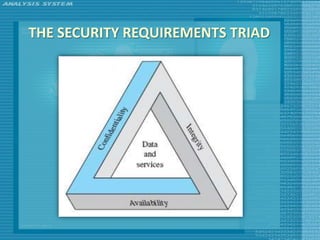
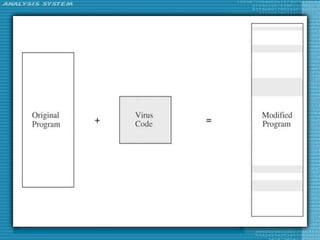
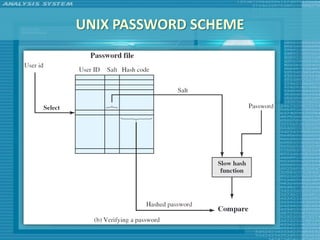
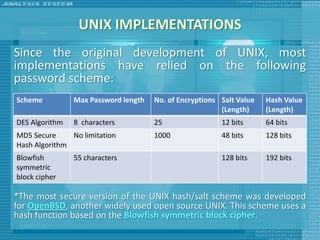
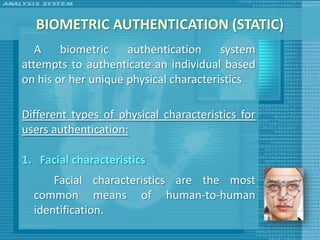
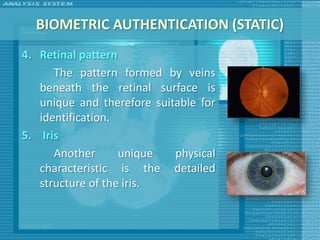
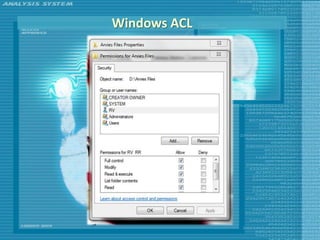
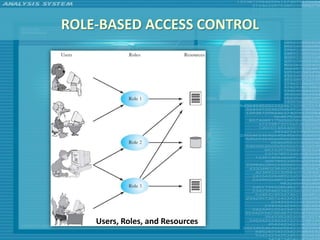
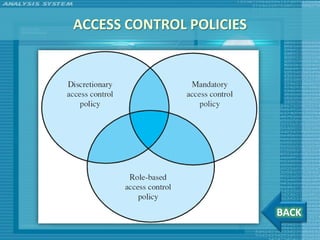
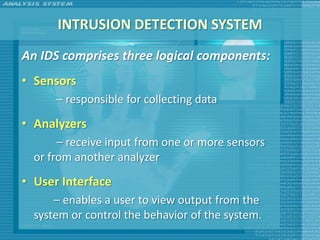
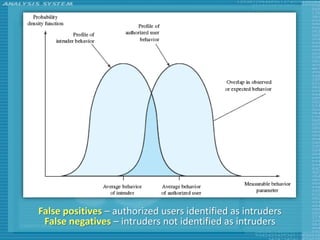
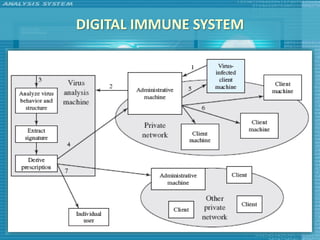
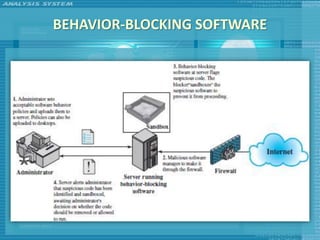
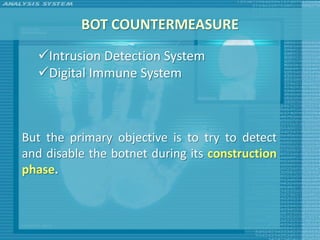
The document discusses various topics related to computer security including threats, attacks, intruders, malware, and security techniques. It describes common security threats like viruses, worms, bots, rootkits, and intruders. It also covers computer security objectives of confidentiality, integrity and availability. Authentication, access control, intrusion detection, and malware defense are discussed as security techniques.