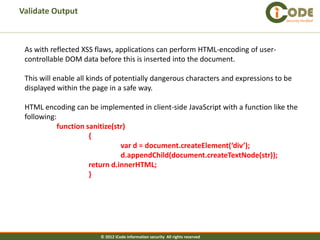
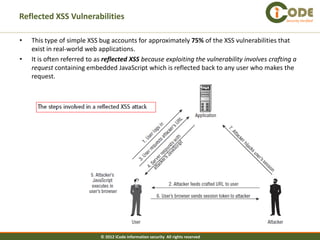
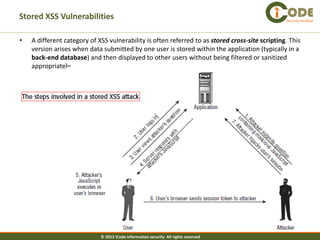
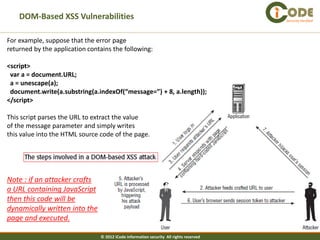
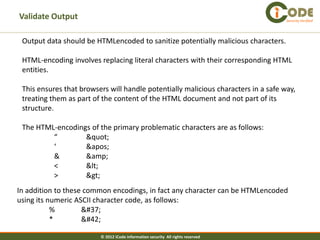
The document discusses cross-site scripting (XSS) attacks, which are one of the most common web application vulnerabilities. It describes different types of XSS attacks, including reflected XSS, stored XSS, and DOM-based XSS. The document also provides examples of how these attacks work and payloads that can be used. Additionally, it discusses how to prevent XSS vulnerabilities by validating input and output and eliminating dangerous insertion points.




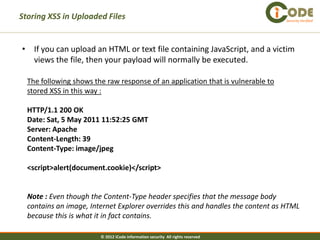










![Validate Input Security Verified
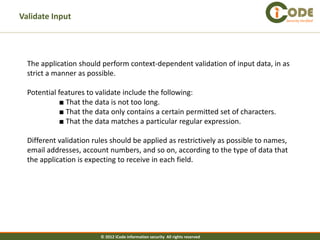
In many situations, applications can perform rigorous validation on the data being
processed. Indeed, this is one area where client-side validation can be more effective
than server-side validation.
Validating that the data about to be inserted into the document only contains
alphanumeric characters and whitespace could be for example:
<script>
var a = document.URL;
a = a.substring(a.indexOf(“message=”) + 8, a.length);
a = unescape(a);
var regex=/^([A-Za-z0-9+s])*$/;
if (regex.test(a))
document.write(a);
</script>
© 2012 iCode information security All rights reserved](https://image.slidesharecdn.com/appsecchapter04appsecxsscasestudy-130203110107-phpapp02/85/Appsec-XSS-Case-Study-21-320.jpg)