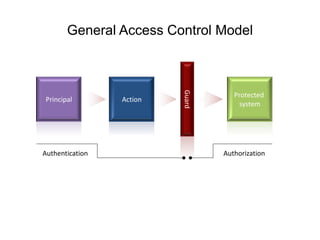
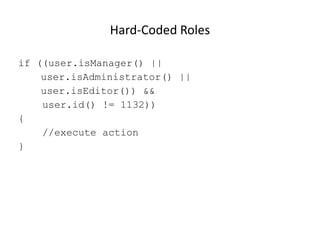
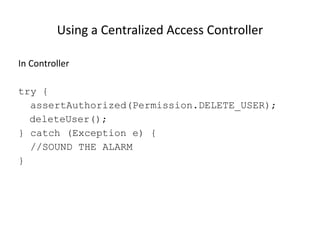
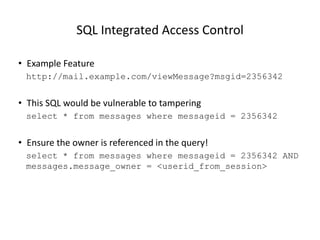
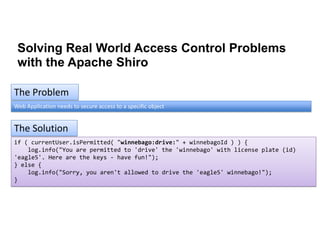
The document discusses access control best practices and common pitfalls in security management. Key recommendations include centralized authorization mechanisms, coding access control based on activities rather than roles, and denying access by default to enhance security. It also highlights risks associated with hard-coded roles and untrusted data that can lead to unauthorized access and data tampering.