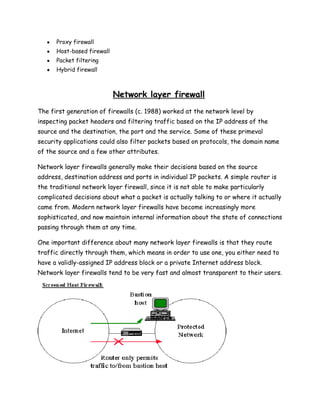
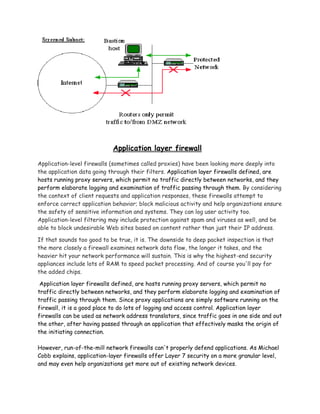
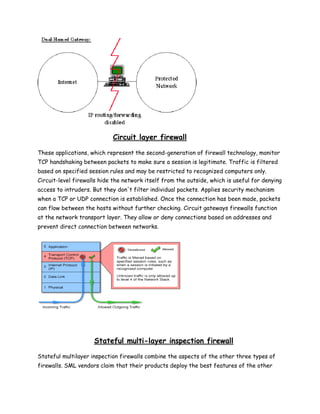
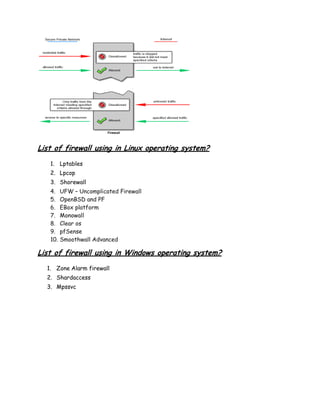
A firewall is a system or set of rules designed to permit or deny computer applications access to networks based on a set of rules. Firewalls can be implemented through software or hardware and work by examining network packets and blocking or allowing passage based on the packet's contents. There are several types of firewalls including network layer, application layer, circuit layer, and stateful multi-layer inspection firewalls. Firewalls help secure private networks from unauthorized access from other networks like the internet.