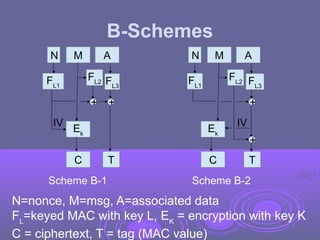
Chapter 12 of 'Cryptography and Network Security' discusses message authentication codes (MACs), emphasizing their role in ensuring message integrity, validating the originator's identity, and providing non-repudiation. It covers various MAC implementations, including HMAC and CMAC, the importance of cryptographic hash functions, and the security considerations necessary for effective message authentication. Additionally, the chapter explains different methodologies for combining encryption and MACs to achieve authenticated encryption, along with pseudorandom number generation using hash functions.




















![HMAC
specified as Internet standard RFC2104
uses hash function on the message:
HMACK(M)= Hash[(K+
XOR opad) ||
Hash[(K+
XOR ipad) || M)]
]
where K+
is the key padded out to block size
opad, ipad are specified padding constants
overhead is just 3 more hash block calculations
than the message needs alone
any hash function can be used
eg. MD5, SHA-1, RIPEMD-160, Whirlpool](https://image.slidesharecdn.com/unit4-11-240821072314-93bf916f/85/unit4-predicate-logic-in-artificial-intelligence-23-320.jpg)