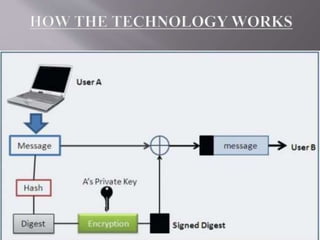
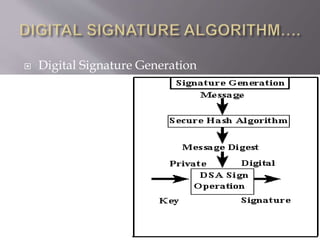
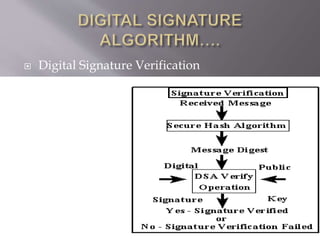
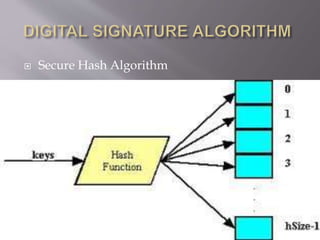
The document provides an overview of digital signatures, their history, purpose, and the technology behind them, emphasizing their importance in ensuring authenticity, integrity, and non-repudiation of electronic documents. It discusses the mechanics of digital signatures involving private and public keys, the digital signature certificate, and the advantages over traditional handwritten signatures. Challenges and opportunities related to the adoption of digital signatures, including costs and public perception, are also addressed.