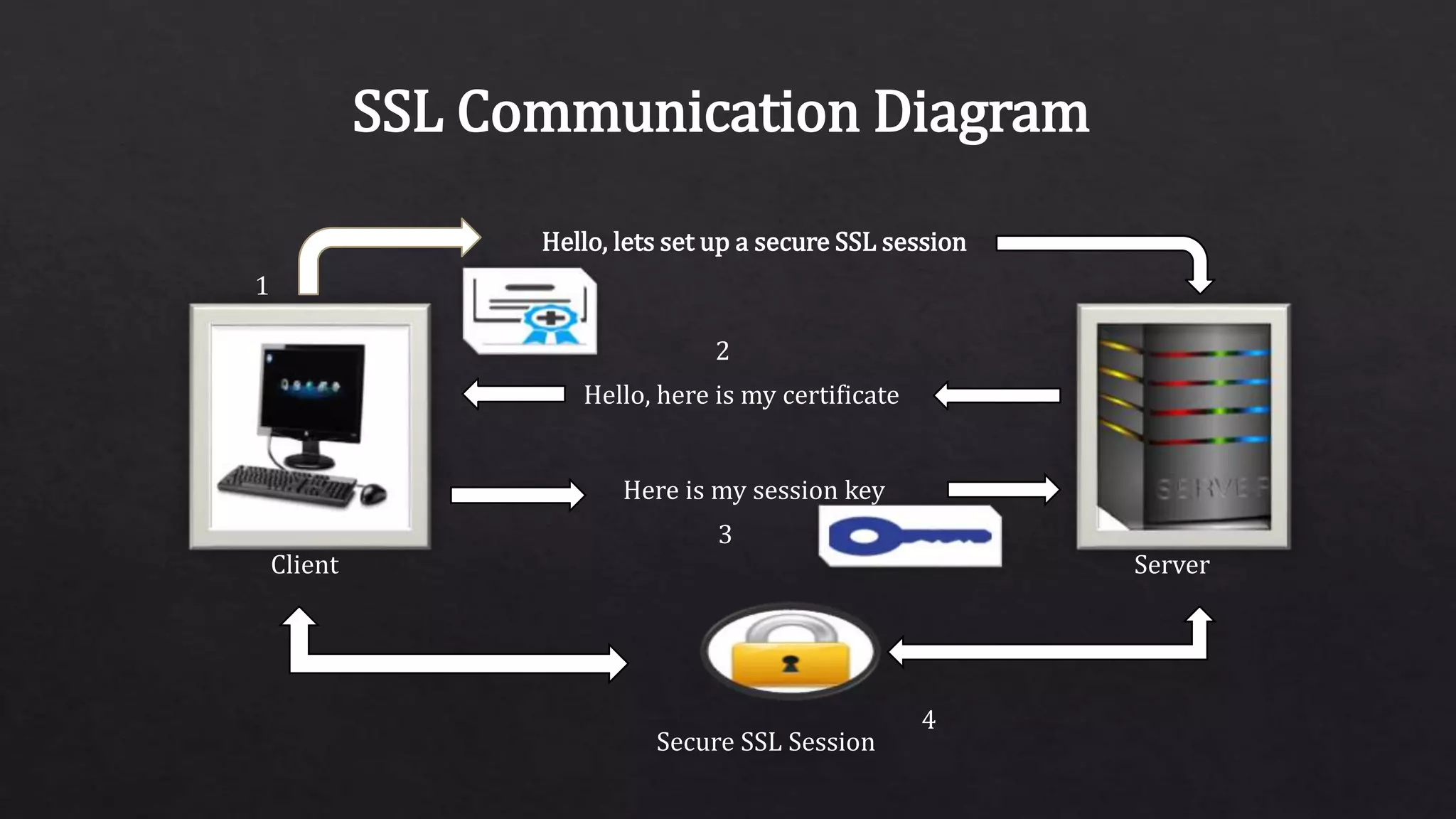
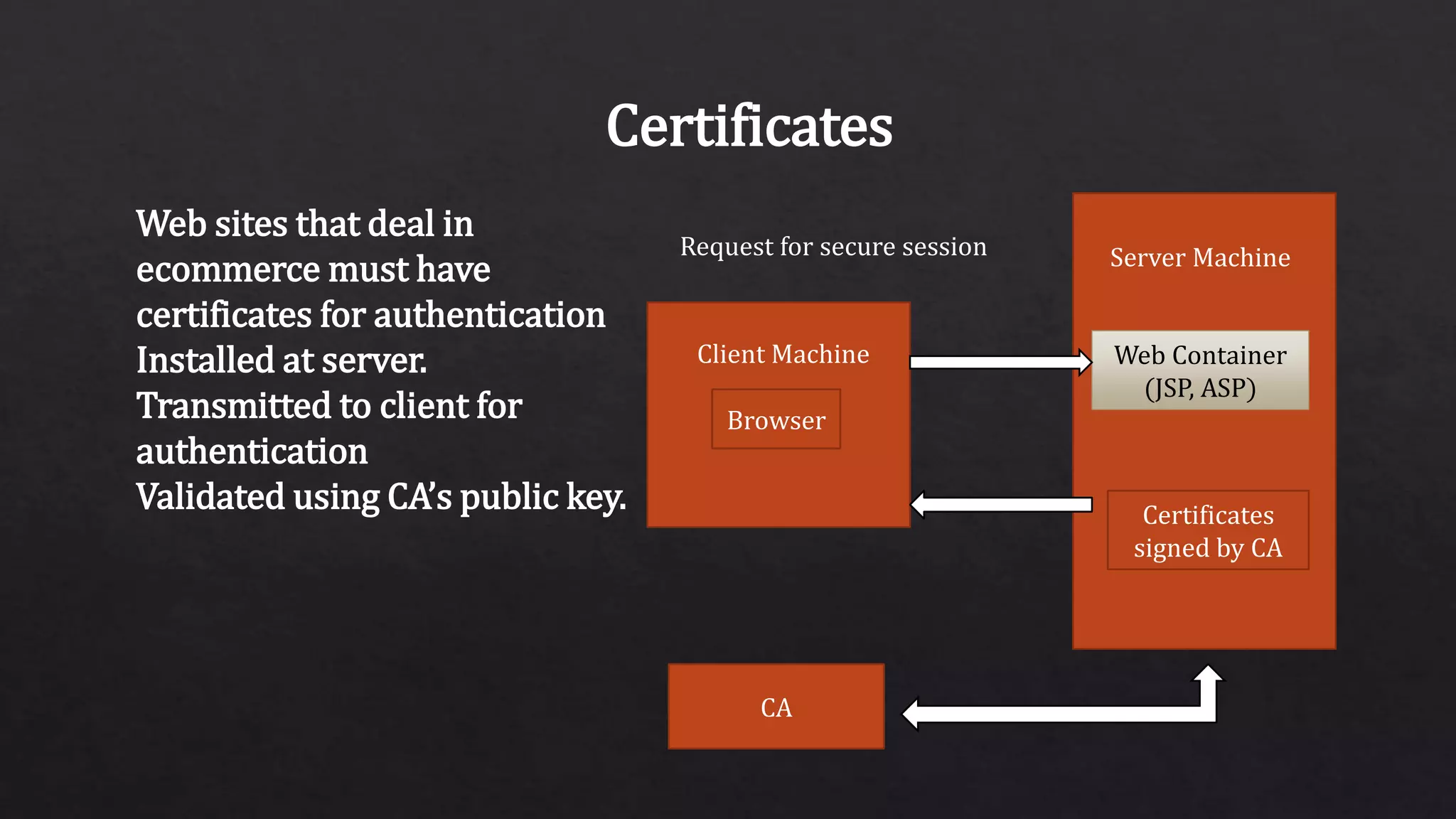
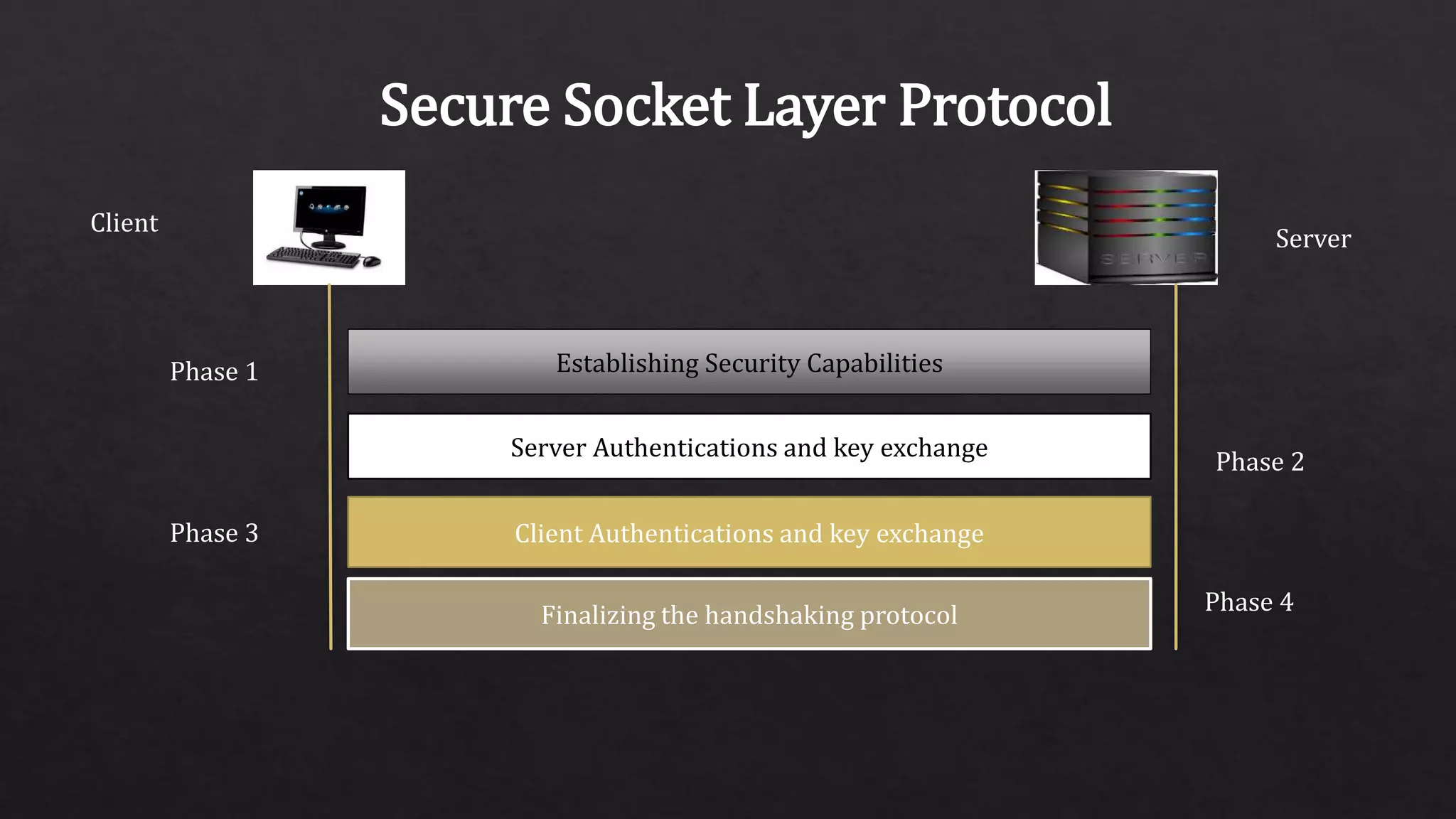
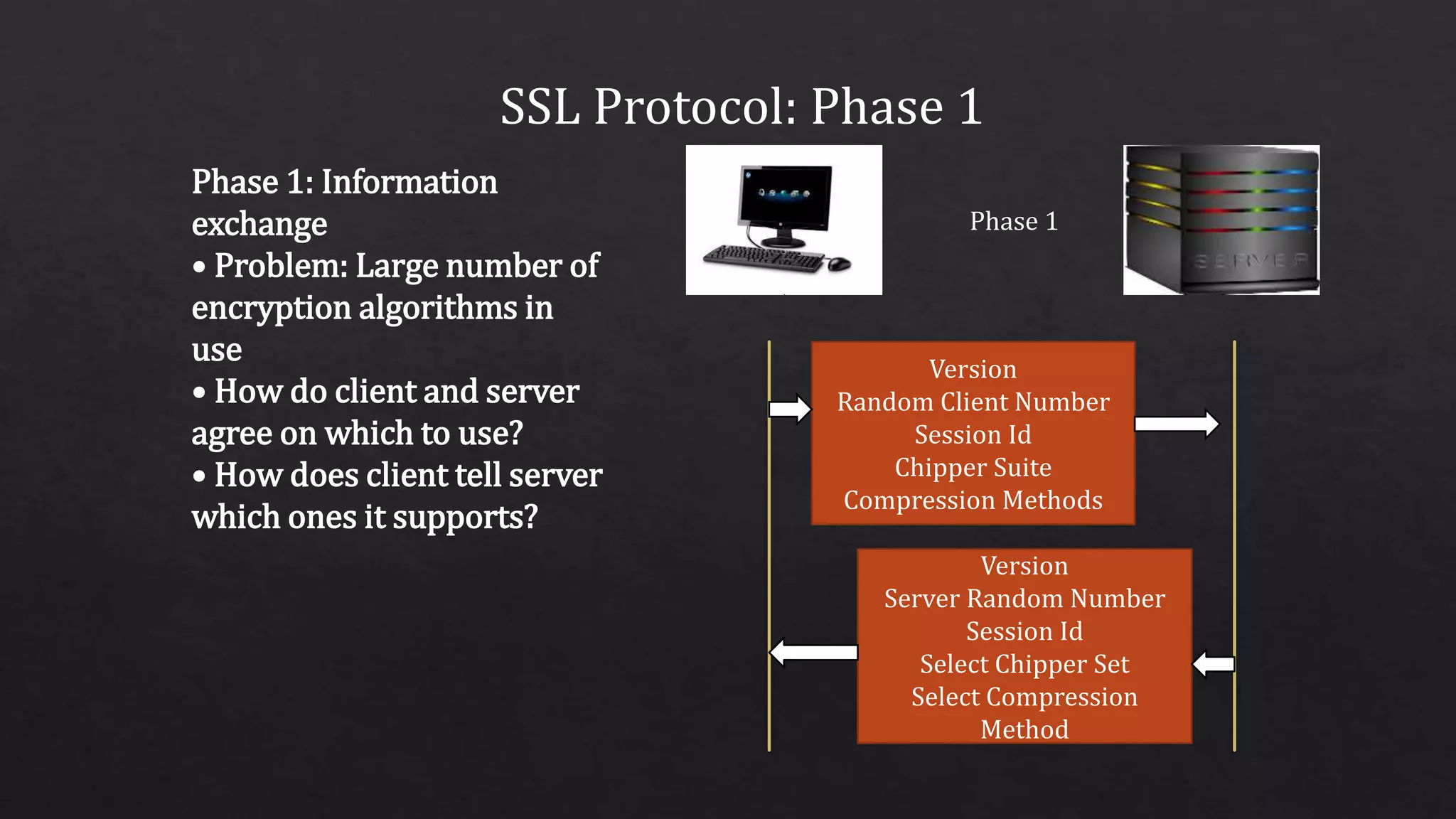
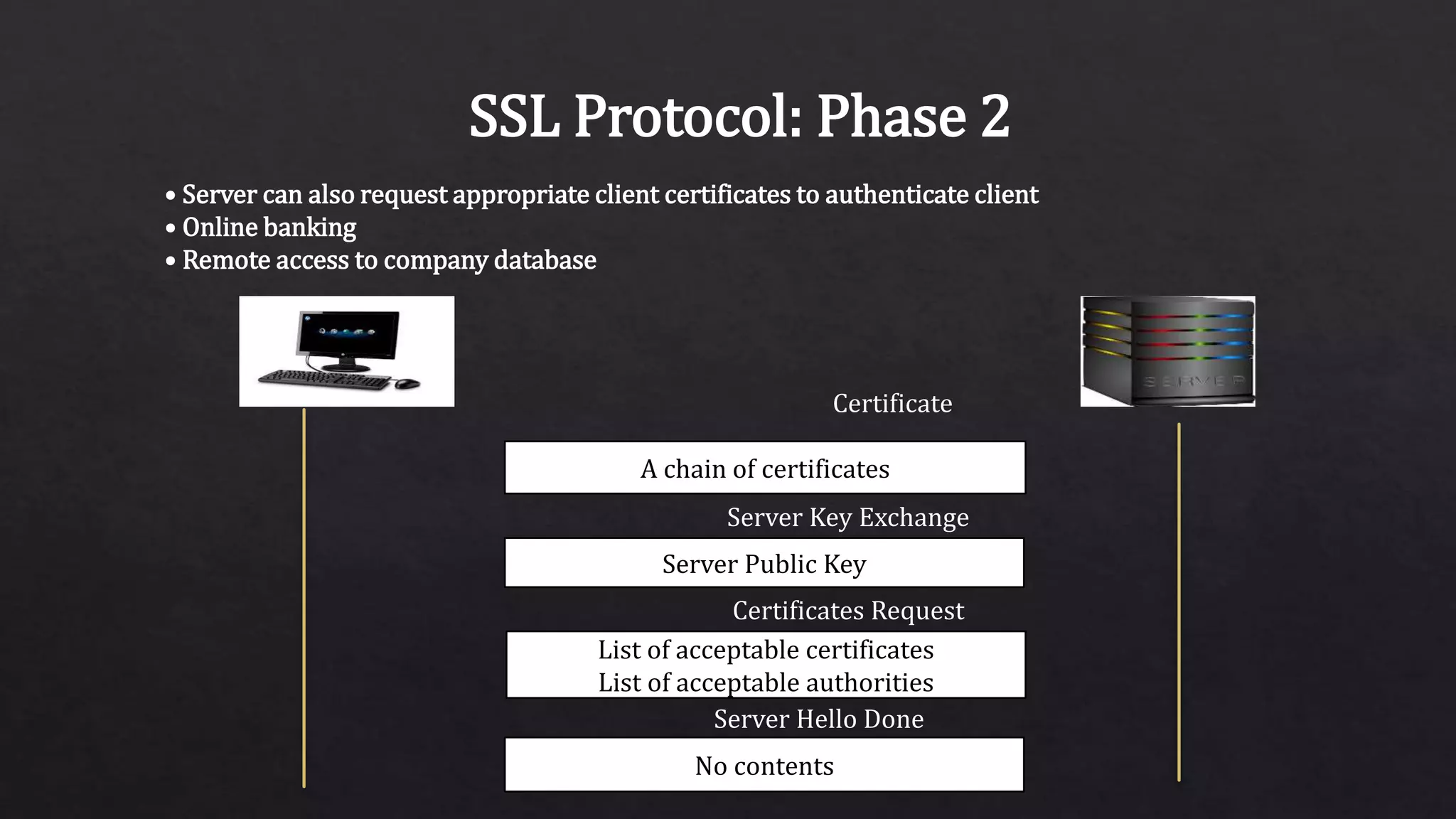
The document provides an overview of the Secure Sockets Layer (SSL) protocol, which is used for establishing an encrypted link between a web server and a browser to ensure data privacy and integrity. It details the SSL architecture, the process of SSL communication—including server and client authentication—and the various versions of the protocol. Additionally, it explains the steps involved in SSL communication and the importance of using certificates for secure transactions, such as those made on e-commerce websites.