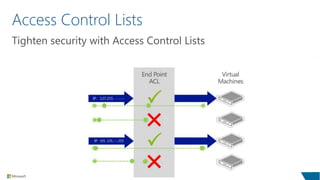
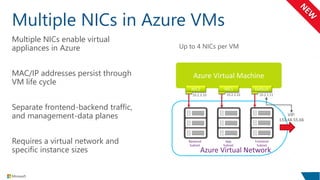
The document outlines compliance standards and security measures related to Microsoft Azure services, highlighting certifications such as ISO 27001, SOC, and PCI DSS. It emphasizes security protocols, including access control lists, network segmentation, and the use of multiple network interface cards in virtual machines. Additionally, it discusses Microsoft Azure Storage's durability and geo-replication features for data protection and backup solutions.