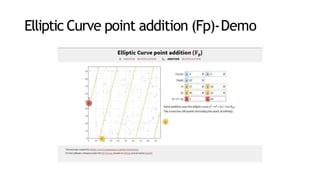
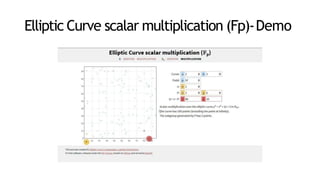
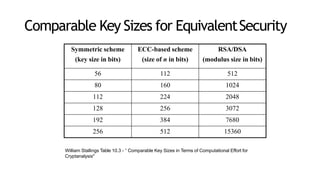
This document provides an introduction to elliptic curve cryptography (ECC). It explains that ECC uses smaller key sizes than RSA for an equivalent security level. ECC performs computations using elliptic curve arithmetic over finite fields rather than integer arithmetic. The document covers elliptic curves over real numbers and finite fields, point addition and scalar multiplication, the discrete logarithm problem that ECC is based on, applications of ECC, and its security advantages compared to RSA. Interactive demos are included to demonstrate point addition and scalar multiplication on elliptic curves over both real numbers and finite fields.









![Elliptic Curve CryptographyDiscrete
Logarithm Problem [ ECCDLP]
• Addition is simple
P + P = 2P
Multiplication is faster , it takes only 8 steps to compute 100P, using point doubling
and add 1. P * 2 = 2P
2. P + 2P = 3P
3. 3P * 2 = 6P
4. 6P *2 = 12P
5. 12P * 2 =24 P
6. P + 24 P = 25 P
7. 25P * 2 = 50 P
8. 50P *2 = 100 P](https://image.slidesharecdn.com/ellipticcurvecryptography-221010081210-1f6b4243/85/ellipticcurvecryptography-pptx-11-320.jpg)
![Elliptic Curve CryptographyDiscrete
Logarithm Problem [ ECCDLP]
• Division is slow,
• In ECC Q is defined as product of n*P is another point on
the curve
Q = nP
given initial point P and final point Q, it is hard to
compute ‘n’ which serves as a secret key.
Brute force method, start with P,every step multiply P
with number 1, 2 and so on,
For each step compare result of P*x where x=1,2,3,…
with Q This problem is known as discrete log problem,
difficult to beak](https://image.slidesharecdn.com/ellipticcurvecryptography-221010081210-1f6b4243/85/ellipticcurvecryptography-pptx-12-320.jpg)