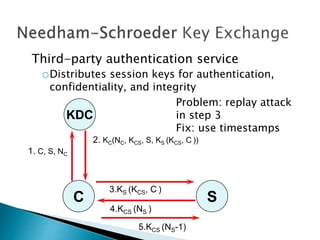
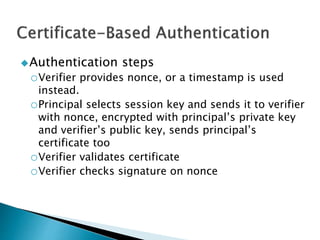
The document discusses key distribution and authentication using symmetric and asymmetric cryptography. It describes the Kerberos protocol which uses a key distribution center (KDC) to authenticate users and distribute session keys. It also discusses using public key certificates and digital signatures to solve the key distribution problem by having a certificate authority (CA) sign public keys.