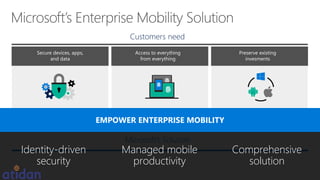
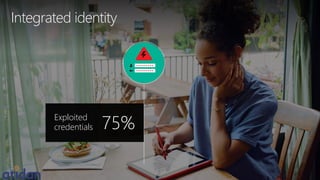
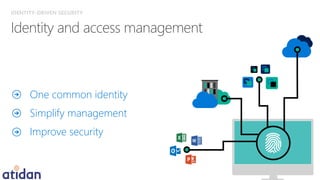
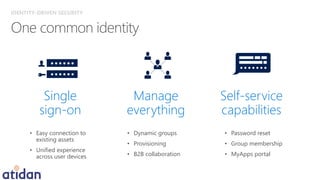
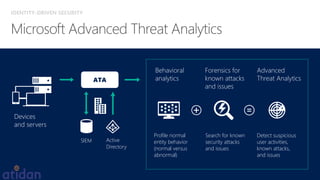
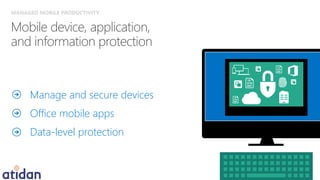
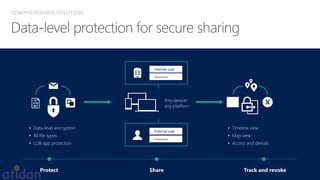
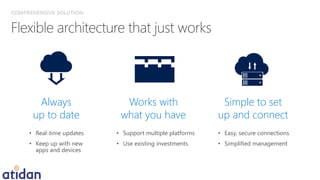
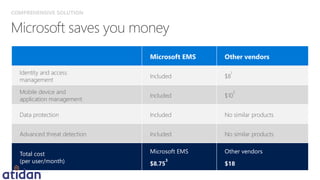
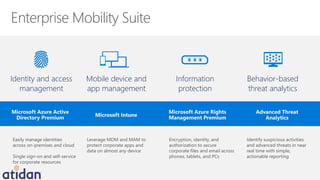
The document discusses the need for enhanced mobile security governance and the importance of identity-driven security in managing enterprise mobility. It highlights the prevalence of credential exploitation in network intrusions and the inadequacy of mobile security measures in large organizations. Microsoft offers a comprehensive solution through its Enterprise Mobility Suite, which integrates identity management and advanced threat analytics to protect apps, devices, and data across platforms.