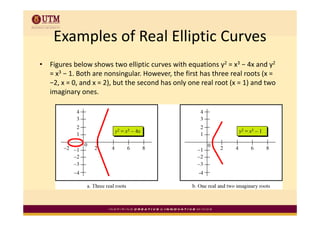
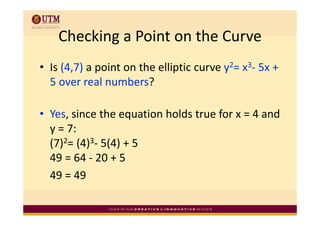
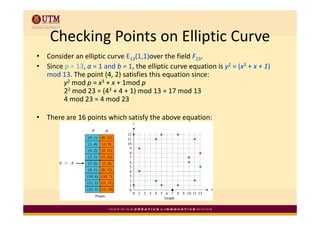
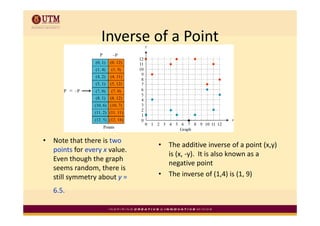
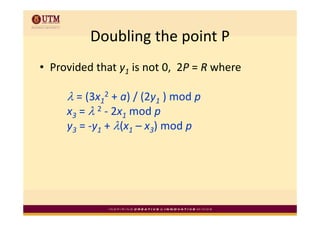
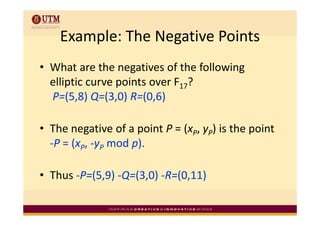
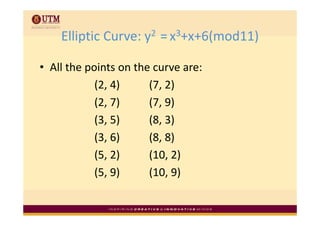
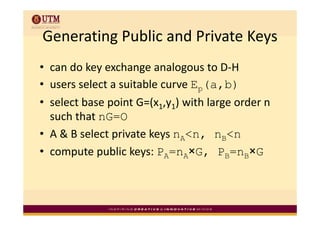
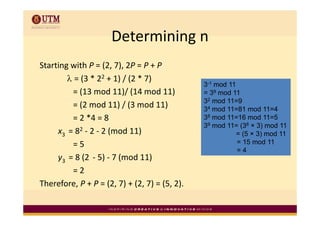
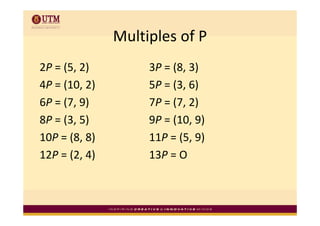
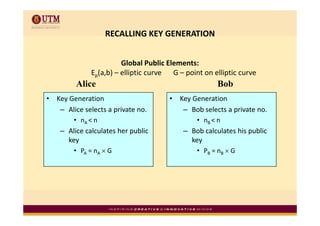
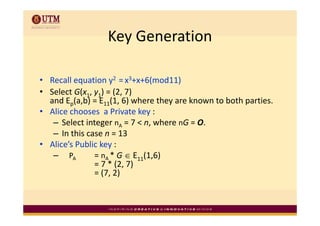
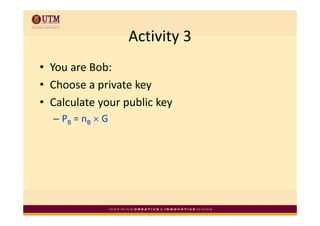
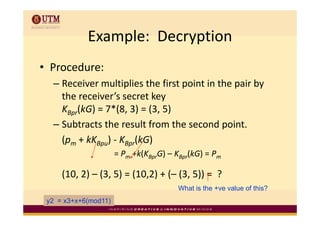
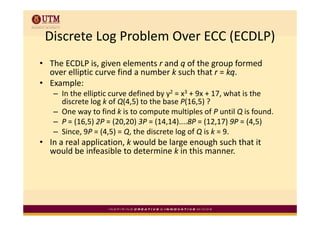
Elliptic curve cryptography uses elliptic curves over finite fields for public-key encryption. It offers the same security as other public-key cryptosystems using smaller key sizes. The points on an elliptic curve over a finite field form a finite abelian group which can be used for cryptographic operations like point addition. Point addition involves calculating the slope between two points and using it to find the x-coordinate of the sum point, while point doubling uses the tangent line to find the double of a point.