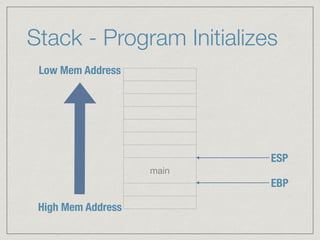
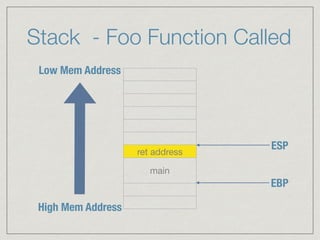
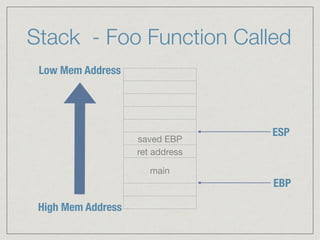
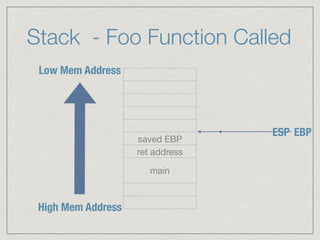
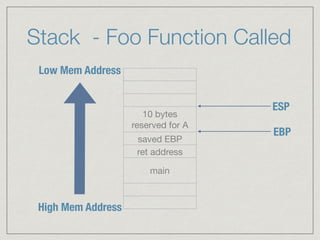
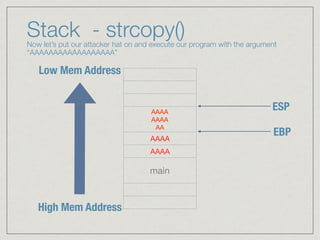
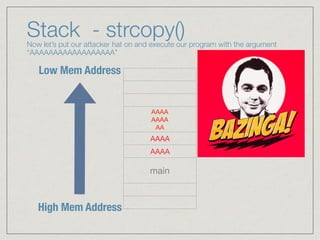
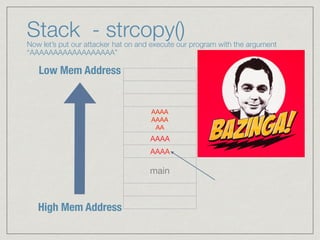
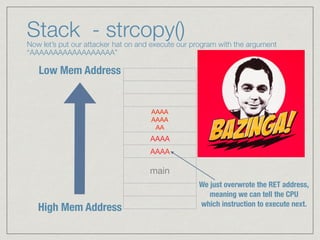
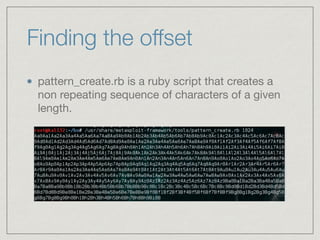
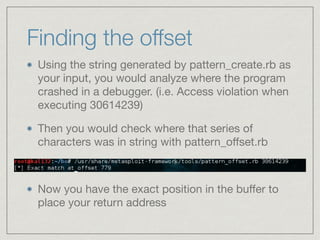
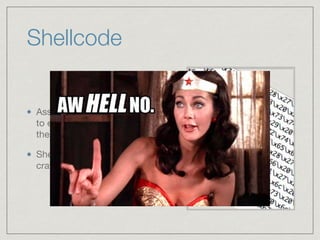
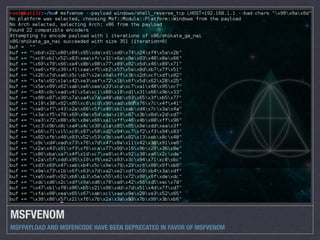
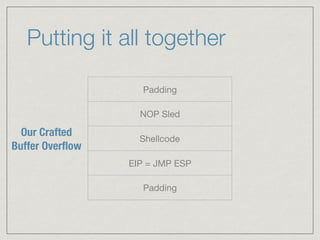
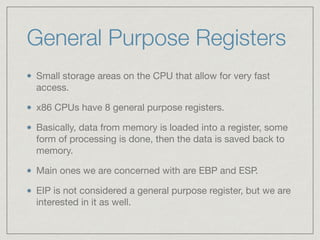
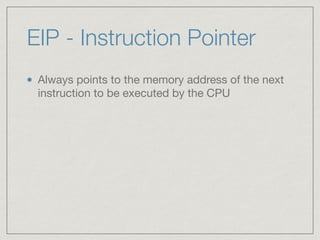
This document provides an introduction to stack buffer overflows on x86 architecture. It explains what a buffer is, how an overflow occurs when too much data is stored in a buffer, and how this can be exploited to overwrite the instruction pointer and redirect program flow. It discusses CPU registers like EBP, ESP and EIP that are involved. Finally, it outlines the steps to craft an exploit, including using patterns to find the offset, msfvenom to generate shellcode, and a NOP sled and JMP ESP to redirect execution to the shellcode.


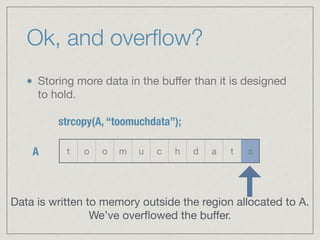
![What’s a buffer?
A buffer can be thought of as an allocated space
in memory intended to hold a certain amount of
data.
char A[10];
Allocate 10 bytes for the variable A](https://image.slidesharecdn.com/bufover101pdf-160729155450/85/Buffer-Overflows-101-Some-Assembly-Required-3-320.jpg)





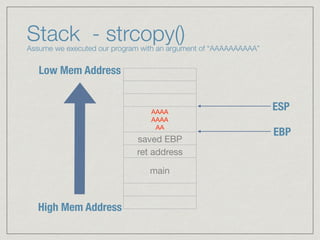
![Assume the below program
#include <string.h>
void foo (char *bar)
{
char A[10];
strcpy(A, bar); // no bounds checking
}
int main (int argc, char **argv)
{
foo(argv[1]);
}
Program simply takes an
argument on the
command line and copies
it into a variable that is
allocated 10 bytes (A)
https://en.wikipedia.org/wiki/Stack_buffer_overflow](https://image.slidesharecdn.com/bufover101pdf-160729155450/85/Buffer-Overflows-101-Some-Assembly-Required-19-320.jpg)