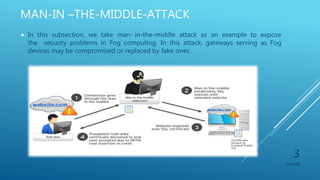
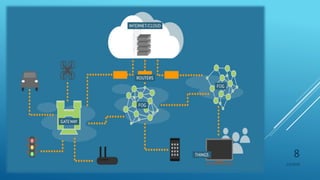
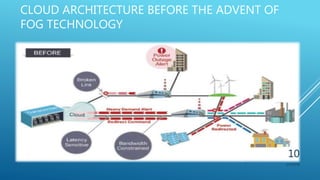
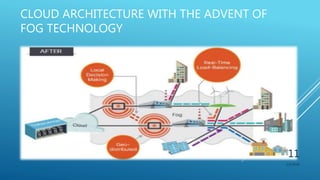
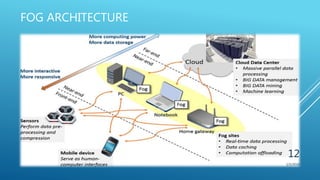
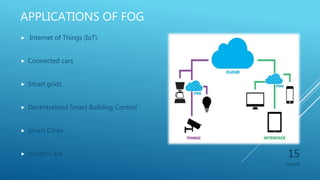
This document presents a seminar on fog computing given by Ajay Dhanraj Sirsat. It discusses the existing cloud computing system and its problems, proposes fog computing as an alternative system, and describes fog computing architecture and its advantages over cloud. Fog computing extends cloud services to the edge of the network to provide low latency and location awareness. It is well-suited for applications such as the Internet of Things, connected cars, smart grids, and smart buildings.