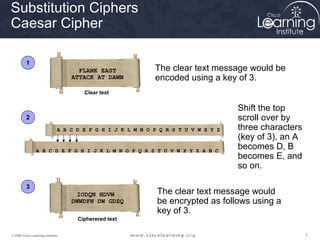
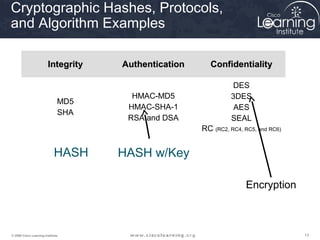
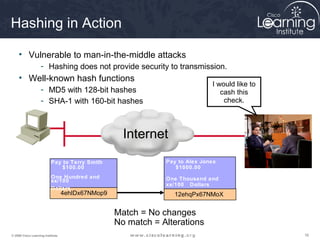
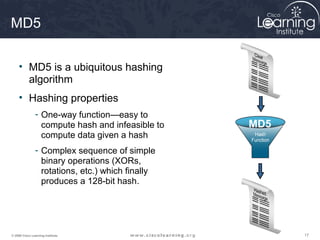
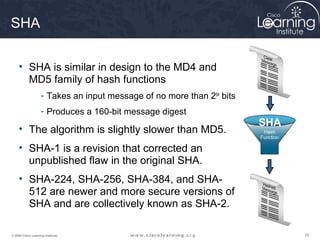
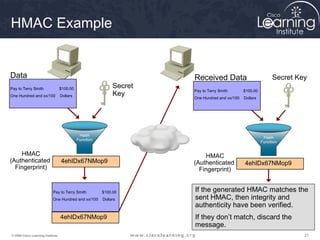
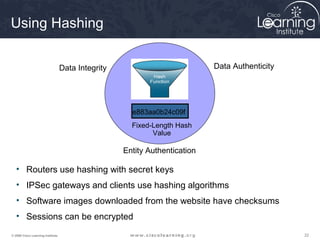
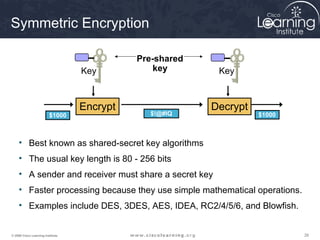
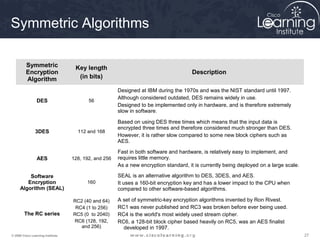
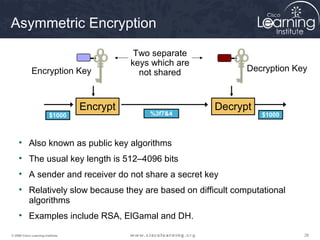
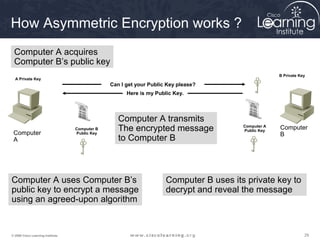
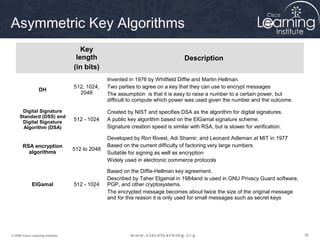
The document provides an overview of cryptographic systems and concepts such as hashing, symmetric and asymmetric encryption, digital signatures, and specific algorithms like MD5, SHA, DES, AES, RSA and DSA. It discusses how these concepts work, their applications in network security, and considerations around key length and strength. Examples are provided to illustrate cryptographic techniques like hashing, HMAC, encryption and digital signatures.