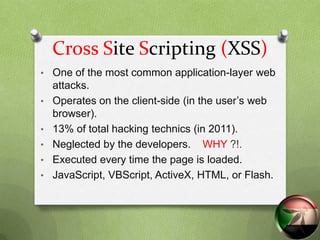
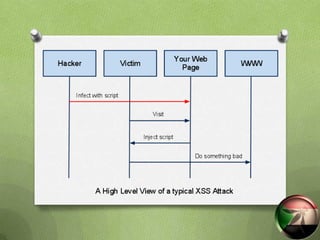
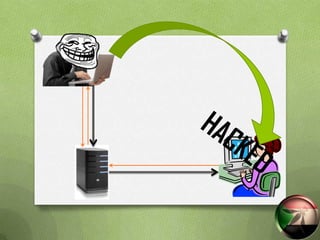
This document discusses cross-site scripting (XSS) attacks. XSS is one of the most common web attacks, operating in the user's browser. It can cause issues like account hijacking or installing malware. There are three main types of XSS attacks. The attacks work by injecting malicious scripts into web pages that are then executed when a user visits the page. Proper input validation and output encoding are recommended to prevent XSS attacks. Developers should filter and encode all untrusted user input to avoid having malicious scripts injected into their applications.



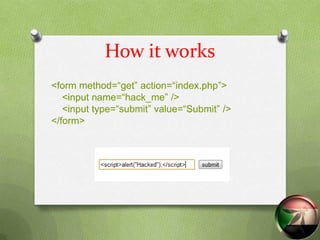
![How it works
<?php
$txt=$_GET[„hack_me‟];
echo $txt; // echo “<script>alert("Hacked");</script>”
?>](https://image.slidesharecdn.com/crosssitescriptingxss-130102142220-phpapp02/85/Cross-Site-Scripting-XSS-9-320.jpg)



![XSS Countermeasures
• HTML Escape Before Inserting Untrusted Data
into HTML Element Content:
• ESAPI Encoder Example:
String safe = ESAPI.encoder().encodeForHTML(
request.getParameter( "input" ) );
• AntiXSS Equivalent:
string safe =
Microsoft.Security.Application.AntiXss.HtmlEncode(
Request.QueryString[ "input" ] );](https://image.slidesharecdn.com/crosssitescriptingxss-130102142220-phpapp02/85/Cross-Site-Scripting-XSS-13-320.jpg)