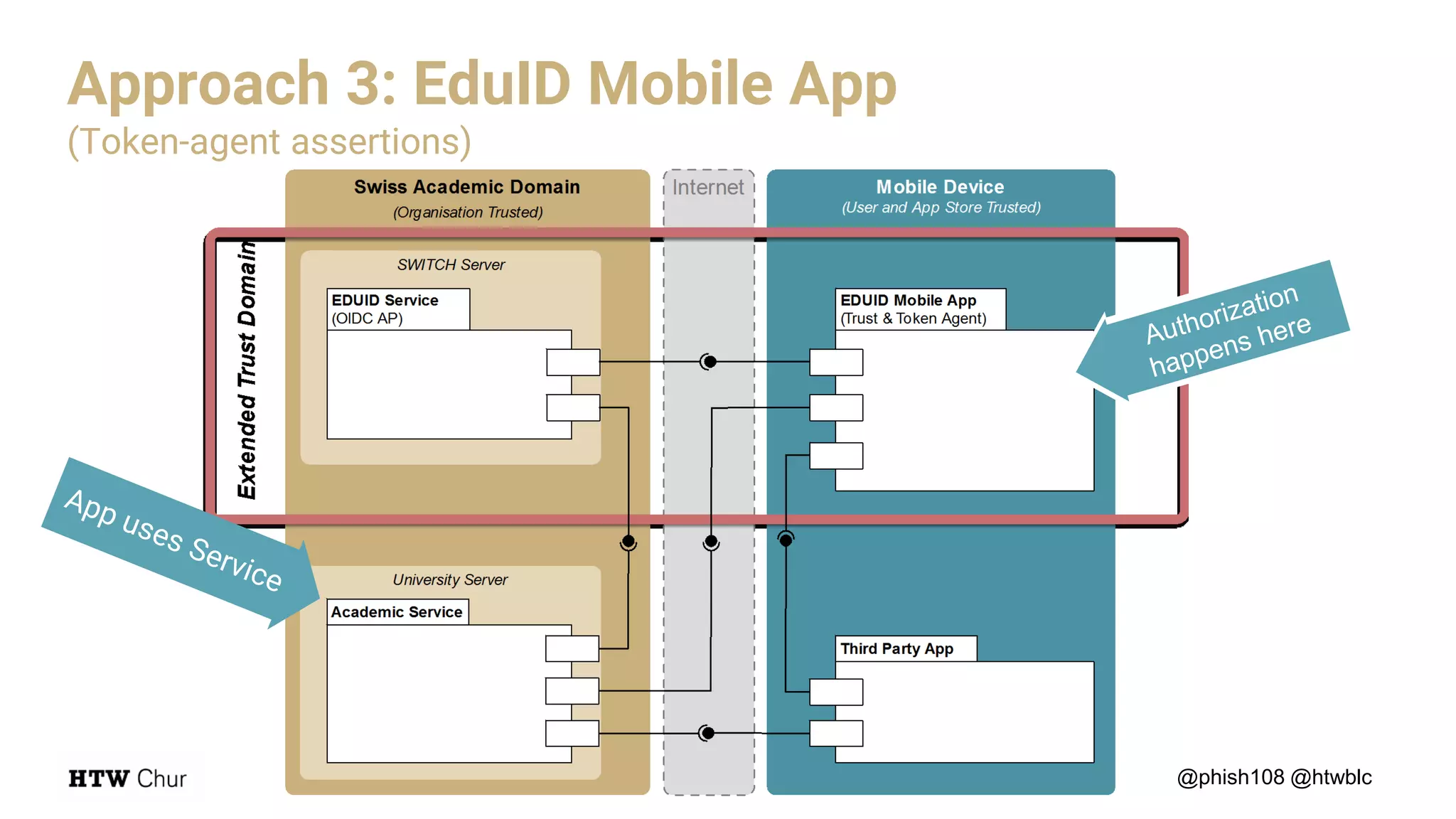
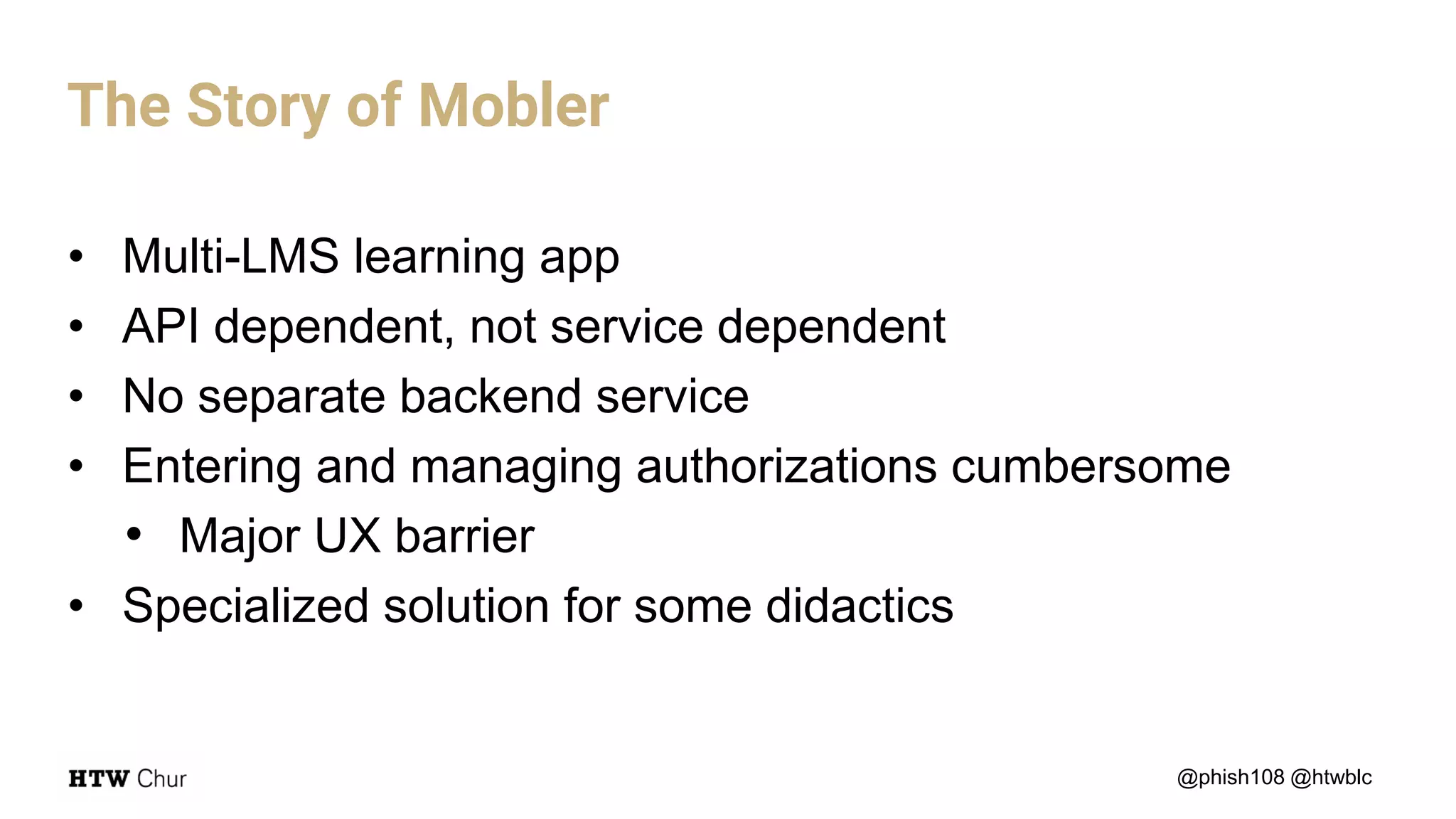
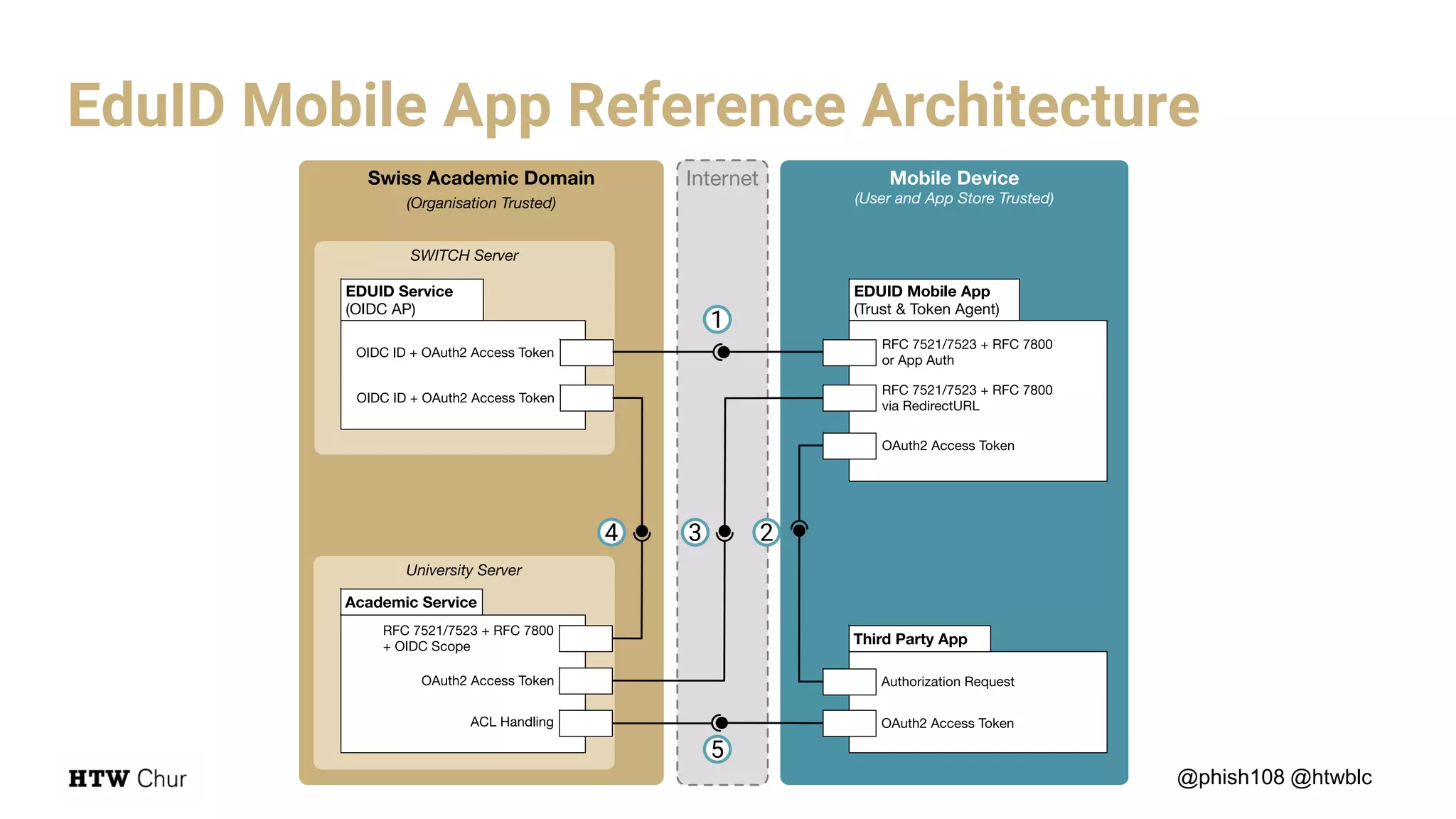
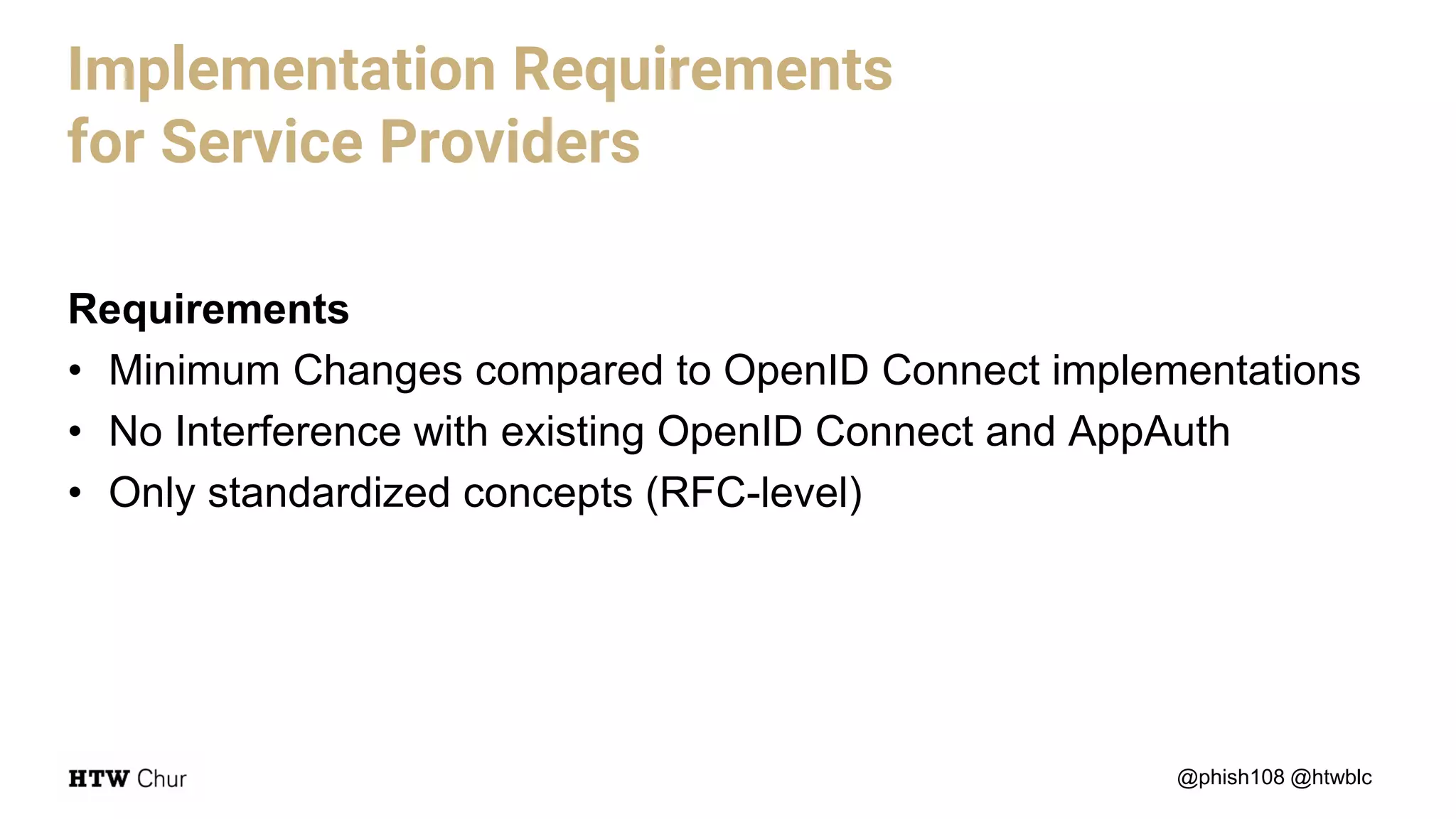
The document outlines the use cases and implementation strategies for the Eduid mobile app, focusing on client, device, and user perspectives of cloud services. It discusses three approaches to mobile app authorization: responsive web-apps using OpenID Connect, integrated service apps, and token-agent assertions for multi-LMS applications. Additionally, it highlights the benefits of a unified architecture for developers and organizations, emphasizing ease of adoption and enhanced user experience.





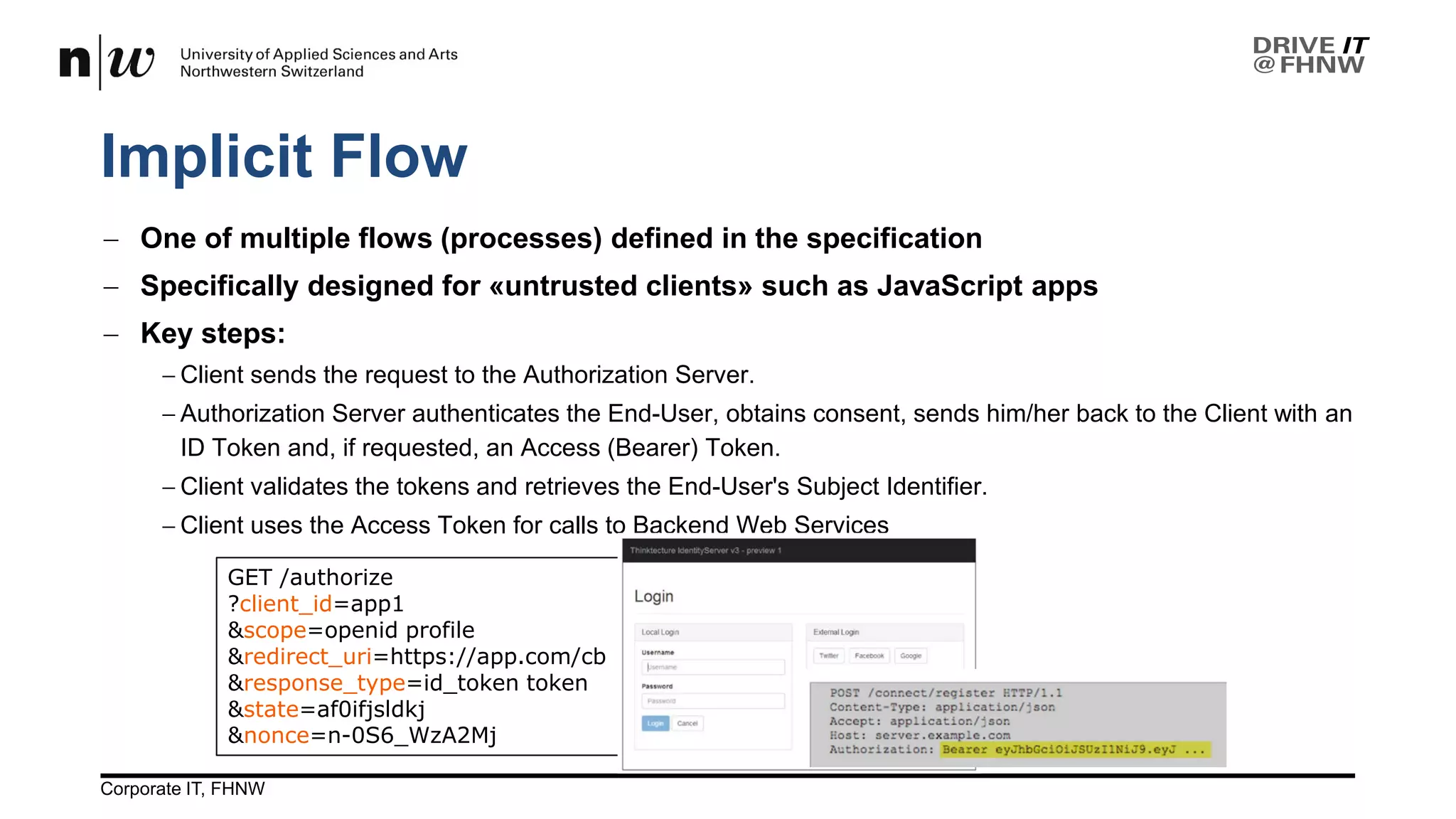









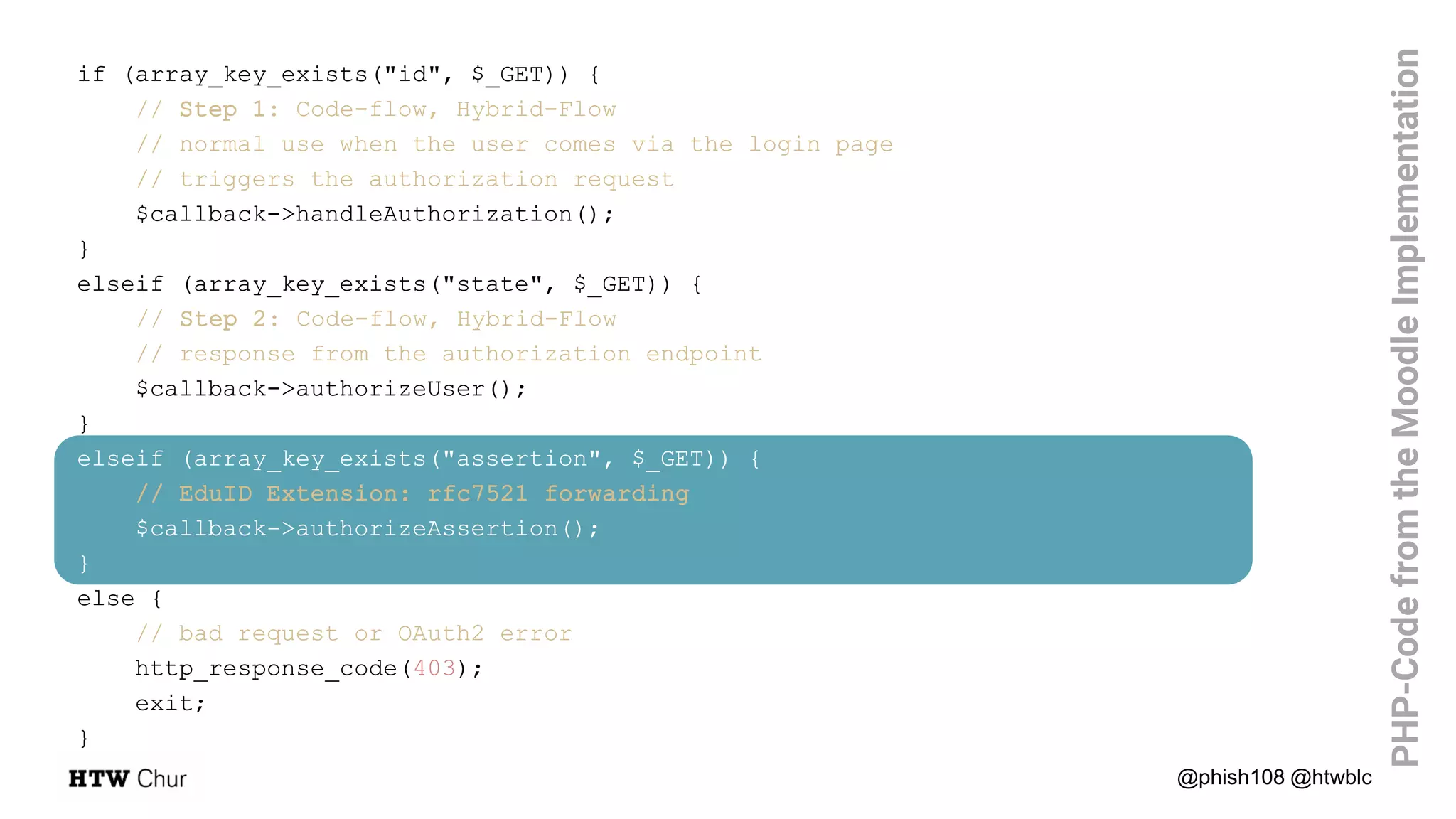
![public function authorizeAssertion() {
// rfc7521 forwarding: extend the incoming assertion parameters
$param = array_merge($_GET, ["scope"=> "openid profile email"]);
// Fetch the access-token and user–information
// - this is the same call as in step 2 of the Code Flow
$res = $this->callTokenEndpoint($param);
if (!$this->handleToken($res)) {
http_response_code(403);
}
}
@phish108 @htwblc
PHP-CodefromtheMoodleImplementation](https://image.slidesharecdn.com/eduid-workshop2-170426115539/75/EduID-Mobile-App-Use-Cases-Concepts-and-Implementation-33-2048.jpg)