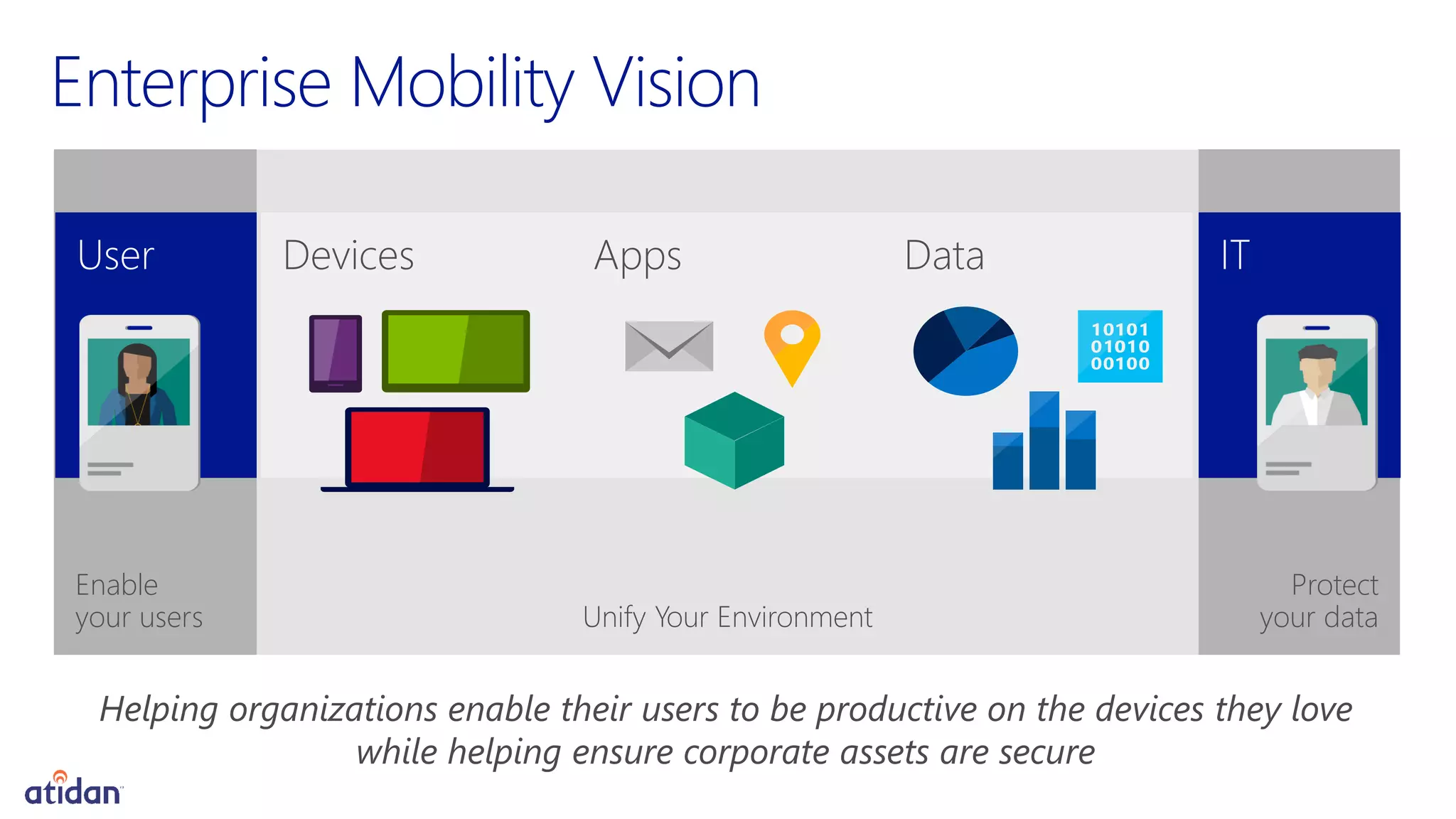
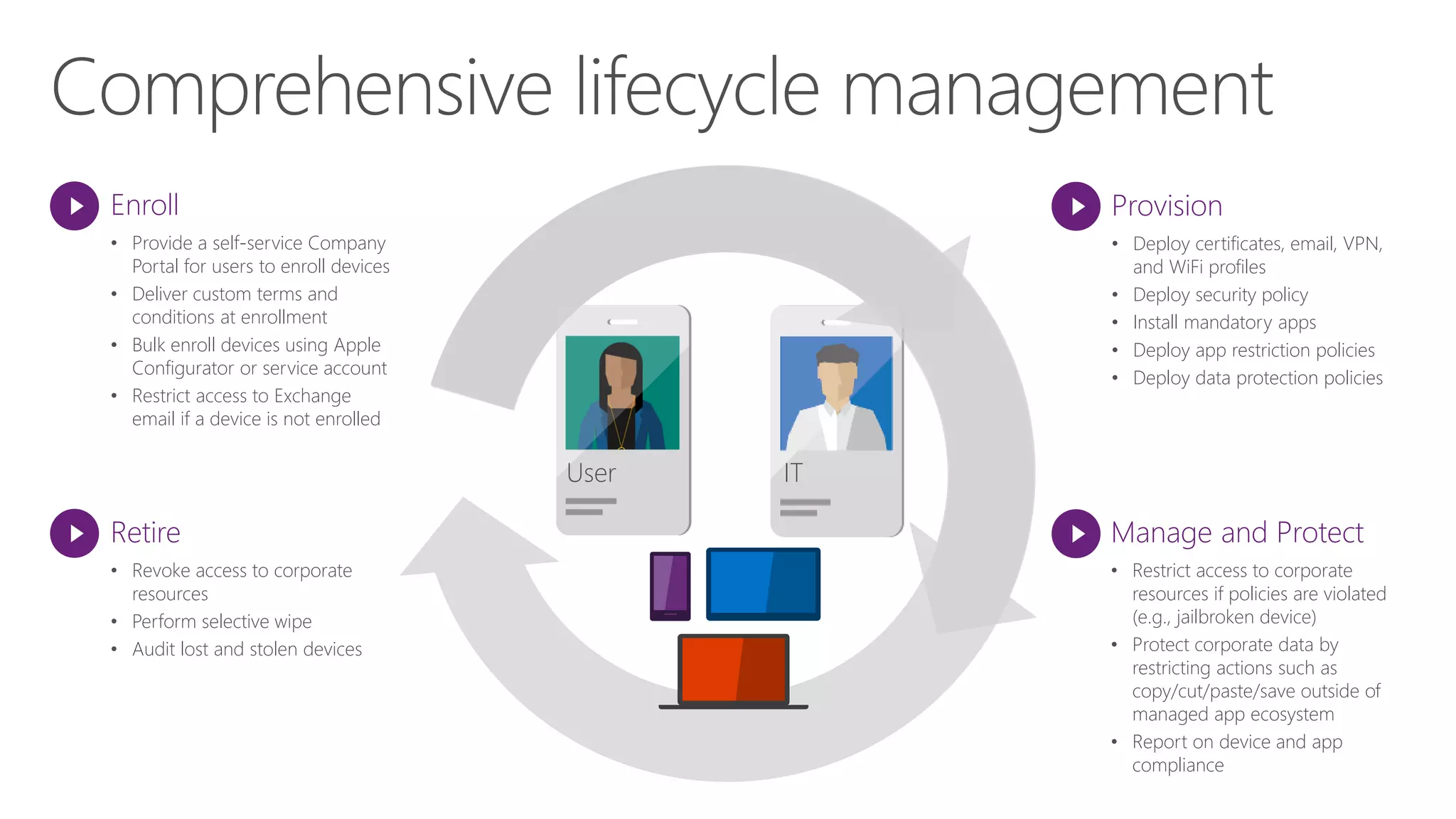
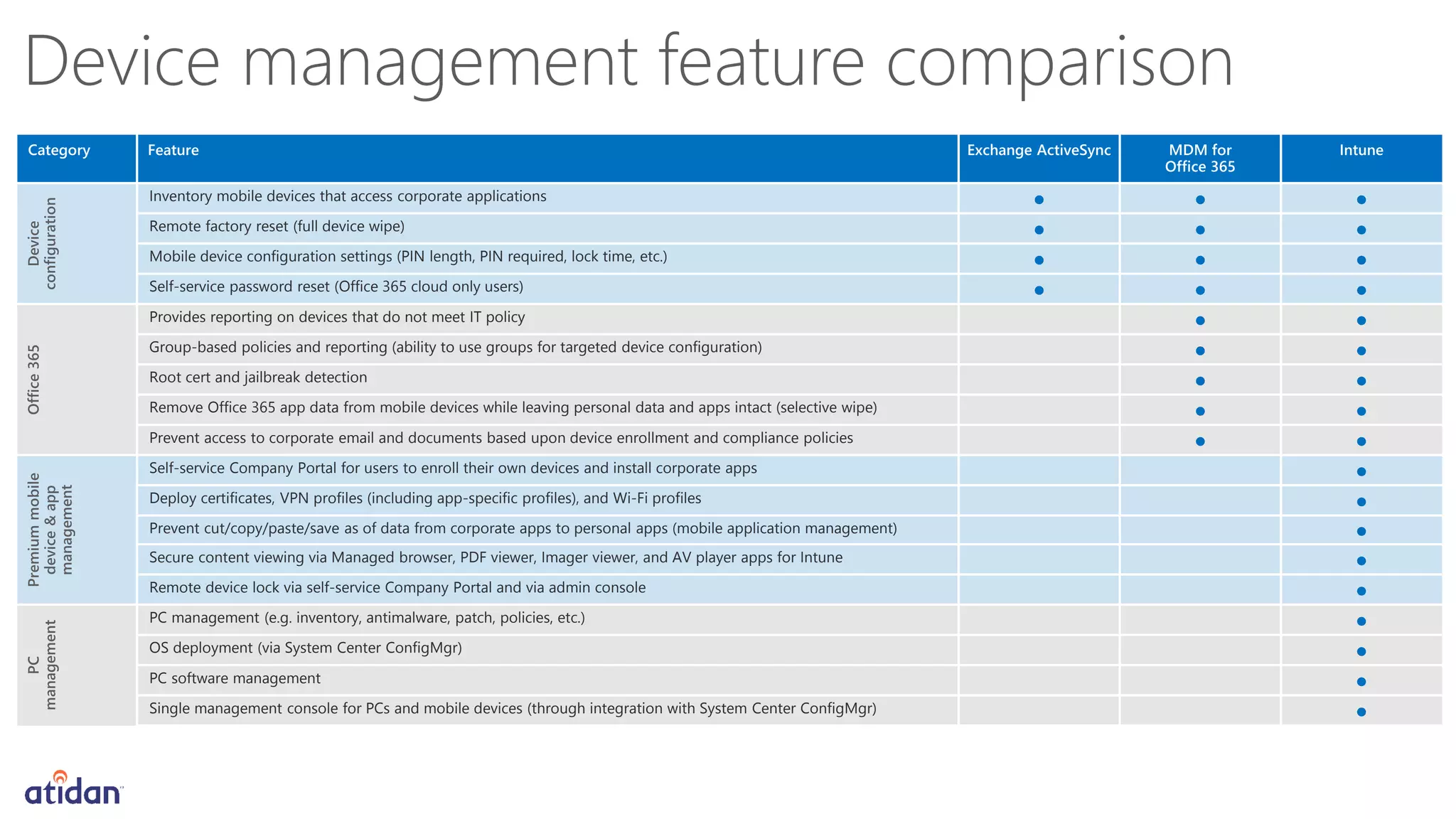
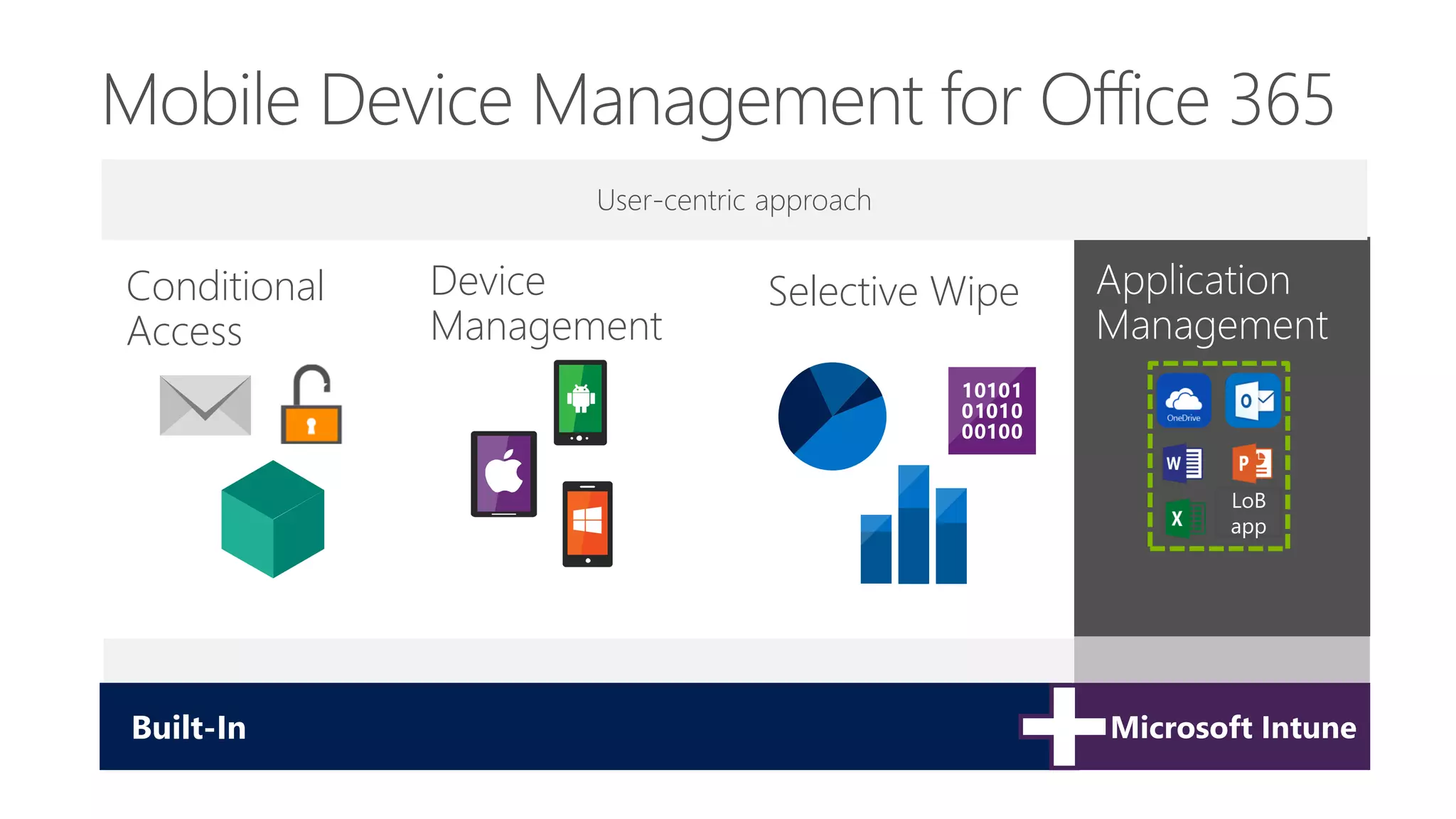
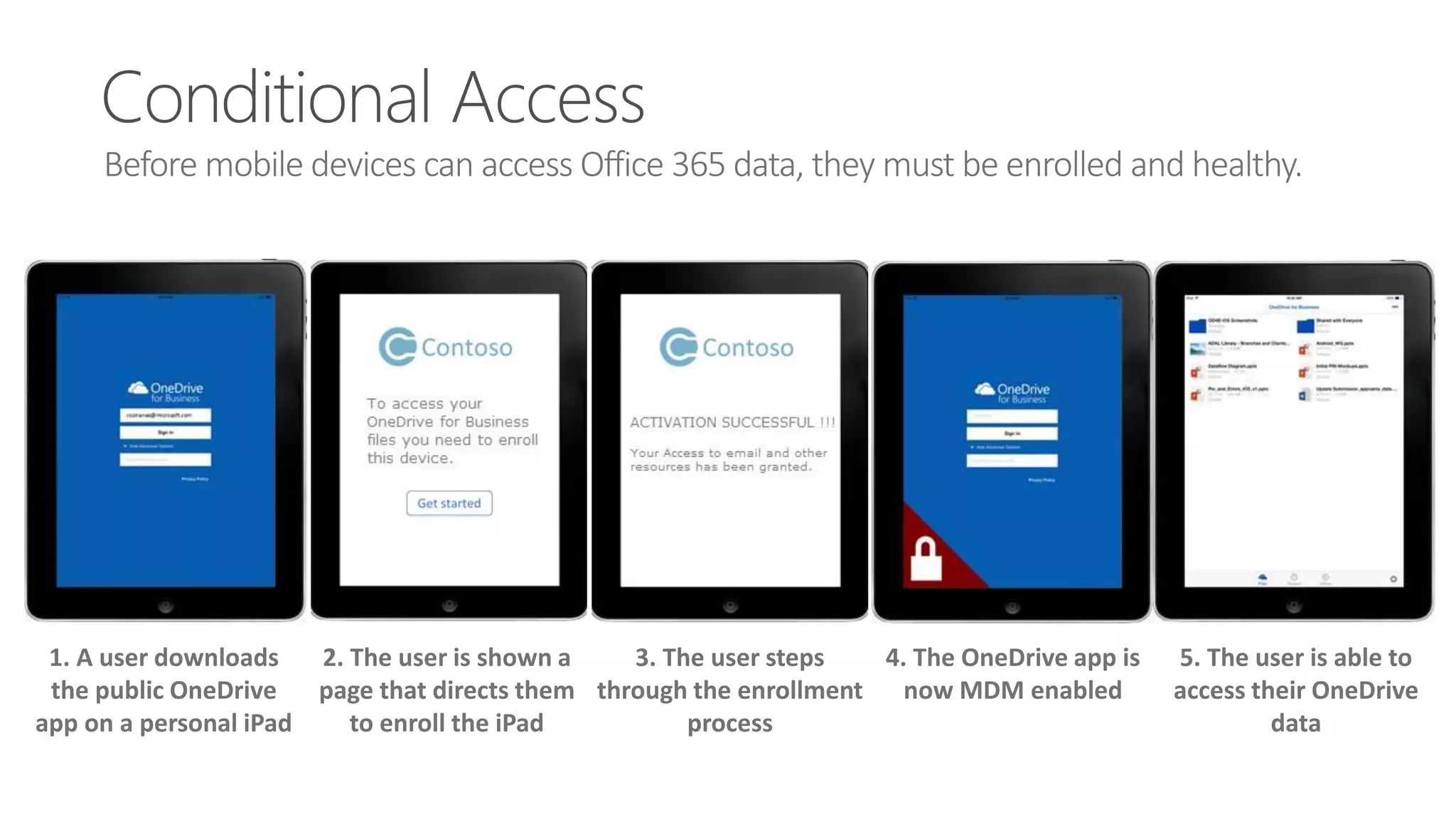
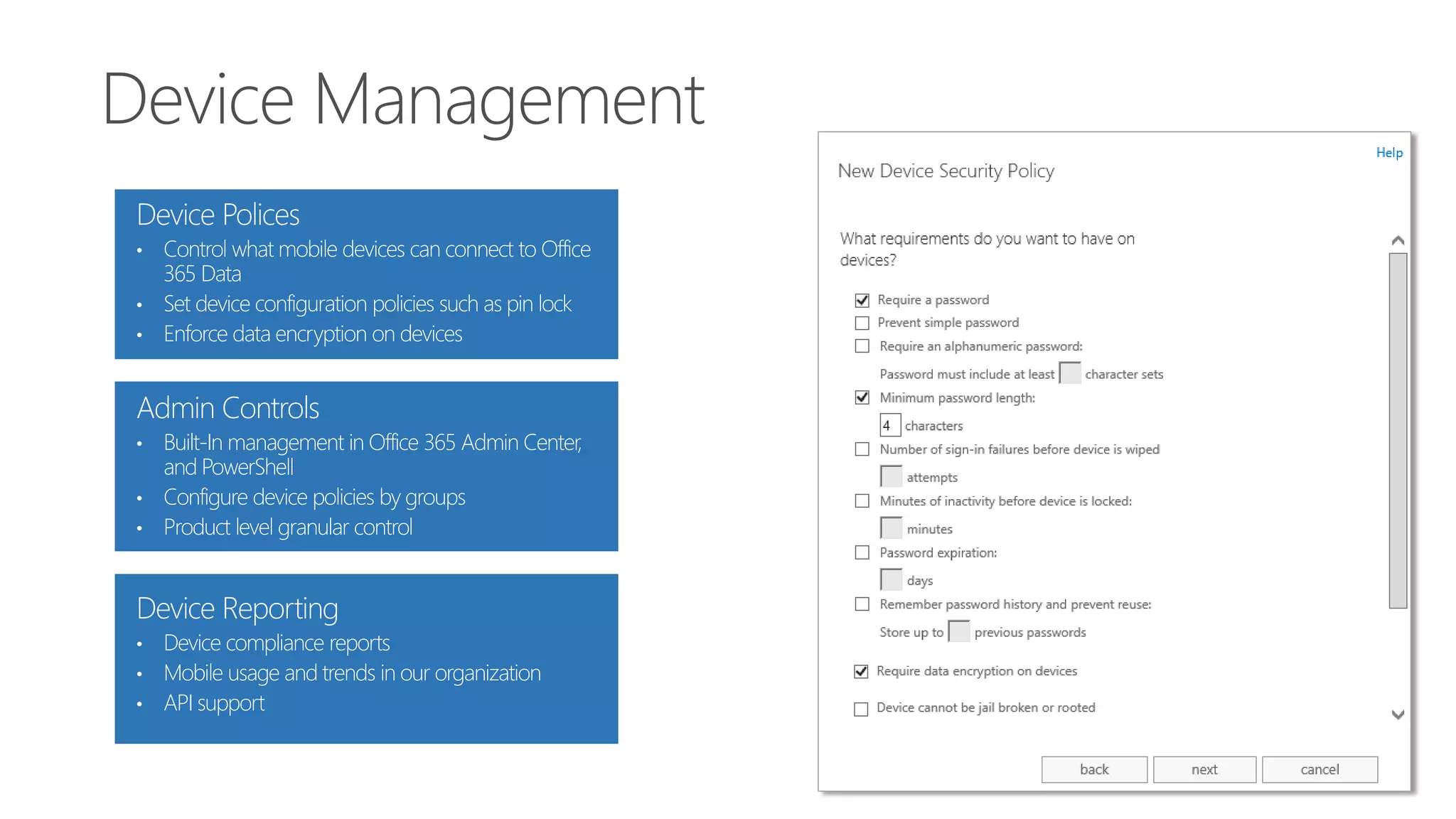
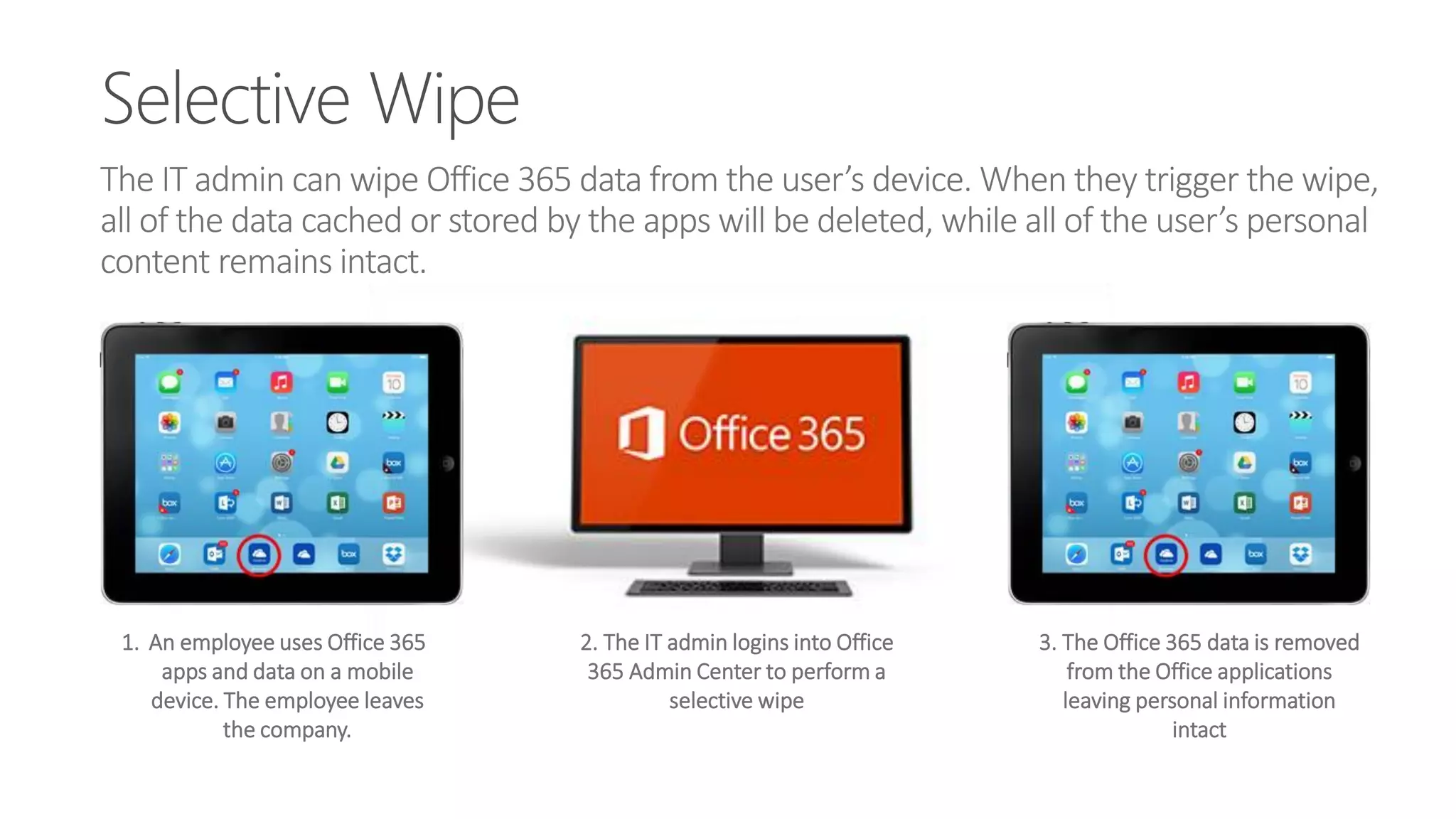
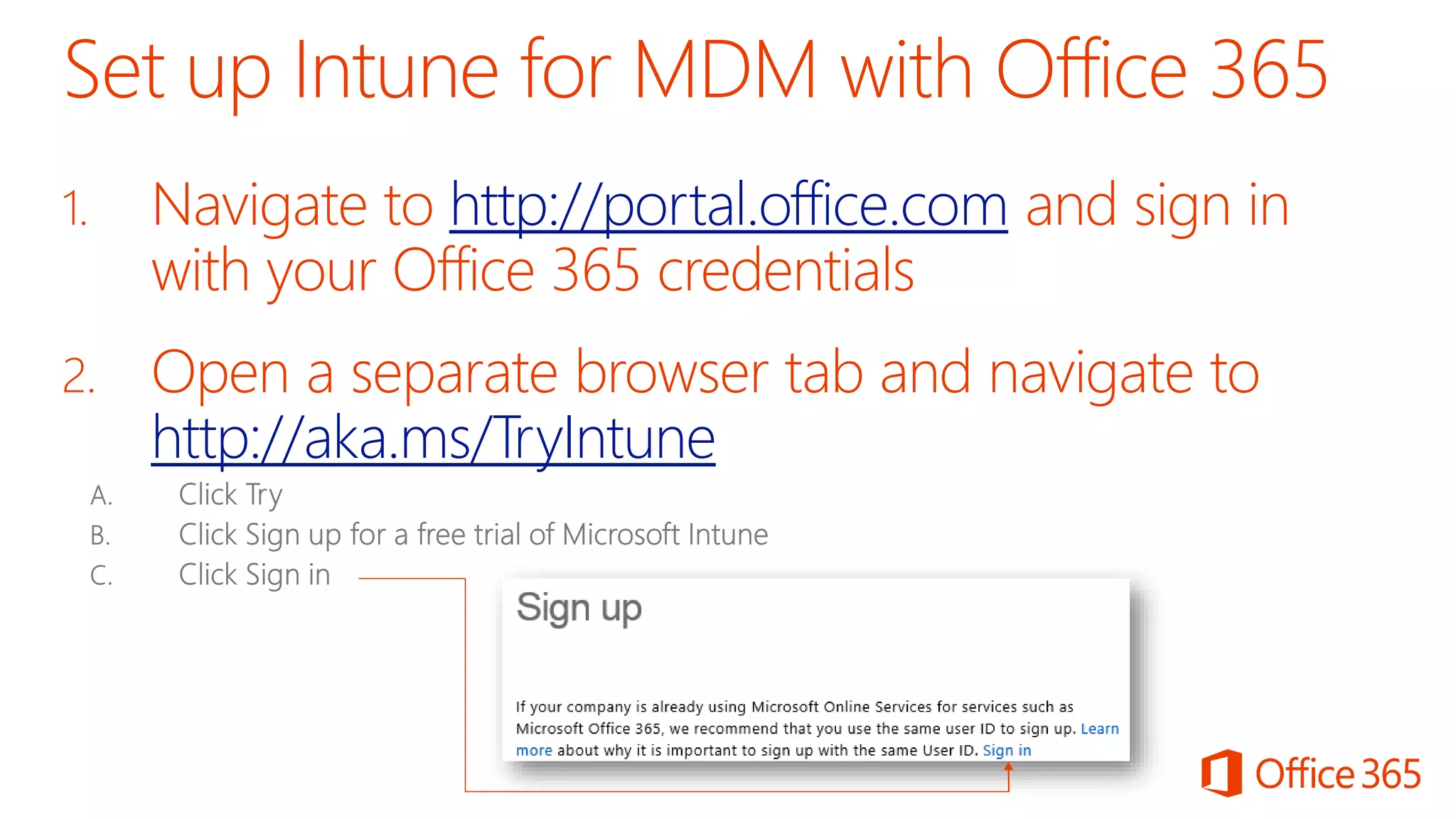
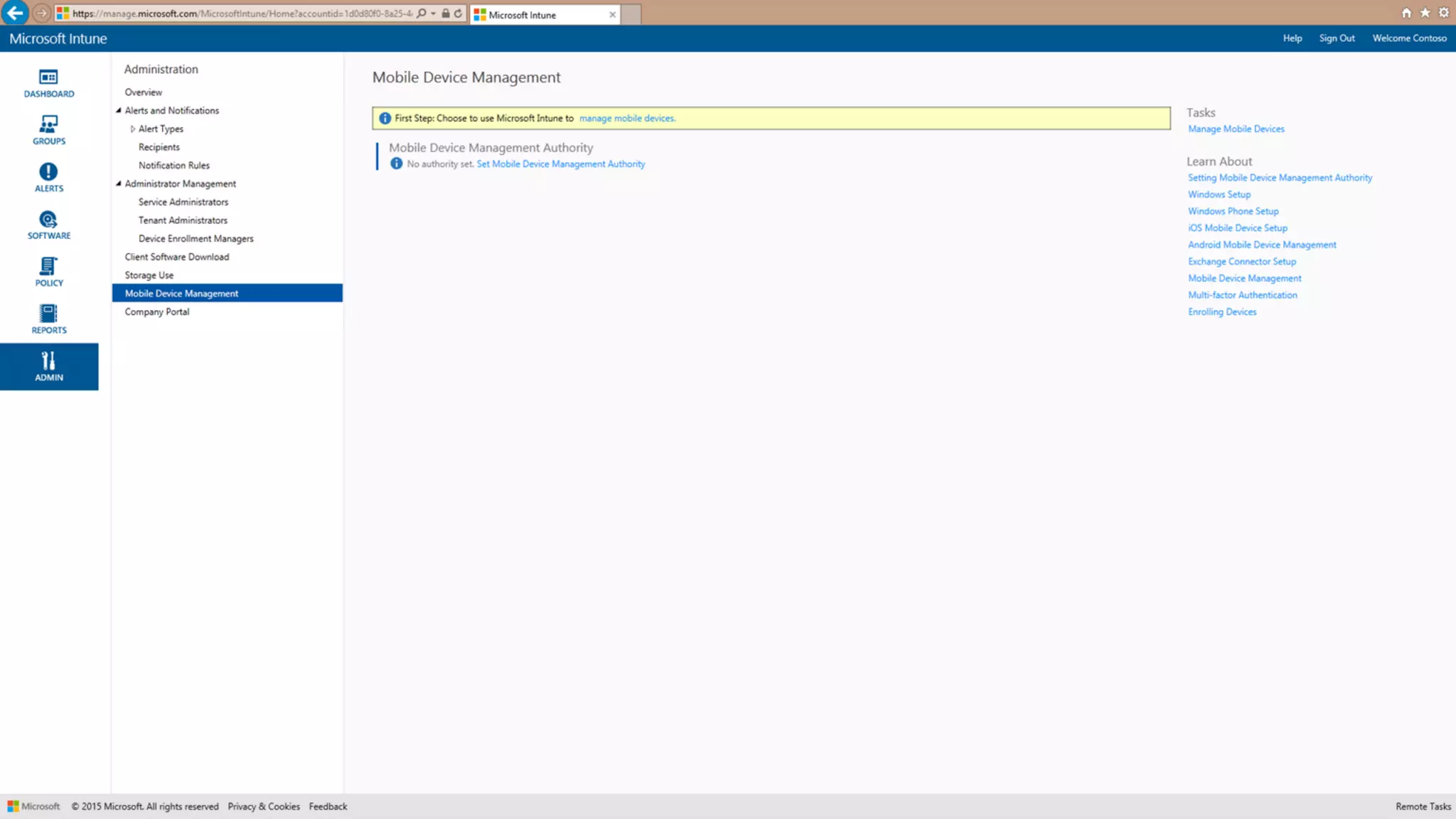
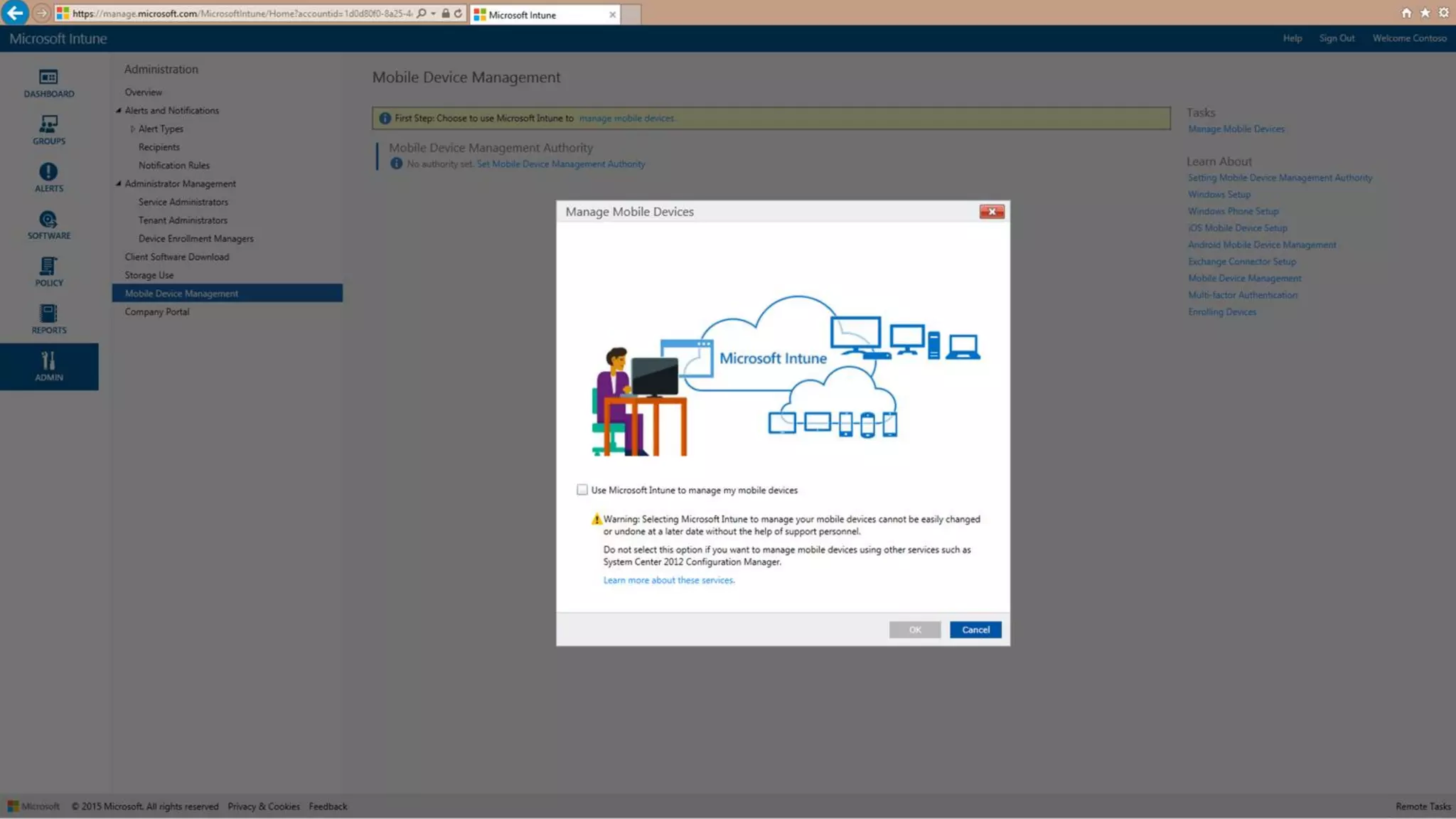
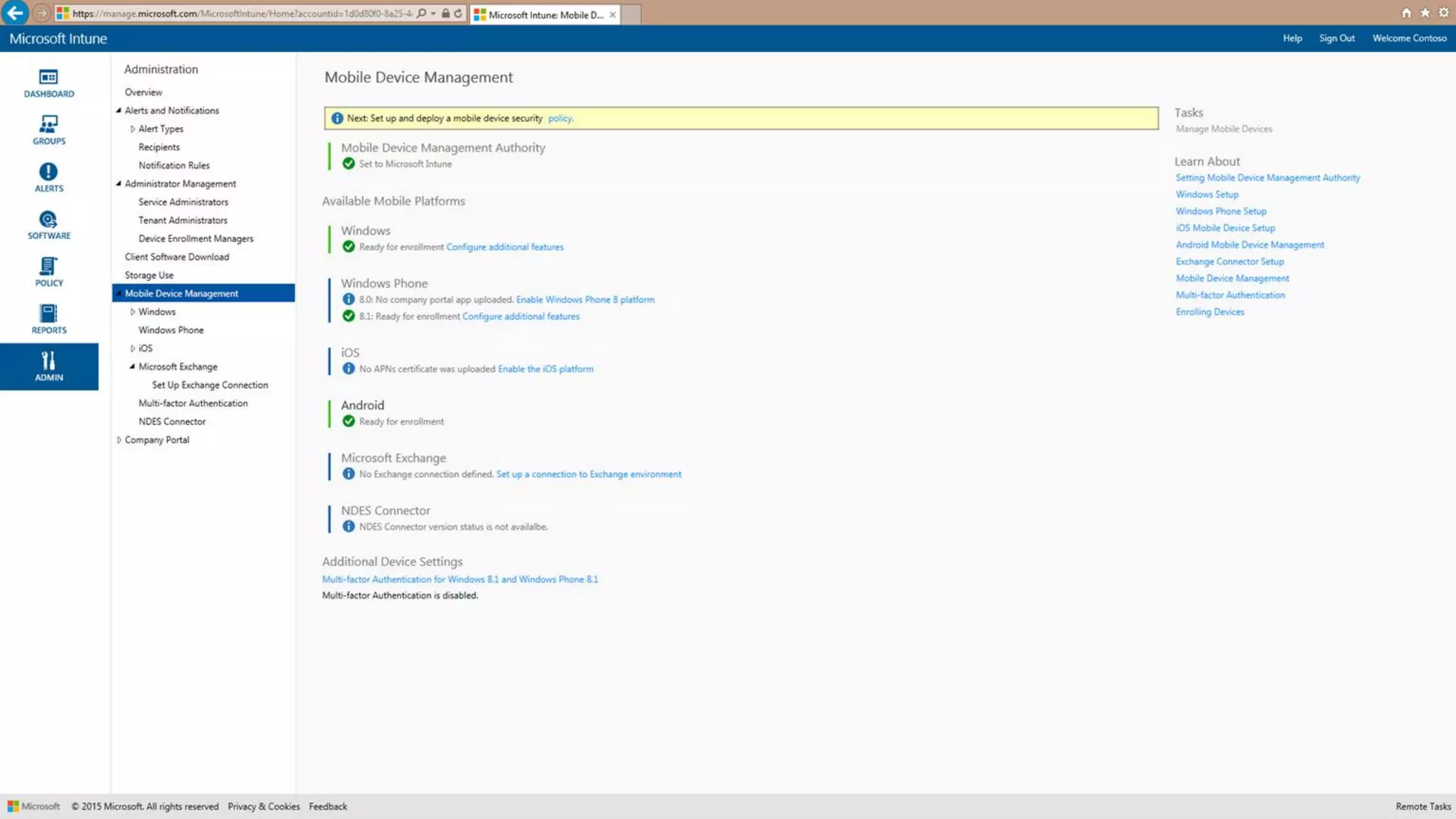
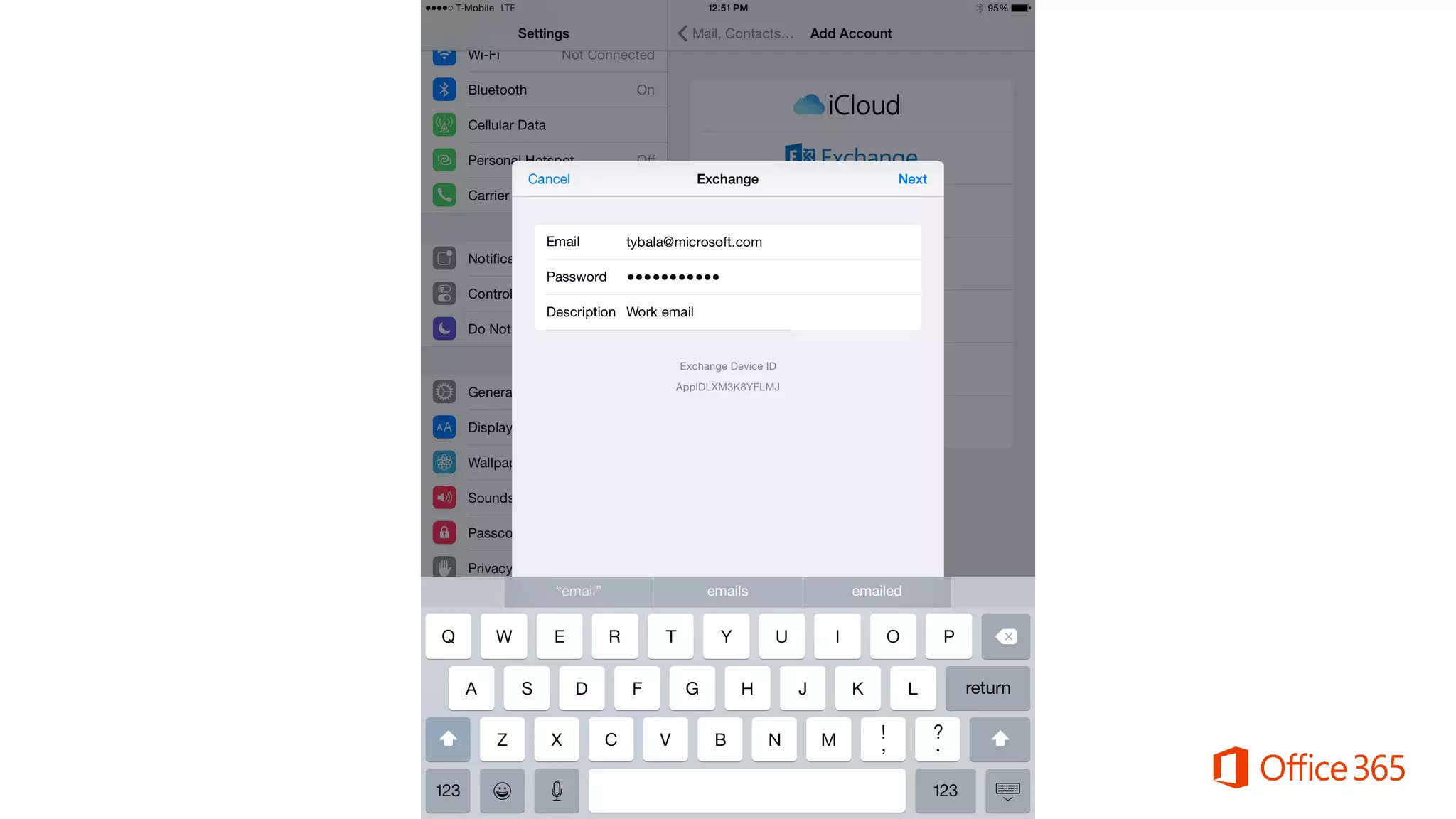
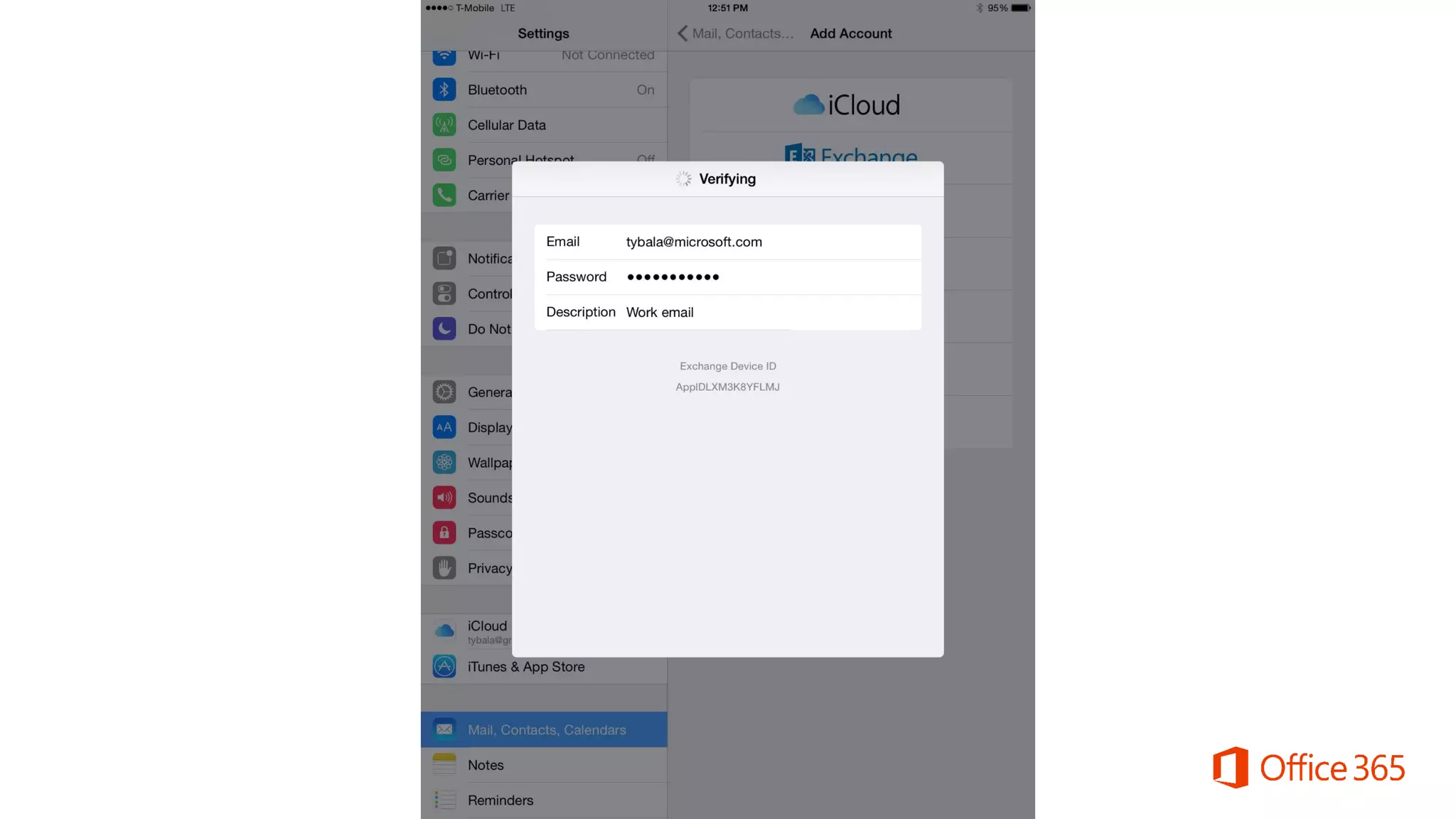
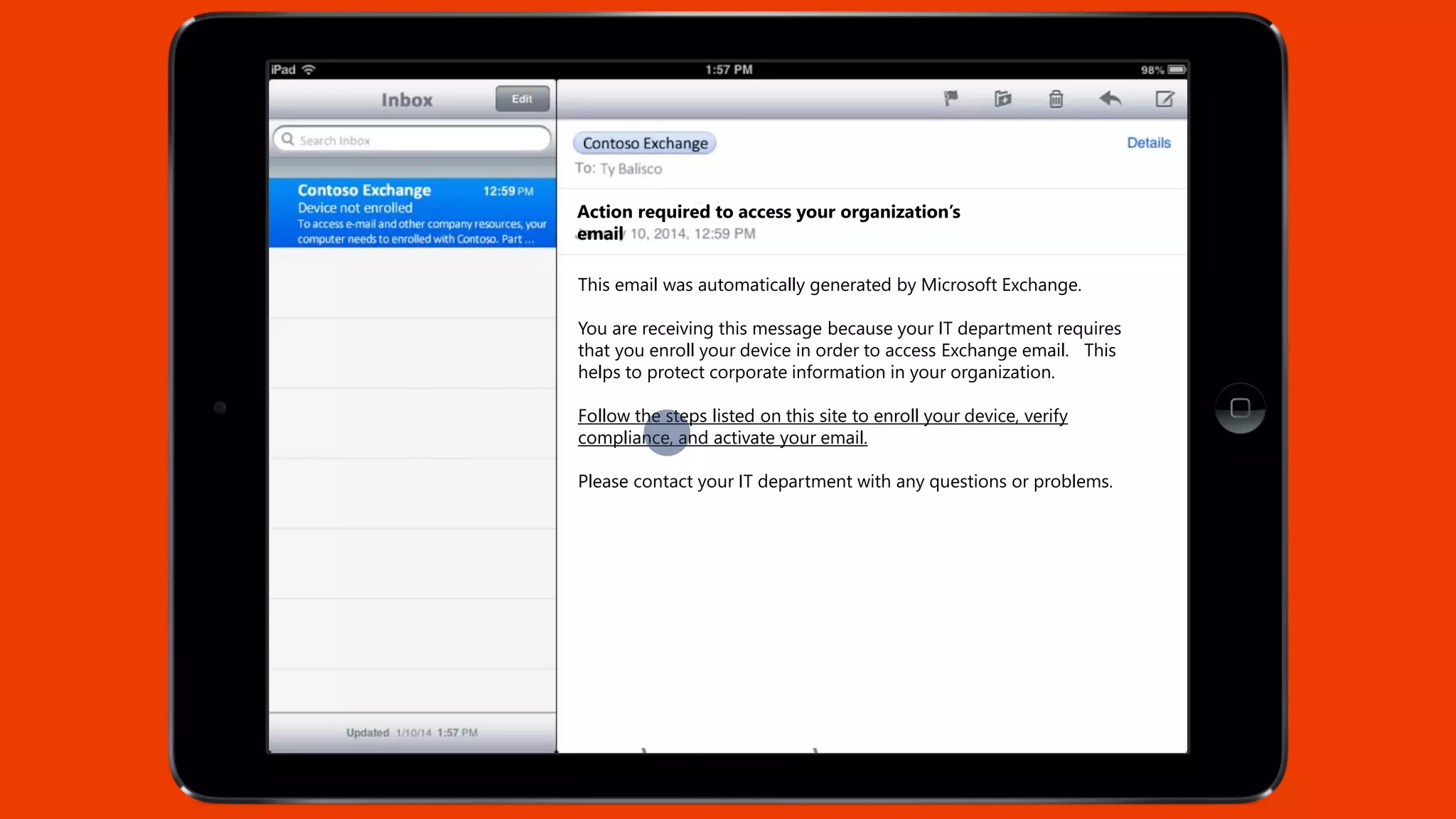
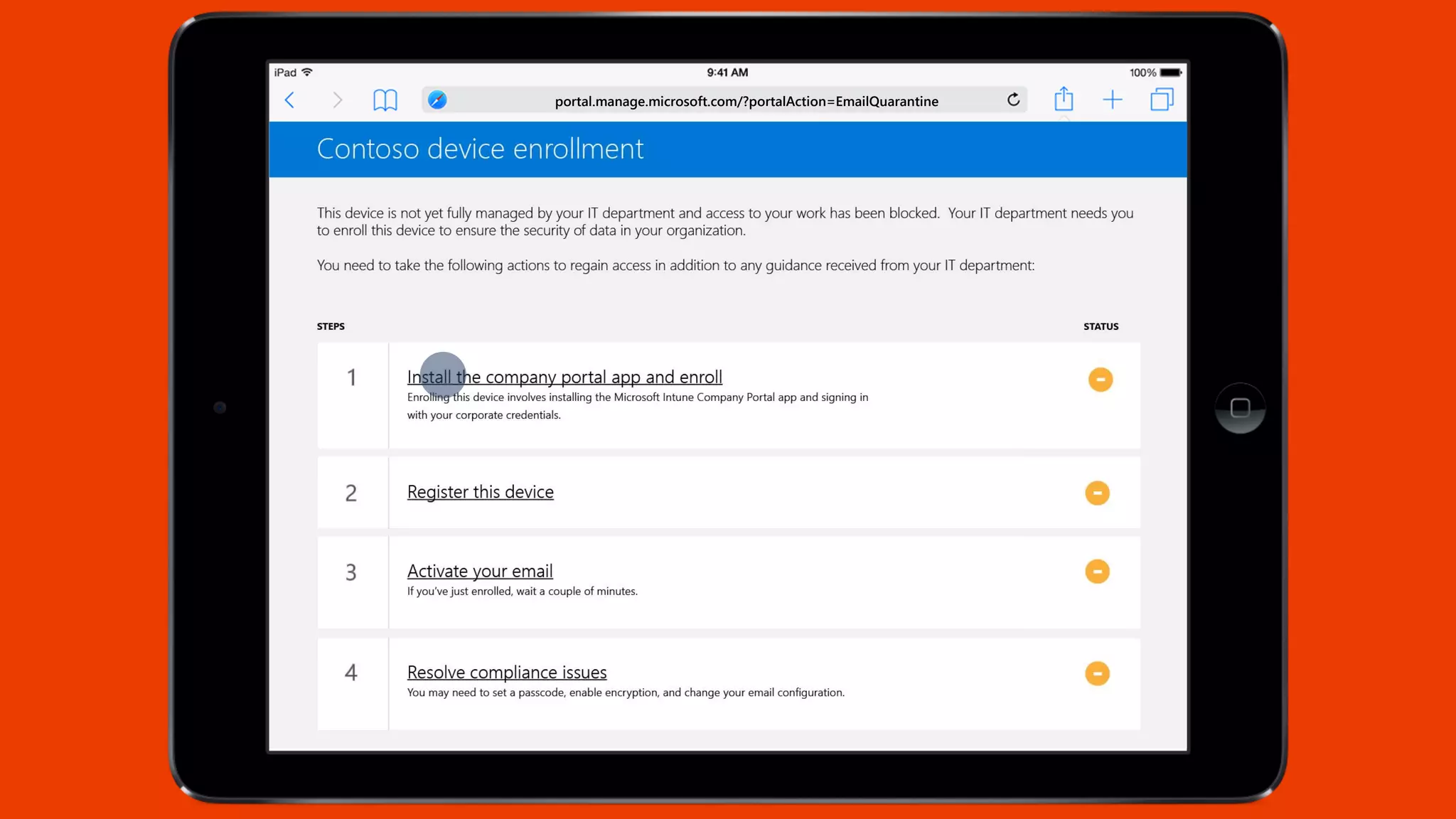
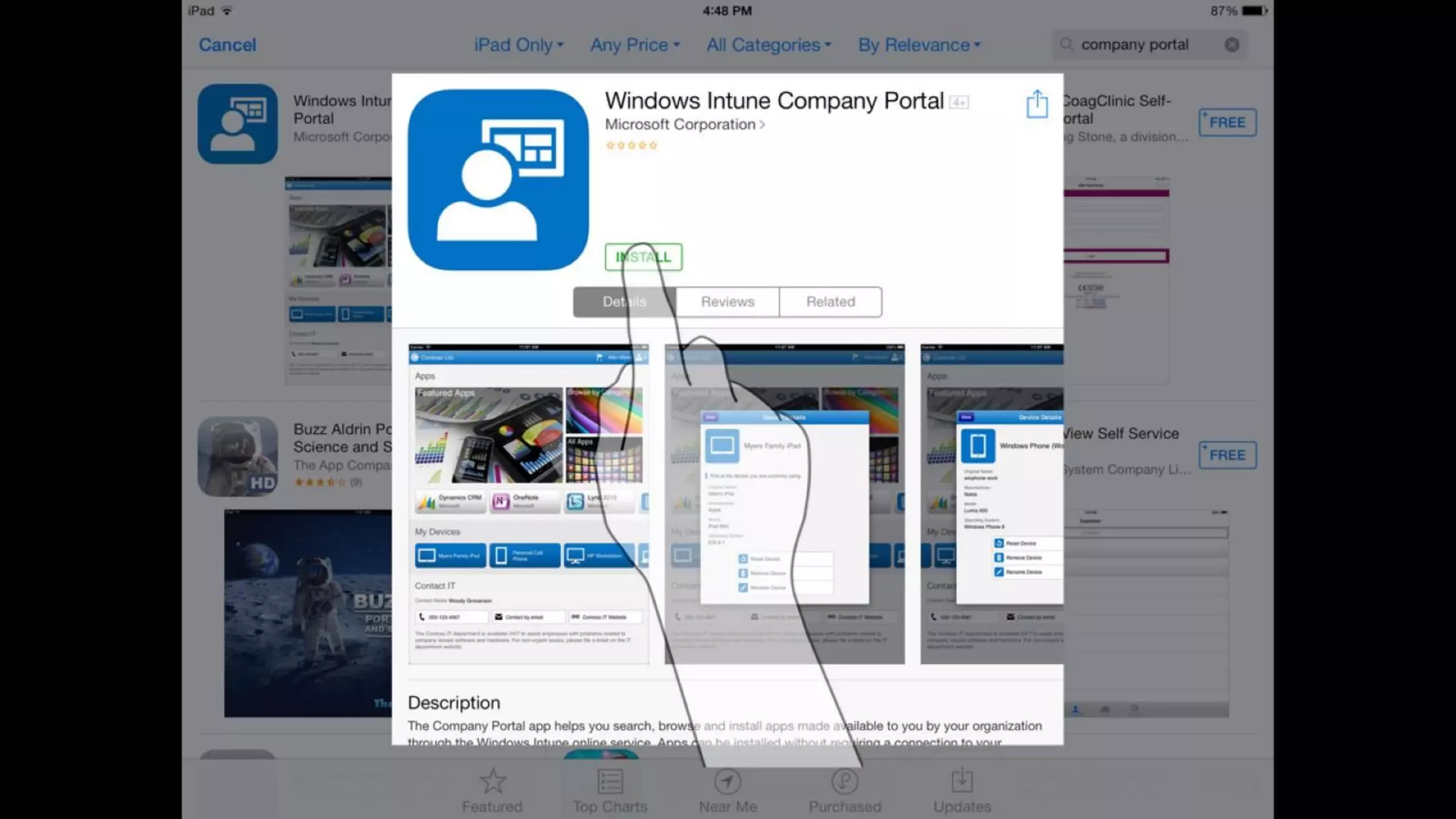
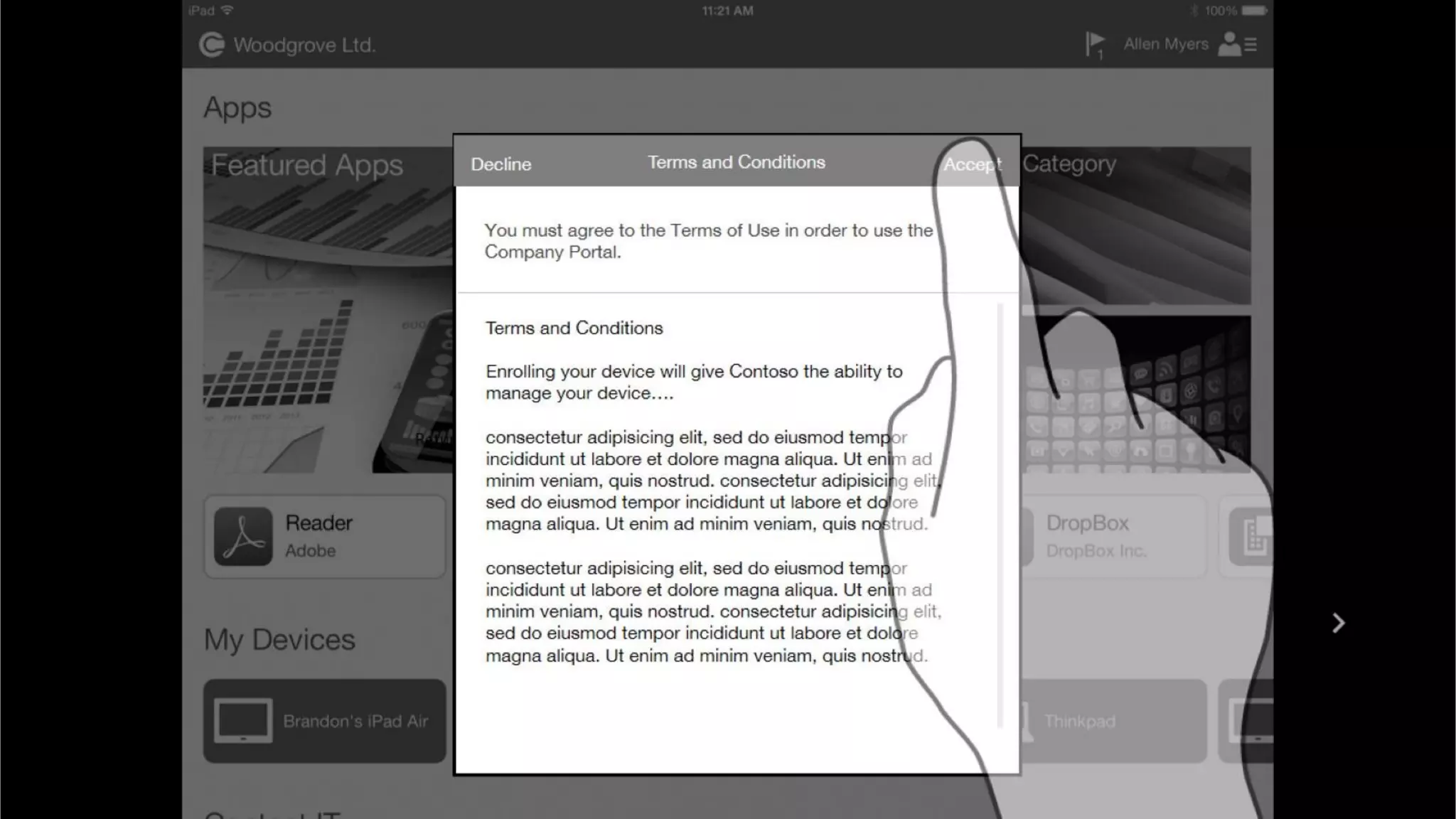
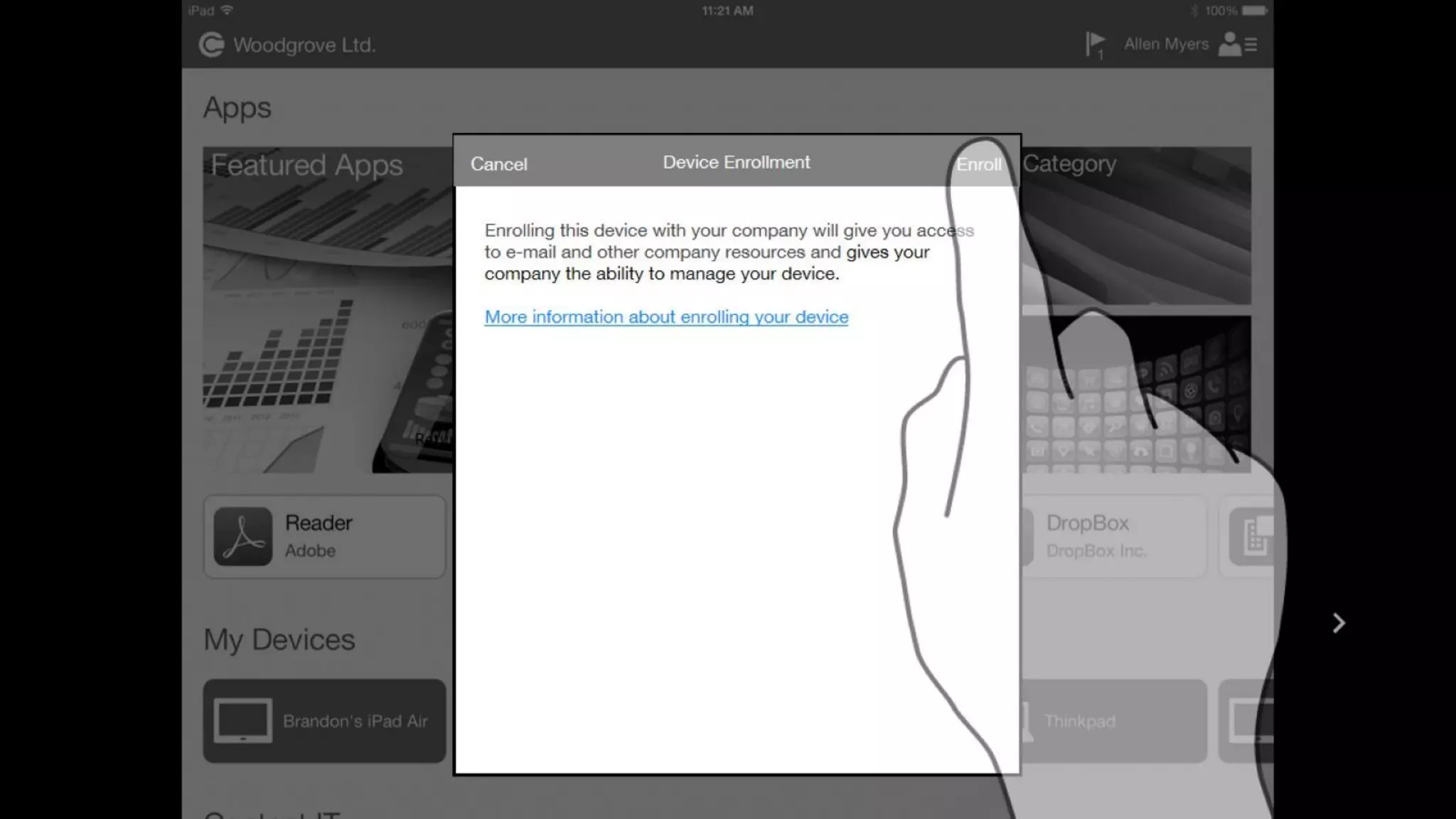
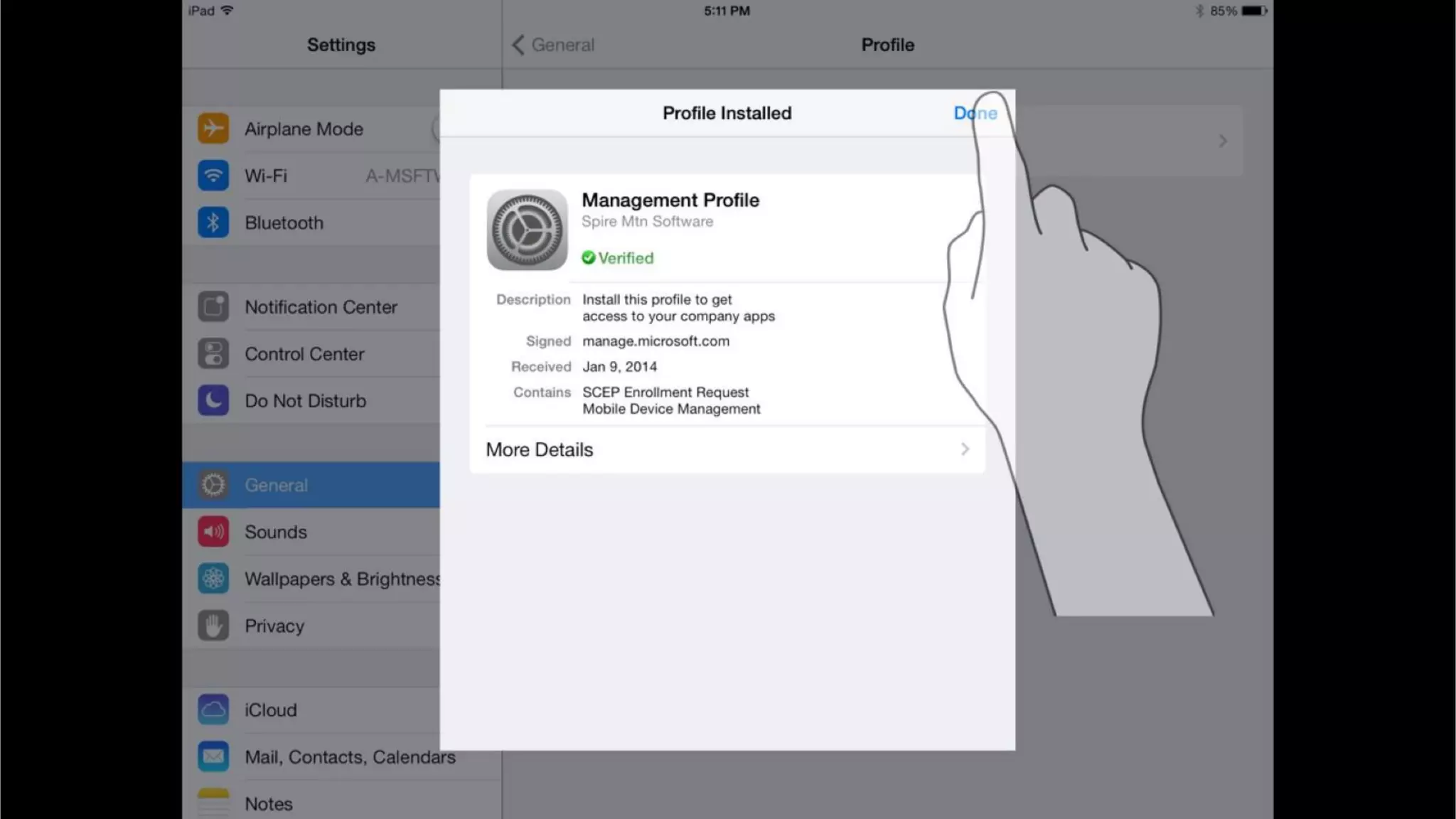
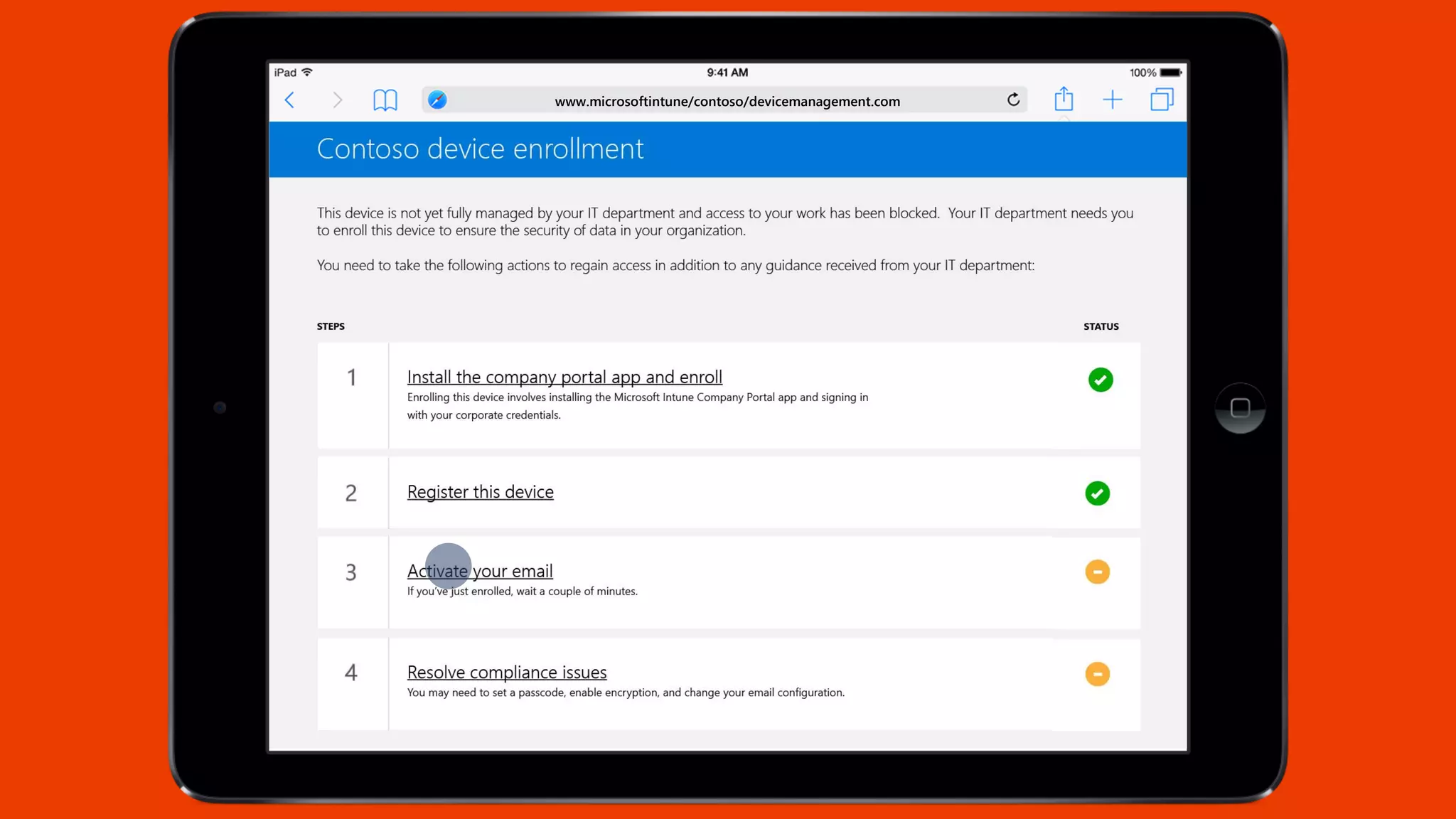
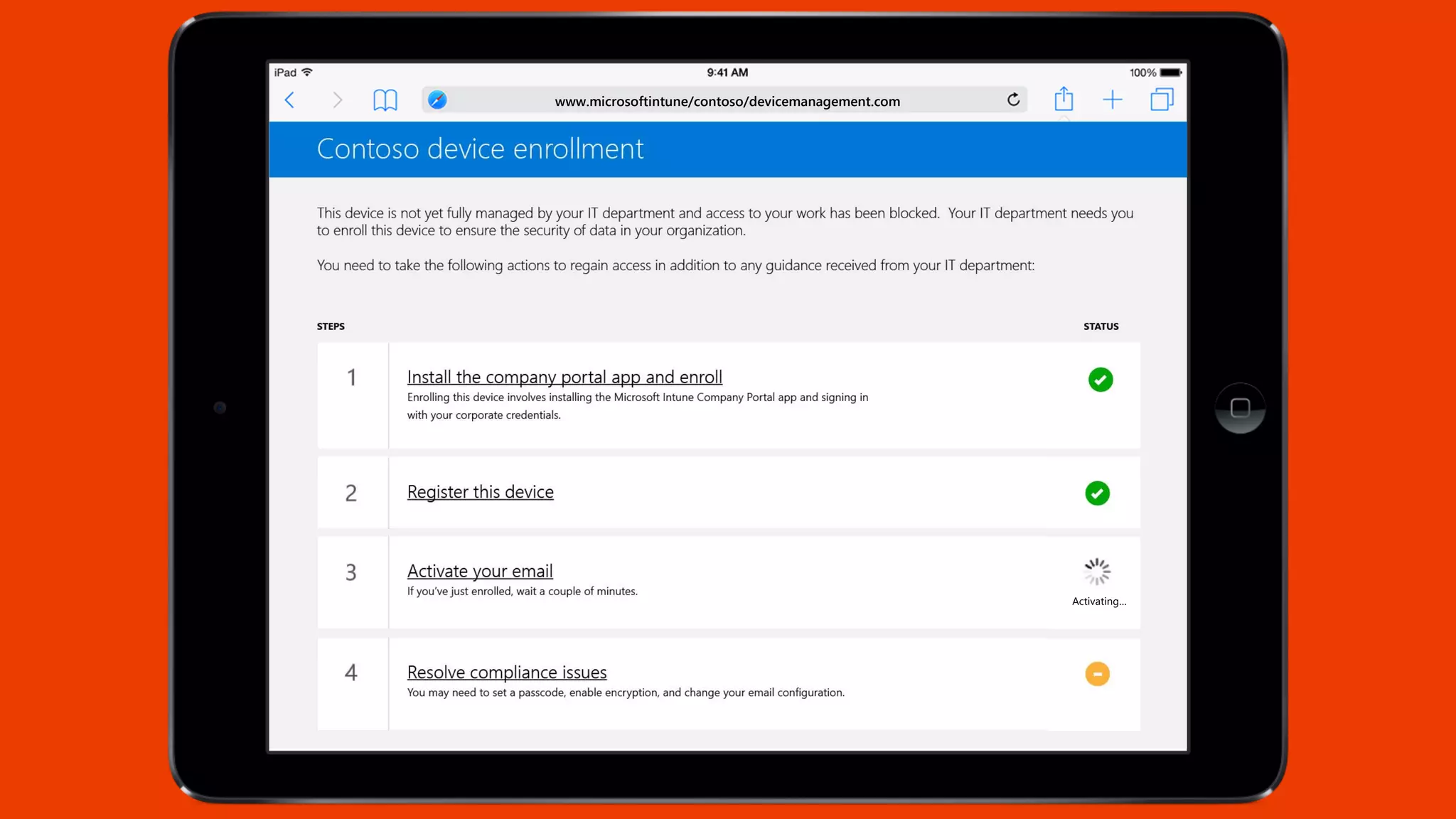
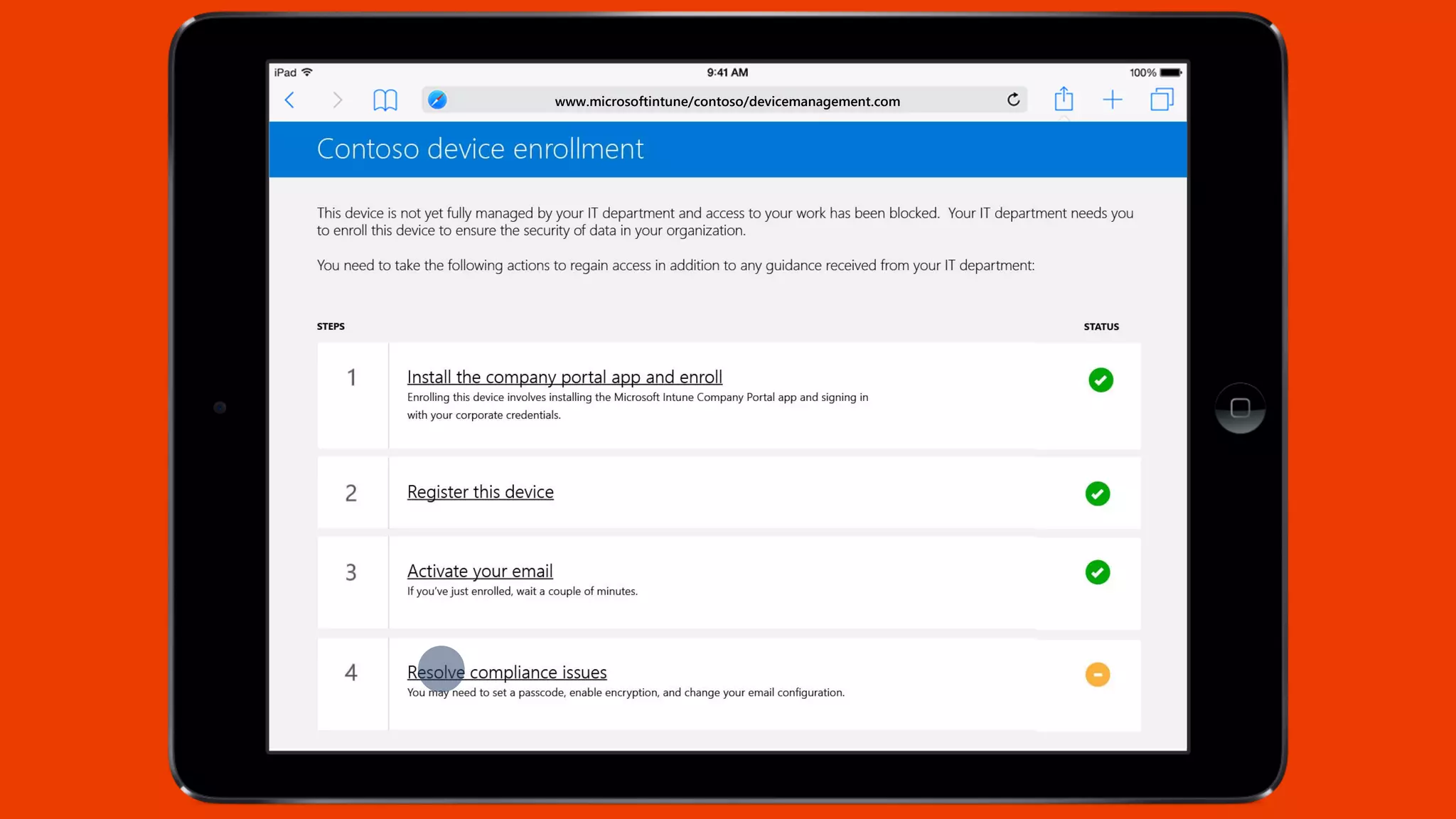
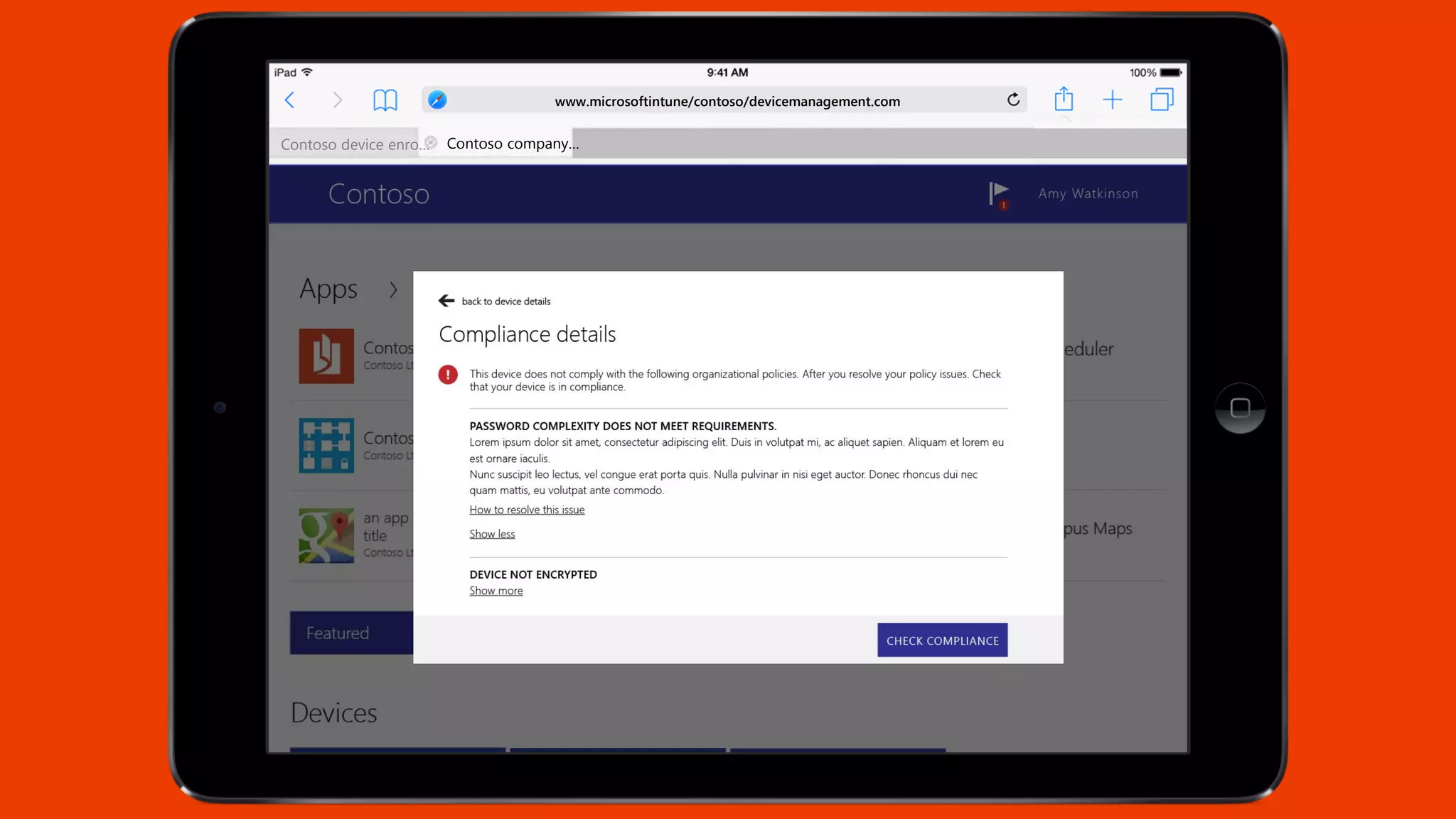
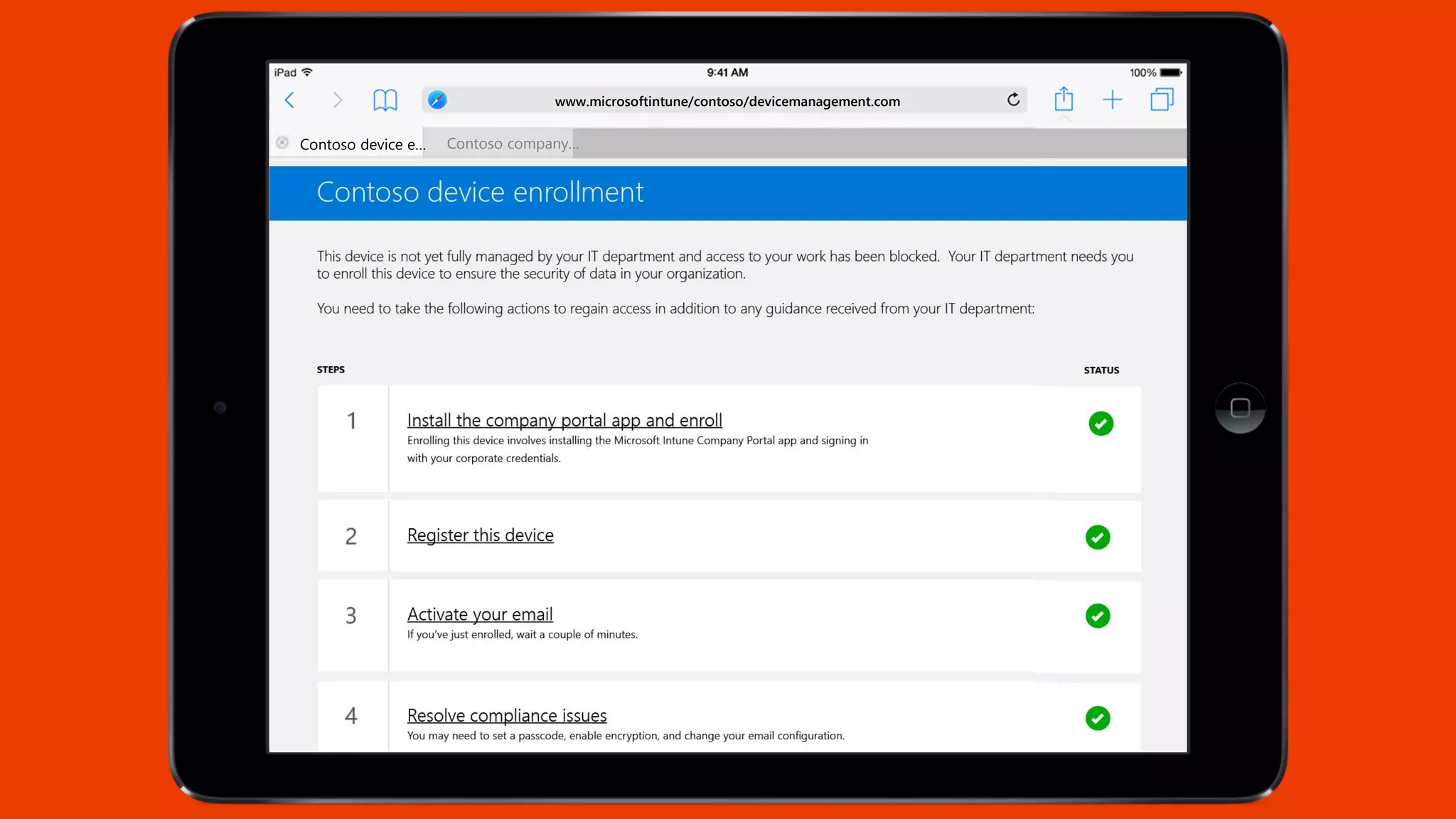
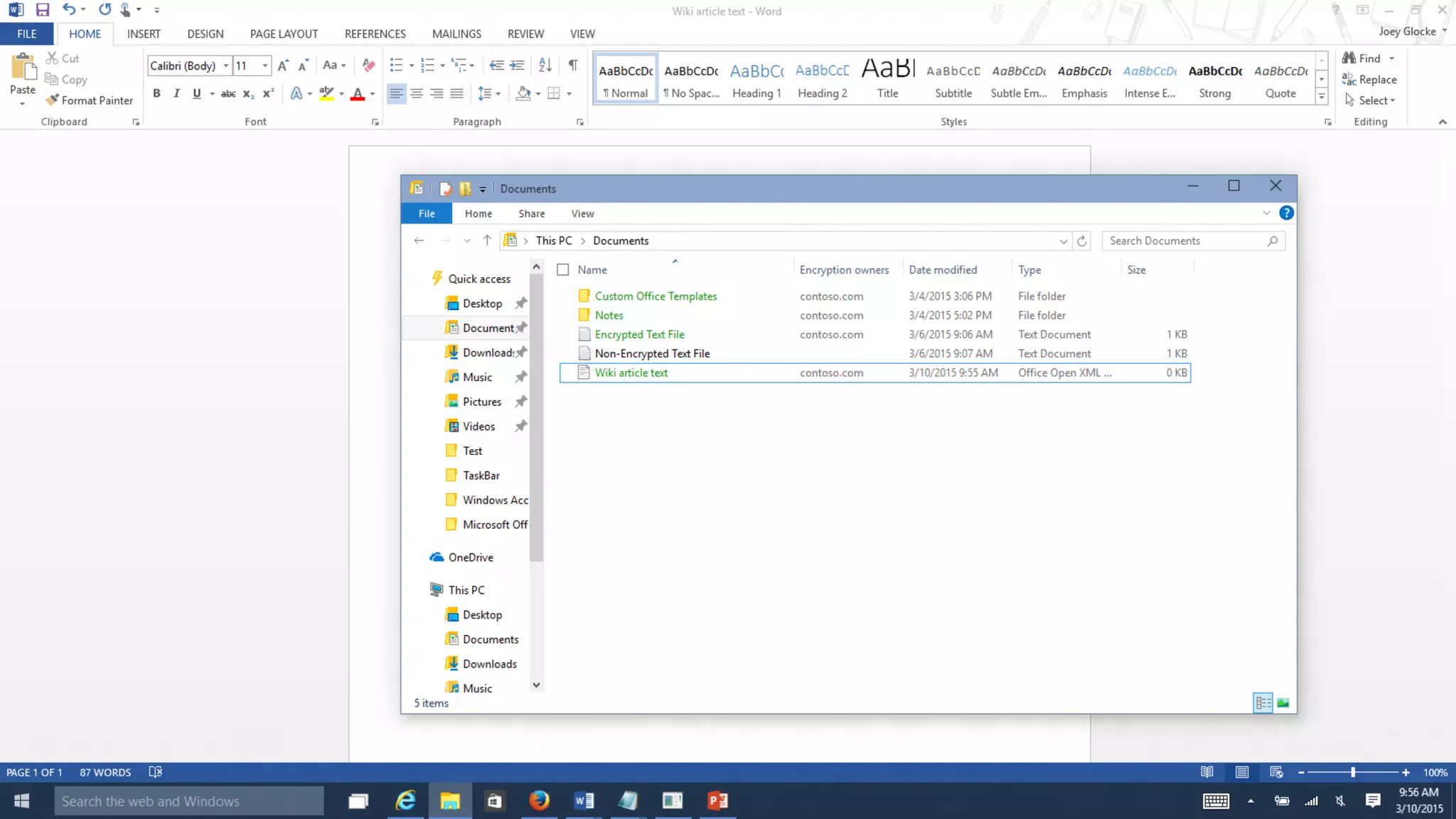
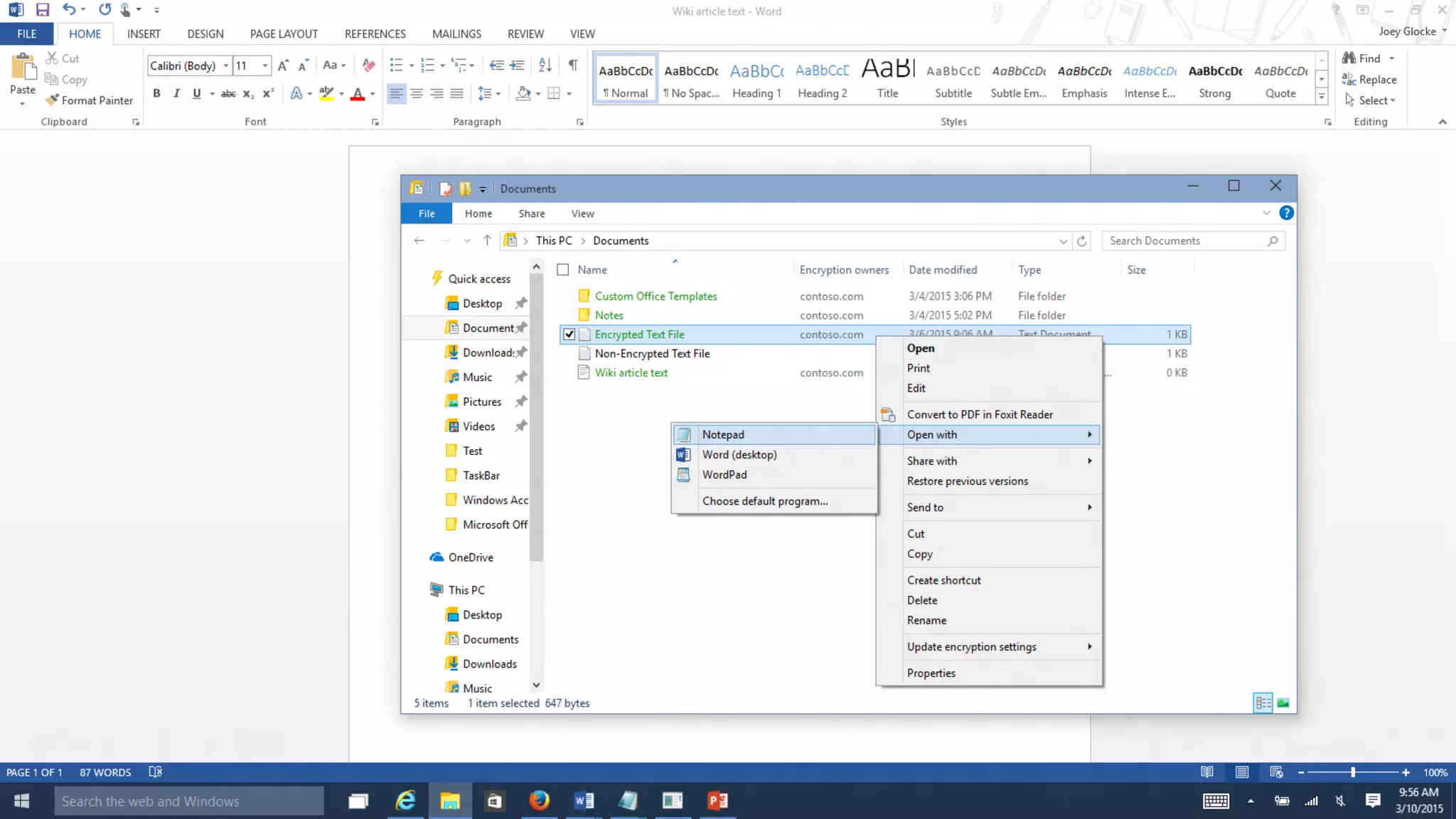
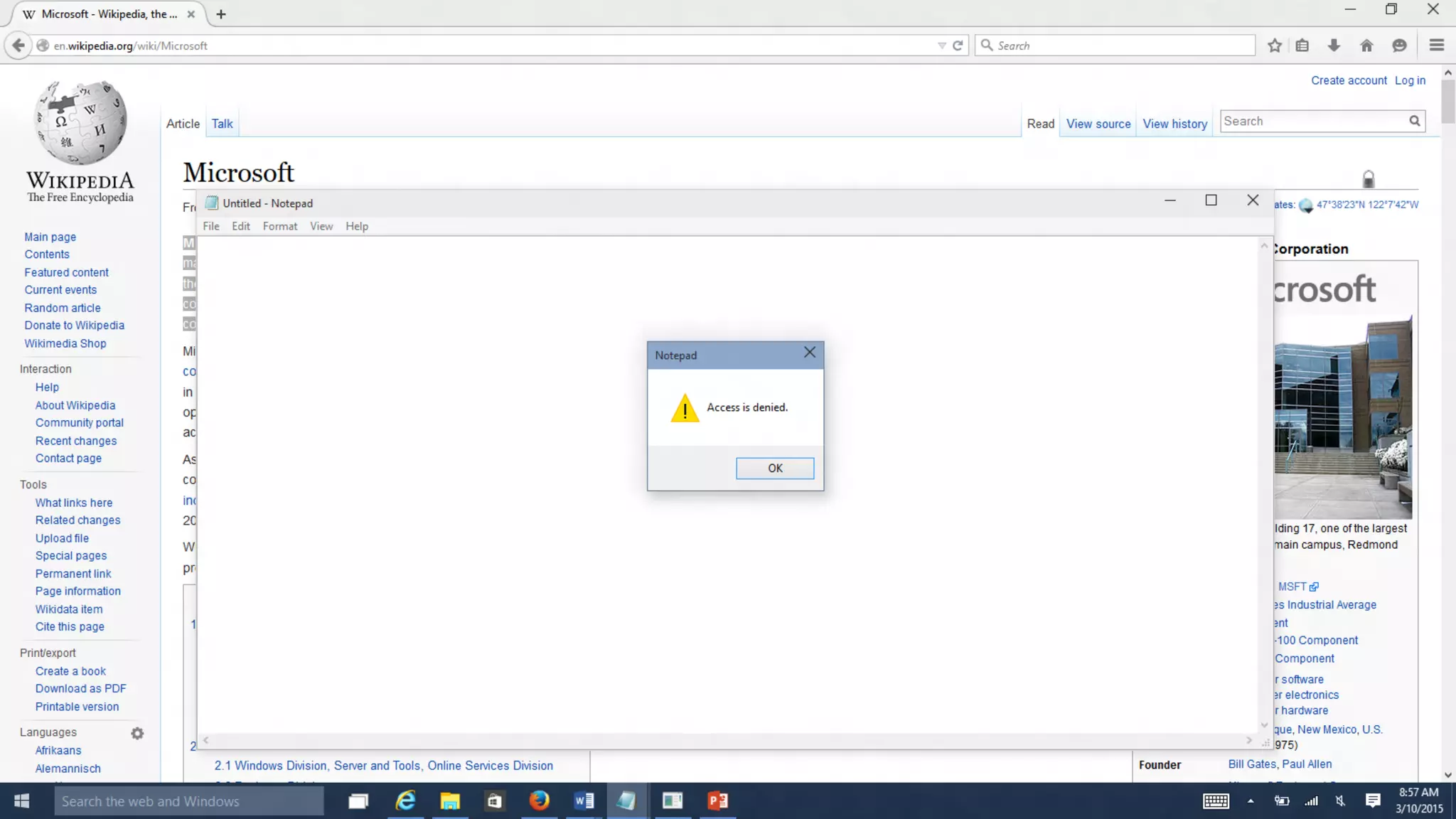
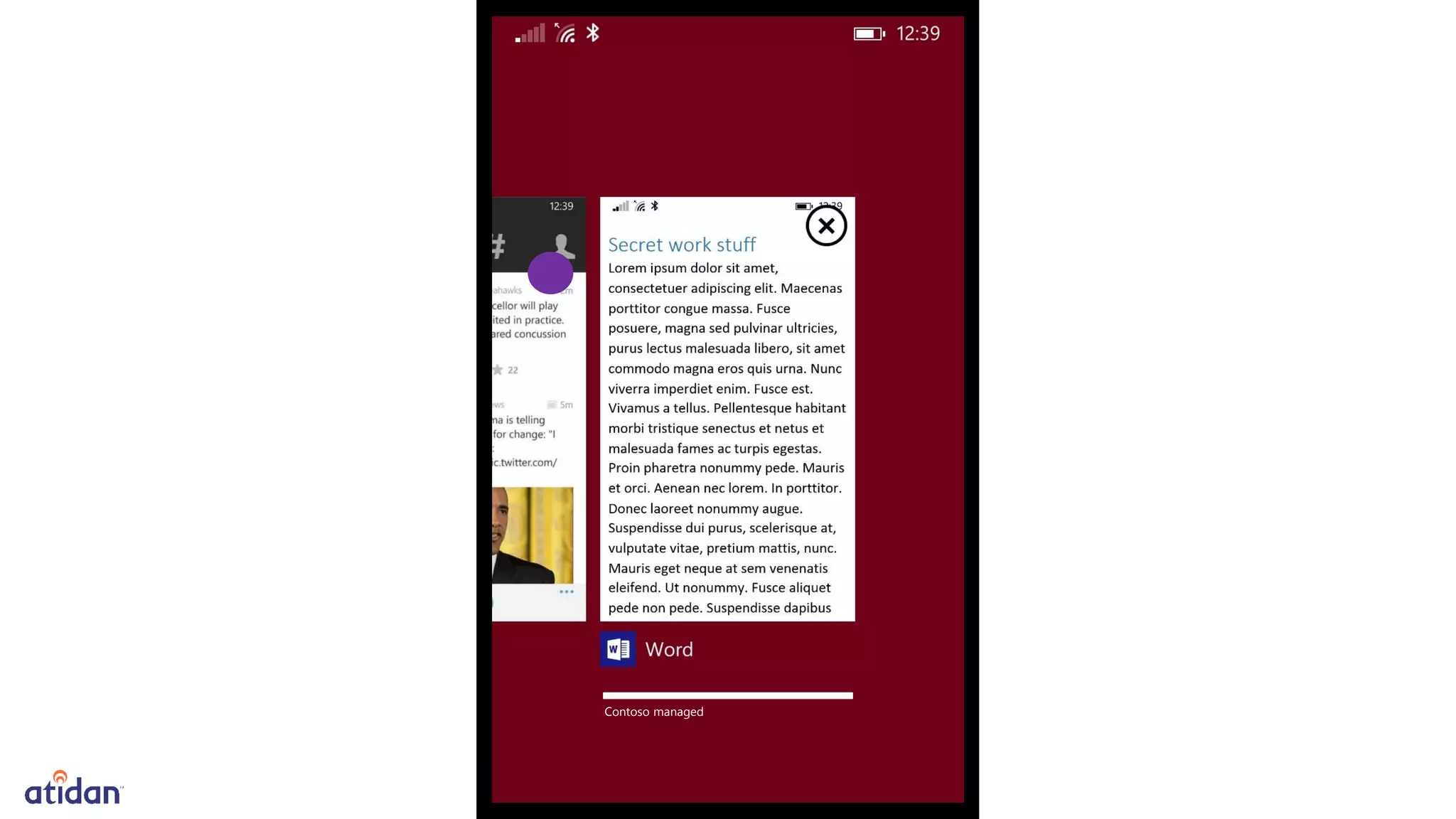
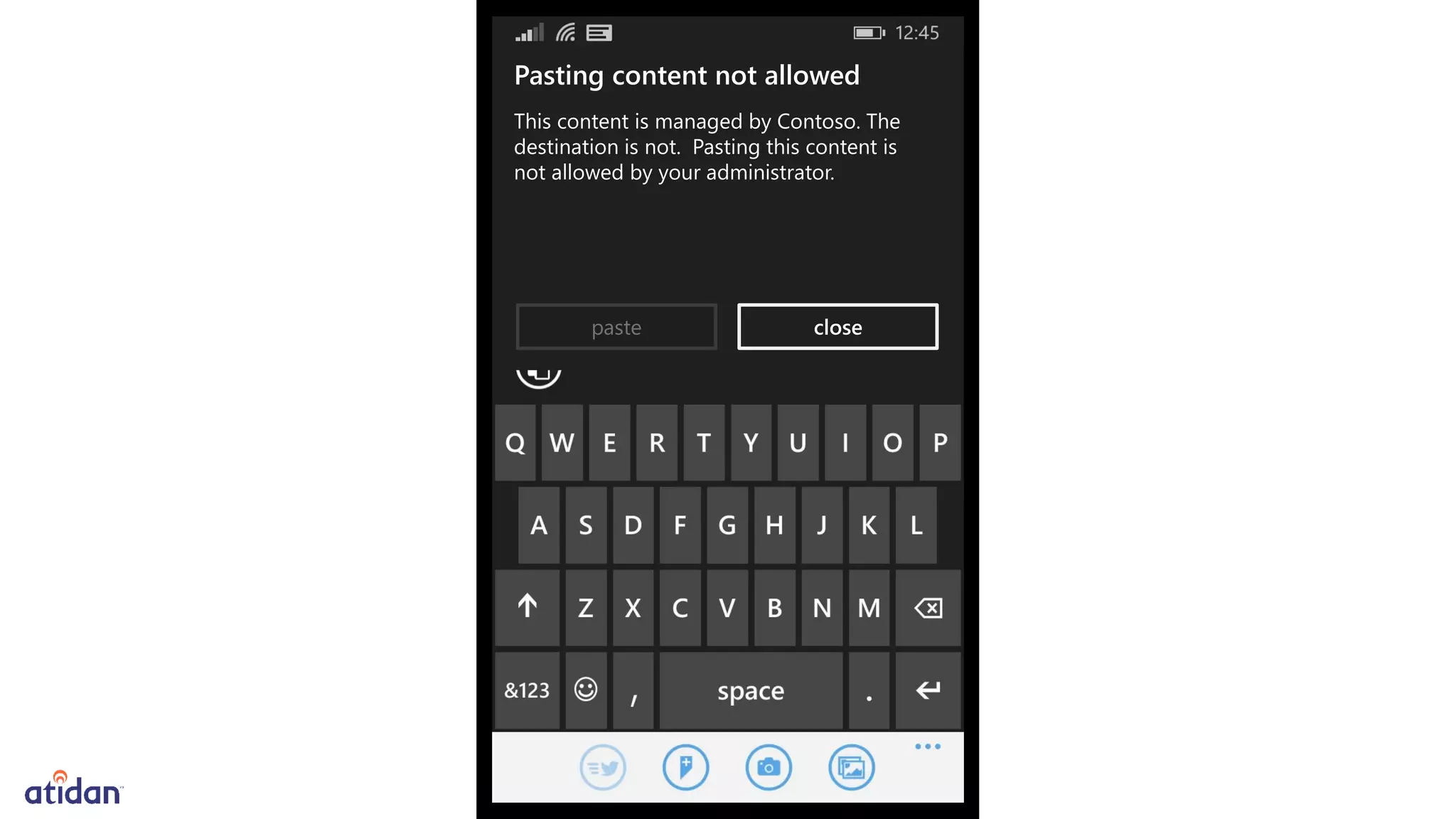
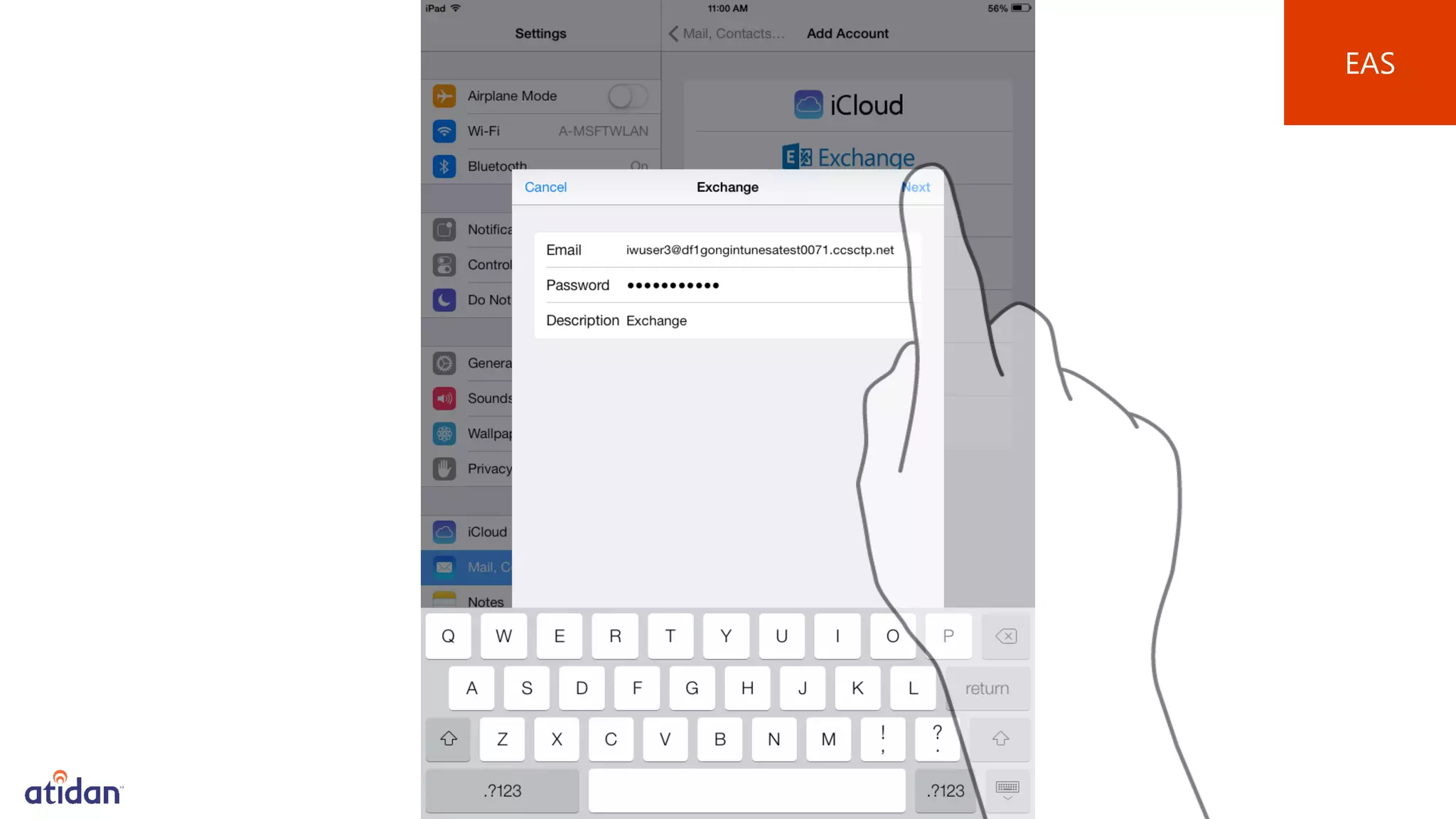
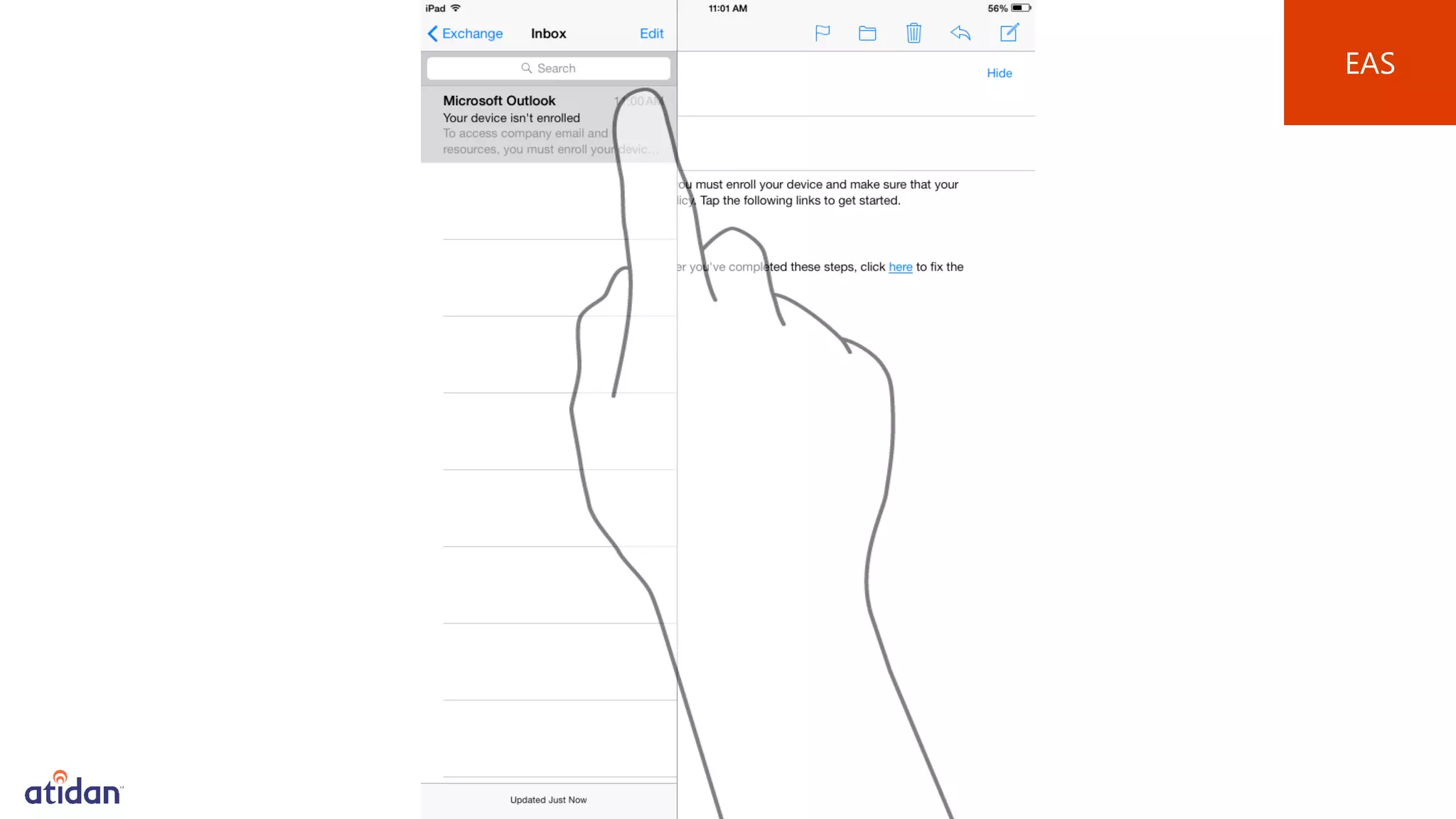
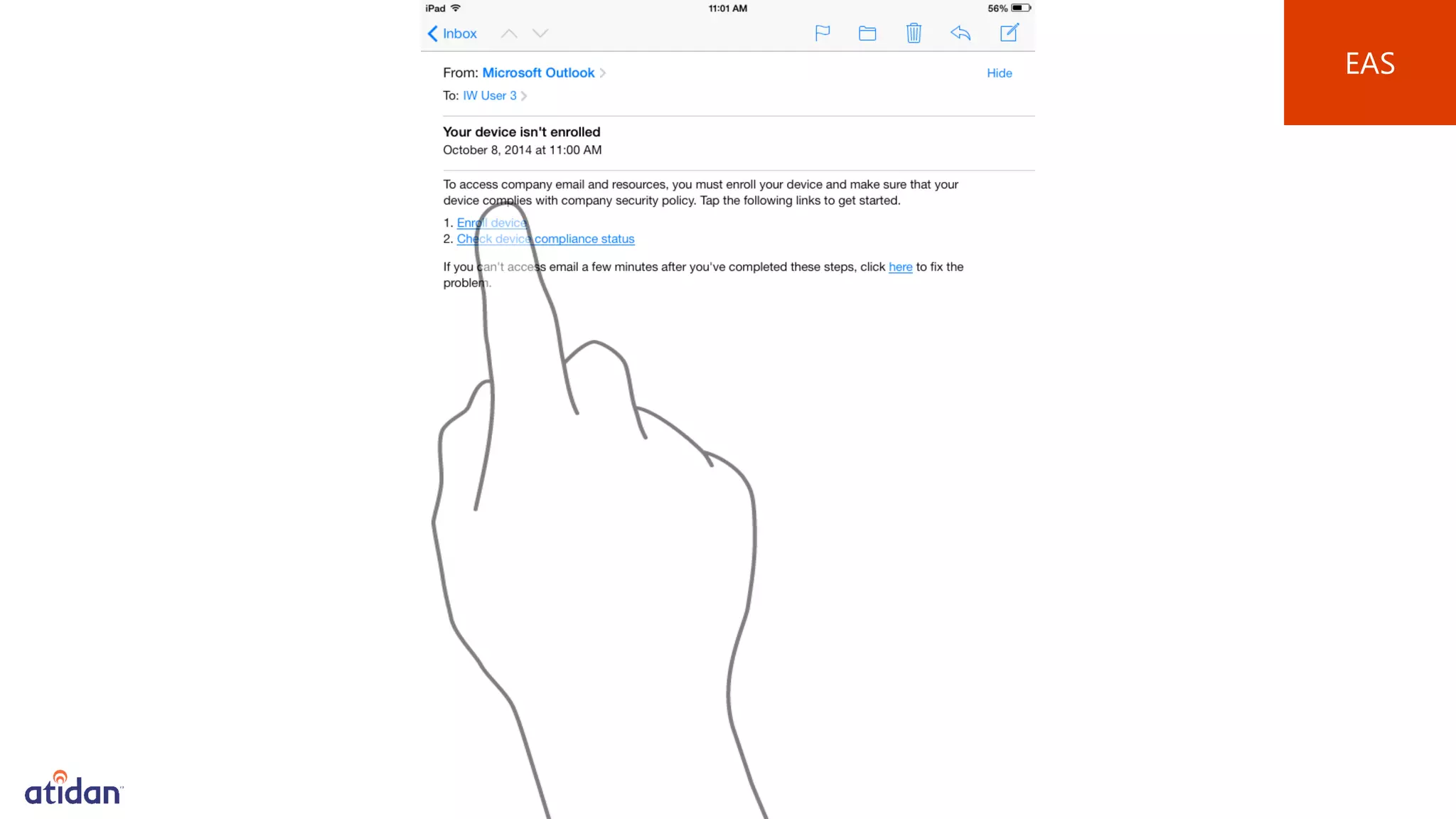
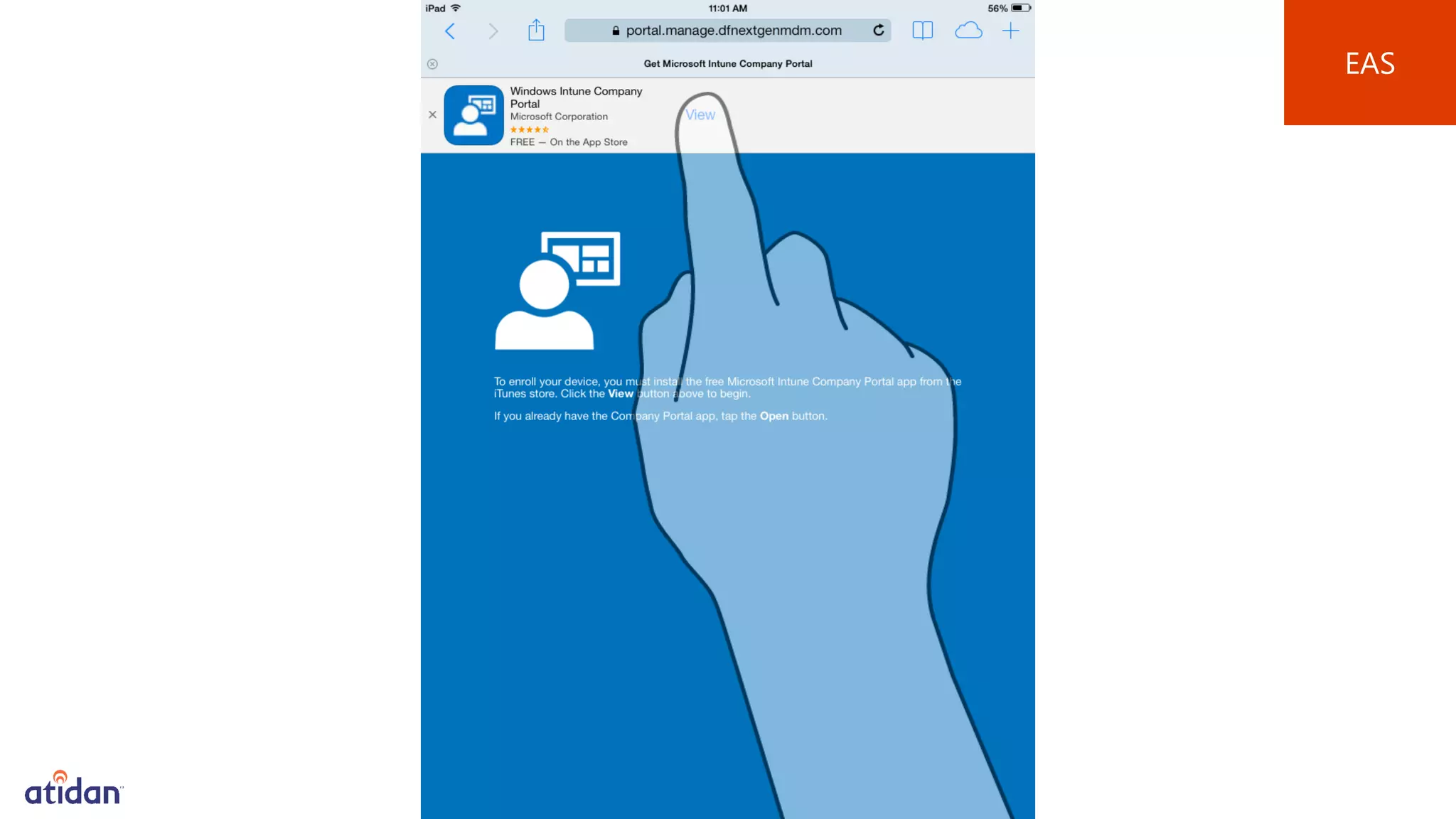
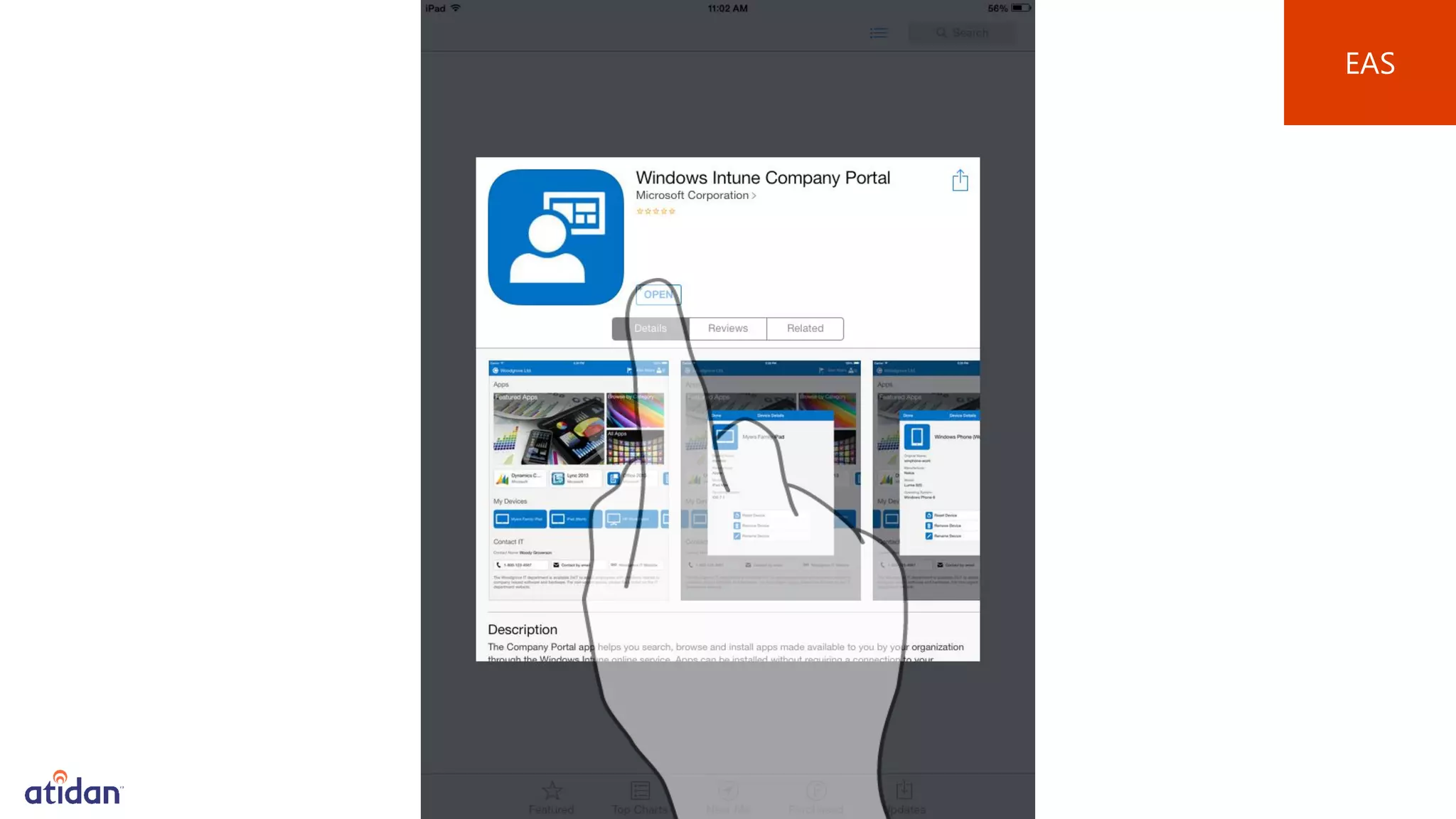
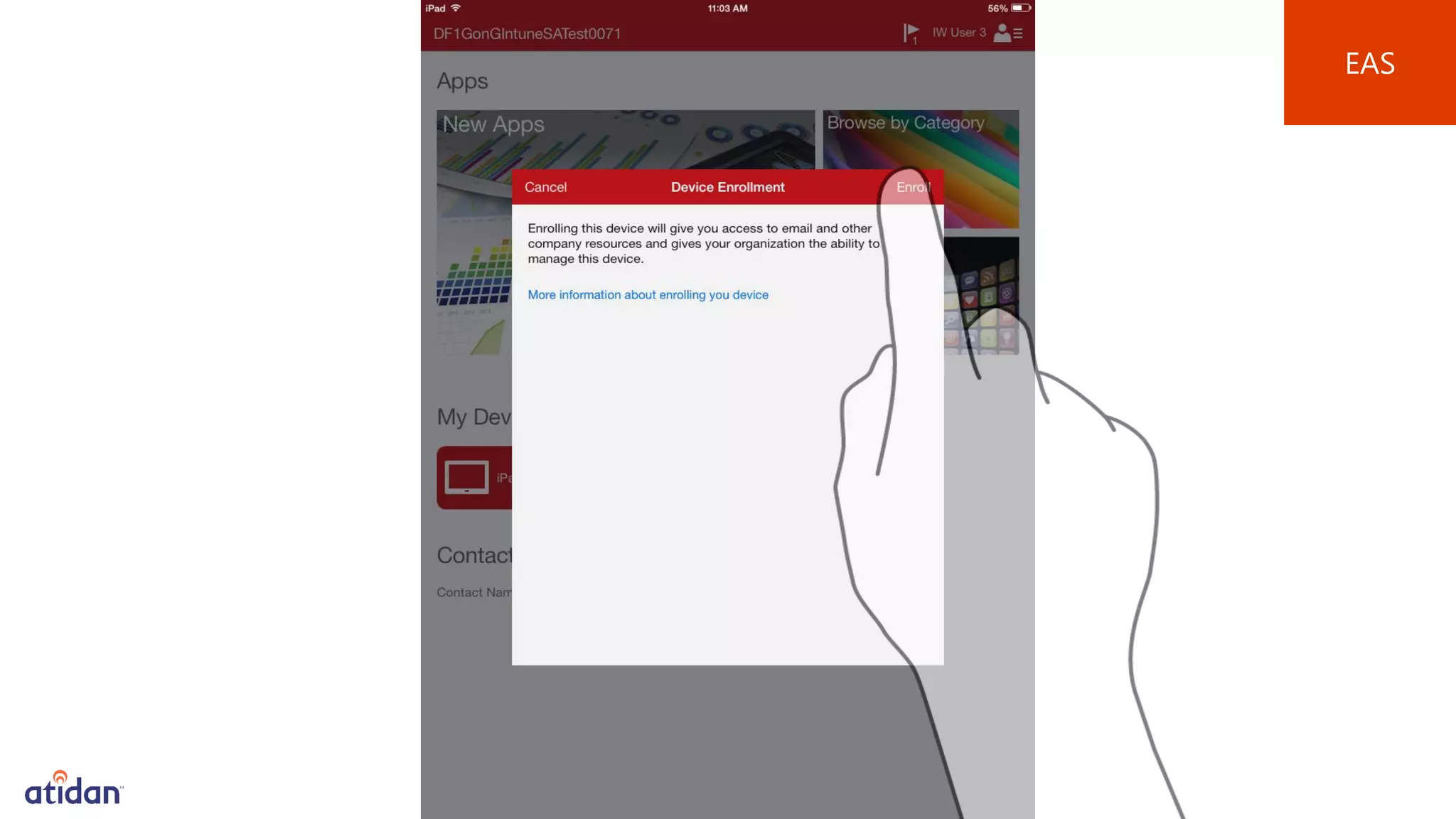
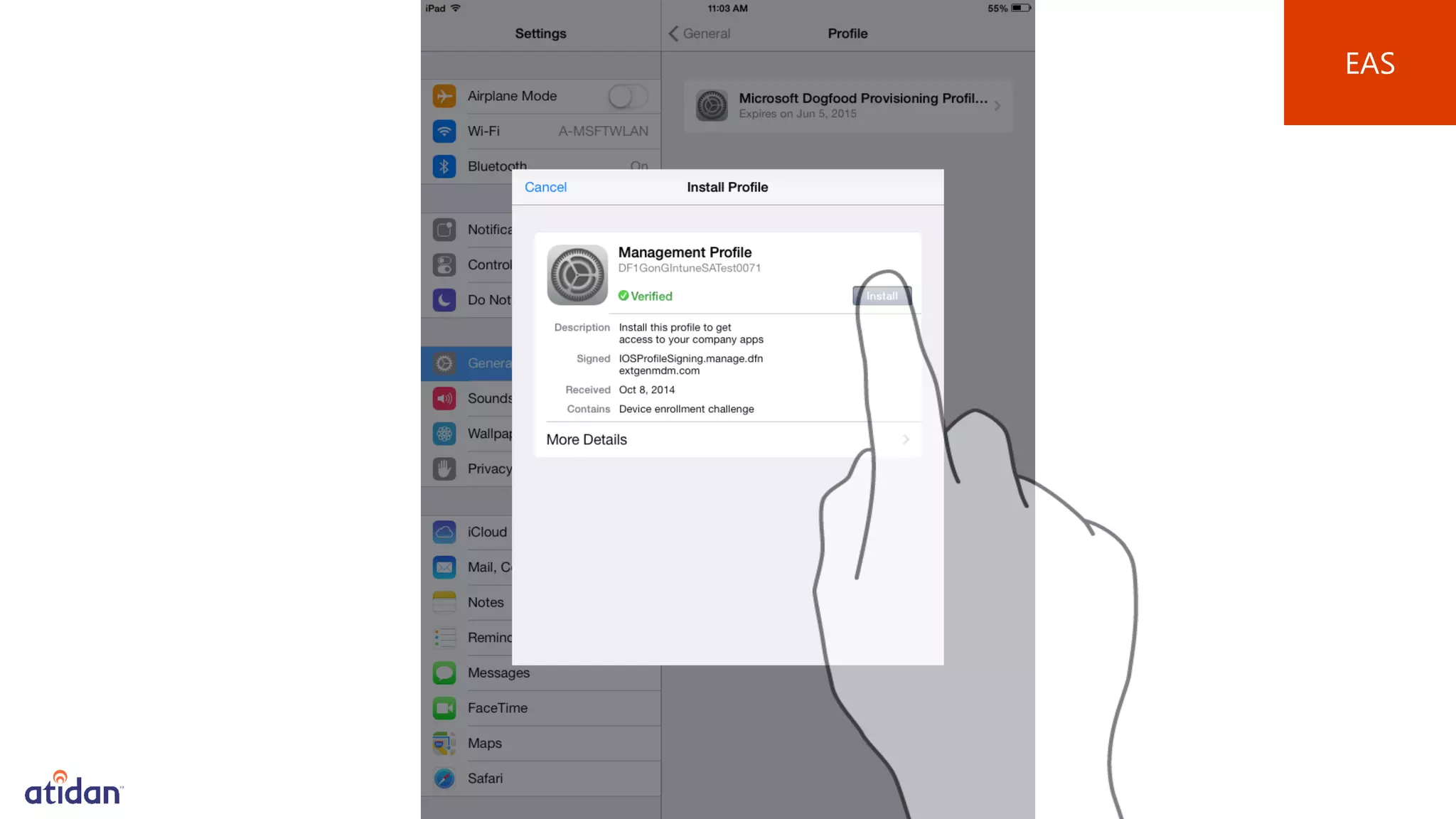
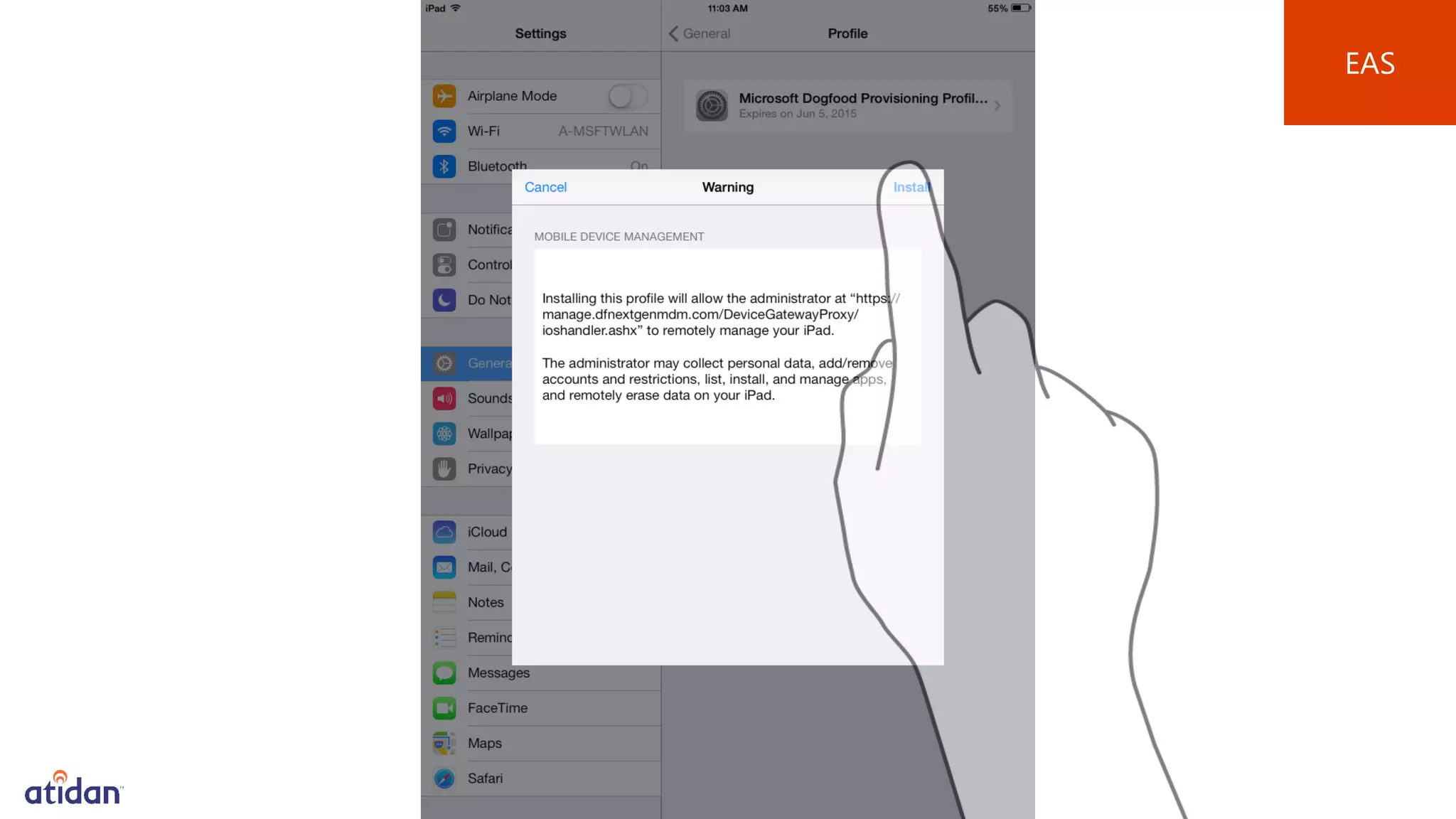
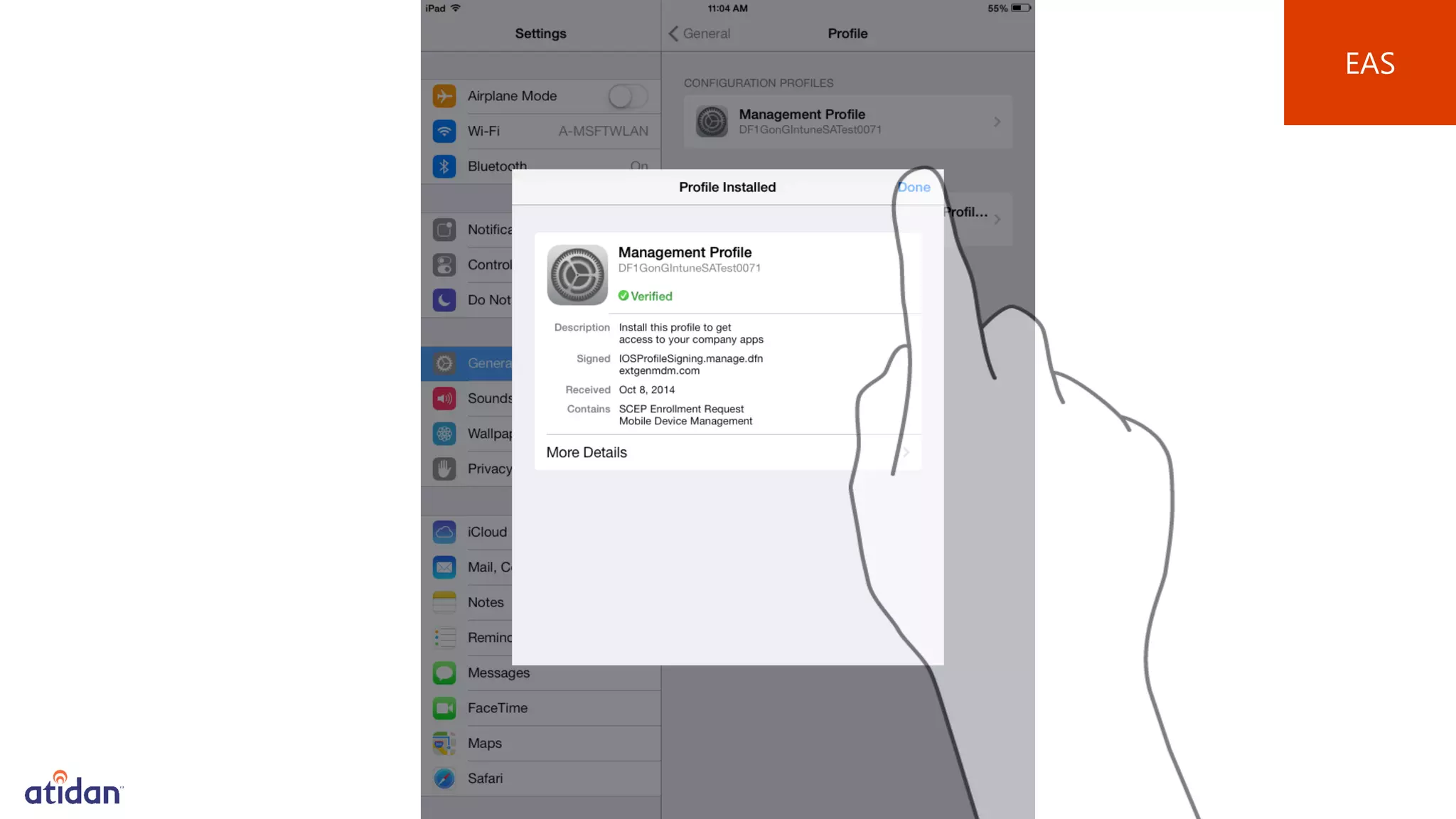
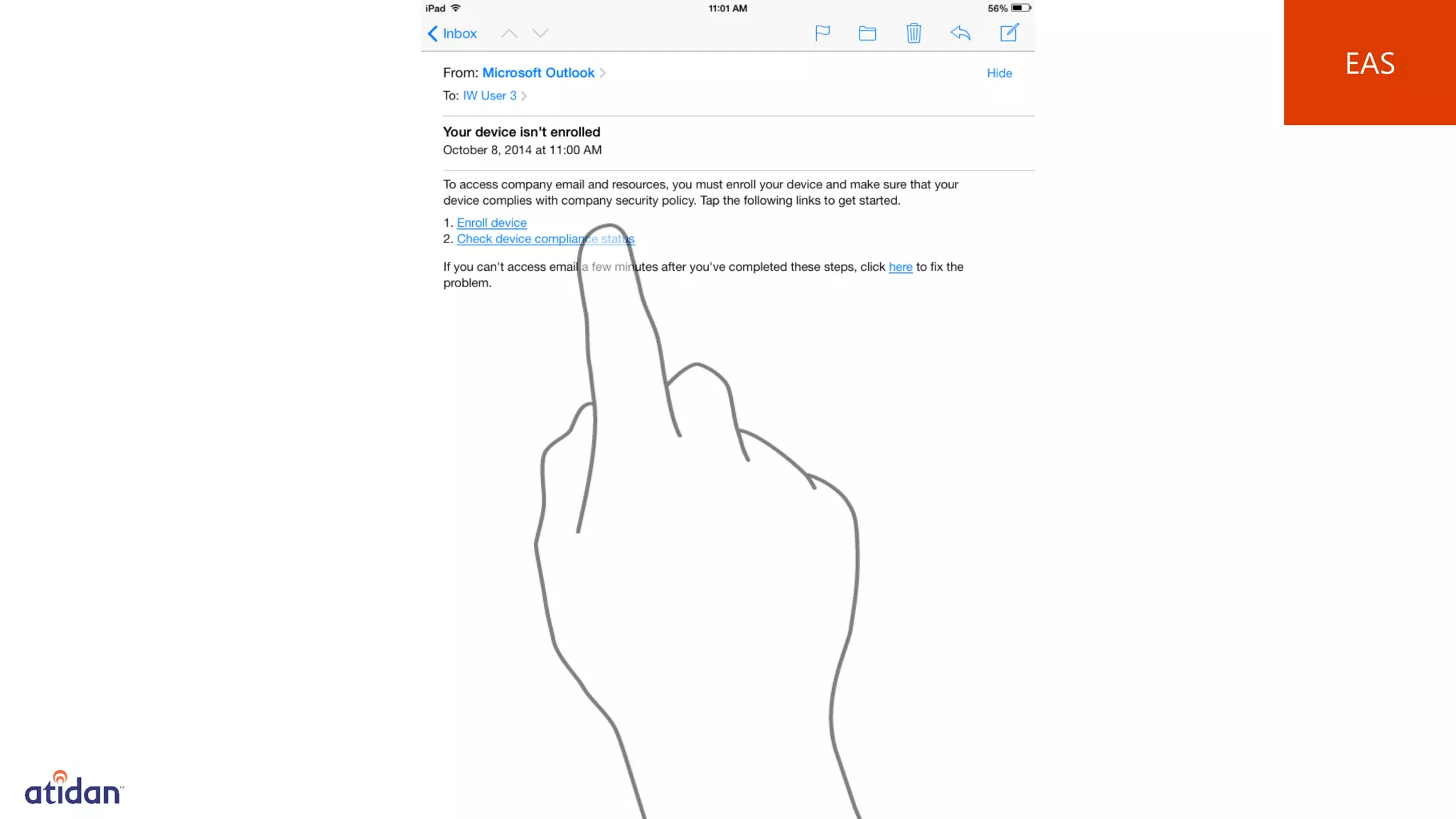
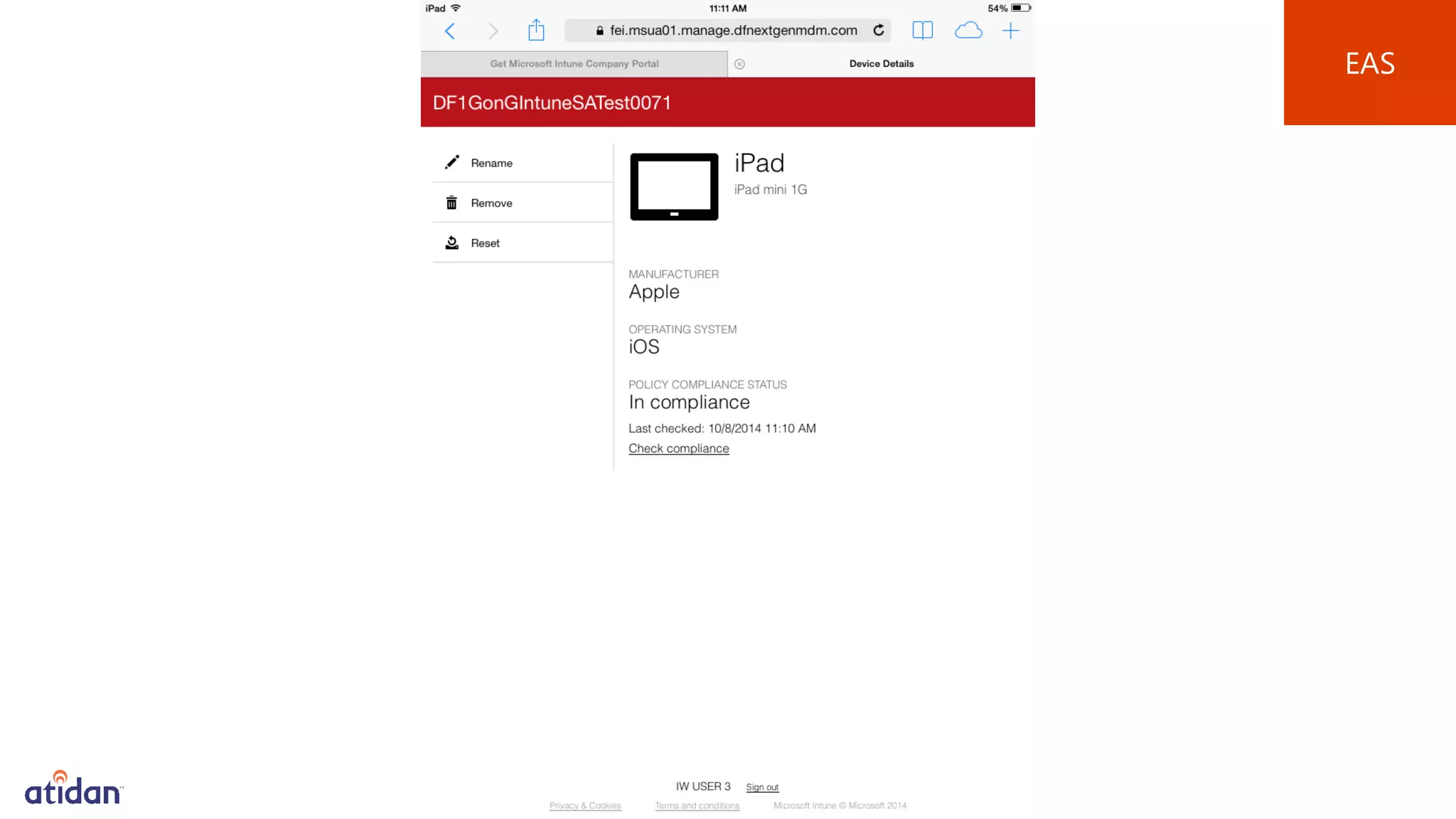
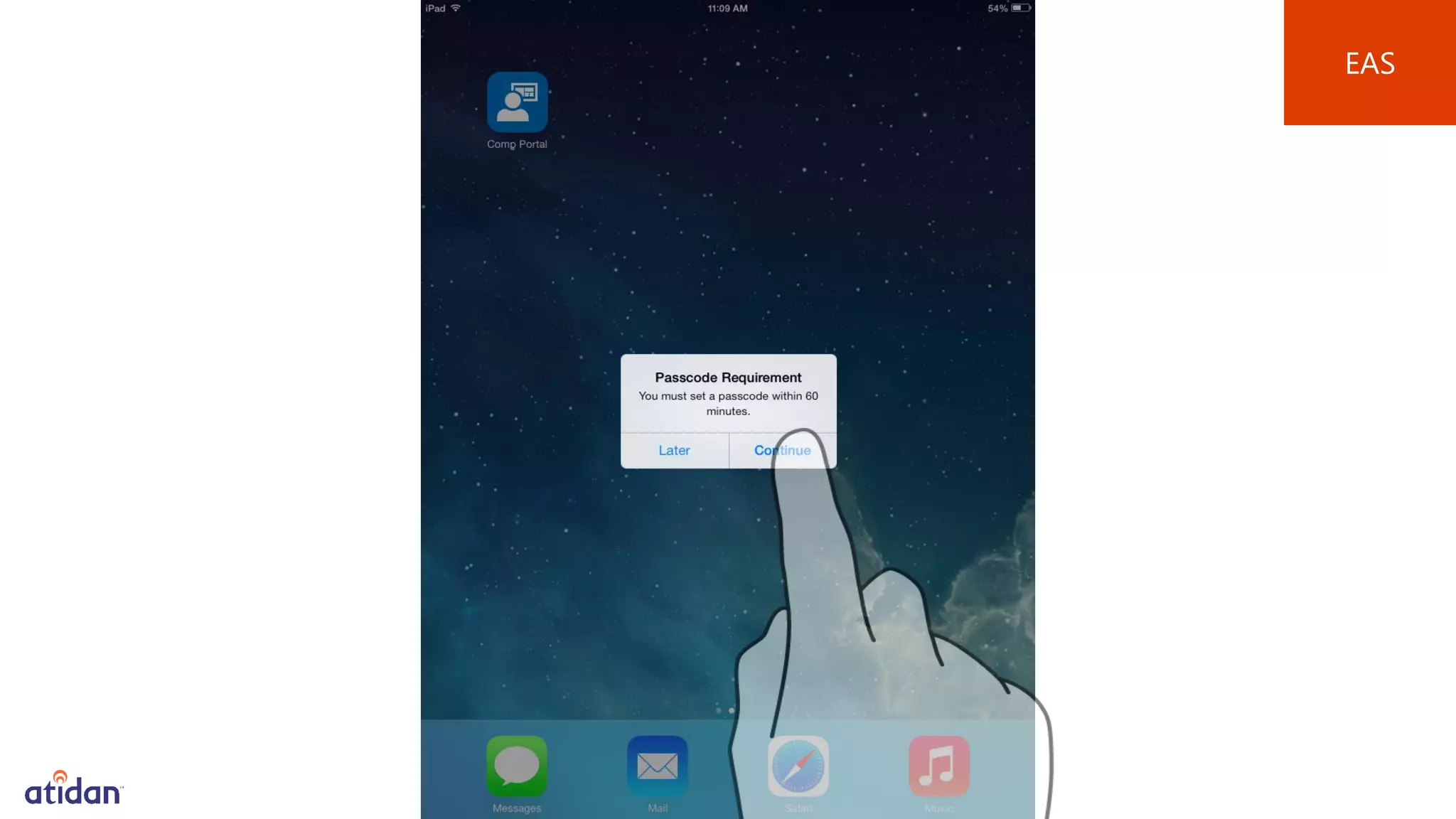
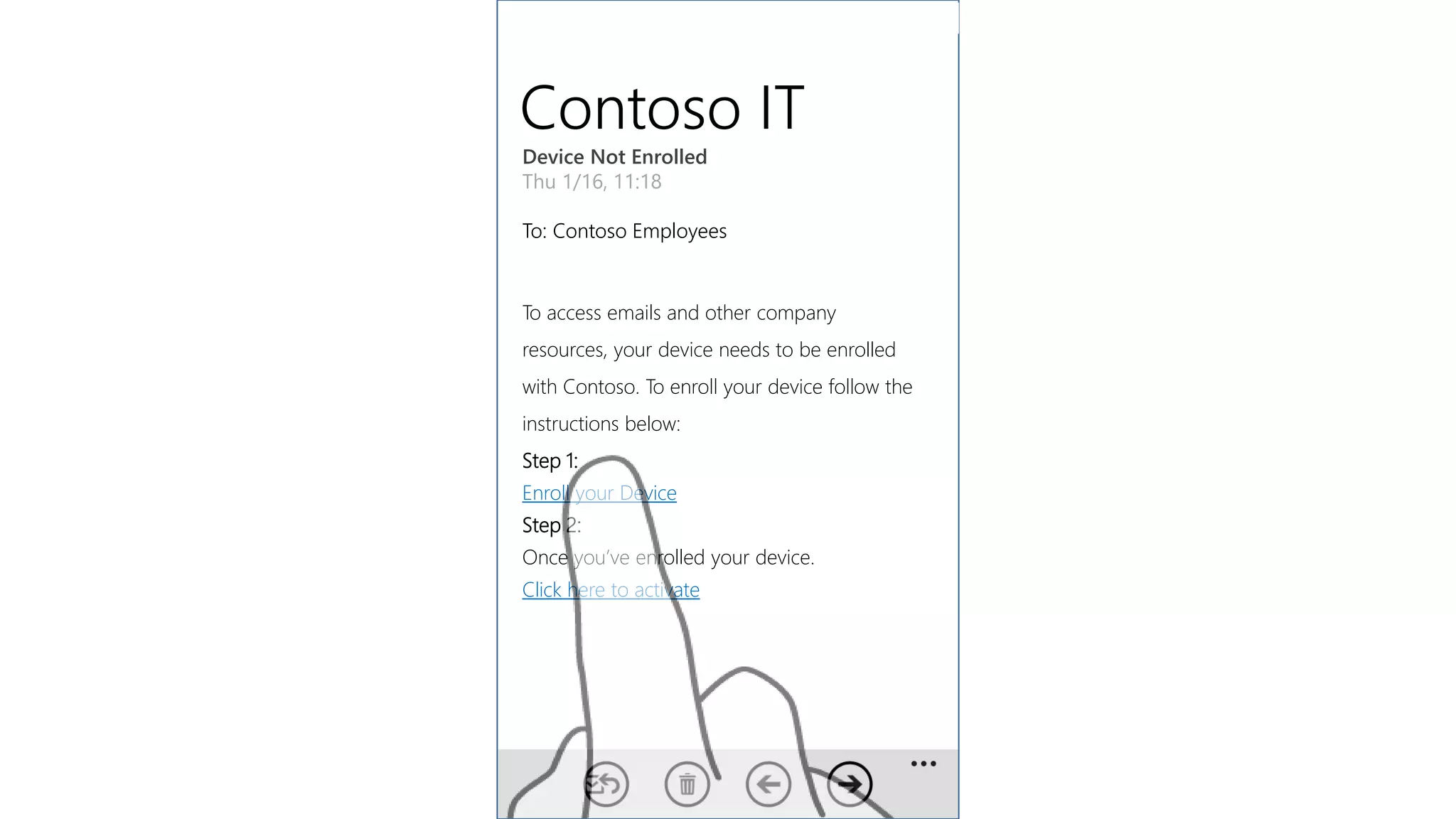
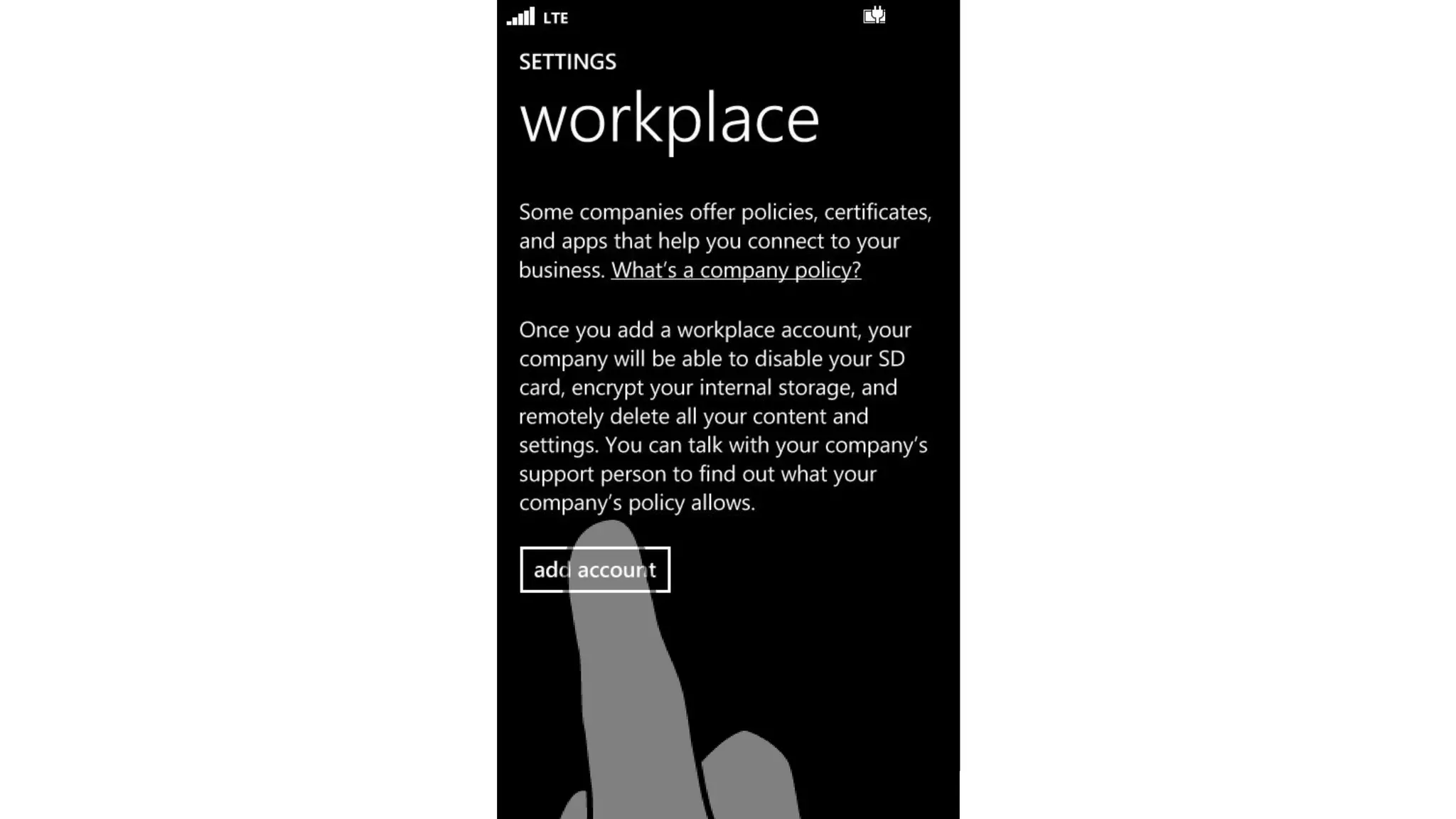
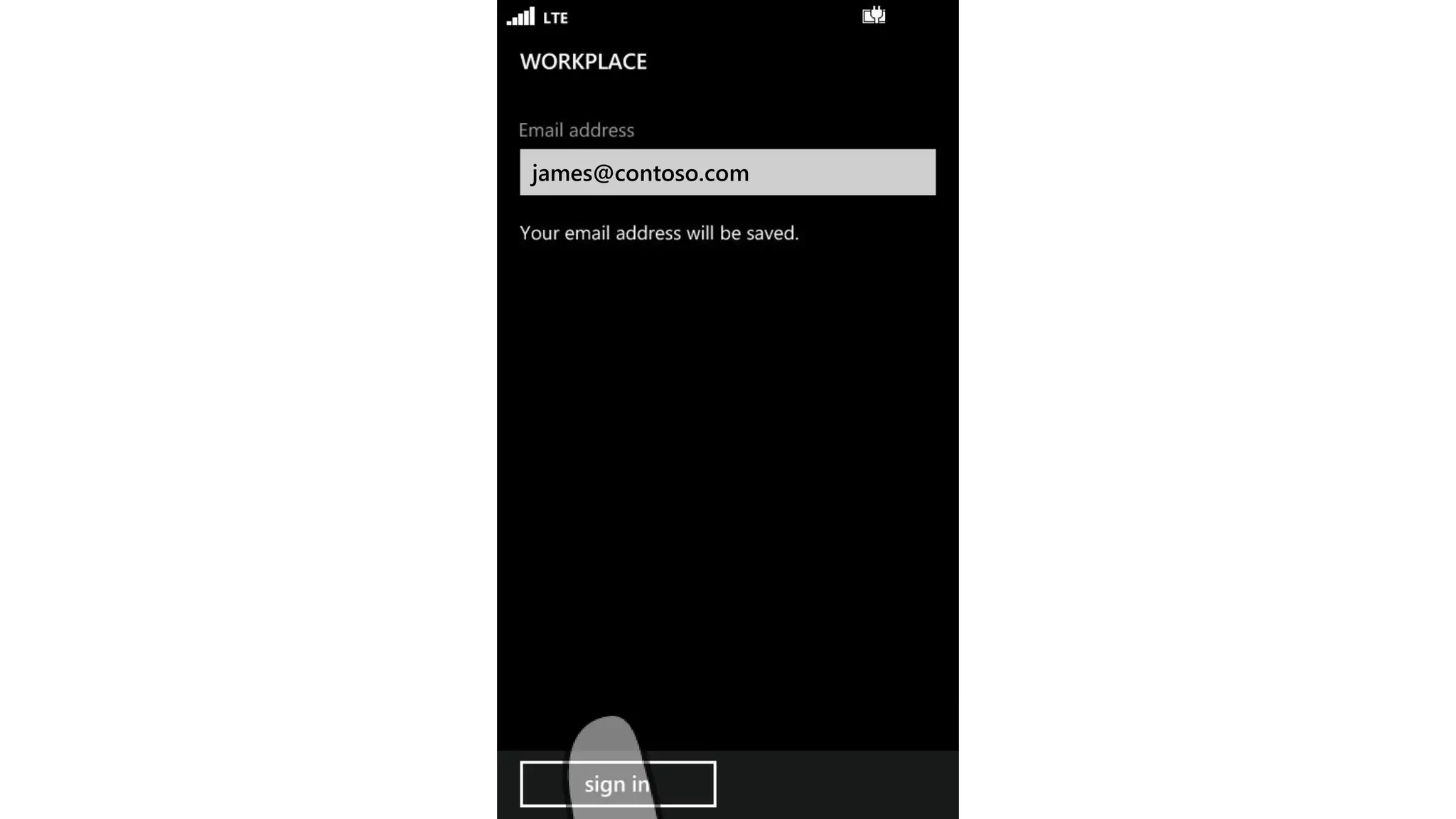
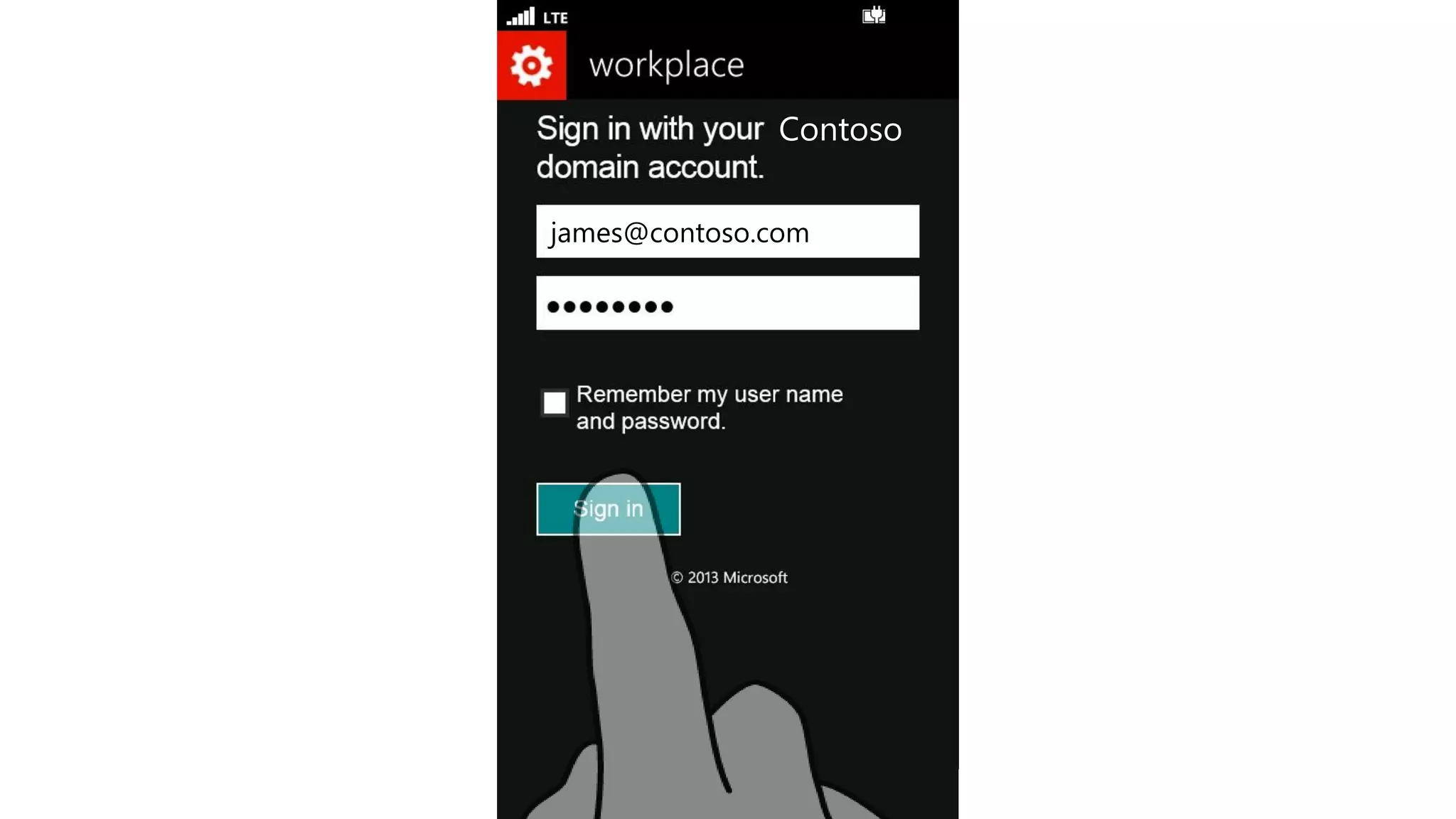
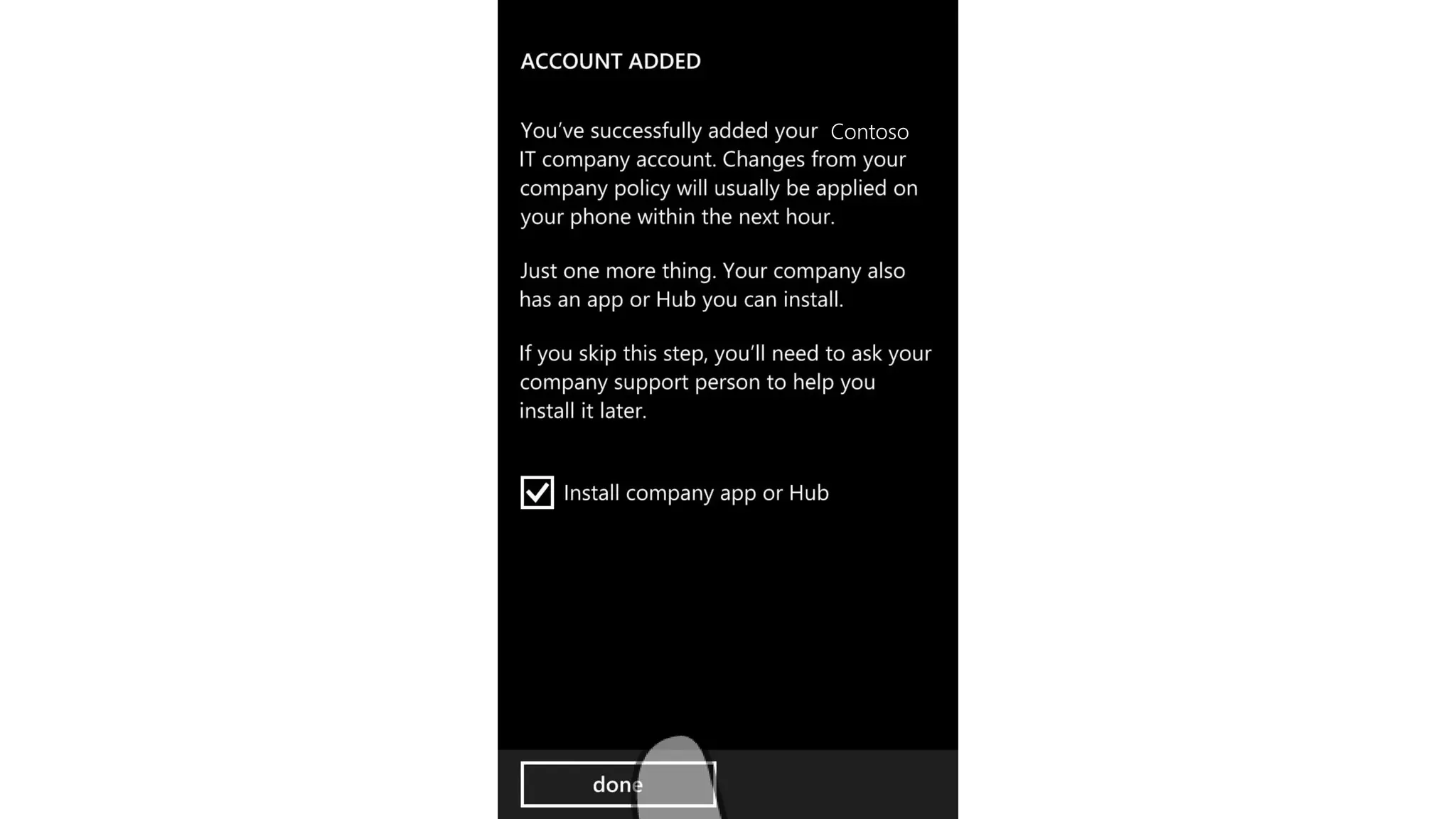
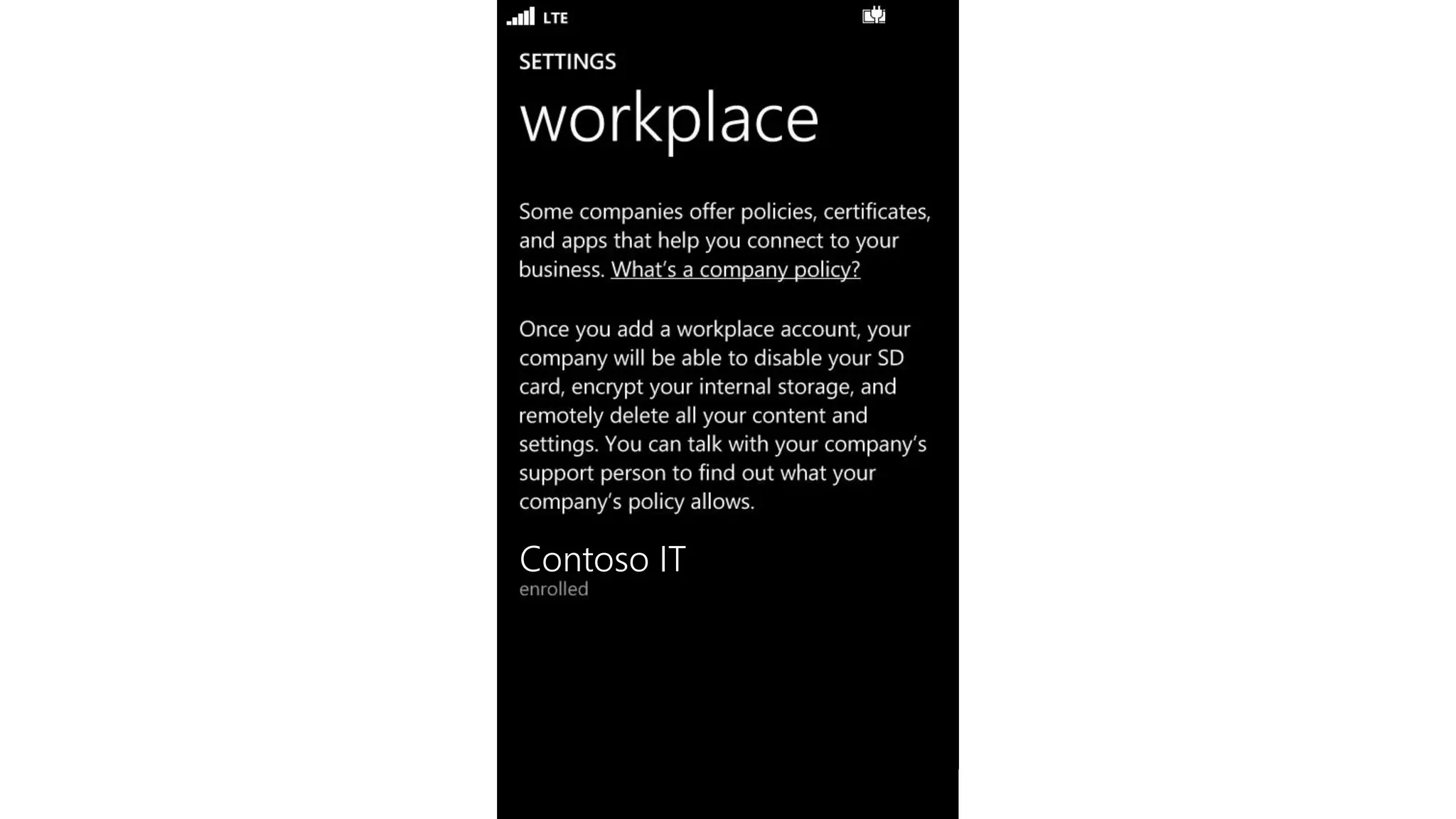
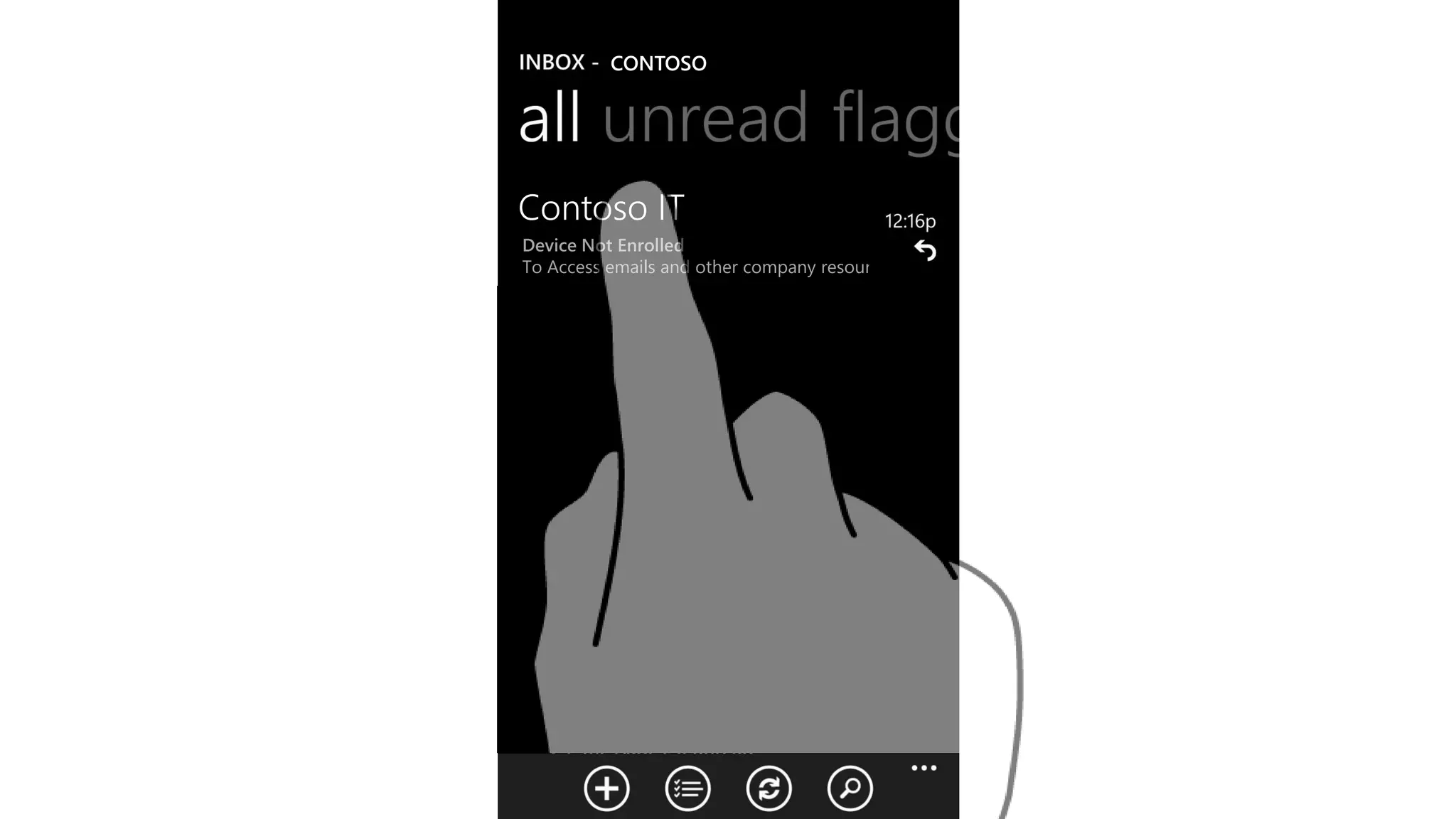
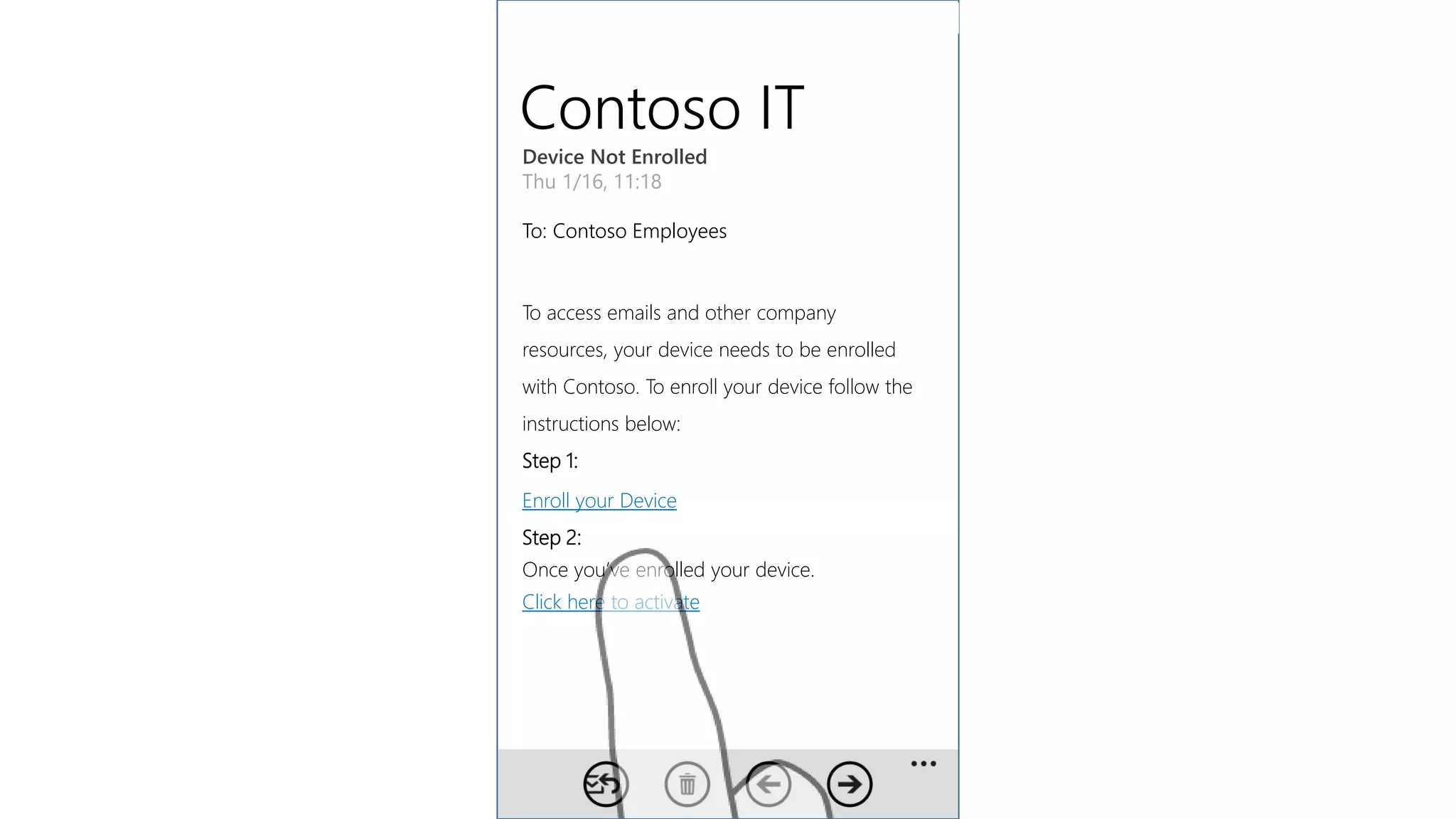
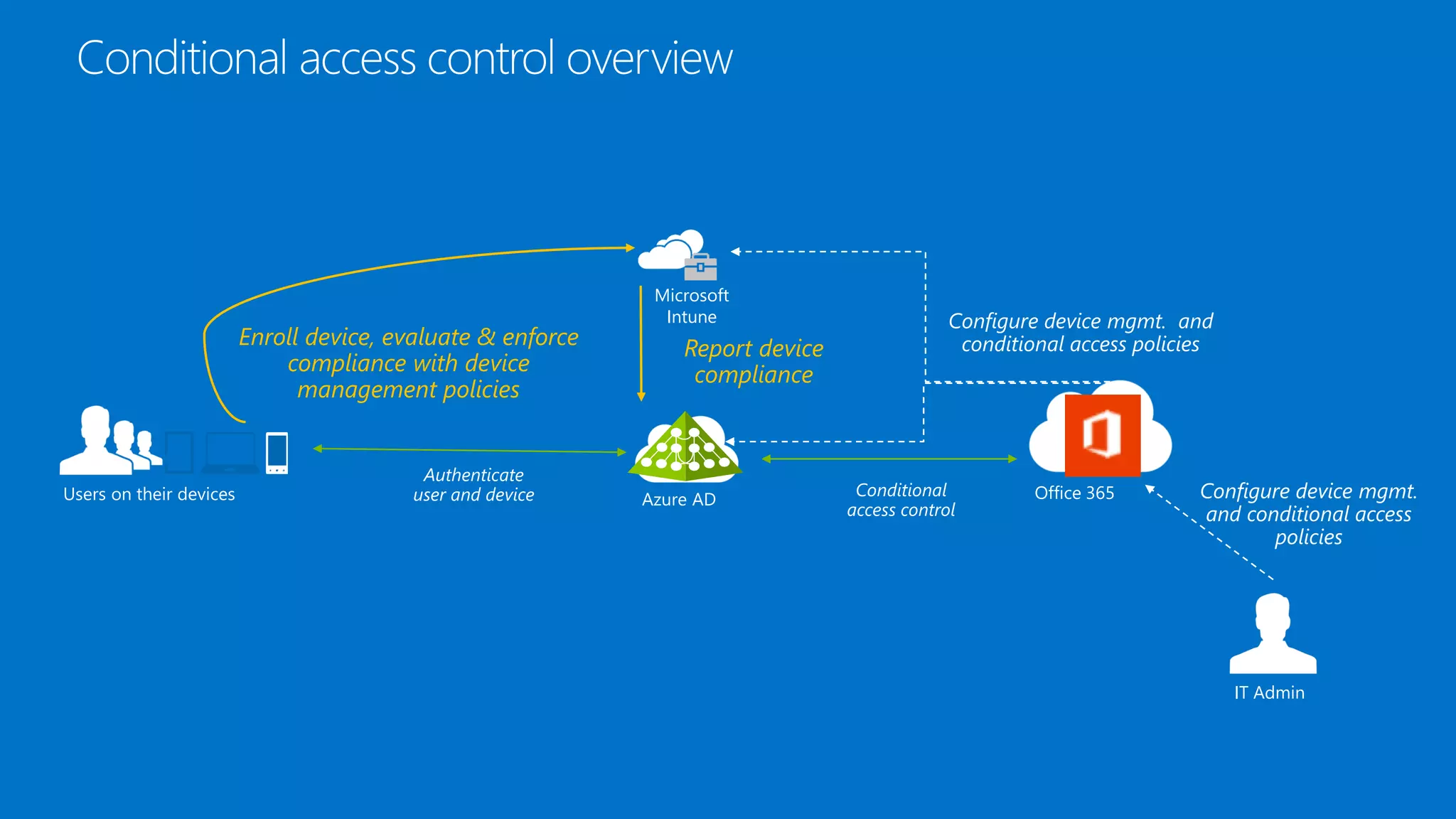
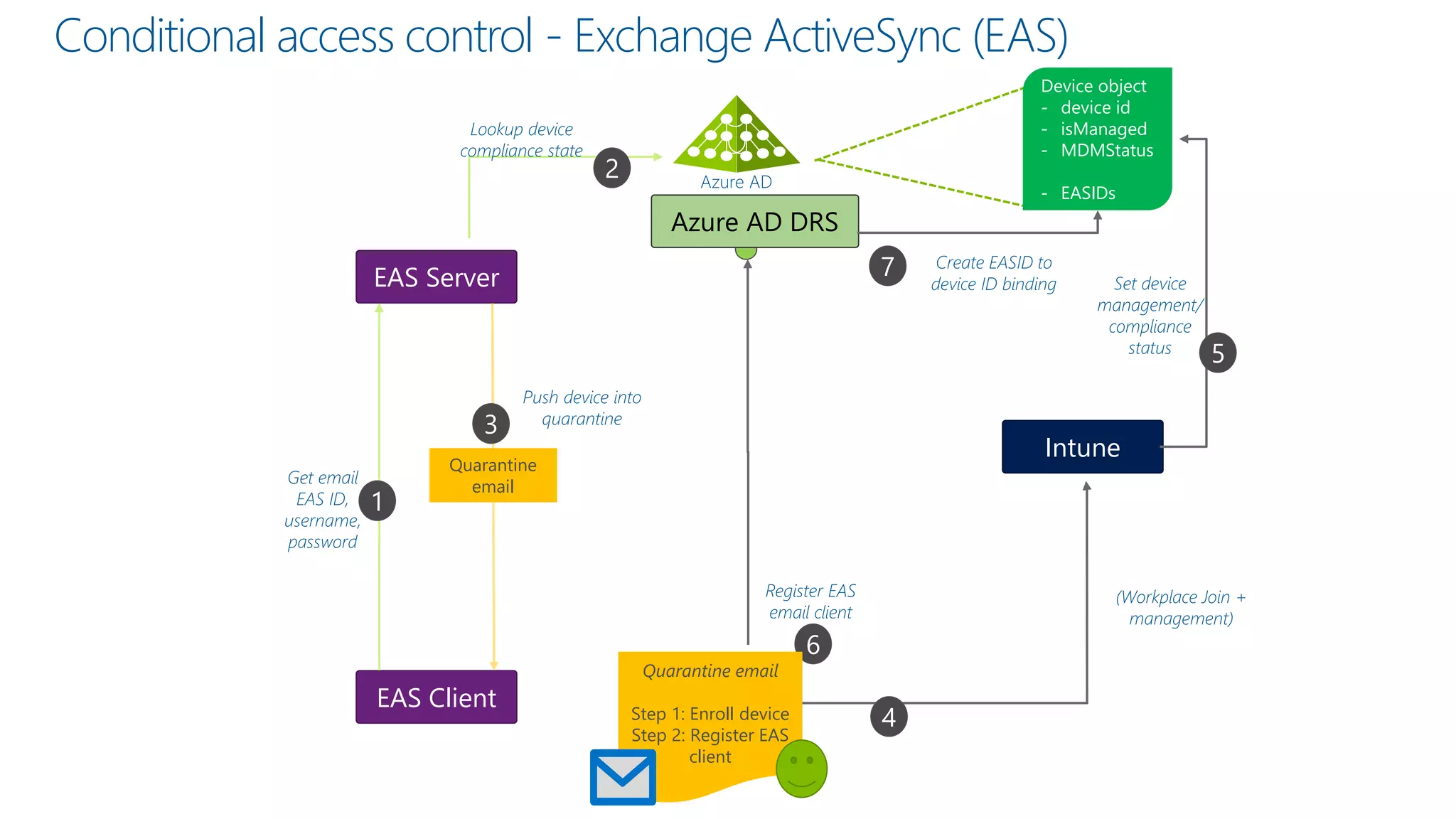
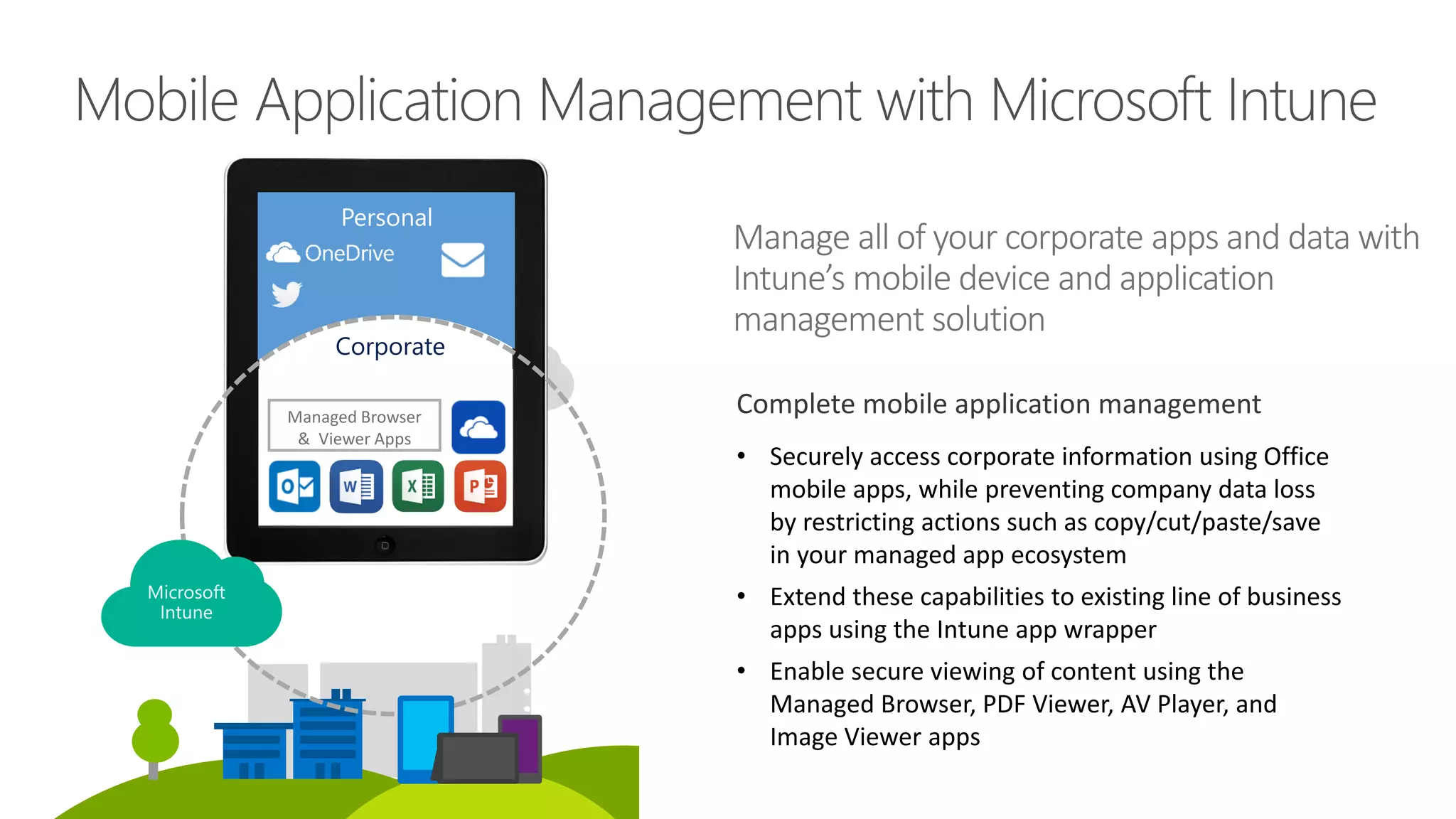
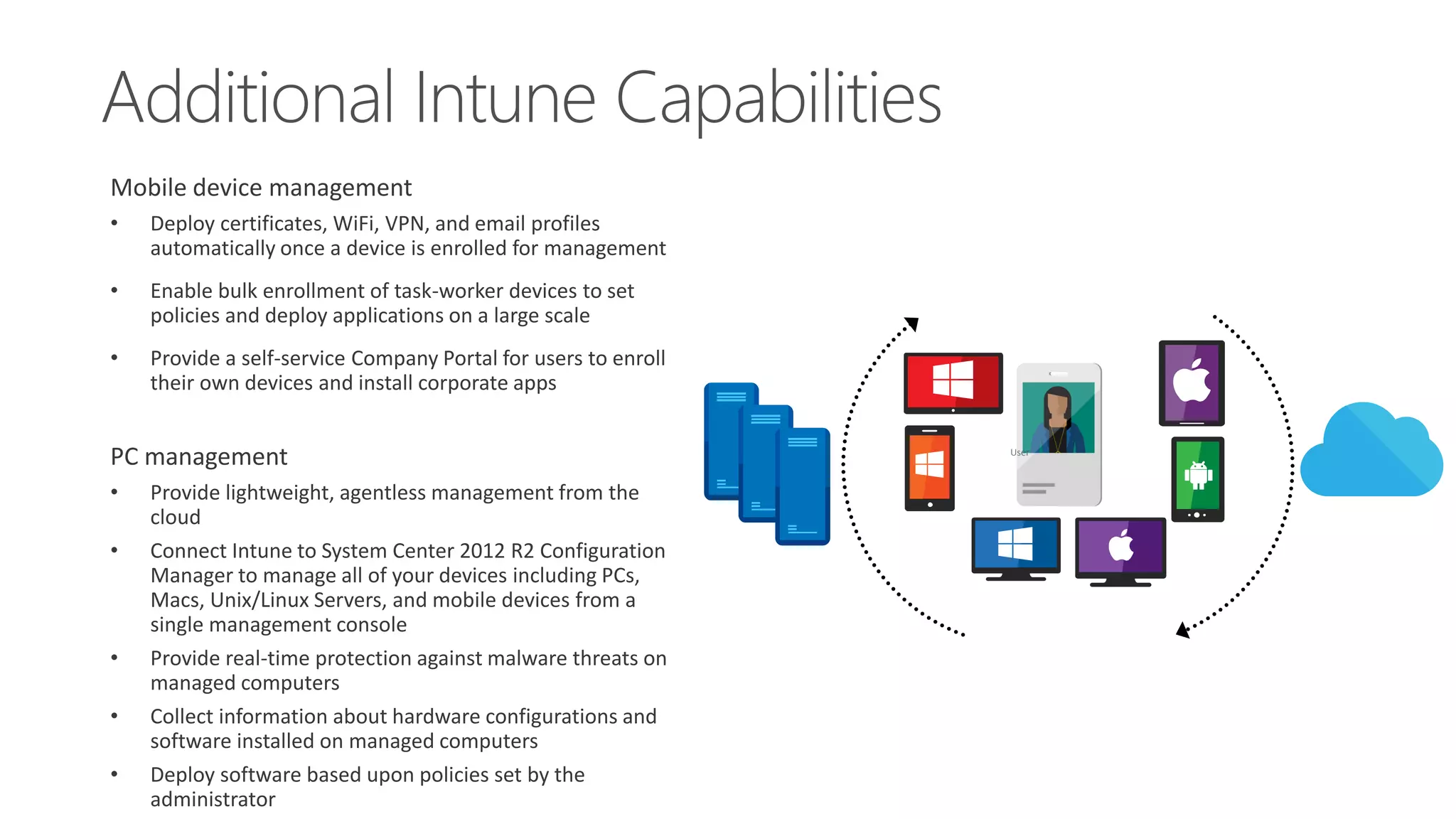
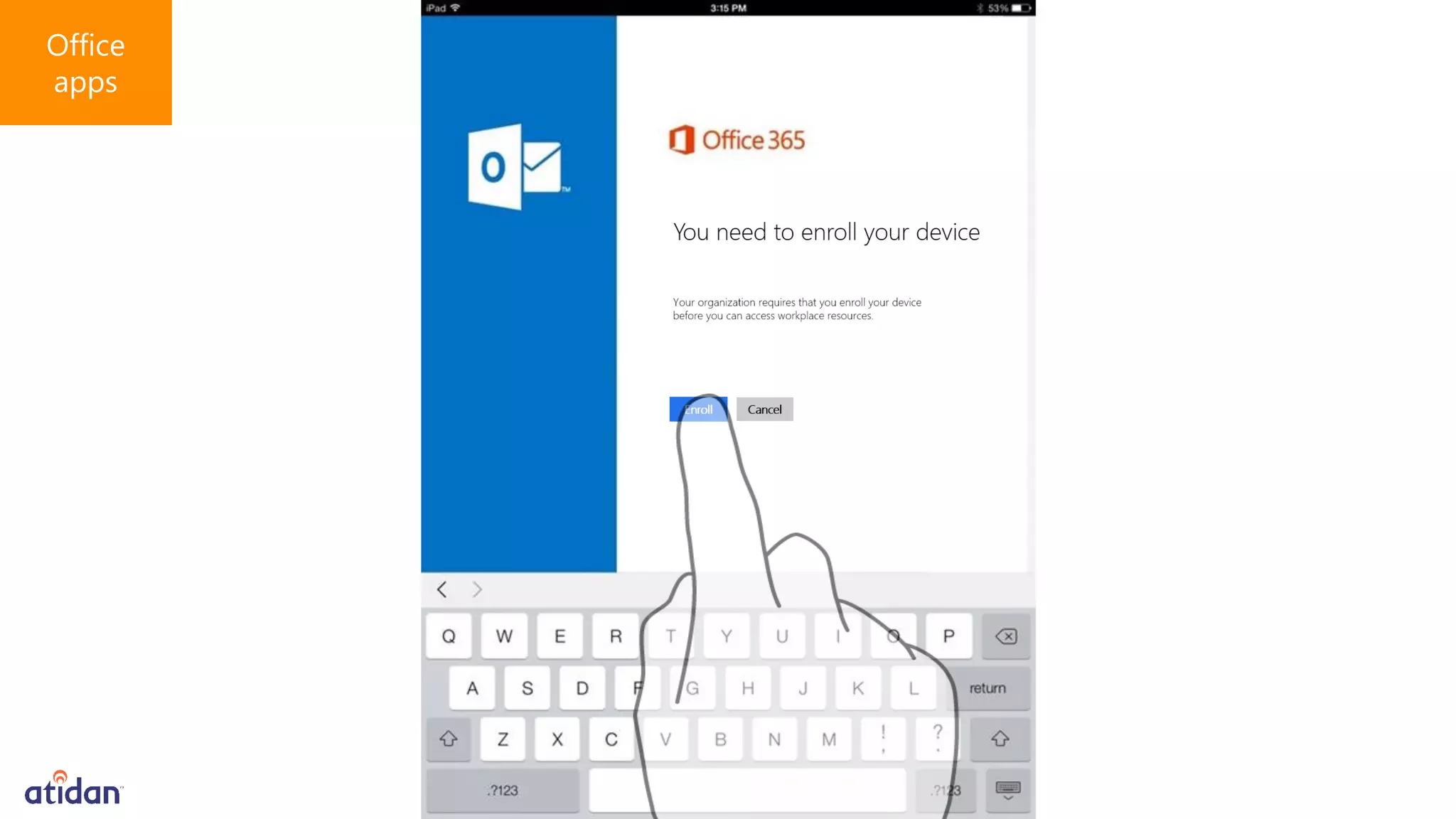
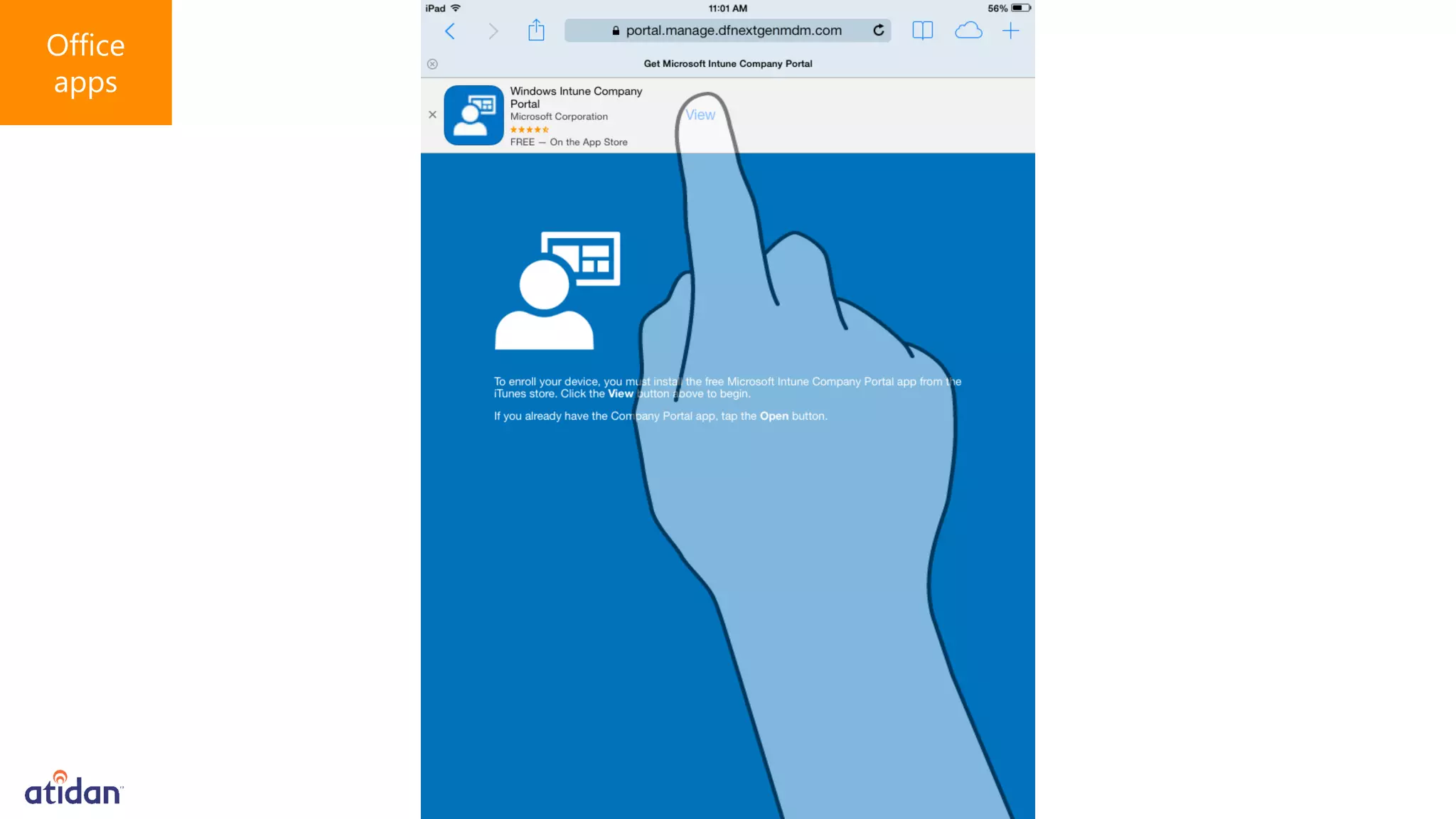
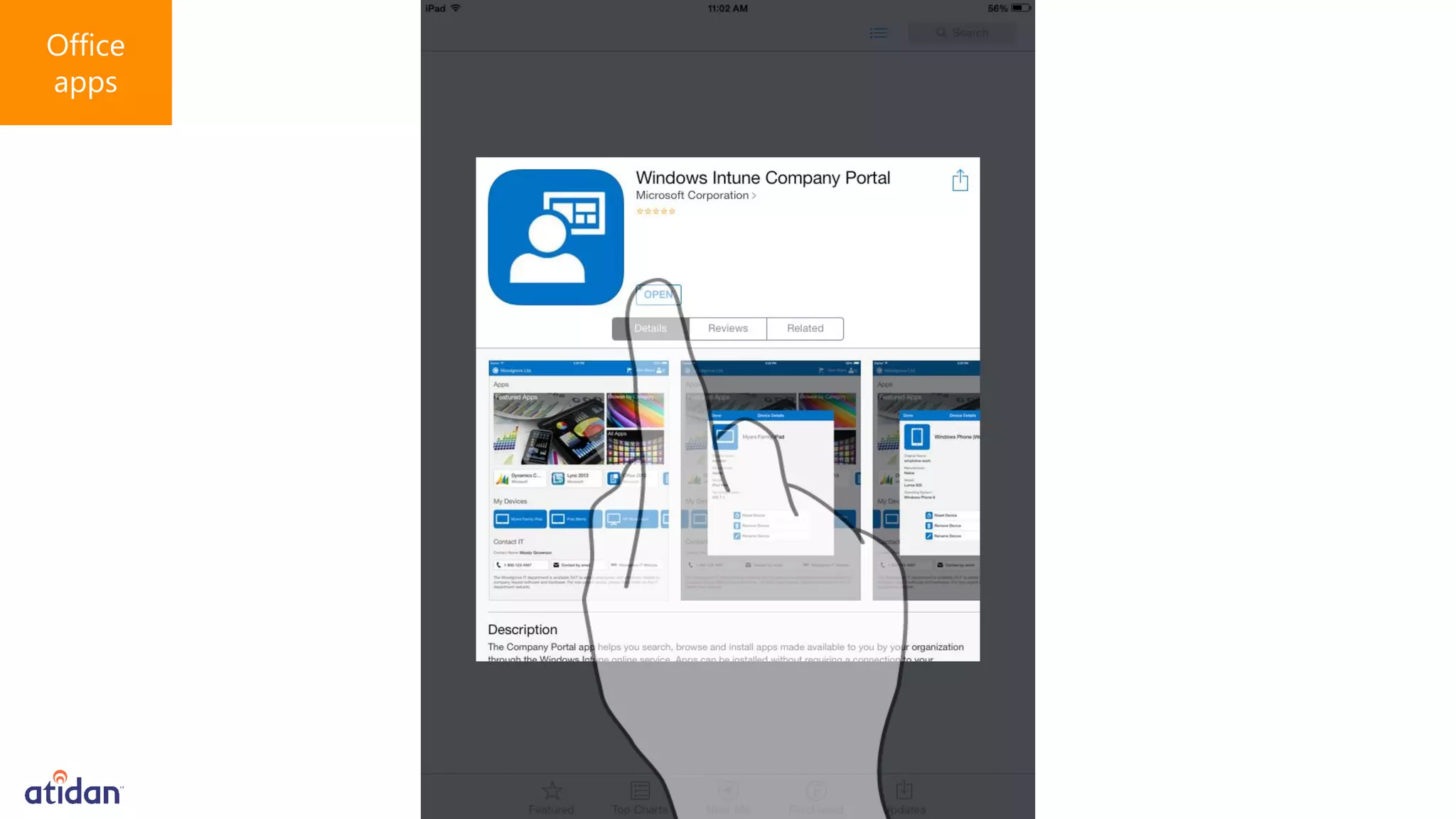
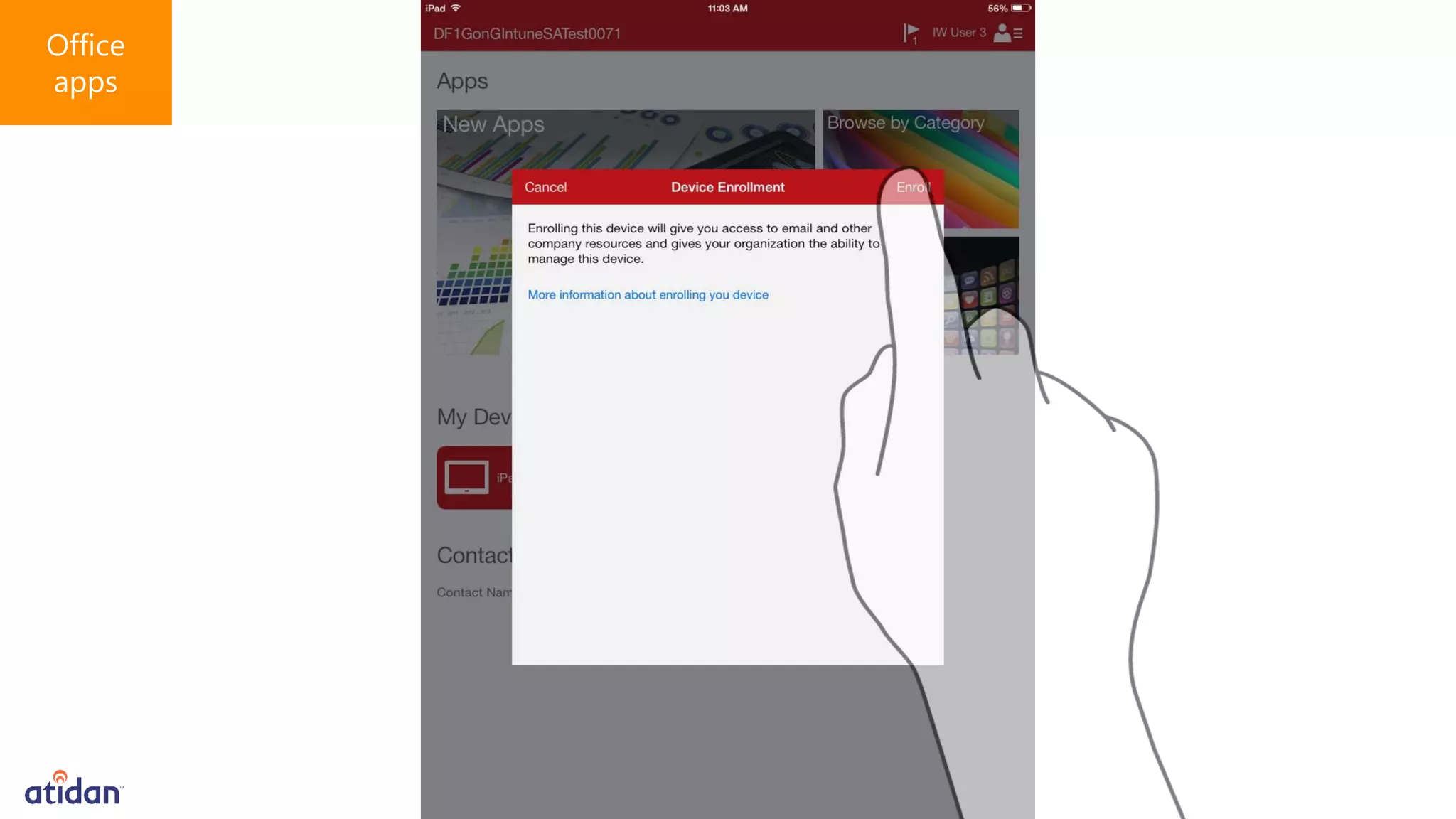
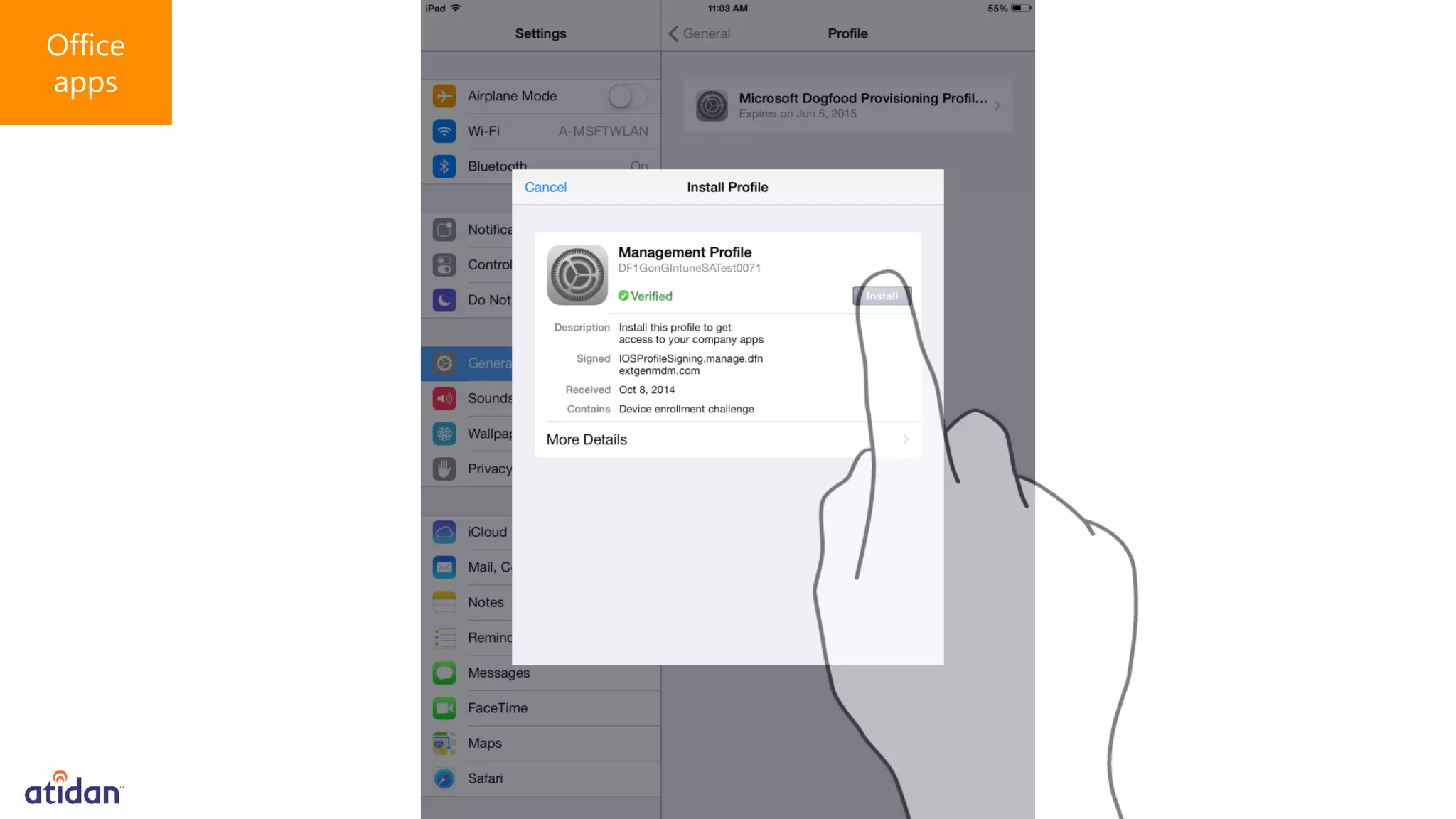
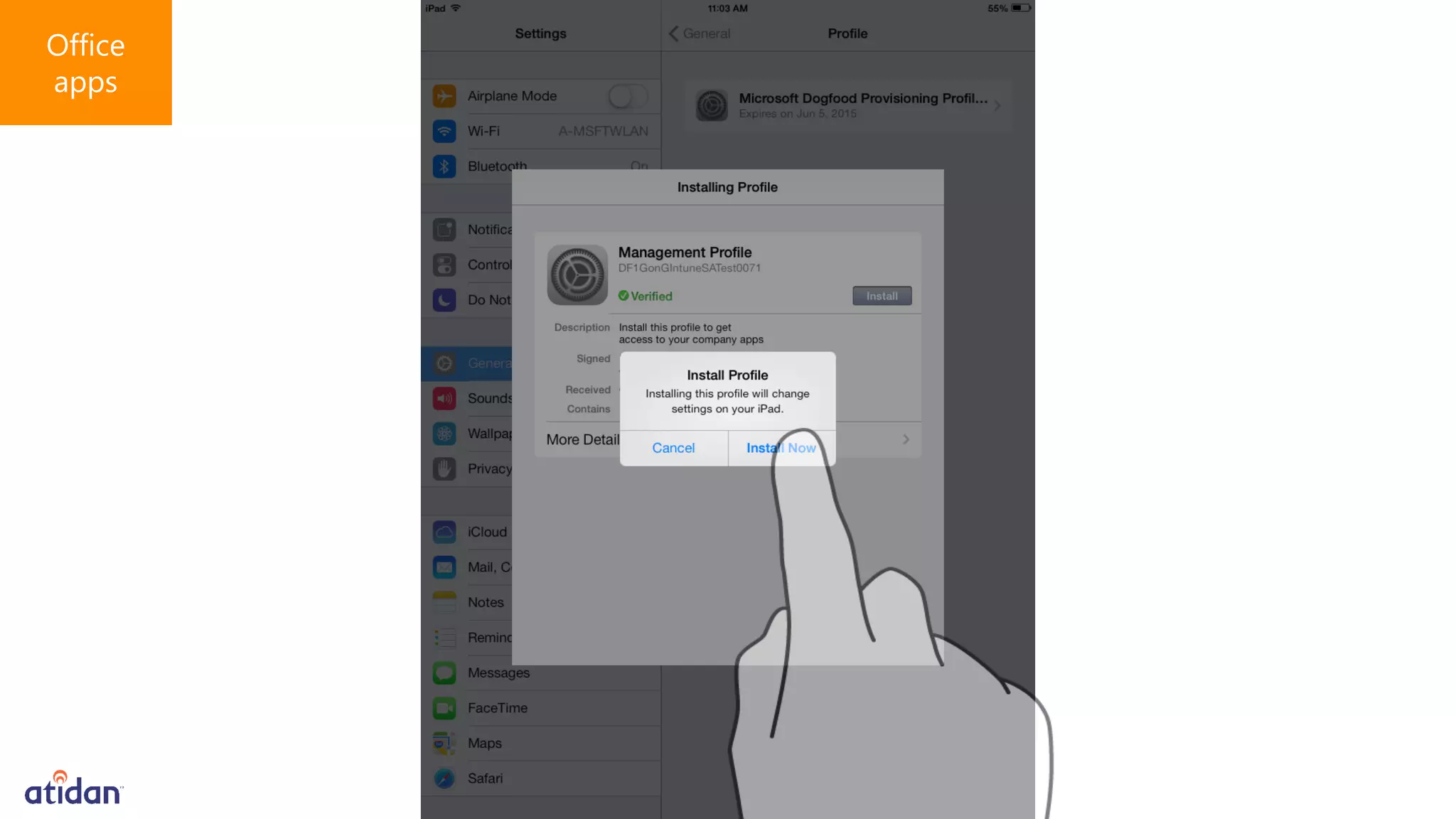
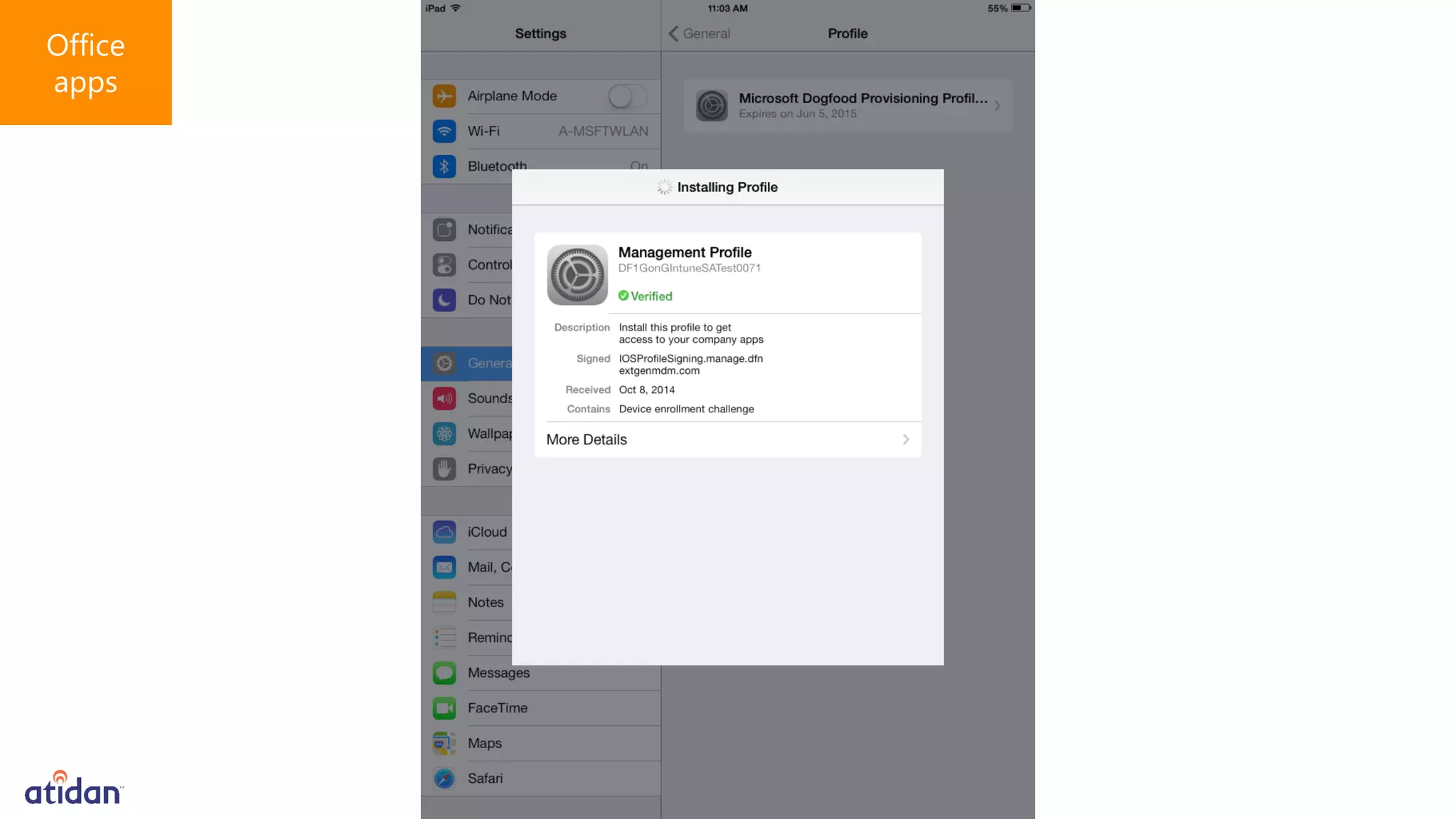
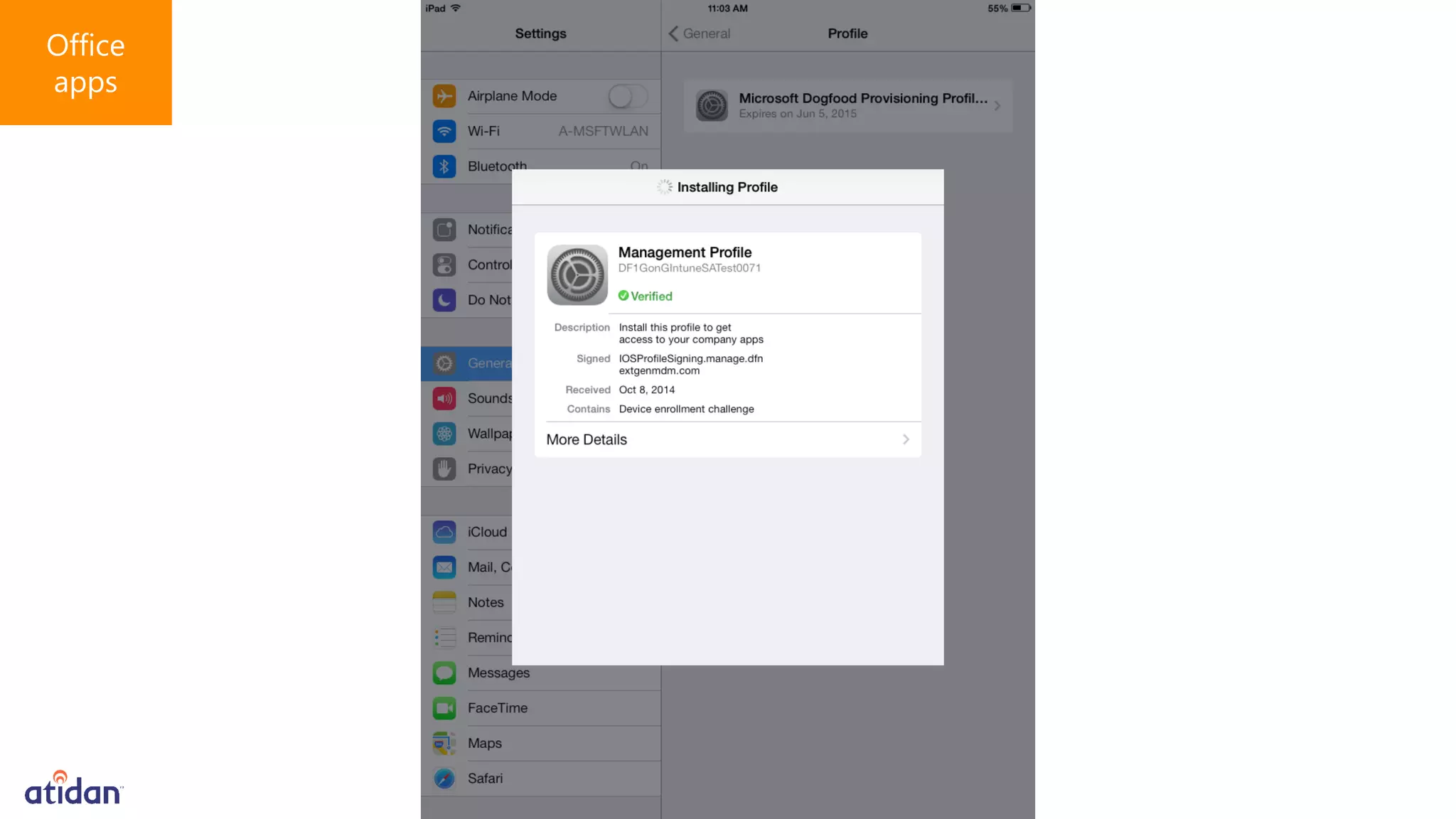
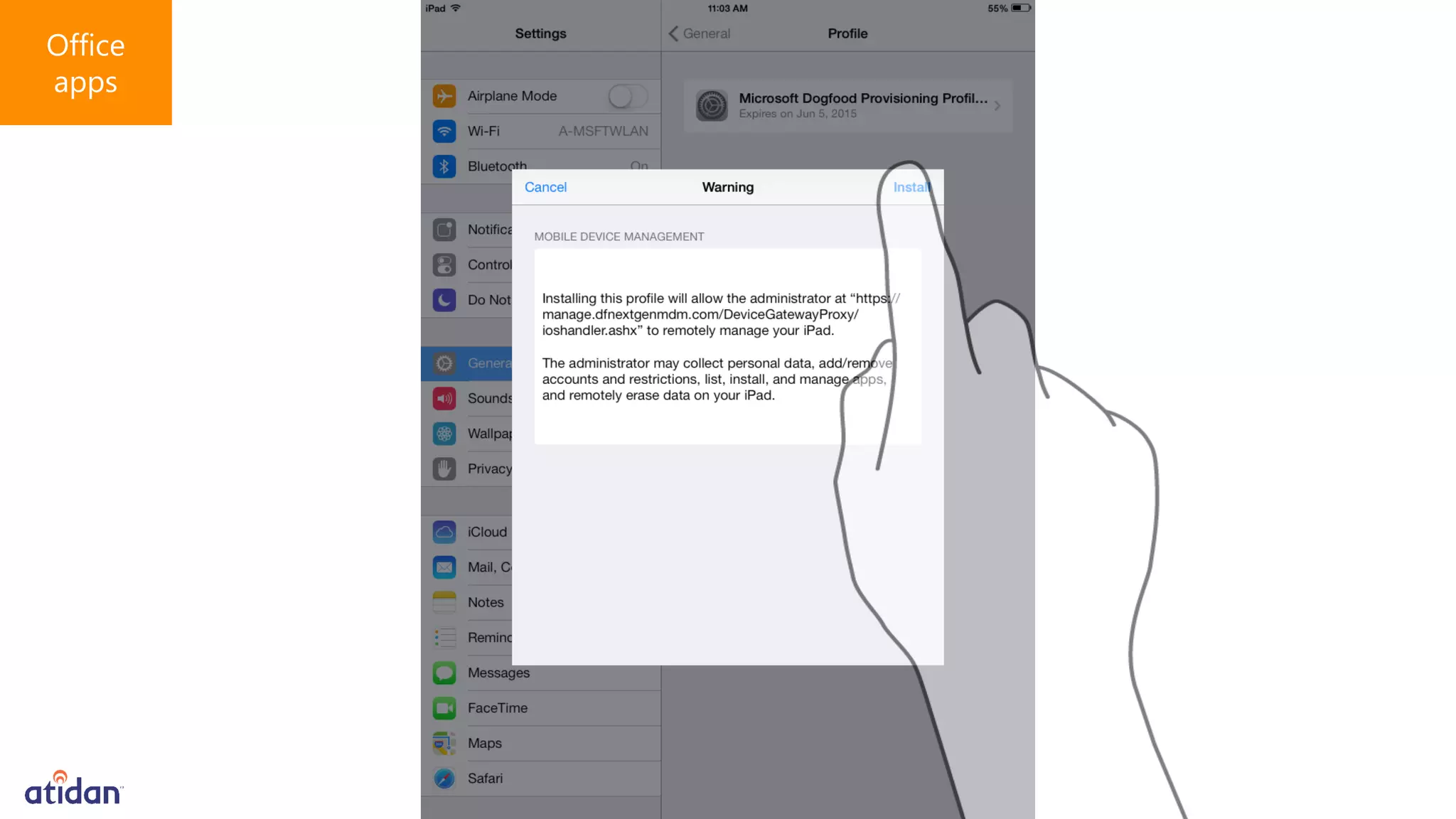
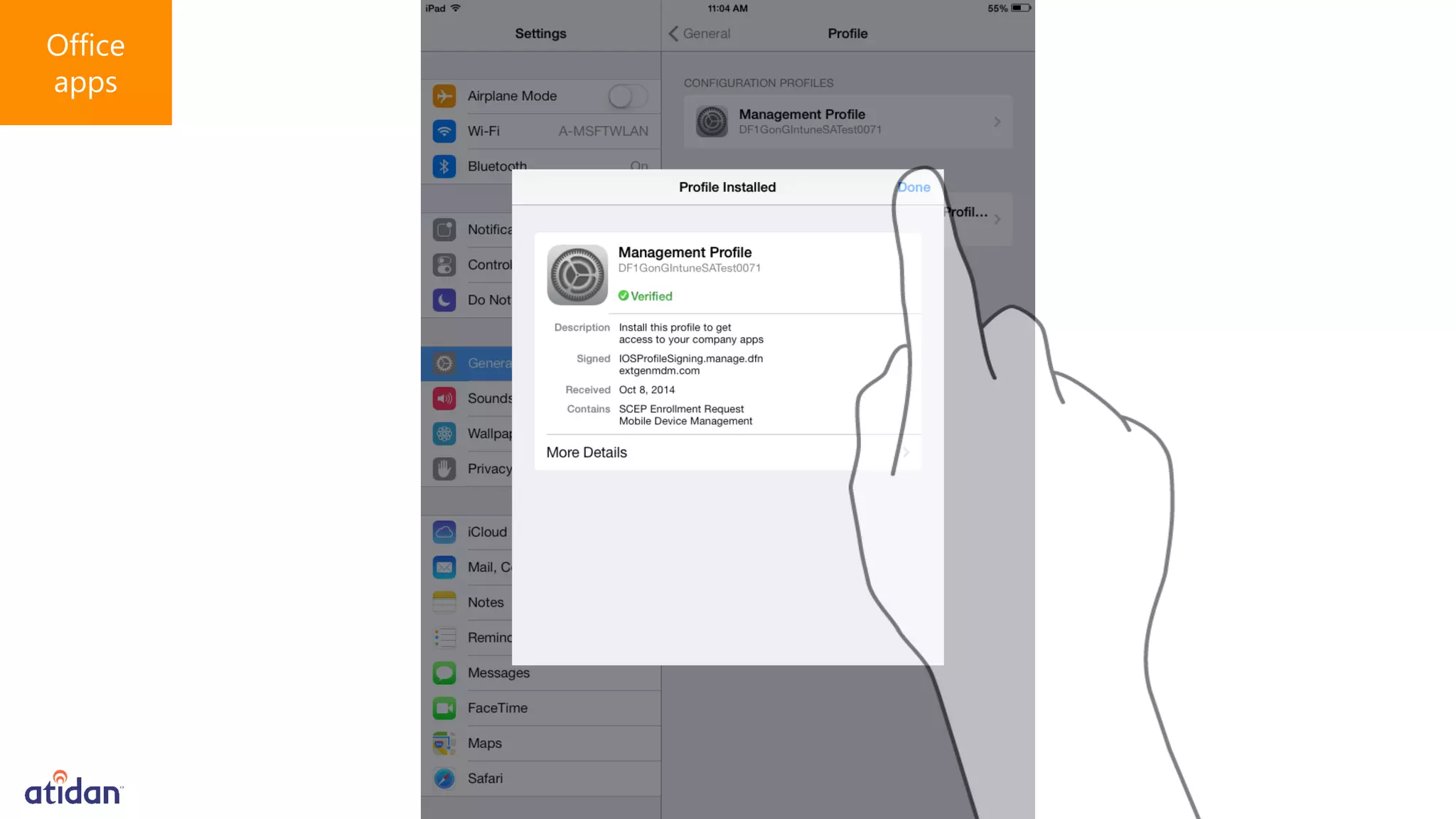
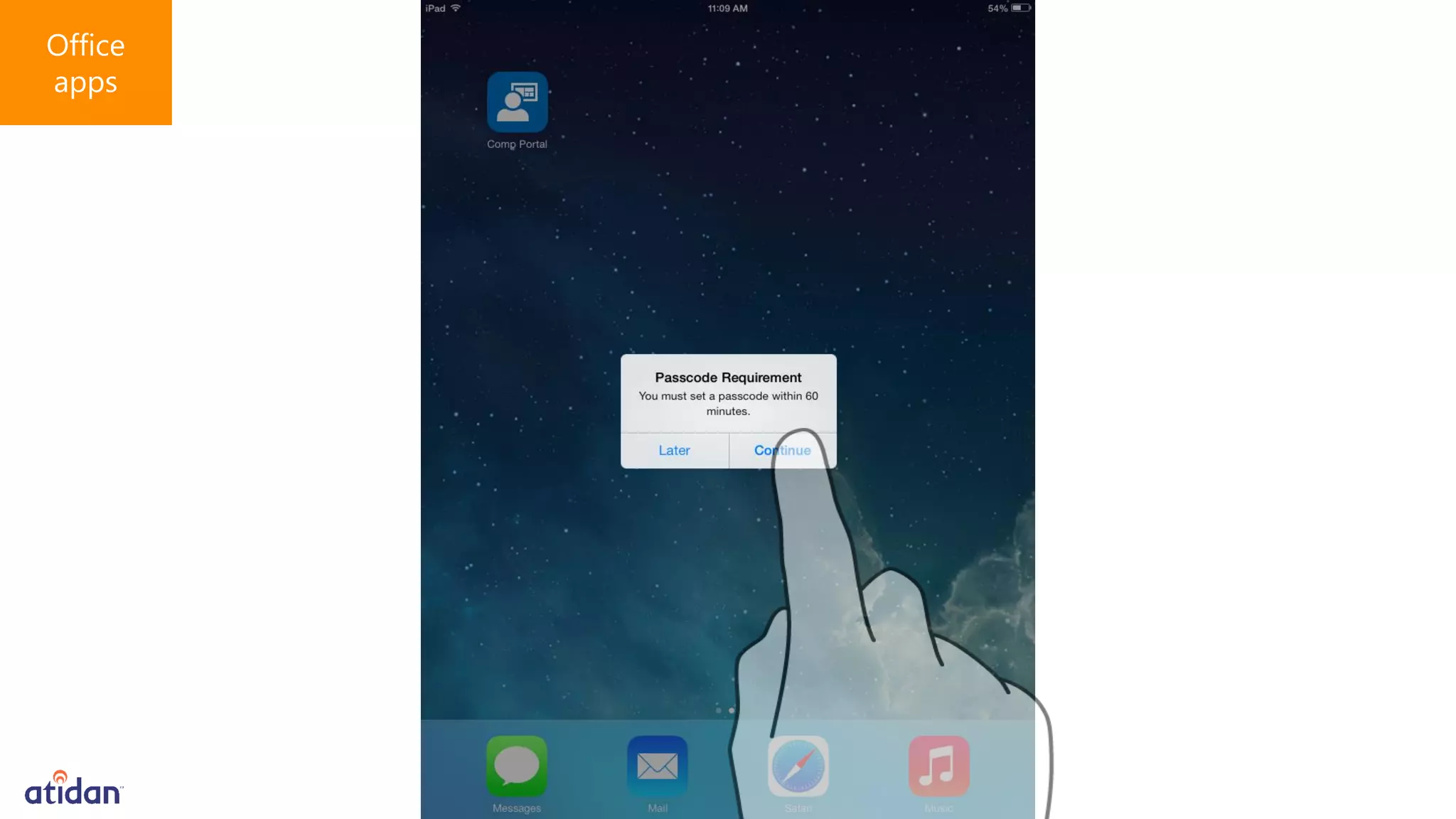
Microsoft Intune provides mobile device management (MDM) capabilities for Office 365. It allows organizations to enroll mobile devices used by employees and set policies to control access to corporate resources. Intune integrates with Azure Active Directory and Office 365 to enable features like conditional access control, selective wiping of Office 365 data from devices while leaving personal data intact, and reporting on device compliance. It also provides broader mobile application management and mobile PC management capabilities through integration with System Center Configuration Manager.