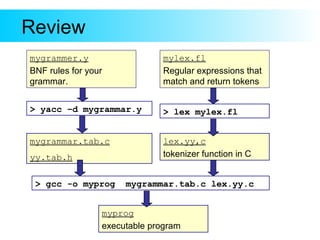
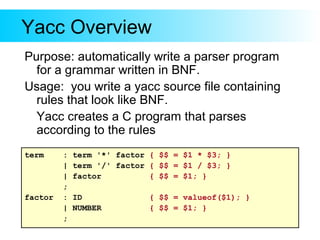
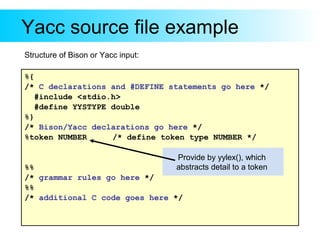
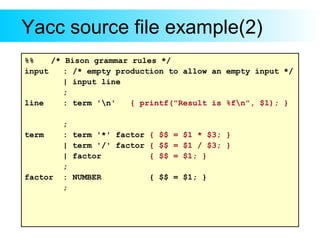
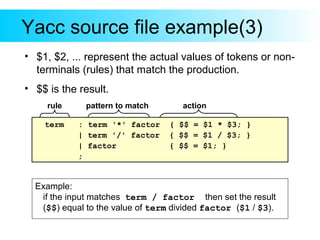
This document provides an introduction to Yacc and Lex, which are parser and lexer generator tools. Yacc is used to describe the grammar of a language and automatically generate a parser. The user provides grammar rules in BNF format. Lex is used to generate a lexer (also called a tokenizer) that recognizes tokens in the input based on regular expressions. It returns tokens to the parser. The document gives examples of Yacc and Lex grammar files and explains how they are compiled and used to build a parser for an input language.









![Regular Expression example
Regular Expression Strings in L(R)
digit = [0-9] “0” “1” “2” “3” …
posint = digit+ “8” “412” …
int = -? posint “-42” “1024” …
[a-zA-Z_][a-zA-Z0-9_]* C identifiers](https://image.slidesharecdn.com/yacclex-140518211555-phpapp02/85/Yacc-lex-16-320.jpg)
![Lex example
• Read input and describes each token
read.
/* flex definitions */
DIGIT [0-9]
%%
[ tn]+ {}
-?{DIGIT}+ { printf("Number: %sn", yytext);
yylval=atoi(yytext); return NUMBER; }
n printf("End of linen"); return 0;
%%
/* all code is copied to the generated .c file*/](https://image.slidesharecdn.com/yacclex-140518211555-phpapp02/85/Yacc-lex-17-320.jpg)
![Example explanation
/* flex definitions */
DIGIT [0-9]
%%
[ tn]+ {}
-?{DIGIT}+ { printf("Number: %sn", yytext);
yylval=atoi(yytext); return NUMBER; }
n printf("End of linen"); return 0;
%%
/* all code is copied to the generated .c file*/
Yacc get the value Yacc get the token](https://image.slidesharecdn.com/yacclex-140518211555-phpapp02/85/Yacc-lex-18-320.jpg)