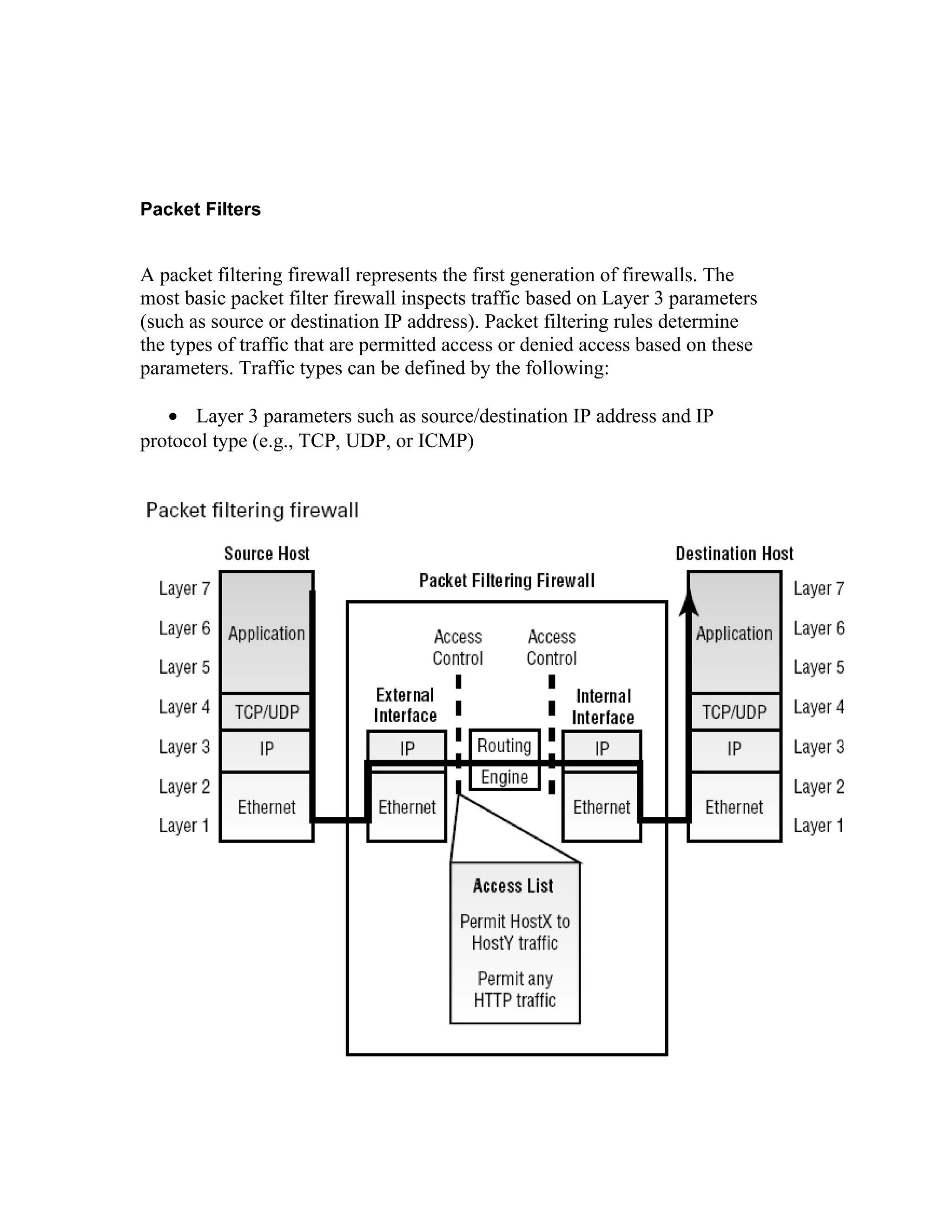
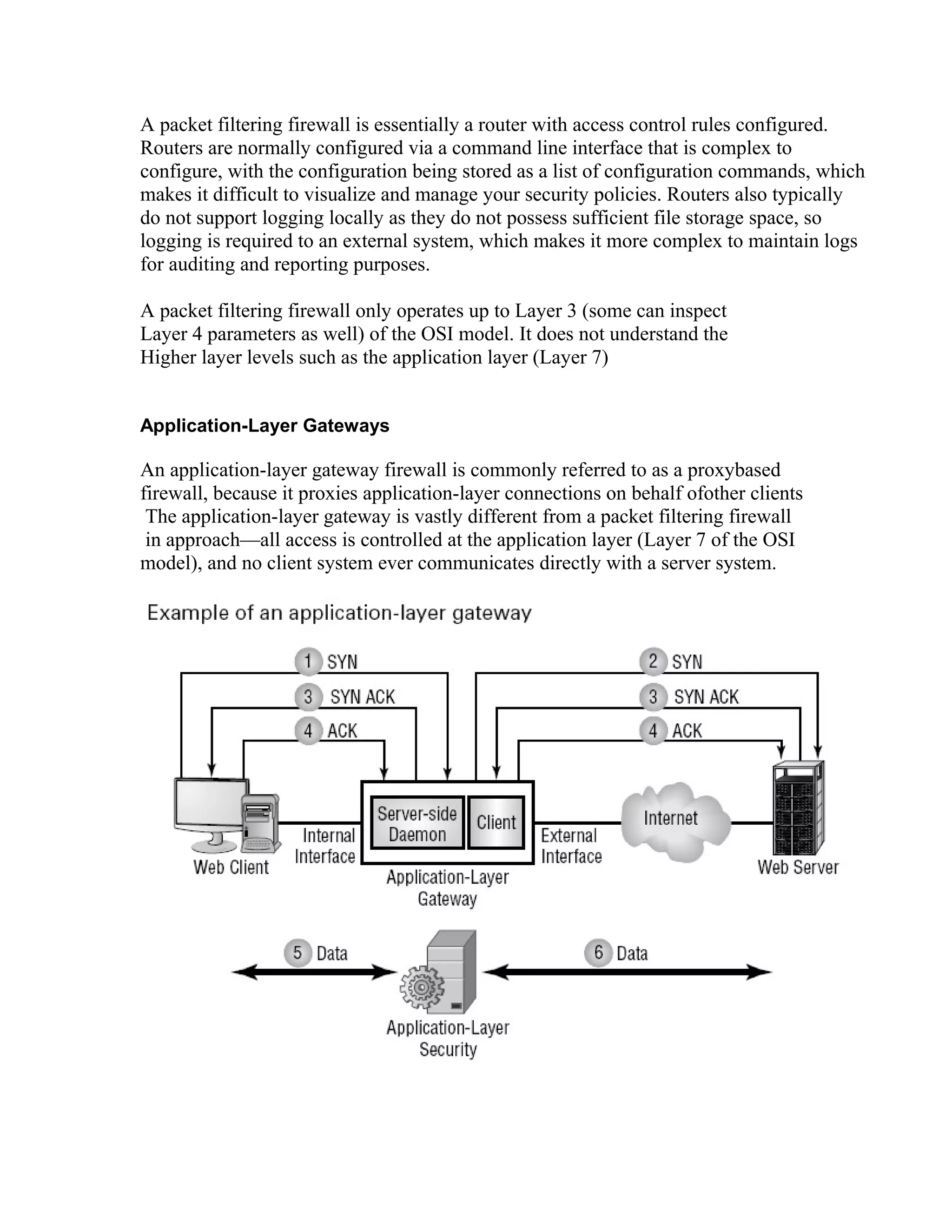
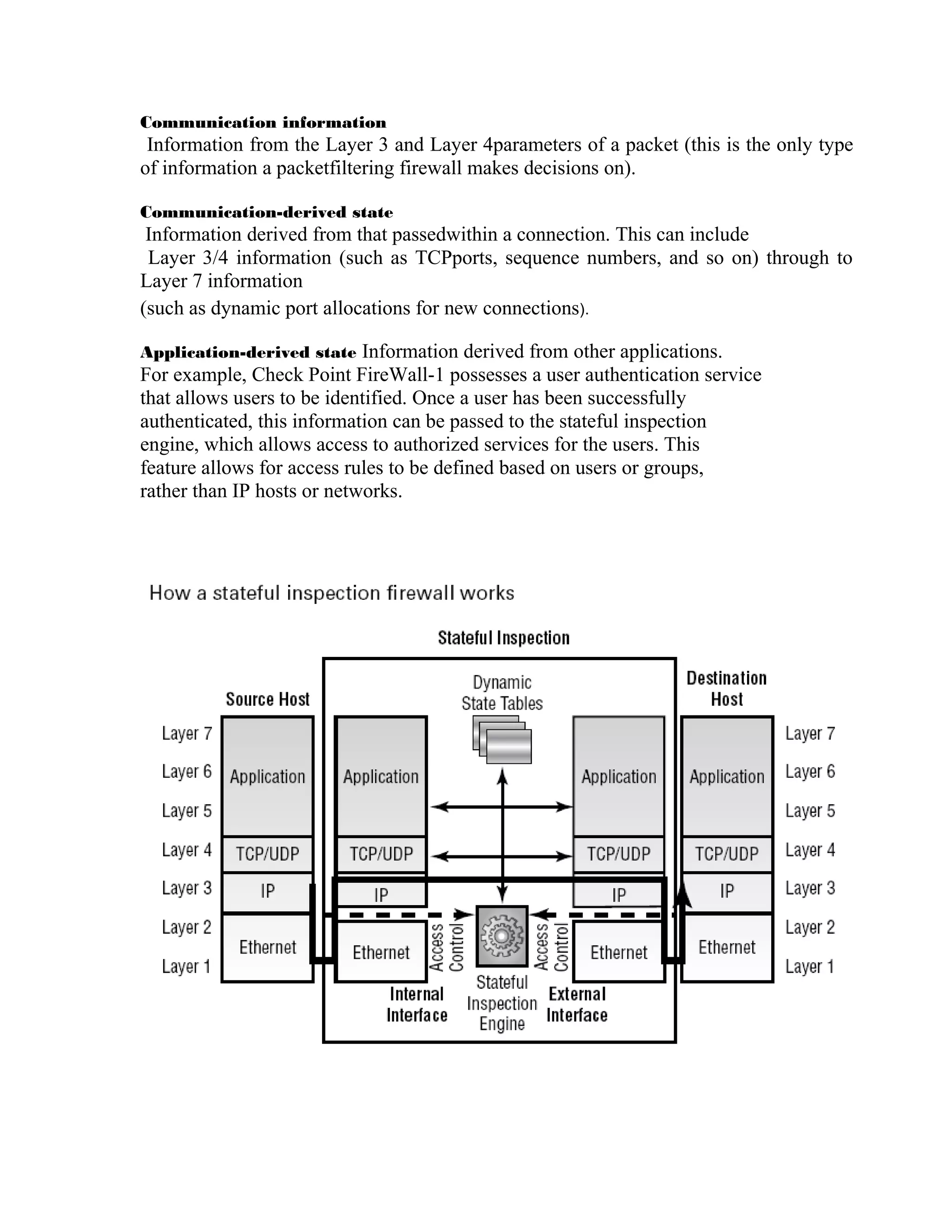
A firewall monitors and controls transmissions between an internal network and the internet. There are different types of firewalls including host-based, network-based, software-based, and hardware-based. Firewalls can also be categorized as packet filters, application-level proxies, or stateful packet filters. Stateful packet filters make access decisions based on layer 3 and 4 parameters as well as derived state information to provide high security while maintaining performance.