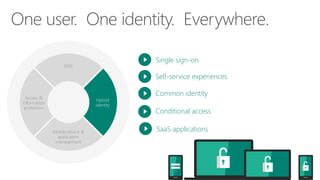
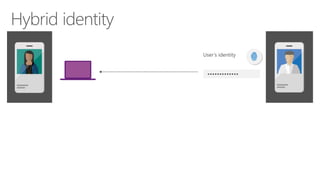
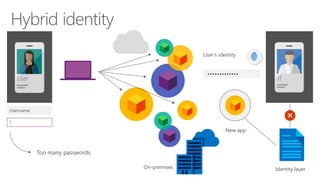
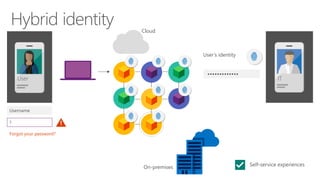
The document discusses enterprise mobility suite (EMS) and its hybrid identity capabilities. EMS provides single sign-on, self-service experiences, and a common identity across cloud and on-premises applications. It enables a unified user experience with a single verified identity that spans both environments. EMS reduces the burden on IT by integrating identity management and lowering risks through a single solution rather than separate cloud and on-premises identities.