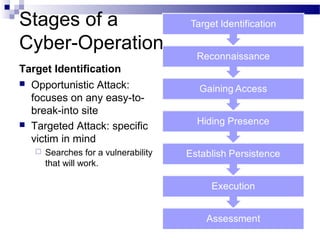
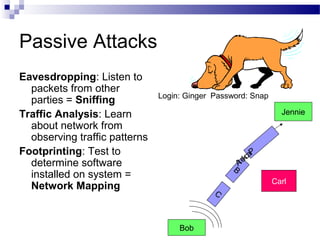
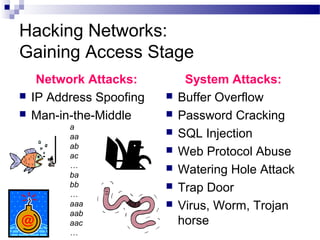
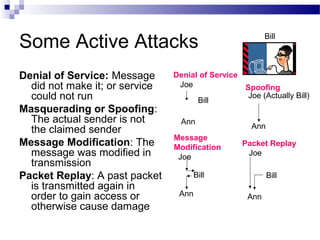
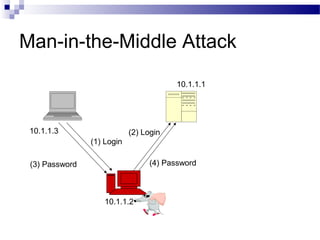
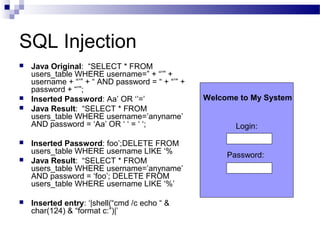
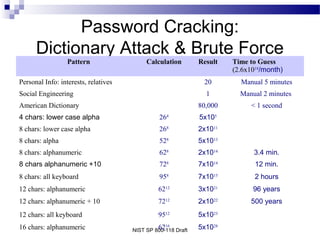
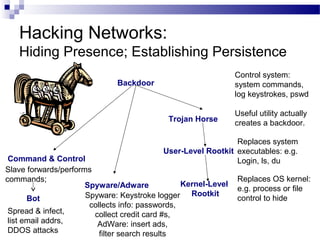
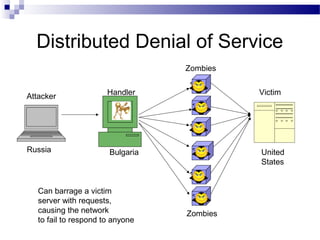
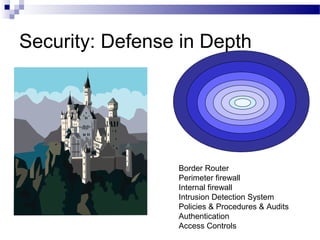
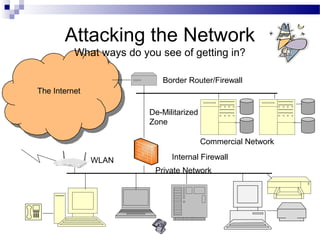
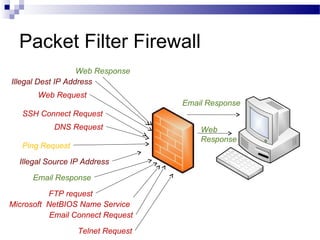
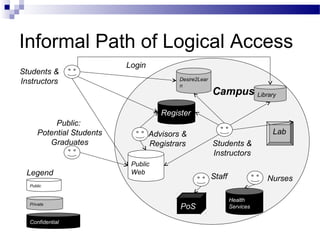
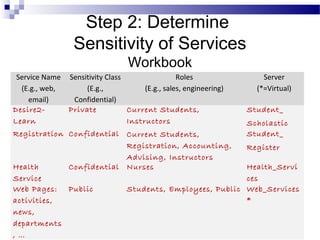
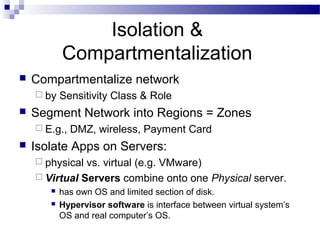
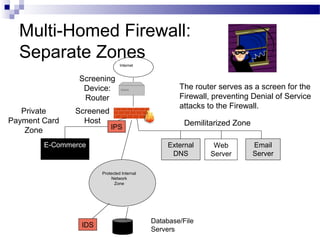
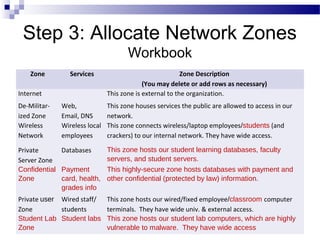
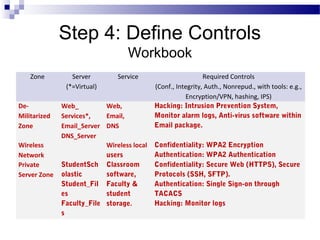
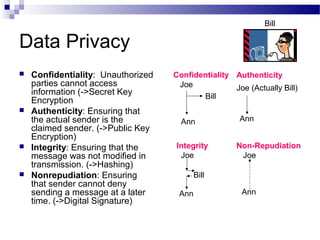
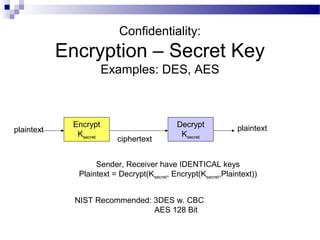
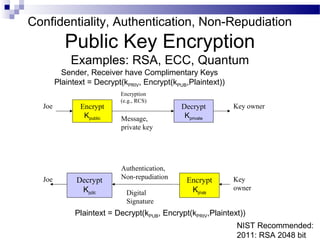
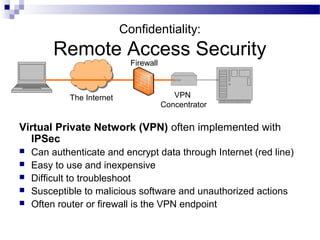
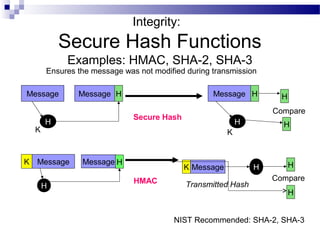
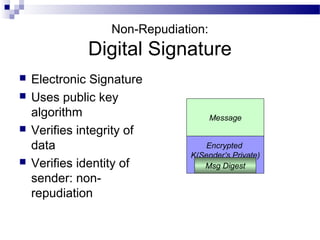
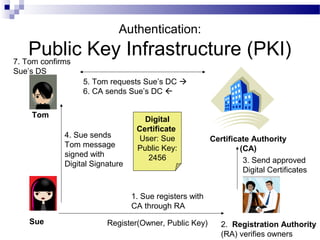
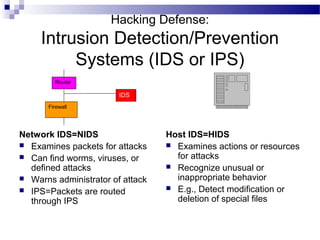
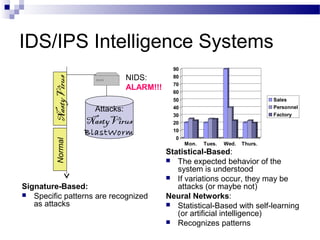
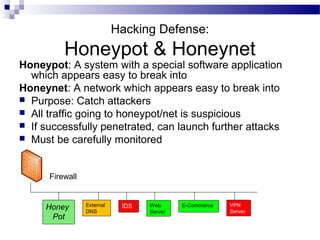
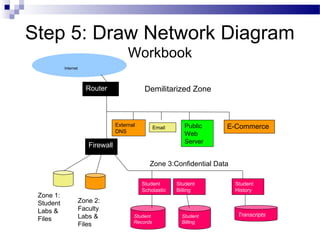
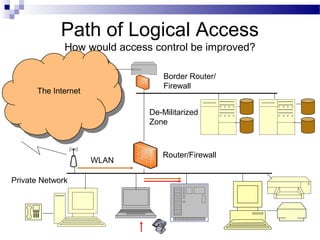
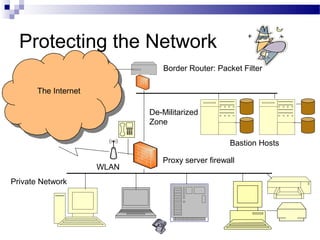
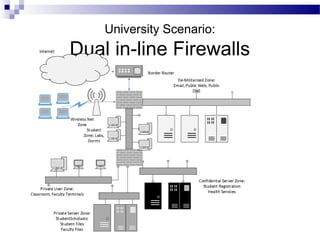
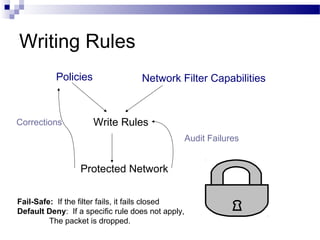
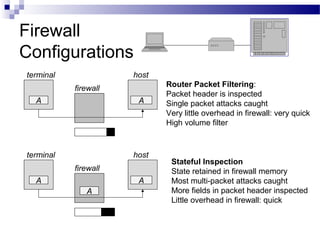
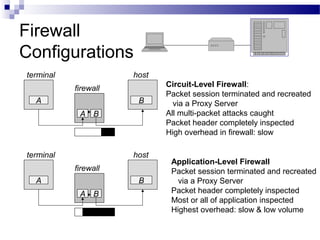
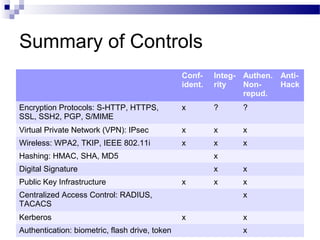
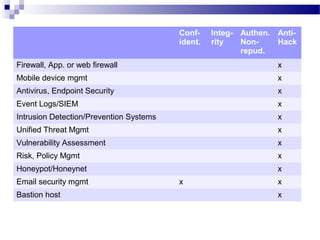
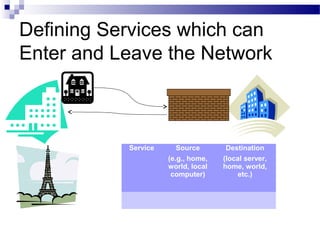
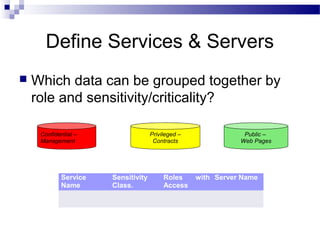
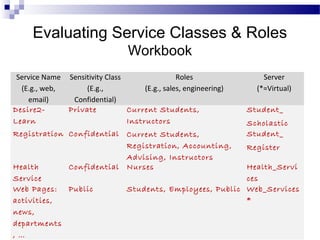
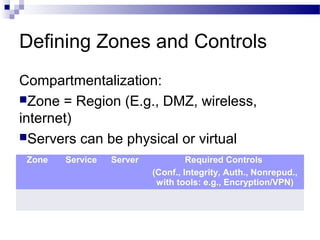
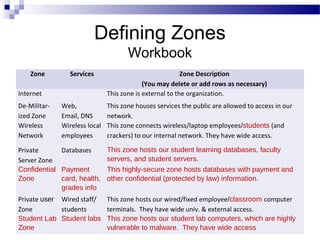
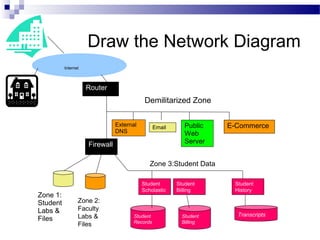
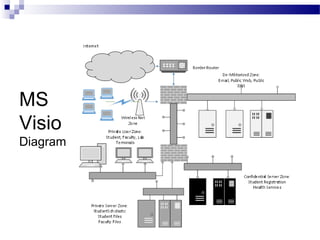
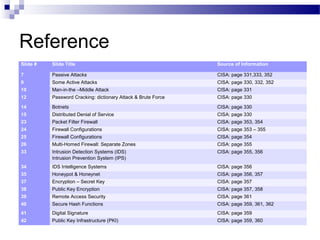
This document discusses network security and provides definitions for common attacks, technical solutions, and objectives. It begins with an overview of the challenges of network security and stages of a cyber operation. Specific attacks covered include denial of service, man-in-the-middle, SQL injection, and password cracking. Defenses such as firewalls, intrusion detection/prevention systems, and encryption techniques are also defined. The objectives are to understand these concepts and apply security best practices like layered defenses and network segmentation.