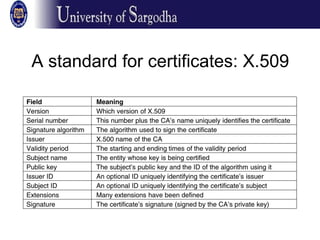
This document discusses key management and protocols for distributing public keys securely. It presents three solutions: appending public keys to emails, posting them on websites, and using a public key authority or certificate authority. The main challenges are authenticating users' identities and distributing updated keys securely. A public key authority maintains a directory of public keys but introduces a bottleneck. A certificate authority signs certificates that bind keys to identities, avoiding the need to be constantly online but requiring in-person identity verification. Standards like X.509 were introduced to format certificates uniformly. A public key infrastructure model is proposed using a hierarchy of certificate authorities to issue certificates at various levels.