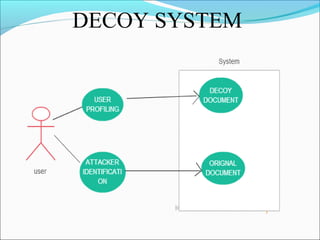
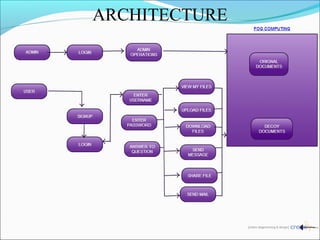
This document discusses fog computing and a proposed system to improve security of data stored in the cloud. It proposes using decoy technology to monitor for abnormal access patterns and generate fake documents to confuse attackers. The system would profile user behavior to validate authorized access and deploy decoys when abnormal access is detected. This helps prevent attackers from distinguishing real user data from fake data.