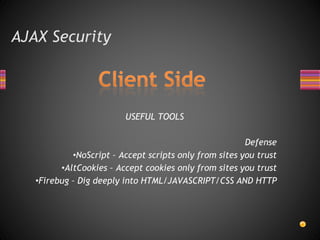
AJAX is a web development technique that allows web pages to be updated asynchronously by exchanging data with a web server behind the scenes, without interfering with the display and behavior of the existing page. While AJAX can improve interactivity, it also introduces some security risks similar to regular web applications, such as cross-site request forgery and malware being introduced through malicious JavaScript code. Developers need to implement authentication, authorization, and data protection to secure AJAX applications and users can help defend themselves using tools like NoScript to block untrusted scripts.