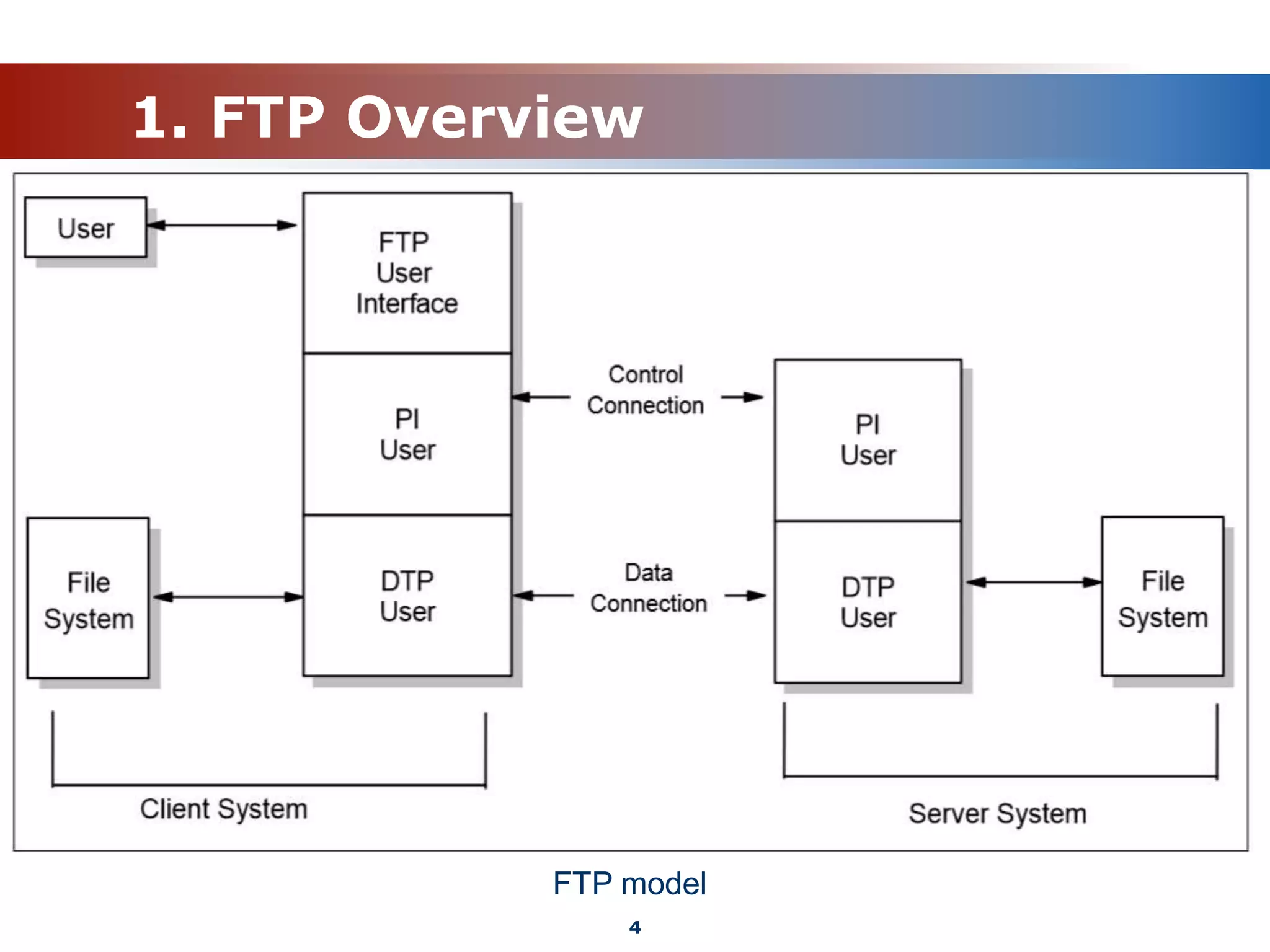
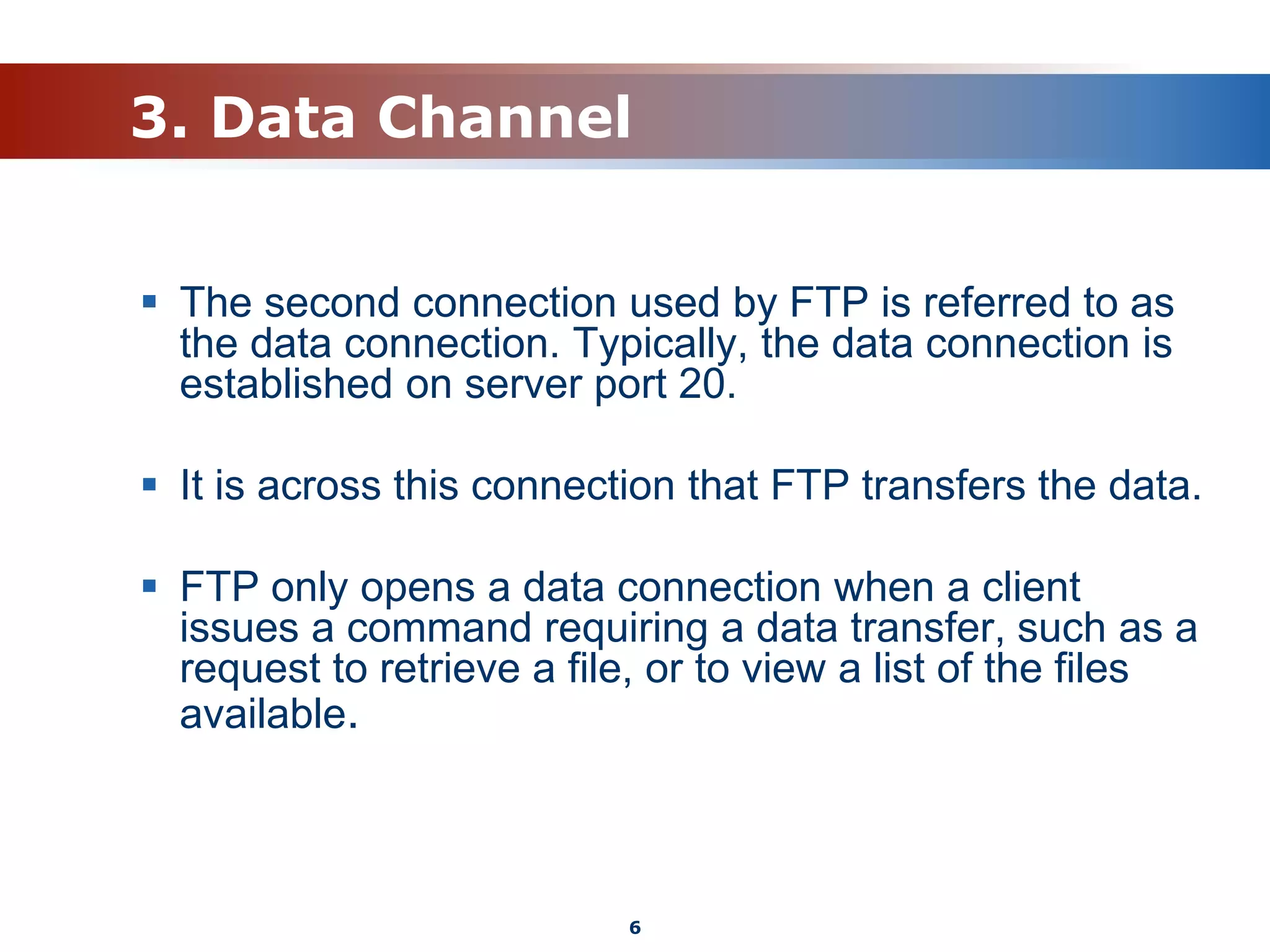
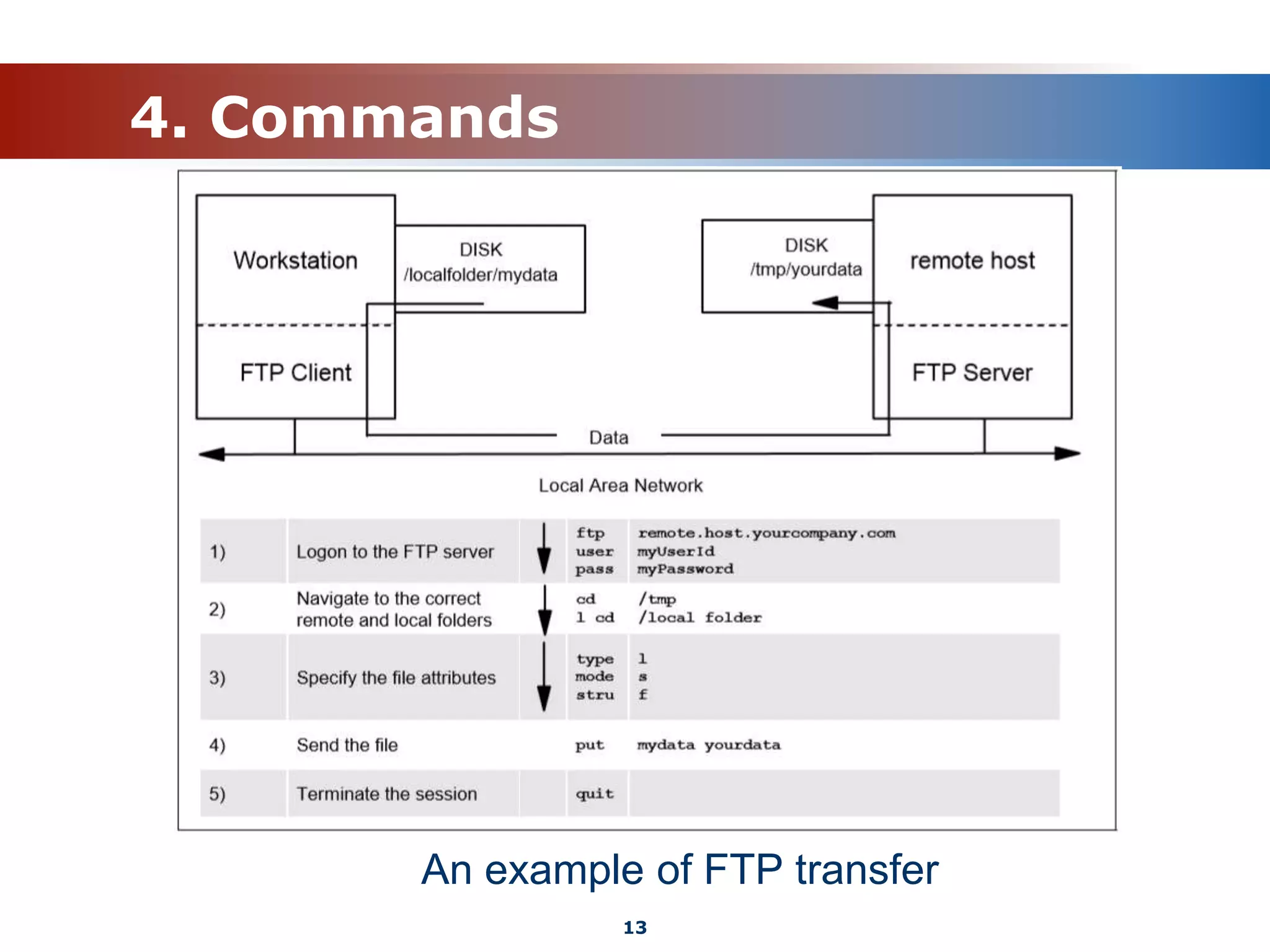
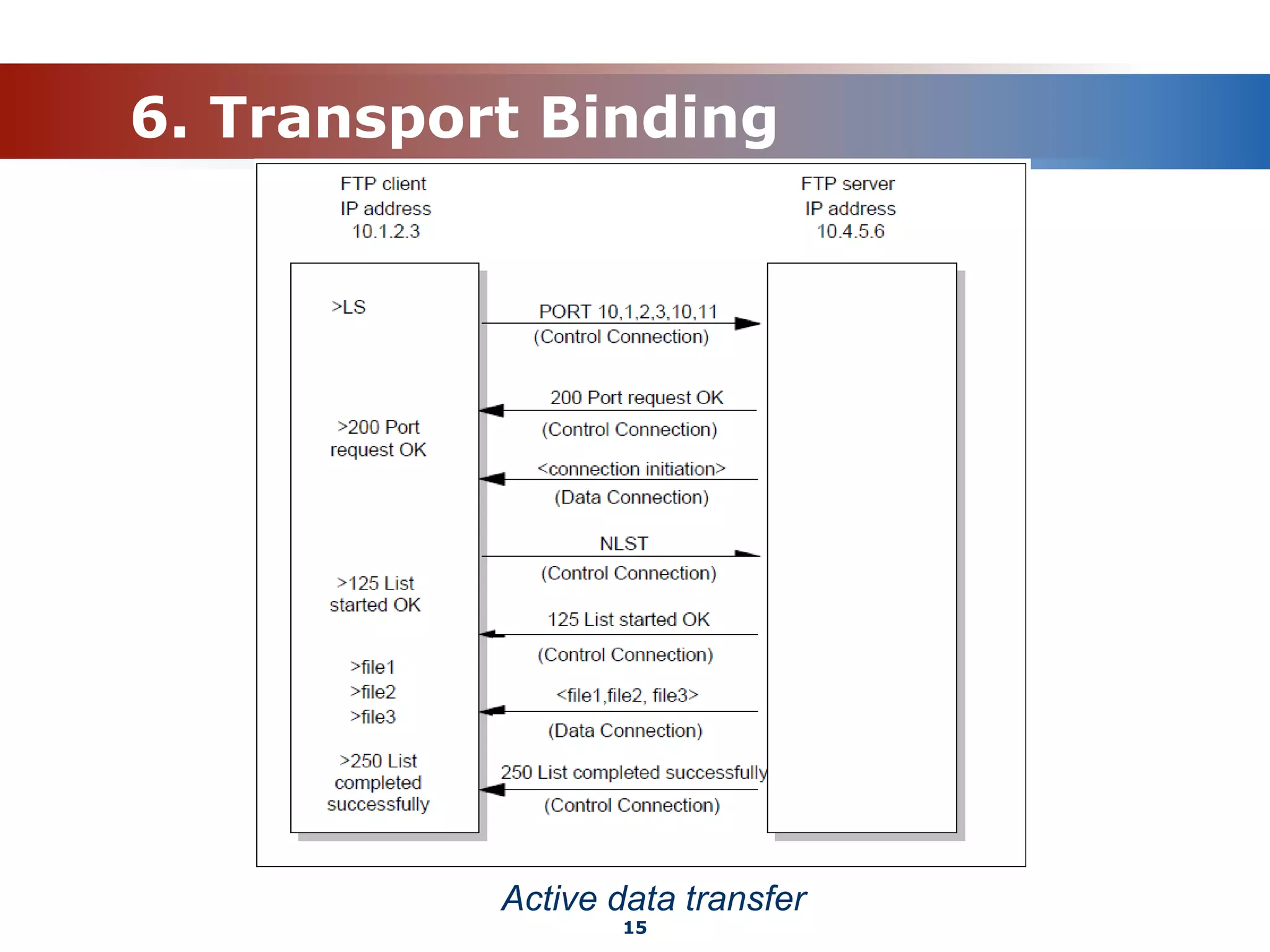
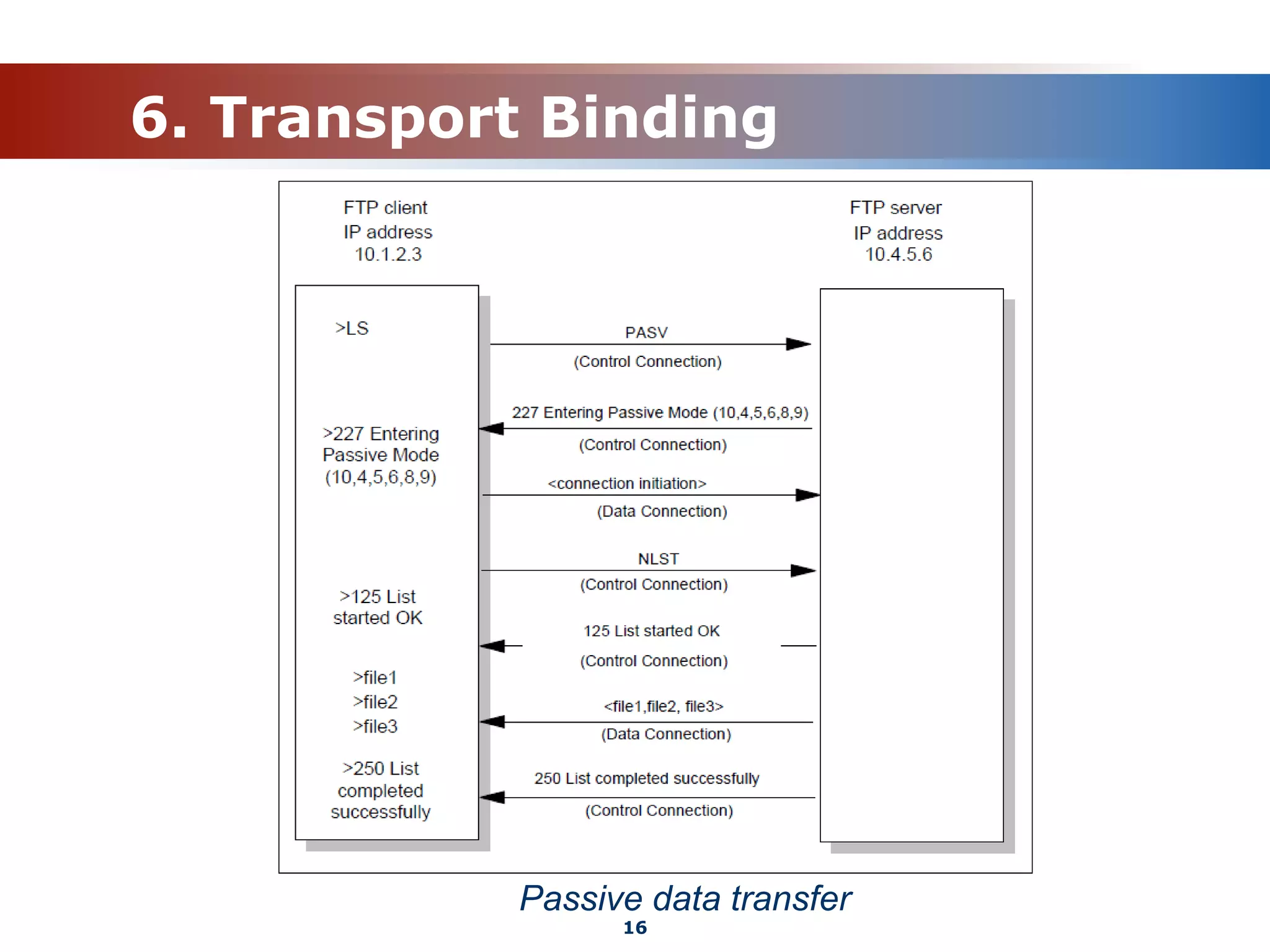
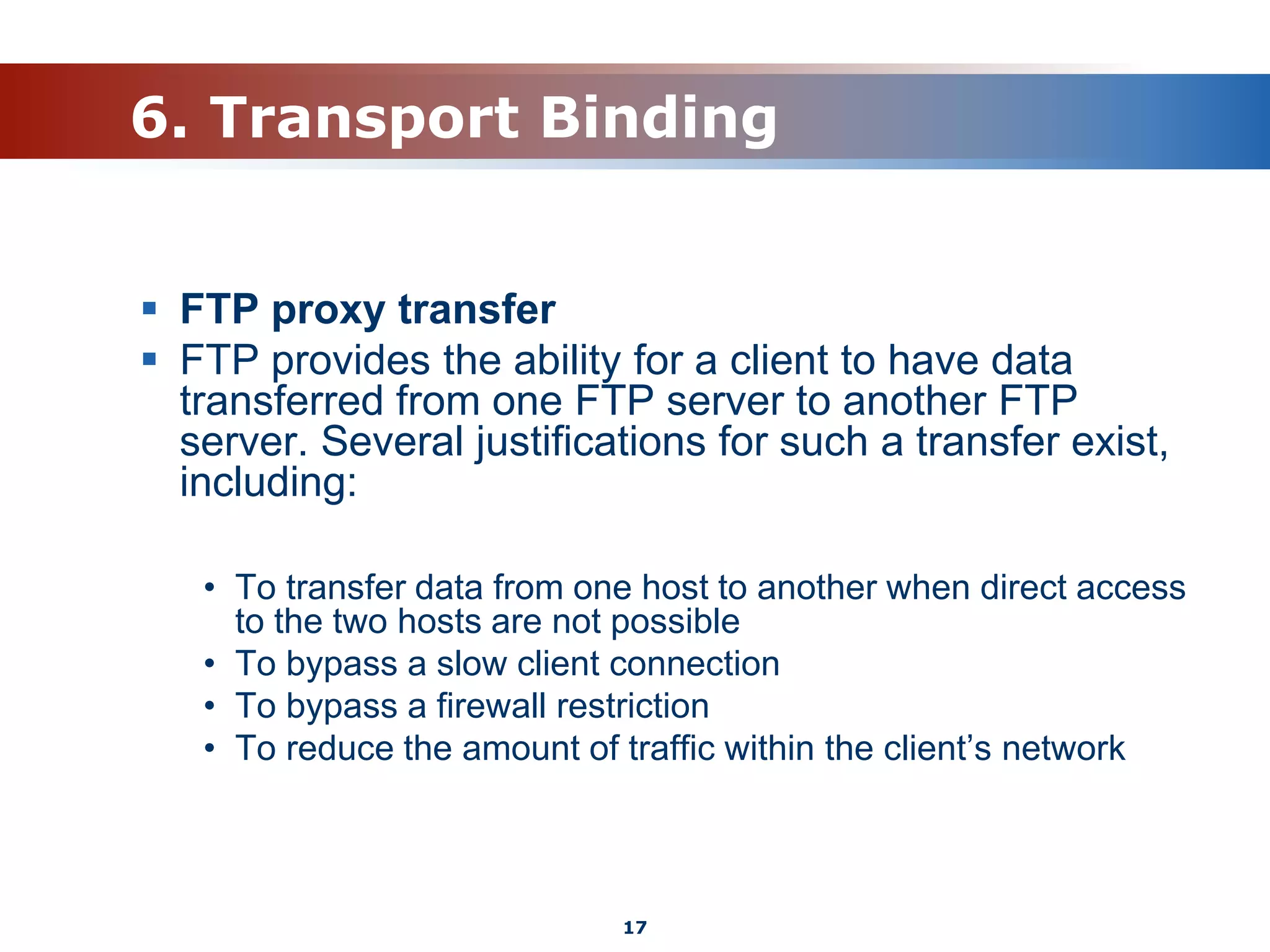
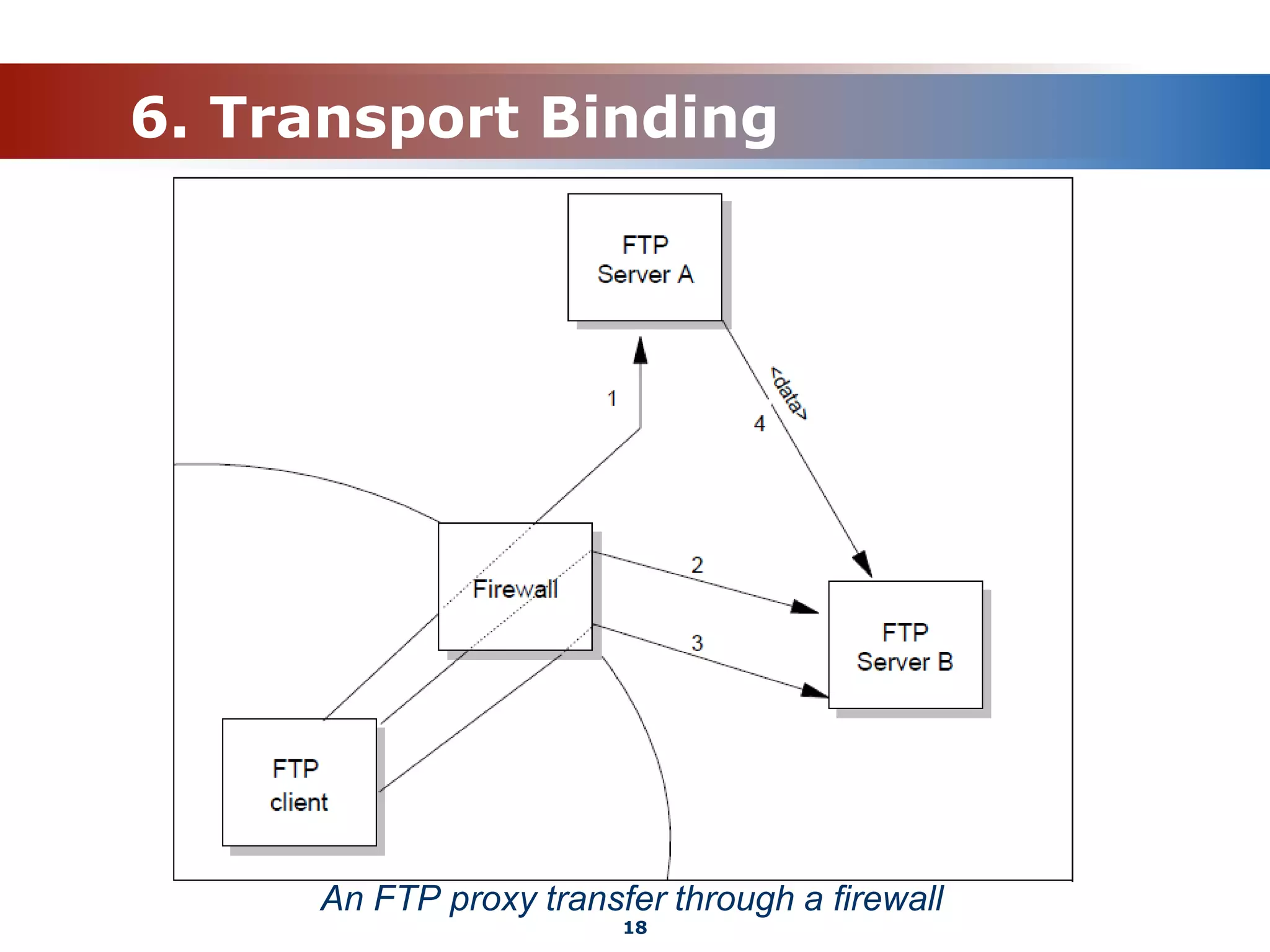
The document discusses the File Transfer Protocol (FTP). FTP uses two channels - a control channel over port 21 to send commands and a data channel over port 20 to transfer files. It describes common FTP commands to connect, navigate directories, set transfer properties, transfer files, and end sessions. The document also covers FTP status codes, transport bindings using active/passive modes, proxy transfers, and security issues like cleartext data transfers that FTP has addressed with TLS encryption.