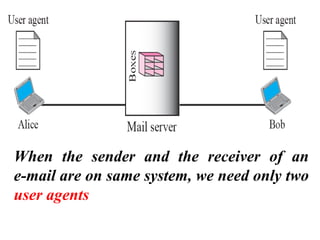
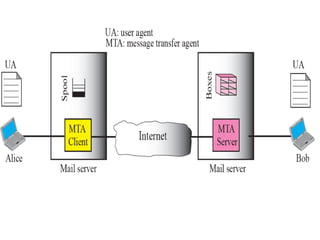
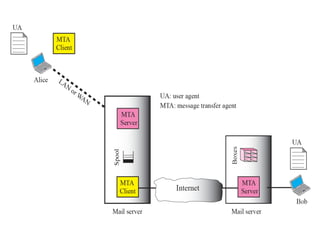
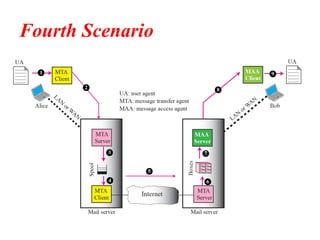
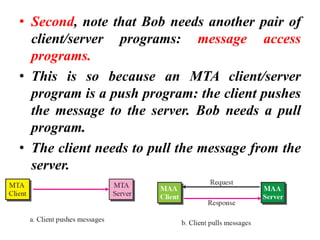
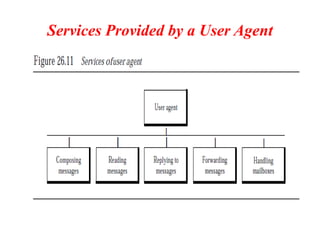
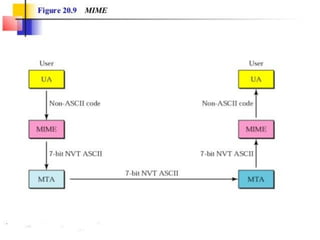
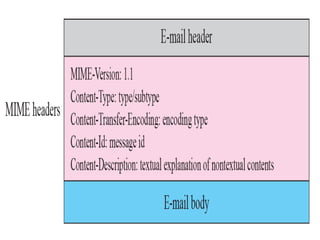
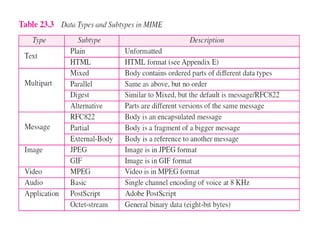
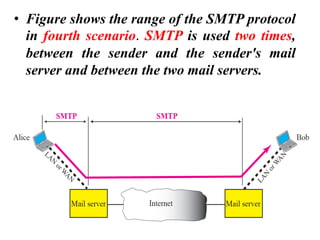
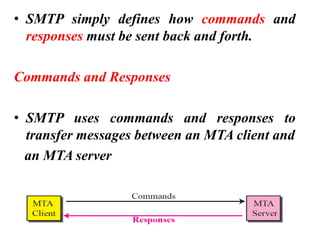
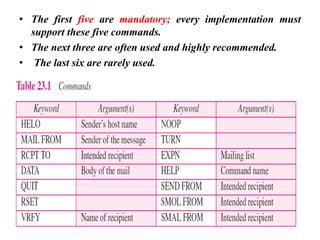
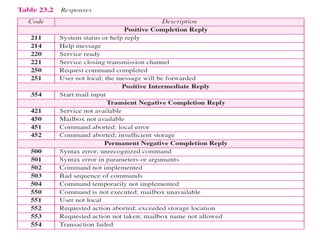
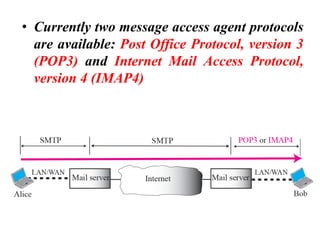
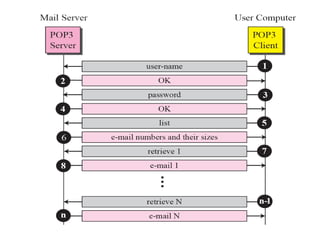
The document discusses the evolution and architecture of electronic mail (e-mail), detailing scenarios for sending and receiving messages across shared systems and the internet. It explains the roles of user agents, message transfer agents (MTAs), and message access agents (MAAs) in handling e-mail, including protocols like SMTP, POP3, and IMAP4. Additionally, it describes MIME for non-ASCII data and various functionalities of user agents, such as composing, reading, and replying to messages.