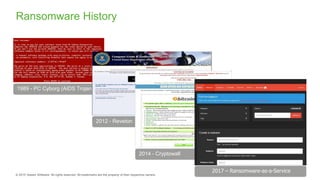
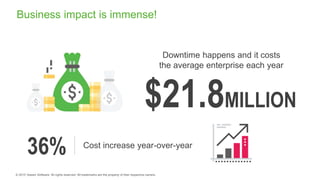
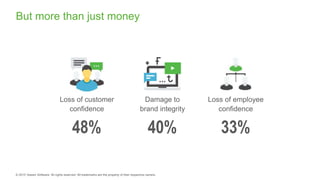
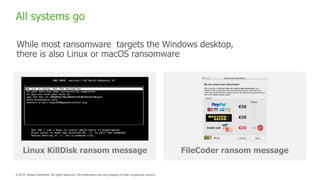
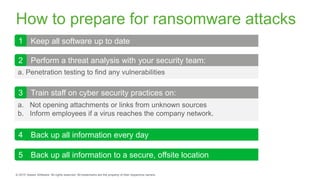
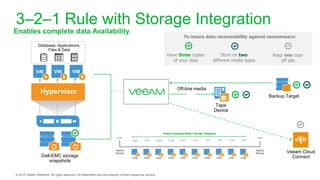
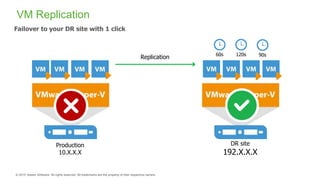
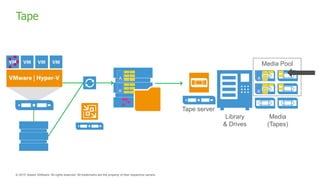
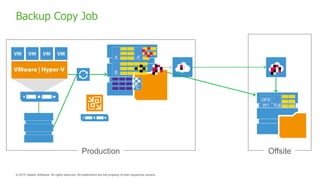
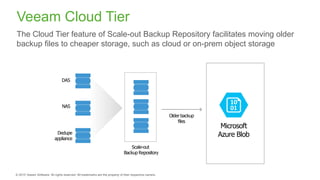
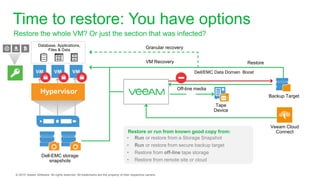
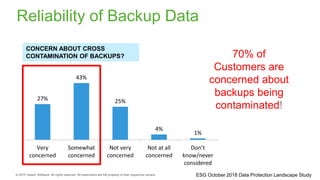
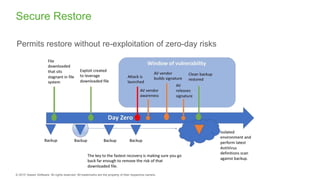
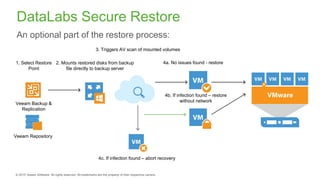
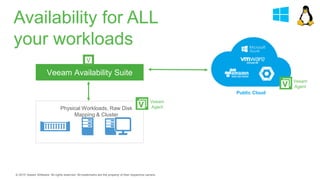
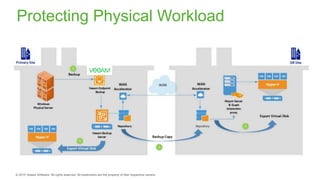
The document provides an overview of ransomware, detailing its nature as a malicious software that encrypts data for ransom and highlights the increasing costs and impact on businesses. It discusses various types of ransomware, infection methods, and emphasizes the importance of preparedness through measures like backups, antivirus effectiveness, and employee training. Additionally, it outlines recovery options and the need for secure restoration practices to mitigate risks associated with potential ransomware attacks.