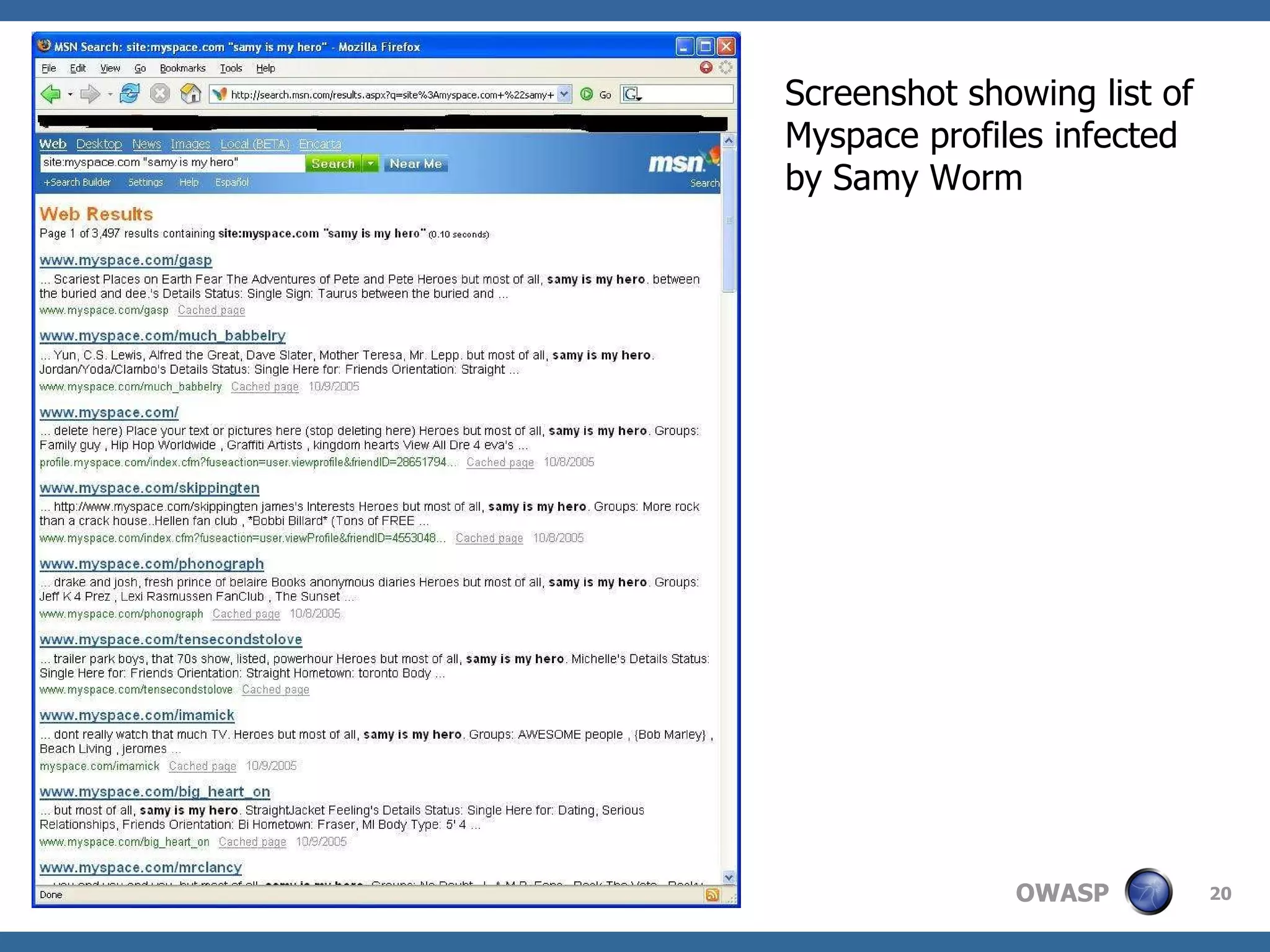
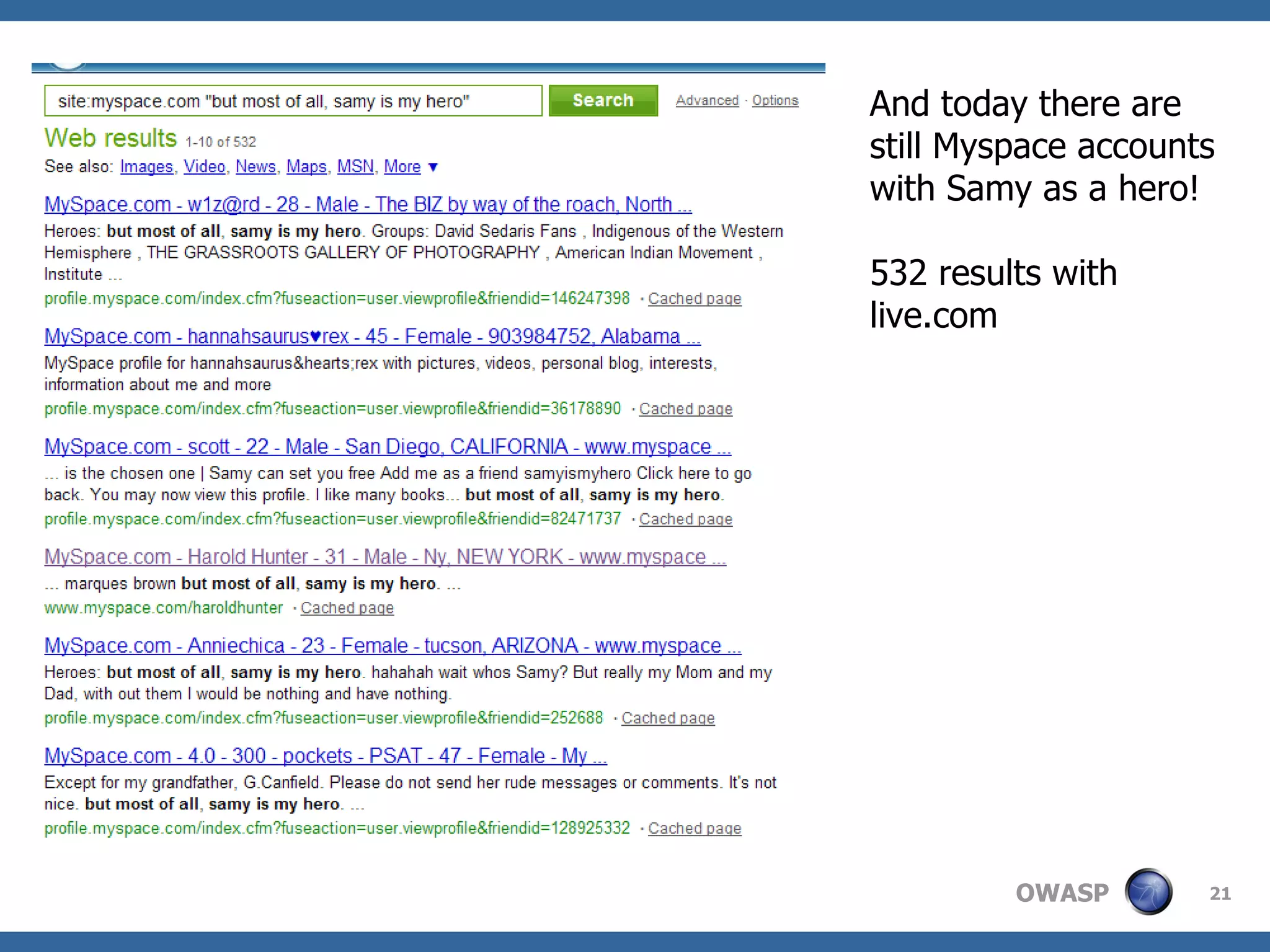
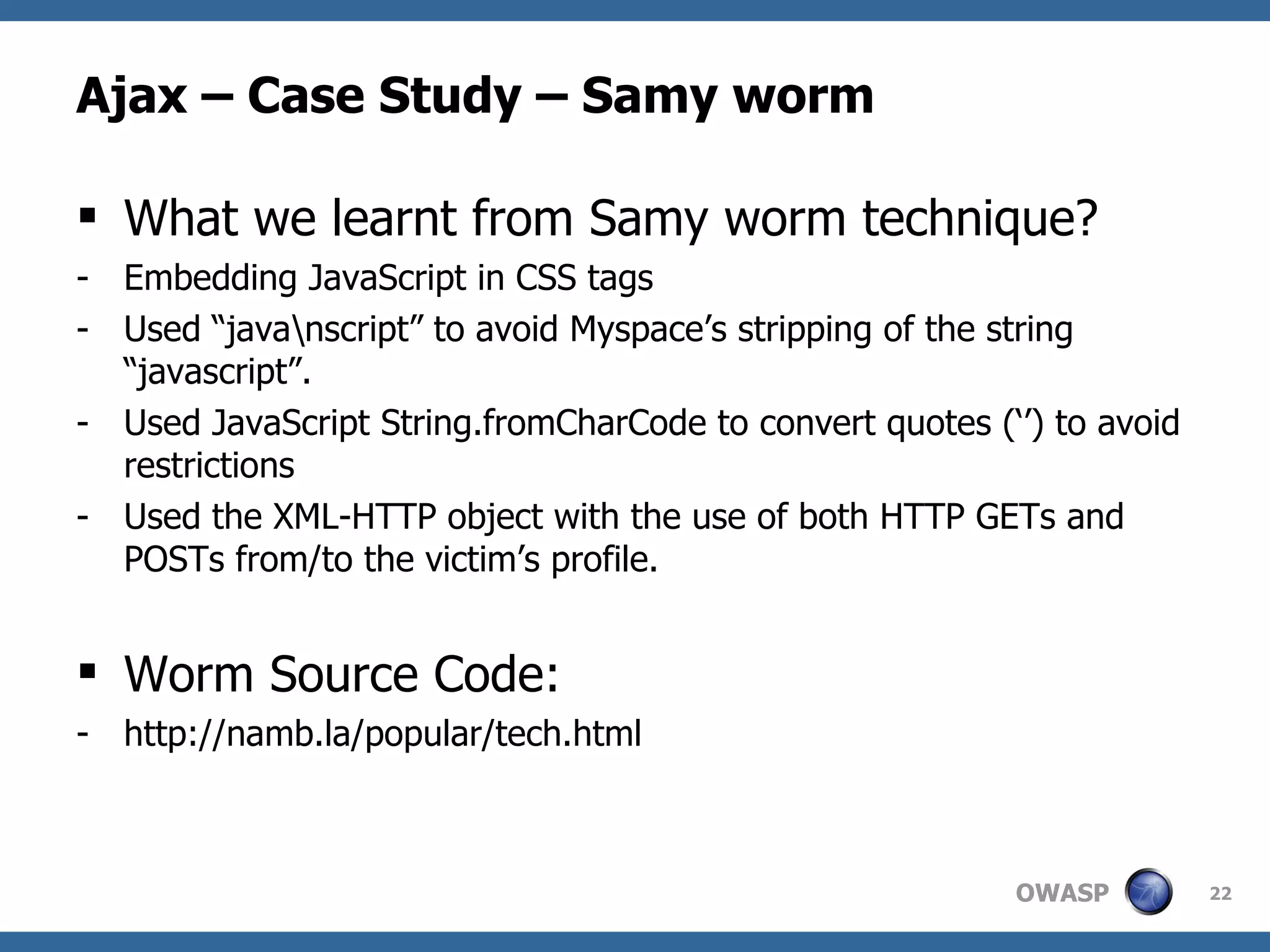
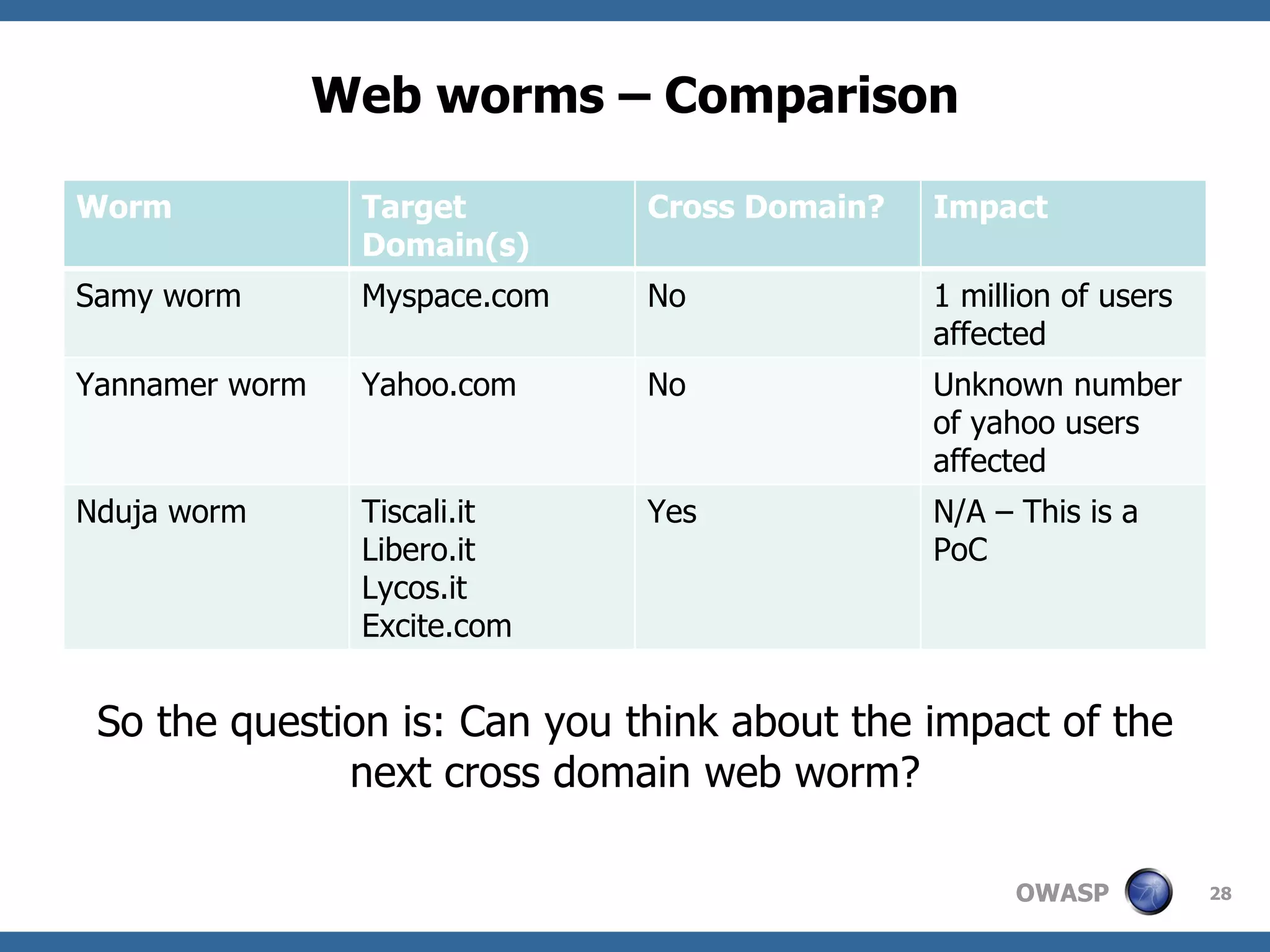
The document discusses AJAX (Asynchronous JavaScript and XML), its components, uses, and associated security concerns, particularly focusing on the server of origin policy. It highlights several real-world attacks, such as the Samy worm and Nguyen webmail XSS worm, illustrating how AJAX can increase attack surfaces and vulnerabilities. The document emphasizes the importance of robust security practices for AJAX applications while providing examples of both developer and user workarounds to security restrictions.








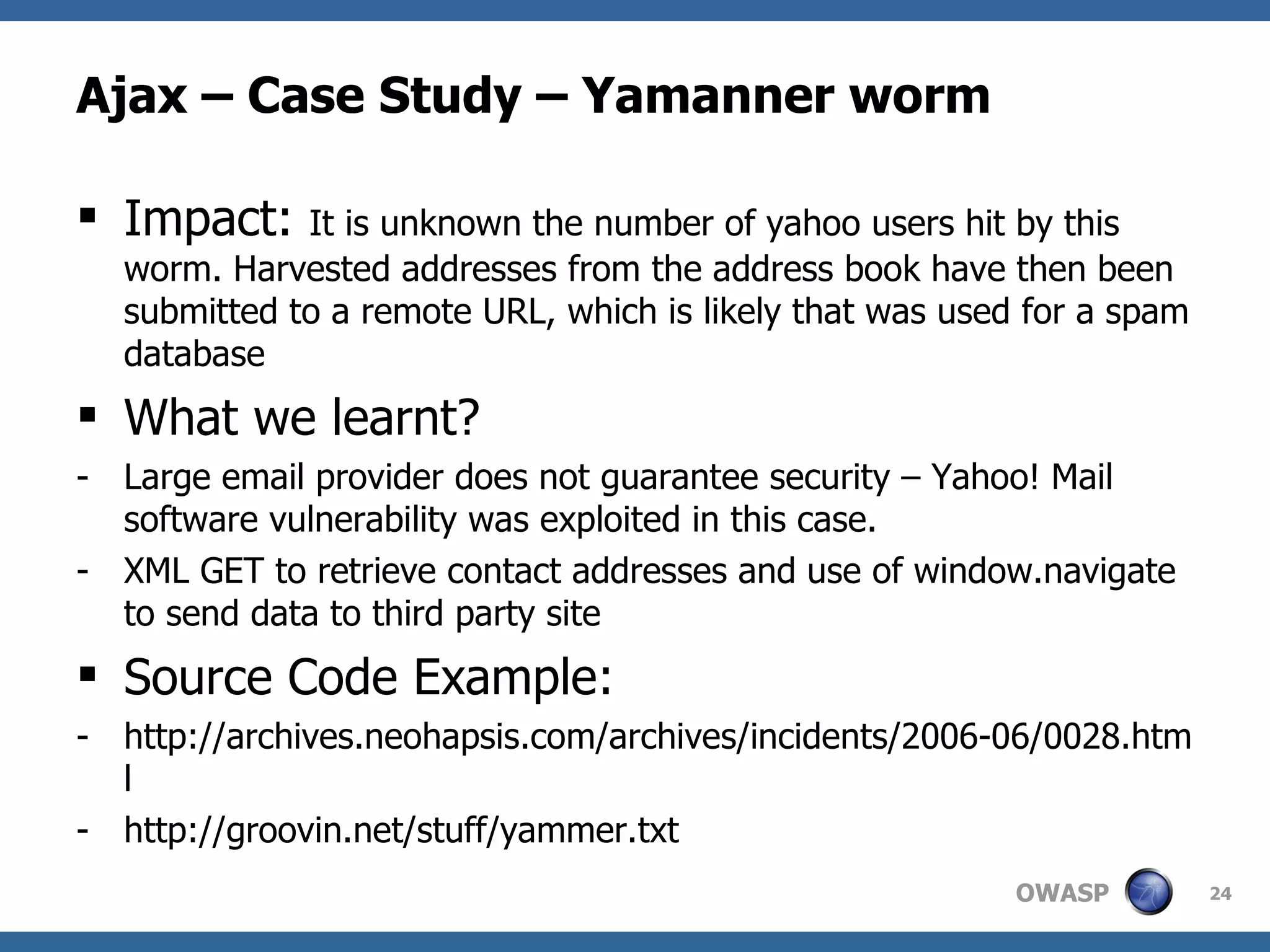
![Ajax – Case Study – Yamanner worm Exploits a vulnerability in the onload event handling of Yahoo! Mail and then executes a script Scans emails in the personal folders of the Yahoo! Mail account Sends a copy of itself to the email addresses gathered Redirects the Web browser from Yahoo! Mail to the following Web site: [http://]www.av3.net/index.htm Sends the list of gathered email addresses to the above URL](https://image.slidesharecdn.com/ajaxsecurity-12695072945114-phpapp01/75/Ajax-Security-23-2048.jpg)



![Questions/Conclusion Thank you! [email_address]](https://image.slidesharecdn.com/ajaxsecurity-12695072945114-phpapp01/75/Ajax-Security-29-2048.jpg)