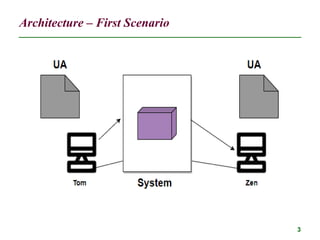
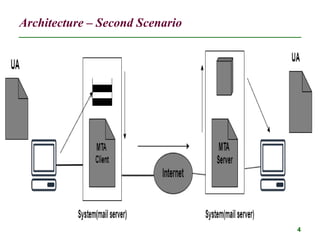
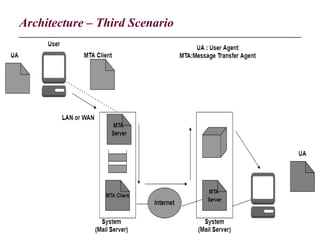
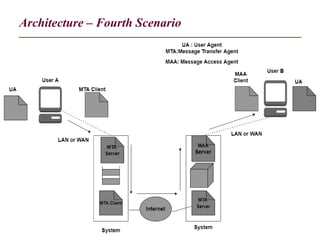
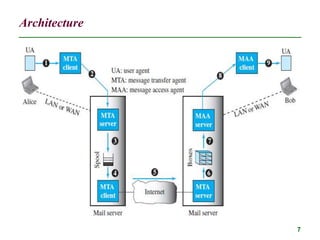
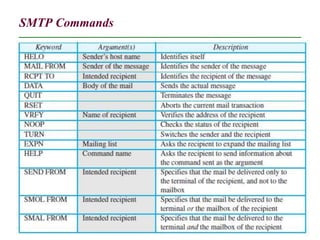
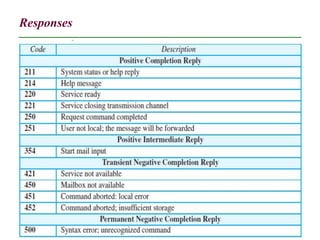
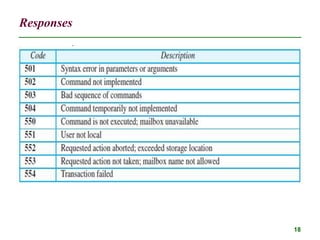
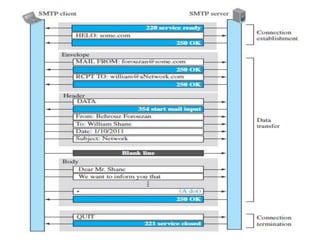
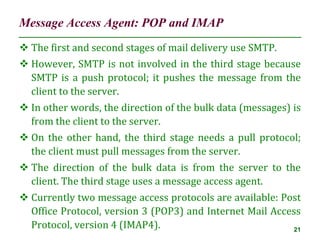
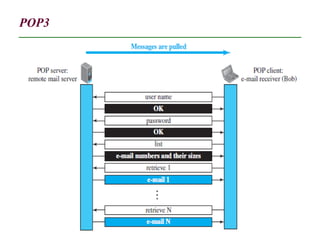
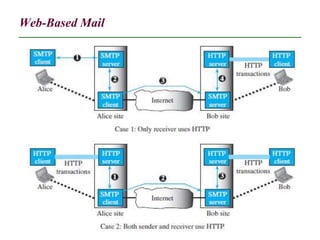
The document discusses electronic mail (email) and its architecture. It describes how email works using a store-and-forward model with email servers accepting, forwarding, delivering, and storing messages on behalf of users. It details the components of an email system including user agents, mail transfer agents (MTA) that use SMTP to transfer messages between servers, and message access agents like POP3 and IMAP that allow users to access stored messages. Key aspects like addressing, commands, responses, and the three phases of mail transfer are also summarized.