Embed presentation
Downloaded 275 times

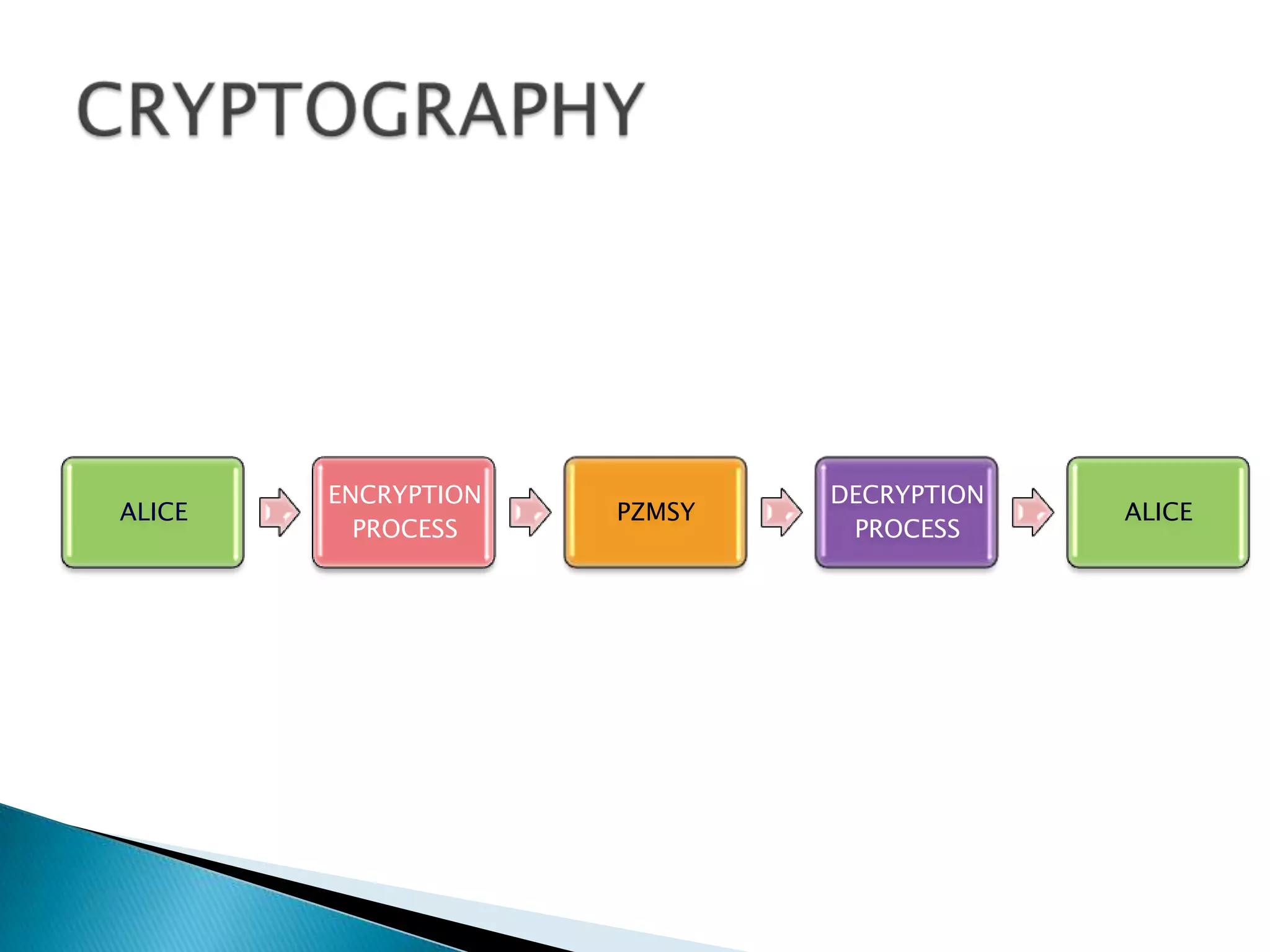
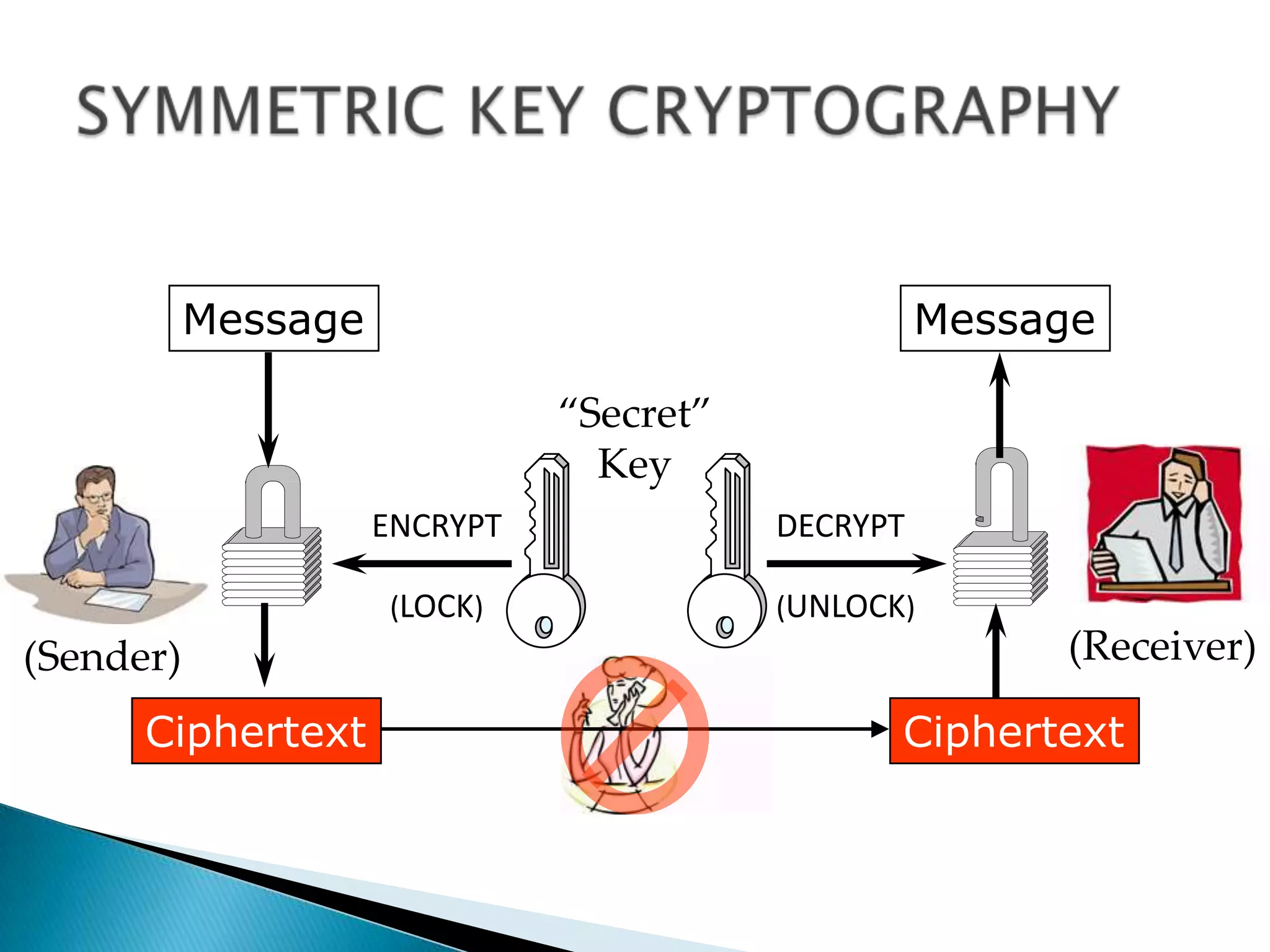
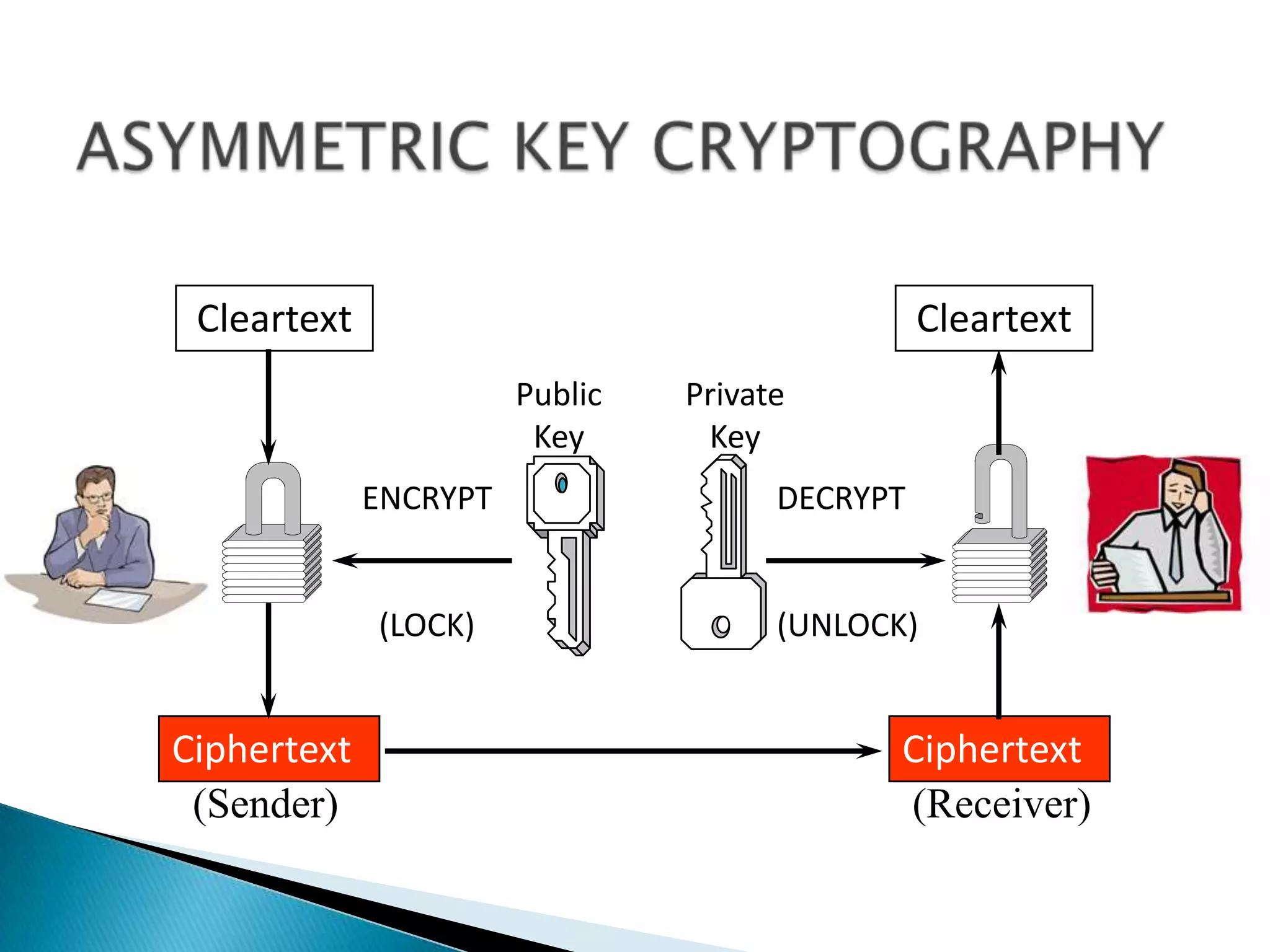
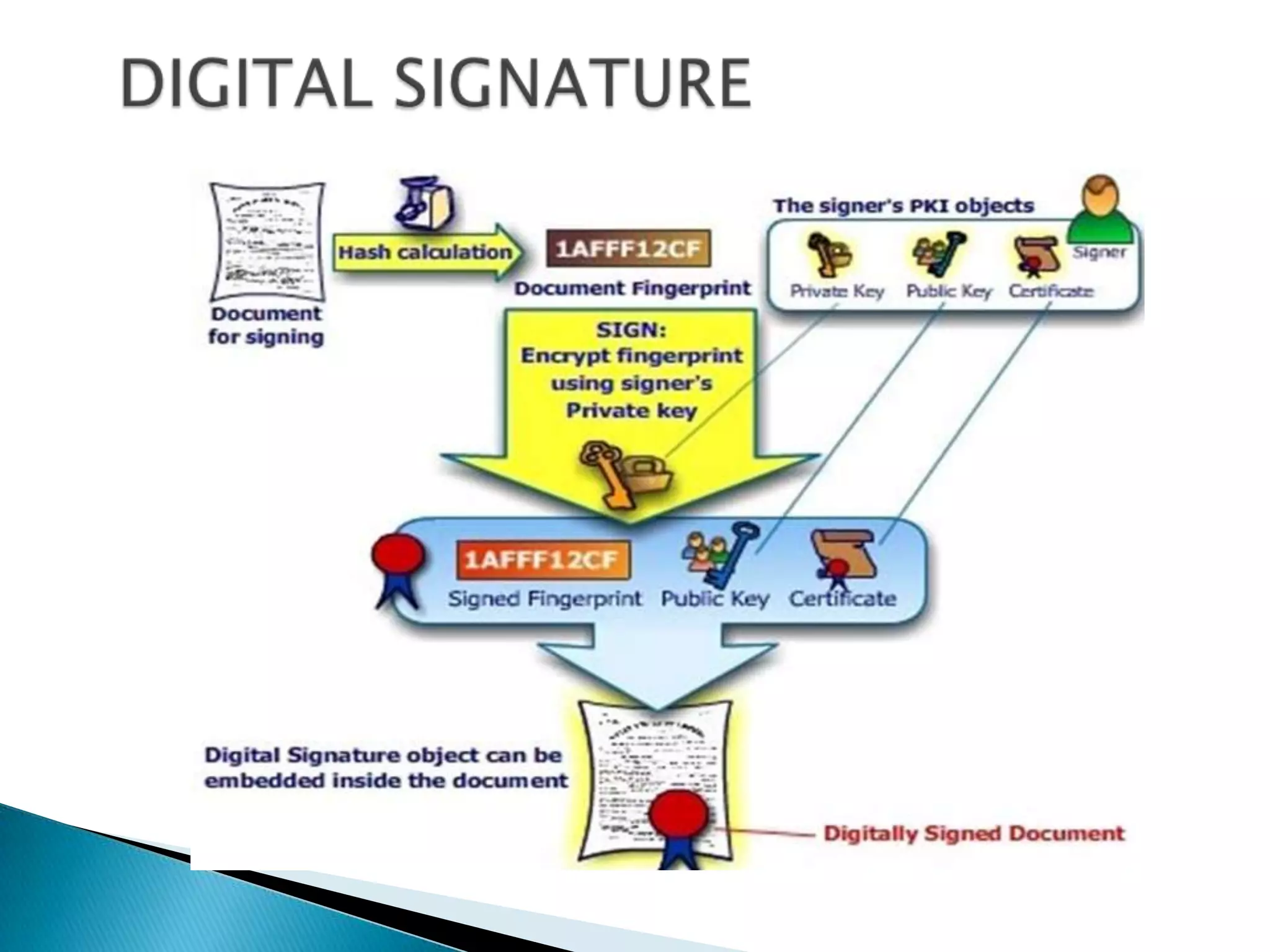


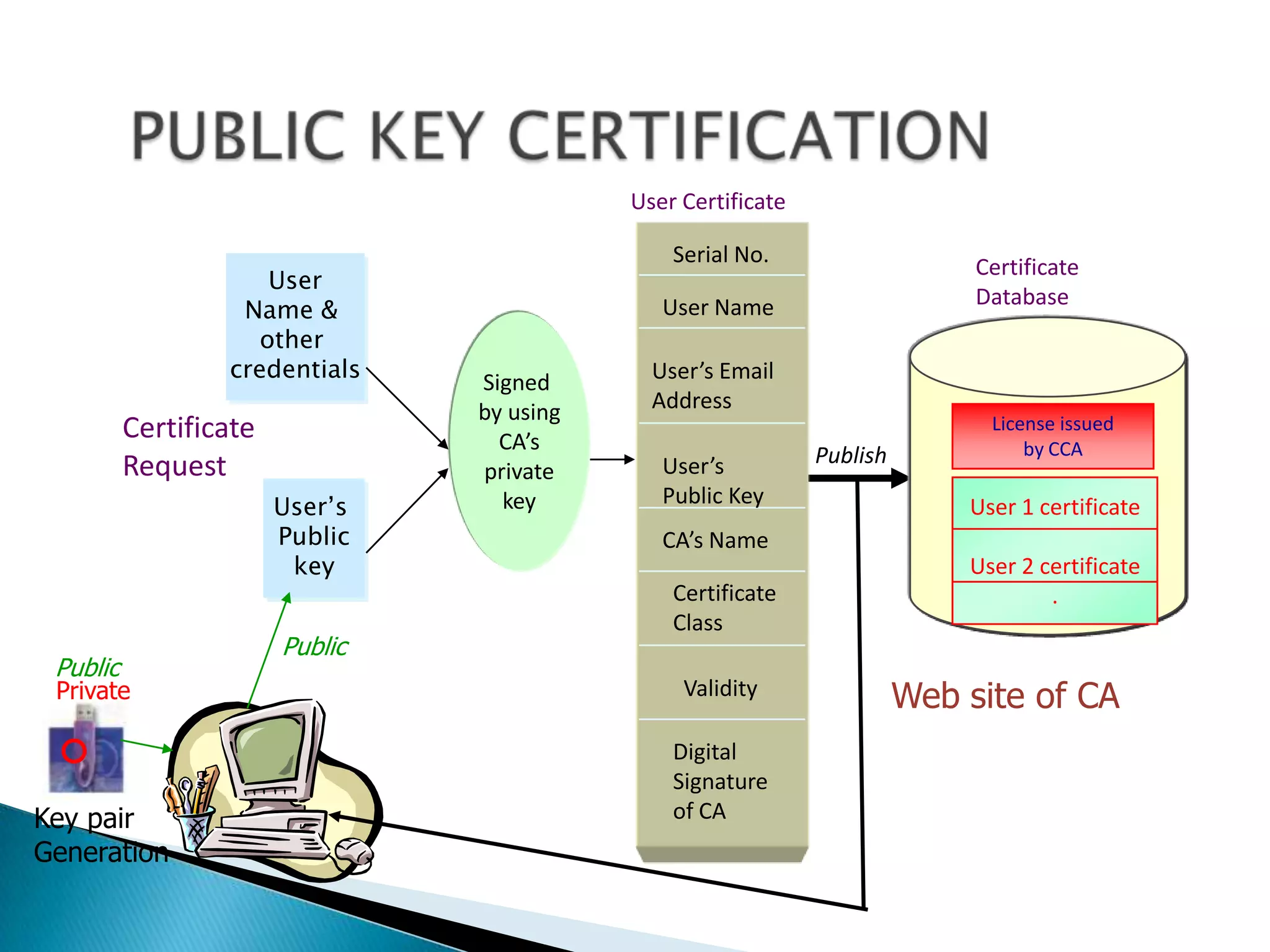
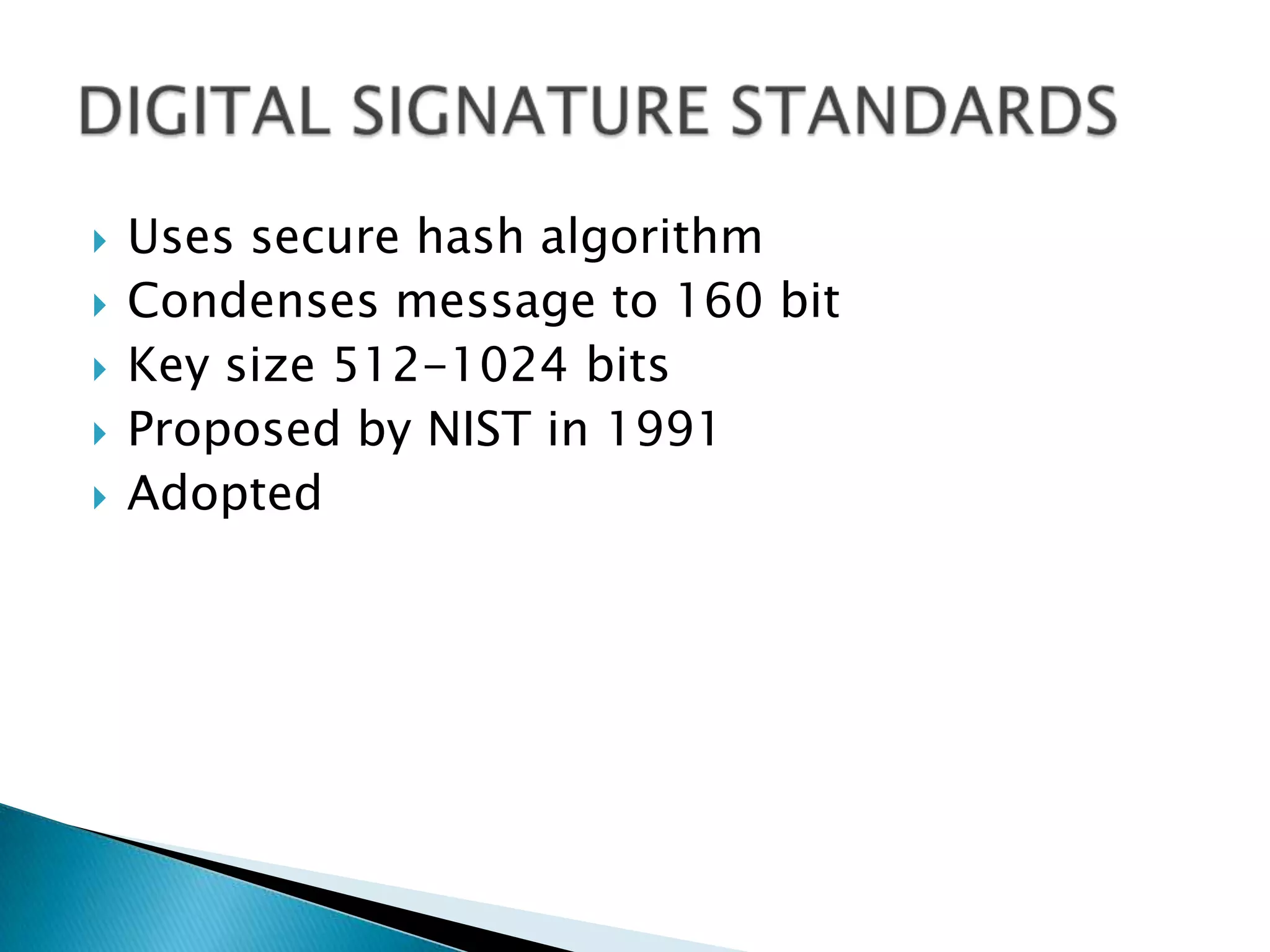
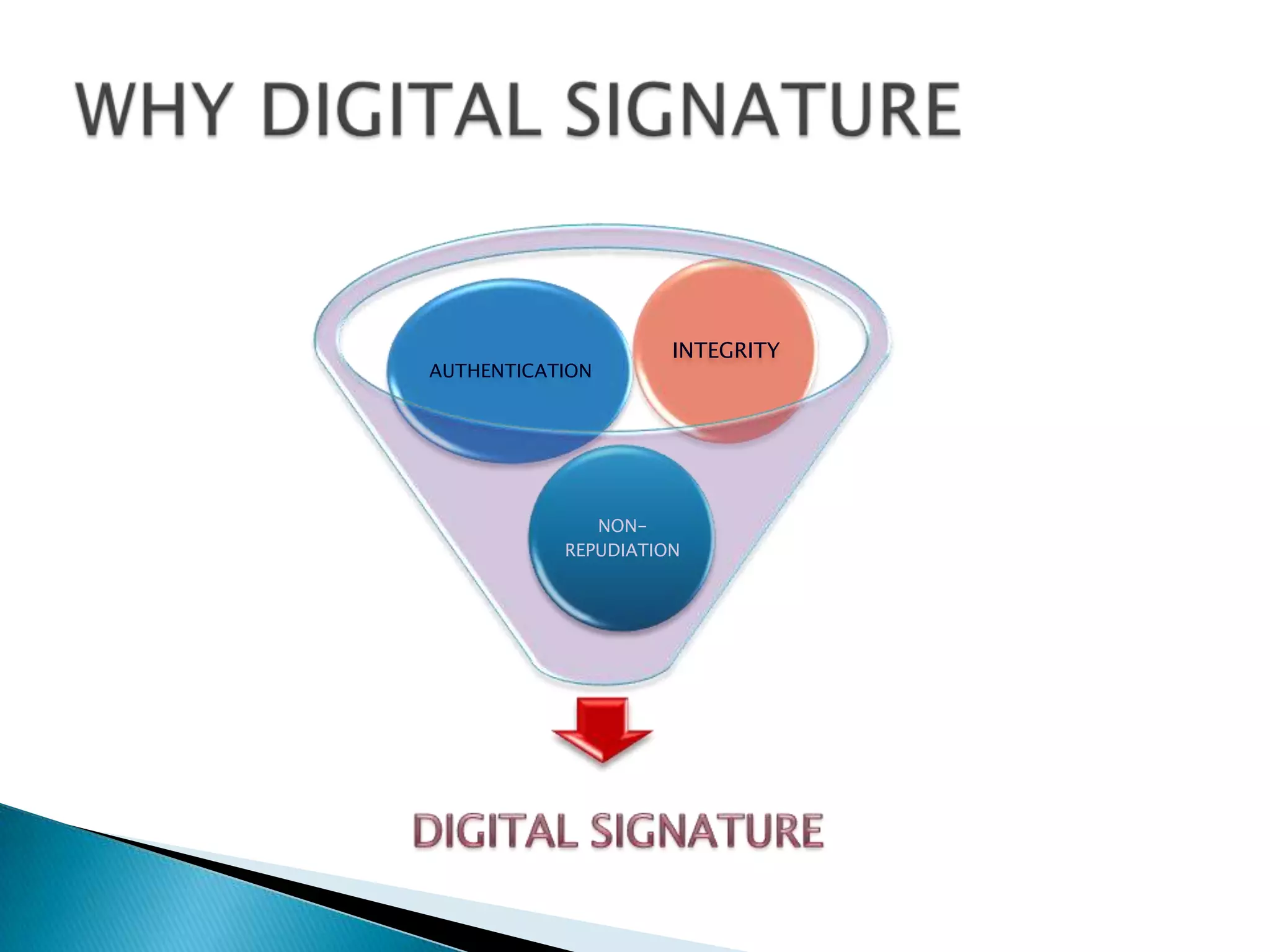
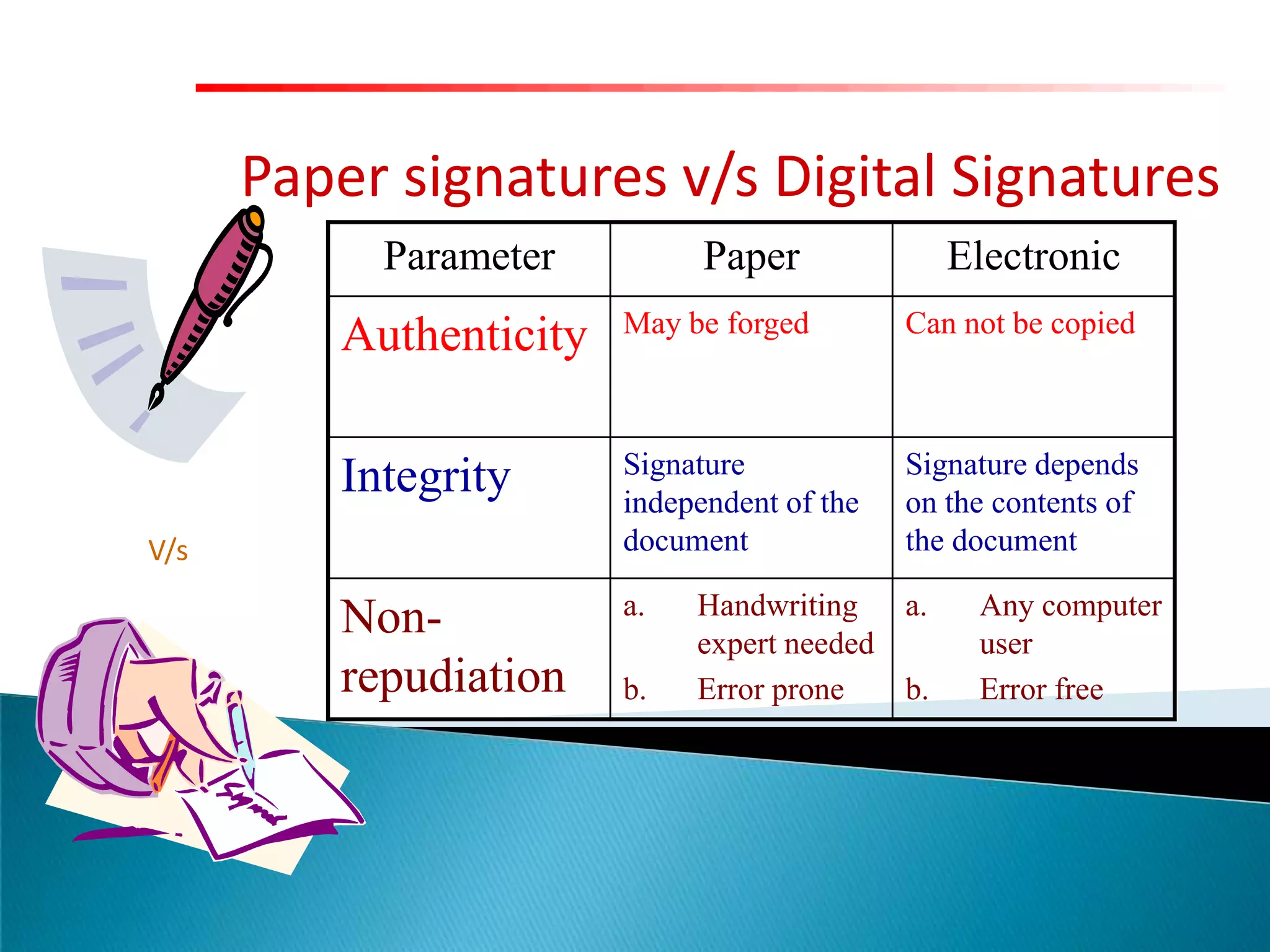

This document summarizes key aspects of digital signatures and encryption. It explains that digital signatures use public/private key pairs to encrypt messages for authentication, integrity and non-repudiation. A certificate authority acts as a trusted third party by issuing digital certificates that contain a user's public key and identity information signed with the CA's private key. The document also compares features of paper signatures to digital signatures.












