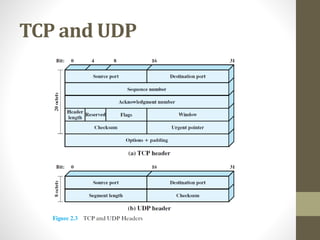
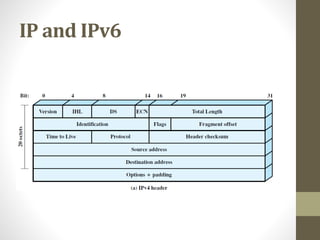
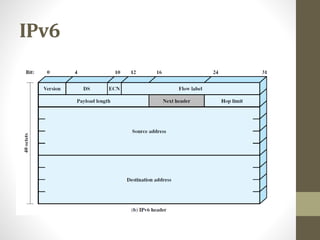
The document provides an overview of protocol architectures and the TCP/IP protocol stack. It discusses how protocol architectures establish rules for exchanging data between systems using layered protocols. The TCP/IP model is then explained in detail through its five layers - physical, network access, internet, transport and application - and core protocols like IP, TCP and UDP. Key differences between IPv4 and IPv6 are also summarized.