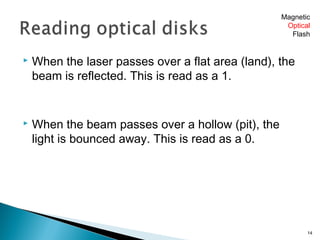
This document discusses different types of computer storage technologies including magnetic, optical, and flash storage. It provides details on the characteristics of hard disks, optical disks, USB flash drives, and tape storage. Hard disks use magnetic particles to store data on spinning platters, while optical disks like CDs and DVDs use lasers to read and write data in pits and lands on a disk. Flash drives are small, portable storage that uses flash memory chips. Tape storage is used for backups and can reliably store large amounts of data but is slower than other options.