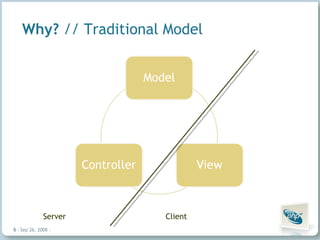
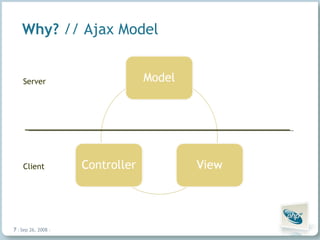
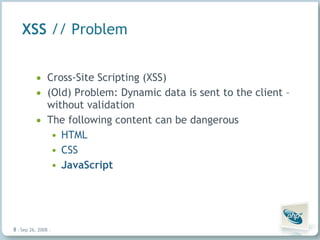
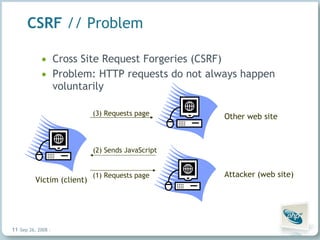
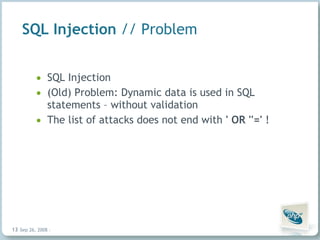
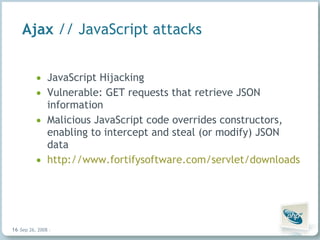
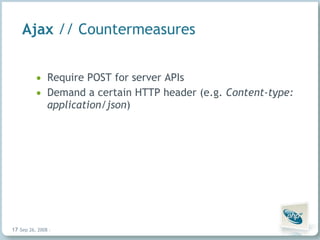
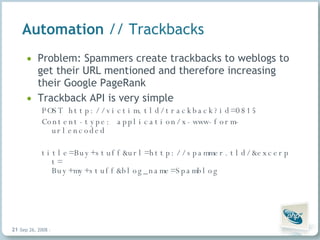
The document discusses common security vulnerabilities in web applications, especially those using AJAX technologies. It notes that 9 out of 10 websites have security issues and over 96% can be compromised manually. The rise of AJAX makes it easier to introduce vulnerabilities like cross-site scripting (XSS) and cross-site request forgery (CSRF). The author advocates validating all user input and escaping all output to bolster security.















![Thank You! http://www.hauser-wenz.de/blog/ [email_address] Please don't forget the session evals! Jun 5, 2009 | |](https://image.slidesharecdn.com/insecure-ajaxy-websites-with-php-1222462878880080-9/85/In-Secure-Ajax-Y-Websites-With-PHP-27-320.jpg)